SSH communication is secured using public key cryptography. When a user connects to the SSH-server using SSH-client for the first time, the SSH program stores the SSH-server public key in the user's home directory inside a file, known_hosts, in a hidden folder named ~/.ssh/, as shown in the following screenshot:
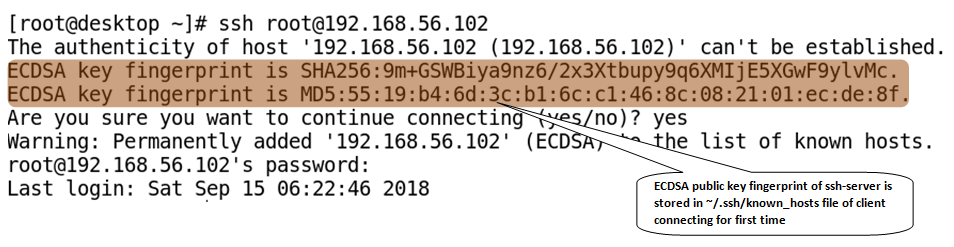
The following screenshot shows an example of a public key fingerprint of the remote host being stored in the client's known host file:

Now, subsequently whenever ssh-client connects to the server, it compares the public key sent by the server to the public key of the server stored in the ~/.ssh/known_hosts file. If the public key does not match, the client assumes that the network traffic is being hijacked or the server to which the connection is being made is not the same, and hence SSH-client breaks the connection, as shown here:
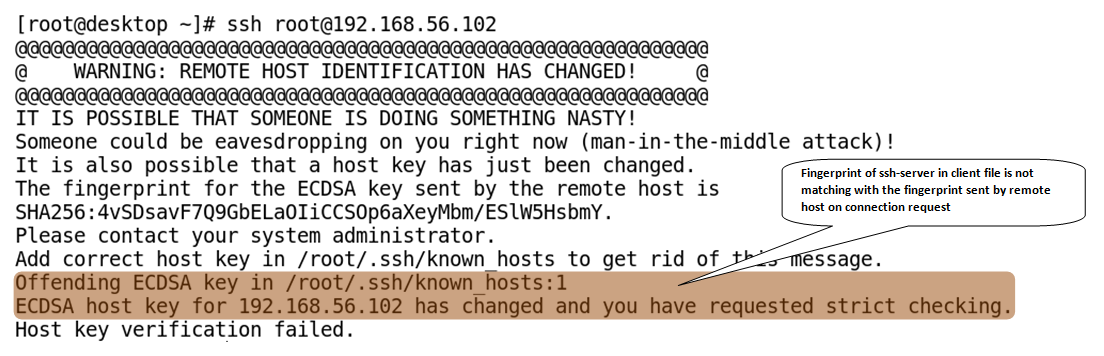
It is also a possibility that the server was reformatted or the server key replaced for any legitimate reason. In such circumstances, the user needs to update their ~/.ssh/known_hosts files by deleting the old keys to enable logging in to the server.
