*4.5. The Elliptic Curve Discrete Logarithm Problem (ECDLP)
Unlike the finite field DLP, there are no general-purpose subexponential algorithms to solve the ECDLP. Though good algorithms are known for certain specific types of elliptic curves, all known algorithms that apply to general curves take fully exponential time. The square root methods of Section 4.4 are the fastest known methods for solving the ECDLP over an arbitrary curve. As a result, elliptic curves are gaining popularity for building cryptosystems. The absence of subexponential algorithms implies that smaller fields can be chosen compared to those needed for cryptosystems based on the (finite field) DLP. This, in particular, results in smaller sizes of keys.
We start with Menezes, Okamoto and Vanstone’s (MOV) algorithm that reduces the ECDLP in a curve over ![]() to the DLP over the field
to the DLP over the field ![]() for some suitable
for some suitable ![]() . Since, the DLP can be solved in subexponential time, the ECDLP is also solved in that time, provided that the extension degree
. Since, the DLP can be solved in subexponential time, the ECDLP is also solved in that time, provided that the extension degree ![]() is small. For supersingular curves, one can choose k ≤ 6. For non-supersingular curves, this k is quite large, in general, and the MOV reduction takes exponential time.
is small. For supersingular curves, one can choose k ≤ 6. For non-supersingular curves, this k is quite large, in general, and the MOV reduction takes exponential time.
A linear-time algorithm is known to solve the ECDLP over anomalous curves (that is, curves with trace of Frobenius equal to 1). This algorithm is called the SmartASS method after its inventors Smart, Araki, Satoh and Semaev [257, 265, 282].
J. H. Silverman [277] has proposed an algorithm known as the xedni calculus method for solving the ECDLP over an arbitrary curve. Rigorous running times of this algorithm are not known, however heuristic analysis and experiments suggest that this algorithm is not really practical.
Let E be an elliptic curve over a finite field ![]() and let
and let ![]() be of order m. We want to compute indP Q (if it exists) for a point
be of order m. We want to compute indP Q (if it exists) for a point ![]() . Unless it is necessary, we will not assume any specific defining equation for E or a specific value of q.
. Unless it is necessary, we will not assume any specific defining equation for E or a specific value of q.
**4.5.1. The MOV Reduction
Let us first look at the structure of the group ![]() of m-torsion points on an elliptic curve defined over K. Here
of m-torsion points on an elliptic curve defined over K. Here ![]() is the algebraic closure of K.
is the algebraic closure of K.
Theorem 4.2.
|
Let K be a field of characteristic
|
Now, let E be an elliptic curve defined over a finite field K of characteristic p. Let ![]() with gcd(m, p) = 1. We use the shorthand notation E[m] for
with gcd(m, p) = 1. We use the shorthand notation E[m] for ![]() (and not for EK[m]). We want to define a function
(and not for EK[m]). We want to define a function
em : E[m] × E[m] → μm,
where ![]() is the group of m-th roots of unity (Exercise 4.24). This function em, known as the Weil pairing, helps us reduce the ECDLP in
is the group of m-th roots of unity (Exercise 4.24). This function em, known as the Weil pairing, helps us reduce the ECDLP in ![]() to the DLP in a suitable field
to the DLP in a suitable field ![]() . Let P,
. Let P, ![]() . The definition of em(P, R) calls for using divisors on E. Recall from Exercise 2.125 that a divisor
. The definition of em(P, R) calls for using divisors on E. Recall from Exercise 2.125 that a divisor ![]() belongs to
belongs to ![]() (that is, is the divisor of a rational function on E) if and only if
(that is, is the divisor of a rational function on E) if and only if ![]() and
and ![]() . Since
. Since ![]() , there is a rational function
, there is a rational function ![]() such that
such that ![]() . Now,
. Now, ![]() as well and p m2. Hence, by Theorem 4.2 there exists a point R′ of order m2 such that R = mR′. Since, #E[m] = m2, it follows that
as well and p m2. Hence, by Theorem 4.2 there exists a point R′ of order m2 such that R = mR′. Since, #E[m] = m2, it follows that ![]() and, therefore, there exists a rational function
and, therefore, there exists a rational function ![]() with
with ![]() . The functions f and g as introduced above are unique up to multiplication by elements of
. The functions f and g as introduced above are unique up to multiplication by elements of ![]() . One can show that we can choose f and g in such a manner that f ο λm = gm, where
. One can show that we can choose f and g in such a manner that f ο λm = gm, where ![]() is the multiplication map Q ↦ mQ. Then for
is the multiplication map Q ↦ mQ. Then for ![]() and
and ![]() we have gm(P + U) = f(mP + mU) = f(mU) = gm(U). Since g has only finitely many poles and zeros (whereas
we have gm(P + U) = f(mP + mU) = f(mU) = gm(U). Since g has only finitely many poles and zeros (whereas ![]() is infinite), we can choose U such that both g(U) and g(P + U) are defined and non-zero. For such a point U, we then have
is infinite), we can choose U such that both g(U) and g(P + U) are defined and non-zero. For such a point U, we then have ![]() and define
and define
em(P, R) := g(P + U)/g(U).
The right side can be shown to be independent of the choice of U. The relevant properties of the Weil pairing em are now listed.
Proposition 4.2.
|
Let P, P′, R,
| |||||||||||||||||||||
The above definition of em is not computationally effective. We will see later how we can compute em(P, T) in probabilistic polynomial time using an alternative (but equivalent) definition.
Algorithm 4.7 shows how the MOV reduction algorithm makes use of Weil pairing. We now clarify the subtle details of this algorithm.
Algorithm 4.7. MOV reduction
|
Input: A point Output: The index indP Q, that is, an integer l with Q = lP. Steps: Choose the smallest |
The correctness of the algorithm
From the bilinearity of the Weil pairing, it follows that if Q = lP, 0 ≤ l < m, then β = em(Q, R) = em(lP, R) = em(P, R)l = αl. Thus treating indα β as the least nonnegative integer modulo ord α we conclude that l = indα β if and only if ord α = m, that is, α is a primitive m-th root of unity. That α is an m-th root of unity for any ![]() is obvious from the definition of em. We now show that there exists some
is obvious from the definition of em. We now show that there exists some ![]() for which α = em(P, R) is primitive.
for which α = em(P, R) is primitive.
Lemma 4.1.
|
Let Proof If R1 + 〈P〉 = R2 + 〈P〉, then R1 = R2 + rP for some integer r and so by bilinearity and identity of Weil pairing em(P, R1) = em(P, R2)em(P, P)r = em(P, R2). Conversely, let em(P, R1) = em(P, R2). By Theorem 4.2, |
As an immediate corollary to Lemma 4.1, the desired result follows.
Proposition 4.3.
|
Let
Then #S/#E[m] = φ(m)/m. In particular, S is non-empty. Proof There are m distinct cosets of 〈P〉 in E[m]. Now, as R ranges over all points of E[m], the coset R+〈P〉 ranges over all of these m possibilities and, accordingly by Lemma 4.1 the value em(P, R) ranges over m distinct values. Since μm is cyclic of order m and hence with φ(m) generators, the theorem follows. |
By Theorem 3.1, one should try an expected number of O(ln ln m) random points ![]() before a primitive m-th root α = em(P, R) is found.
before a primitive m-th root α = em(P, R) is found.
Choosing k
Since E[m] consists of finitely many (m2) points, it is obvious that there exist finite values of k such that ![]() . It can also be shown that if
. It can also be shown that if ![]() , then
, then ![]() that is,
that is, ![]() for all P,
for all P, ![]() . The computation of the discrete logarithm indα β is then carried out in
. The computation of the discrete logarithm indα β is then carried out in ![]() . For Algorithm 4.7 to be efficient, one requires k to be rather small. However, for most curves, k is rather large implying that the MOV reduction is impractical for these curves. For the specific class of curves, the so-called supersingular curves, one can choose k to be rather small, namely k ≤ 6. We don’t go to the details of the choices for k for various cases of supersingular curves, but refer the reader to Menezes [192].
. For Algorithm 4.7 to be efficient, one requires k to be rather small. However, for most curves, k is rather large implying that the MOV reduction is impractical for these curves. For the specific class of curves, the so-called supersingular curves, one can choose k to be rather small, namely k ≤ 6. We don’t go to the details of the choices for k for various cases of supersingular curves, but refer the reader to Menezes [192].
Computing em(P, R)
We start with an alternative definition of the Weil pairing ![]() for P,
for P, ![]() . First note that if
. First note that if ![]() is a divisor and if
is a divisor and if ![]() is a rational function on E such that for every pole or zero T of f one has mT = 0 (that is, such that Div(f) and T have disjoint supports), then one can define
is a rational function on E such that for every pole or zero T of f one has mT = 0 (that is, such that Div(f) and T have disjoint supports), then one can define
![]()
Choose points U, ![]() (where
(where ![]() ) and consider the divisors DP := [P + U] – [U] and DR := [R + V] – [V]. Since
) and consider the divisors DP := [P + U] – [U] and DR := [R + V] – [V]. Since ![]() ) is infinite, one can choose both P + U and U distinct from R + V and V. Since P,
) is infinite, one can choose both P + U and U distinct from R + V and V. Since P, ![]() , it follows that mDP and mDR are principal, namely, there are rational functions fP and fR such that Div(fP) = mDP = m[P + U] – m[U] and Div(fR) = mDR = m[R + V] – m[V]. One can show that
, it follows that mDP and mDR are principal, namely, there are rational functions fP and fR such that Div(fP) = mDP = m[P + U] – m[U] and Div(fR) = mDR = m[R + V] – m[V]. One can show that
Equation 4.11
![]()
independent of the choice of U and V as long as fP (DR) and fR(DP) are defined. Therefore, em(P, R) can be computed efficiently, if fP and fR can be computed efficiently. To this effect we now describe an algorithm for computing the rational function f of a principal divisor ![]() , where
, where ![]() . Since deg
. Since deg ![]() , we can write
, we can write ![]() . Suppose that we have an Algorithm A that, for a pair of reduced divisors
. Suppose that we have an Algorithm A that, for a pair of reduced divisors
![]()
and
![]()
computes the sum (a reduced divisor)
![]()
Then, f can be computed by repeated application of Algorithm A as follows.
Compute for each i = 1, . . . , r the reduced divisor
 . Let 1 = ai1, ai2, . . . , aiti = |mi| be an addition chain for |mi| (Exercise 3.18). Clearly, ti – 1 applications of Algorithm A computes Δi. Since we can choose ti ≤ 2 ⌈lg |mi|⌉, each Δi can be computed using O(log |mi|) applications of Algorithm A.
. Let 1 = ai1, ai2, . . . , aiti = |mi| be an addition chain for |mi| (Exercise 3.18). Clearly, ti – 1 applications of Algorithm A computes Δi. Since we can choose ti ≤ 2 ⌈lg |mi|⌉, each Δi can be computed using O(log |mi|) applications of Algorithm A.Compute f by computing D = Div(f) = Δ1 + ··· + Δr. This can be done by applying Algorithm A a total of r – 1 times.
What remains is the description of Algorithm A that computes P3 and f3 from a knowledge of P1, P2, f1 and f2. Clearly, if ![]() , then we have P3 = P2 and f3 = f1f2. Similar is the case for
, then we have P3 = P2 and f3 = f1f2. Similar is the case for ![]() . So assume
. So assume ![]() and
and ![]() . Let l1 be the line passing through P1 and P2 and P′ := –(P1 + P2). First, assume that
. Let l1 be the line passing through P1 and P2 and P′ := –(P1 + P2). First, assume that ![]() . By Exercise 2.125, we have
. By Exercise 2.125, we have ![]() . Let l2 be the (vertical) line passing through P′ and –P′. Again by Exercise 2.125, we have
. Let l2 be the (vertical) line passing through P′ and –P′. Again by Exercise 2.125, we have ![]() . But then
. But then ![]() , that is, we take P3 = –P′ = P1+P2 and f3 = f1f2l1/l2. Finally, if
, that is, we take P3 = –P′ = P1+P2 and f3 = f1f2l1/l2. Finally, if ![]() , then
, then ![]() and, therefore,
and, therefore, ![]() . Thus, in this case too, we take
. Thus, in this case too, we take ![]() and f3 = f1f2l1/l2 with l2 := 1.
and f3 = f1f2l1/l2 with l2 := 1.
Before we finish the description of the MOV reduction, some comments are in order. First note that if f1, ![]() and P1,
and P1, ![]() , then both l1 and l2 are in K(E) and the computation of f3 and P3 can be carried out by working in K only.
, then both l1 and l2 are in K(E) and the computation of f3 and P3 can be carried out by working in K only.
Second, consider the (general) case ![]() . Since
. Since ![]() , the rational function f3 has poles and is, therefore, undefined only at the points P3 and
, the rational function f3 has poles and is, therefore, undefined only at the points P3 and ![]() . f3 is certainly defined at –P3, but l2(–P3) = 0 and, therefore, evaluating f3(–P3) as (f1f2l1)(–P3)/l2(–P3) fails. Of course, there is a rational function g such that both f1f2l1g and l2g are defined and non-zero at –P3, but finding such a rational function is an added headache. So we choose to continue to have the representation f3 = f1f2l1/l2 and agree not to evaluate f3 at –P3. Recall from Equation (4.11) that we want to evaluate fP at DR (that is, at R + V and V) and also fR and DP (that is, at P + U and U). Let us assume that we use the addition chain 1 = a1, a2, . . . , at = m for m. This means that we cannot evaluate fP at the points ±ai(P + U) and ±aiU for all i = 1, . . . , t. Therefore, V should be chosen such that both R + V and V are not one of these points. Similar constraints dictate the choice of U. However, if m is sufficiently large (m ≥ 1024) and if we choose an addition chain of length t ≤ 2 ⌈lg m⌉, then it can be easily seen that for a random choice of (U, V) the evaluation of fP (DR) or fR(DP) fails with a probability of no more than 1/2. Therefore, few random choices of (U, V) are expected to make the algorithm work. This is the only place where a probabilistic behaviour of the algorithm creeps in. In practice, however, this is not a serious problem, since we have much larger values of m (than 1024) and accordingly the above probability of failure becomes negligibly small.
. f3 is certainly defined at –P3, but l2(–P3) = 0 and, therefore, evaluating f3(–P3) as (f1f2l1)(–P3)/l2(–P3) fails. Of course, there is a rational function g such that both f1f2l1g and l2g are defined and non-zero at –P3, but finding such a rational function is an added headache. So we choose to continue to have the representation f3 = f1f2l1/l2 and agree not to evaluate f3 at –P3. Recall from Equation (4.11) that we want to evaluate fP at DR (that is, at R + V and V) and also fR and DP (that is, at P + U and U). Let us assume that we use the addition chain 1 = a1, a2, . . . , at = m for m. This means that we cannot evaluate fP at the points ±ai(P + U) and ±aiU for all i = 1, . . . , t. Therefore, V should be chosen such that both R + V and V are not one of these points. Similar constraints dictate the choice of U. However, if m is sufficiently large (m ≥ 1024) and if we choose an addition chain of length t ≤ 2 ⌈lg m⌉, then it can be easily seen that for a random choice of (U, V) the evaluation of fP (DR) or fR(DP) fails with a probability of no more than 1/2. Therefore, few random choices of (U, V) are expected to make the algorithm work. This is the only place where a probabilistic behaviour of the algorithm creeps in. In practice, however, this is not a serious problem, since we have much larger values of m (than 1024) and accordingly the above probability of failure becomes negligibly small.
Finally, note that if we multiply the factors f1, f2 and l1 in the numerator, then the coefficients of the numerator grow very rapidly, when the algorithm is applied repeatedly. Thus we prefer to keep the numerator in the factored form. The same applies to the denominator as well.
**4.5.2. The SmartASS Method
The SmartASS method, named after its inventors Smart [282], Satoh and Araki [257] and Semaev [265], is also called the anomalous attack to solve the ECDLP, since it is applicable to anomalous elliptic curves. Let ![]() be a finite field of odd prime cardinality p and E an elliptic curve defined over
be a finite field of odd prime cardinality p and E an elliptic curve defined over ![]() . We assume that E is anomalous: that is, the trace of Frobenius of E at p is 1; that is,
. We assume that E is anomalous: that is, the trace of Frobenius of E at p is 1; that is, ![]() . Since p is prime, the group
. Since p is prime, the group ![]() is cyclic and, in particular, isomorphic to the additive group (
is cyclic and, in particular, isomorphic to the additive group (![]() , +). This isomorphism is effectively exploited by the SmartASS method to give a polynomial time algorithm for computing ECDLP in the group
, +). This isomorphism is effectively exploited by the SmartASS method to give a polynomial time algorithm for computing ECDLP in the group ![]() .
.
Before proceeding further we introduce some auxiliary results. Recall (Exercise 2.133) that a local PID is called a discrete valuation ring (DVR). Now, we see an equivalent definition of a DVR, that gives a justification to its name.
Definition 4.3.
A DVR can be characterized as follows:
Proposition 4.4.
|
Let R be an integral domain and let K := Q(R) be the field of fractions of R. Then R is a DVR if and only if there exists a discrete valuation Proof [if] By definition, Let By definition, |
Recall that the ring ![]() of p-adic integers (Definition 2.111) is a DVR. The field
of p-adic integers (Definition 2.111) is a DVR. The field ![]() of fractions of
of fractions of ![]() is called the field of p-adic numbers. We now explicitly describe a valuation v on
is called the field of p-adic numbers. We now explicitly describe a valuation v on ![]() of which
of which ![]() is the valuation ring. Let the p-adic expansion (Exercises 2.144 and 2.145) of a p-adic integer α be
is the valuation ring. Let the p-adic expansion (Exercises 2.144 and 2.145) of a p-adic integer α be
Equation 4.12
![]()
A rational integer can be naturally viewed as a p-adic integer with finitely many nonzero terms, that is, one for which ki = 0 except for finitely many ![]() . However, a p-adic integer with infinitely many non-zero ki does not correspond to a rational integer. If in Expansion (4.12) we have k1 = k2 = ··· = kr–1 = 0, we can write
. However, a p-adic integer with infinitely many non-zero ki does not correspond to a rational integer. If in Expansion (4.12) we have k1 = k2 = ··· = kr–1 = 0, we can write
α = pr(kr + kr+1p + kr+2p2 + ···).
A p-adic integer is, in general, an infinite series and a representation with finite precision looks like
k0 + k1p + k2p2 + ··· + ksps + O(ps+1).
Arithmetic on p-adic numbers is done like integers written in base p, but from left to right. Thus, for example, if one wants to add two p-adic integers k0 + k1p + k2p2 + ... and ![]() , one may add the base-p integers ... k2k1k0 and
, one may add the base-p integers ... k2k1k0 and ![]() in the usual manner till the desired level of precision. A p-adic integer α = k0 + k1p k2p2 + ··· is invertible (in
in the usual manner till the desired level of precision. A p-adic integer α = k0 + k1p k2p2 + ··· is invertible (in ![]() ) if and only if k0 ≠ 0 (Proposition 2.52).
) if and only if k0 ≠ 0 (Proposition 2.52).
An element ![]() also has a p-adic expansion, but in this case one has to allow terms involving a finite number of negative exponents of p. That is to say, we have an expansion of the form
also has a p-adic expansion, but in this case one has to allow terms involving a finite number of negative exponents of p. That is to say, we have an expansion of the form
β = k–tp–t + k–t+1p–t+1 + ··· + k–1p–1 + k0 + k1p + k2p2 + ···
or
β = p–t(k–t + k–t+1p + ··· + k–1pt–1 + k0pt + k1pt+1 + k2pt+2 + ···).
Of course, if k–t = k–t+1 = ··· = k–1 = 0, then β is already in ![]() .
.
From the arguments above, it follows that any non-zero ![]() can be written uniquely as γ = pδ(γ0 + γ1p + γ2p2 + ···) with
can be written uniquely as γ = pδ(γ0 + γ1p + γ2p2 + ···) with ![]() and γ0 ≠ 0. We then set v(γ) := δ. It is easy to see that v defines a discrete valuation on
and γ0 ≠ 0. We then set v(γ) := δ. It is easy to see that v defines a discrete valuation on ![]() of which
of which ![]() is the valuation ring. Moreover, since γ0 + γ1p + γ2p2 + ··· is a unit in
is the valuation ring. Moreover, since γ0 + γ1p + γ2p2 + ··· is a unit in ![]() , p = 0 + 1 · p + 0 · p2 + ··· plays the role of a uniformizer of the DVR
, p = 0 + 1 · p + 0 · p2 + ··· plays the role of a uniformizer of the DVR ![]() . As usual, we write v(0) = +∞.
. As usual, we write v(0) = +∞.
Now, back to our ECDLP business. Let E be an elliptic curve defined over ![]() . Here we consider the case that E is anomalous. We can naturally think of E as a curve over the field
. Here we consider the case that E is anomalous. We can naturally think of E as a curve over the field ![]() as well and denote this curve by ε. The coordinate-wise application of the canonical surjection
as well and denote this curve by ε. The coordinate-wise application of the canonical surjection ![]() induces the reduction homomorphism
induces the reduction homomorphism ![]() . Now, we define the following subgroups of
. Now, we define the following subgroups of ![]() :
:

It can be shown that ![]() is a subgroup of
is a subgroup of ![]() and
and ![]() is a subgroup of
is a subgroup of ![]() . Furthermore, since E is anomalous, we have
. Furthermore, since E is anomalous, we have
![]()
Now, let ![]() and Q a point in the subgroup of
and Q a point in the subgroup of ![]() generated by P. Our purpose is to find an integer l such that Q = lP. Let
generated by P. Our purpose is to find an integer l such that Q = lP. Let ![]() ,
, ![]() be such that
be such that ![]() and
and ![]() . It is not difficult to find such points
. It is not difficult to find such points ![]() and
and ![]() . For example, if P = (a, b), we can take
. For example, if P = (a, b), we can take ![]() , where b0 = b and b1, b2, . . . are successively obtained by Hensel lifting.
, where b0 = b and b1, b2, . . . are successively obtained by Hensel lifting.
Since ![]() , the point
, the point ![]() and, therefore,
and, therefore, ![]() . Now, if we take the so-called p-adic elliptic logarithm ψp on both sides, we get
. Now, if we take the so-called p-adic elliptic logarithm ψp on both sides, we get ![]() (mod p2), whence it follows that
(mod p2), whence it follows that
![]()
provided that ![]() is invertible modulo p. The function ψp can be easily calculated. Therefore, this gives a very efficient probabilistic algorithm for computing discrete logarithms over anomalous elliptic curves. Here the most time-consuming step is the linear-time computation of the points p
is invertible modulo p. The function ψp can be easily calculated. Therefore, this gives a very efficient probabilistic algorithm for computing discrete logarithms over anomalous elliptic curves. Here the most time-consuming step is the linear-time computation of the points p![]() and p
and p![]() . For further details on the algorithm (like the computation of
. For further details on the algorithm (like the computation of ![]() and
and ![]() from P and Q, and the definition of p-adic elliptic logarithms), see Blake et al. [24] and Silverman [275].
from P and Q, and the definition of p-adic elliptic logarithms), see Blake et al. [24] and Silverman [275].
**4.5.3. The Xedni Calculus Method
Joseph Silverman’s xedni calculus method (XCM) is a recent algorithm for solving the ECDLP in an arbitrary elliptic curve over a finite field. The algorithm is based on some deep mathematical conjectures and heuristic ideas. However, its performance has been experimentally established to be poor. Here we give a sketchy description of the XCM. For simplicity, we concentrate on elliptic curves over prime fields ![]() only.
only.
The basic idea of the XCM is to lift an elliptic curve E over ![]() to a curve ε over
to a curve ε over ![]() . In view of this, we start with a couple of important results regarding elliptic curves over
. In view of this, we start with a couple of important results regarding elliptic curves over ![]() (or, more generally, over a number field). See Silverman [275], for example, for the proofs.
(or, more generally, over a number field). See Silverman [275], for example, for the proofs.
Let ε be an elliptic curve defined over a number field K.
Theorem 4.3. Mordell–Weil theorem
|
The group ε(K) is finitely generated. The group structure of ε(K) is made explicit by the next theorem. Note that the elements of ε(K) of finite order form a subgroup εtors(K) of ε(K), called the torsion subgroup of ε(K) (Exercise 4.26). |
Theorem 4.4.
|
The non-negative integer ρ of Theorem 4.4 is called the rank of ε(K). Now, let E be an elliptic curve defined over a prime field The basic idea of the XCM is to select r points 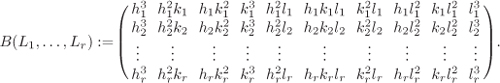
|
We start by fixing an integer r, 4 ≤ r ≤ 9. We then choose r random pairs (si, ti) of integers and compute the points
![]()
We now apply a change of coordinates of the form
Equation 4.13

so that the first four of the points Rp,i become Rp,1 = [1, 0, 0], Rp,2 = [0, 1, 0], Rp,3 = [0, 0, 1] and Rp,4 = [1, 1, 1]. This change of coordinates fails if some three of the four points Rp,1, Rp,2, Rp,3 and Rp,4 sum to ![]() . But in that case the desired index indP Q can be computed with high probability. If, for example,
. But in that case the desired index indP Q can be computed with high probability. If, for example, ![]() , then we have (s1 + s2 + s3)P = (t1 + t2 + t3)Q and, therefore, if gcd(t1 + t2 + t3, n) = 1, then indP Q ≡ (t1 + t2 + t3)–1(s1 + s2 + s3) (mod n). On the other hand, if gcd(t1 + t2 + t3, n) ≠ 1, we repeat with a different set of pairs (si, ti).
, then we have (s1 + s2 + s3)P = (t1 + t2 + t3)Q and, therefore, if gcd(t1 + t2 + t3, n) = 1, then indP Q ≡ (t1 + t2 + t3)–1(s1 + s2 + s3) (mod n). On the other hand, if gcd(t1 + t2 + t3, n) ≠ 1, we repeat with a different set of pairs (si, ti).
Henceforth, we assume that the change of coordinates, as given in Equation (4.13), is successful. This transforms the equation for E to a general cubic equation:
Cp : up,1X3 + up,2X2Y + up,3XY2 + up,4Y3 + up,5X2Z + up,6XY Z + up,7Y2Z + up,8XZ2 + up,9Y Z2 + up,10Z3 = 0.
Now, we carry out a step that heuristically ensures that the curve ε over ![]() (that we are going to construct) has a small rank. We choose a product M of small primes with p M, a cubic curve
(that we are going to construct) has a small rank. We choose a product M of small primes with p M, a cubic curve
CM : uM,1X3 + uM,2X2Y + uM,3XY2 + uM,4Y3 + uM,5X2Z + uM,6XYZ + uM,7Y2Z + uM,8XZ2 + uM,9Y Z2 + uM,10Z3 ≡ 0 (mod M)
over ![]() and points RM,1, . . . , RM,r on CM and with coordinates in
and points RM,1, . . . , RM,r on CM and with coordinates in ![]() . The first four points should be RM,1 = [1, 0, 0], RM,2 = [0, 1, 0], RM,3 = [0, 0, 1] and RM,4 = [1, 1, 1]. We have to ensure also that for every prime divisor q of M, the matrix B(RM,1, . . . , RM,r) has maximal rank modulo q. In practice, it is easier to choose the points RM,1, . . . , RM,r first and then compute a curve CM passing through these points by solving a set of linear equations in the coefficients uM,1, . . . , uM,10 of CM. The curve CM should be so chosen that it has the minimum possible number of solutions modulo M. This, in conjunction with some deep conjectures in the theory of elliptic curves, guarantees that the curve ε that we will construct shortly will have a rank less than the expected value.
. The first four points should be RM,1 = [1, 0, 0], RM,2 = [0, 1, 0], RM,3 = [0, 0, 1] and RM,4 = [1, 1, 1]. We have to ensure also that for every prime divisor q of M, the matrix B(RM,1, . . . , RM,r) has maximal rank modulo q. In practice, it is easier to choose the points RM,1, . . . , RM,r first and then compute a curve CM passing through these points by solving a set of linear equations in the coefficients uM,1, . . . , uM,10 of CM. The curve CM should be so chosen that it has the minimum possible number of solutions modulo M. This, in conjunction with some deep conjectures in the theory of elliptic curves, guarantees that the curve ε that we will construct shortly will have a rank less than the expected value.
We now combine the curves Cp and CM as follows. Using the Chinese remainder theorem, we compute integers ![]() such that
such that ![]() (mod p) and
(mod p) and ![]() (mod M) for each i = 1, . . . , 10. Similarly, we compute points R1, . . . , Rr with integer coefficients such that Ri ≡ Rp,i (mod p) and Ri ≡ RM,i (mod M) for each i = 1, . . . , r, where congruence of points stands for coordinate-wise congruence. Here we have R1 = [1, 0, 0], R2 = [0, 1, 0], R3 = [0, 0, 1] and R4 = [1, 1, 1].
(mod M) for each i = 1, . . . , 10. Similarly, we compute points R1, . . . , Rr with integer coefficients such that Ri ≡ Rp,i (mod p) and Ri ≡ RM,i (mod M) for each i = 1, . . . , r, where congruence of points stands for coordinate-wise congruence. Here we have R1 = [1, 0, 0], R2 = [0, 1, 0], R3 = [0, 0, 1] and R4 = [1, 1, 1].
Clearly, the points R1, . . . , Rr are lifts of the points Rp,1, . . . , Rp,r respectively, whereas the cubic curve
![]()
over ![]() is a lift of E. However,
is a lift of E. However, ![]() , treated as a curve over
, treated as a curve over ![]() , need not pass through the points R1, . . . , Rr. In order to ensure this last condition, we modify the coefficients
, need not pass through the points R1, . . . , Rr. In order to ensure this last condition, we modify the coefficients ![]() of
of ![]() to the (small integer) coefficients u1, . . . , u10 by solving the system of linear equations
to the (small integer) coefficients u1, . . . , u10 by solving the system of linear equations
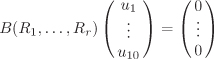
subject to the condition that ![]() (mod pM) for each i = 1, . . . , 10. The resulting cubic curve
(mod pM) for each i = 1, . . . , 10. The resulting cubic curve
C : u1X3 + u2X2Y + u3XY2 + u4Y3 + u5X2Z + u6XYZ + u7Y2Z + u8XZ2 + u9Y Z2 + u10Z3 = 0
over ![]() evidently continues to be a lift of E.
evidently continues to be a lift of E.
Now, we apply a change of coordinates in order to transfer ![]() to the standard Weierstrass equation
to the standard Weierstrass equation
ε : Y2 + a1XY + a3Y = X3 + a2X2 + a4X + a6
with integer coefficients ai. This transformation changes the points R1, . . . , Rr to the points S1, . . . , Sr. One should also ensure that ![]() .
.
Finally, we check if S2, . . . , Sr are linearly dependent. If so, we determine a (non-trivial) relation ![]() with
with ![]() . This corresponds to the relation
. This corresponds to the relation ![]() , where n1 := –(n2 + ··· + nr), that is, sP = tQ with s := n1s1 + ··· + nrsr and t := n1t1 + ··· + nrtr. If gcd(t, n) = 1, we have indP Q ≡ t–1s (mod n).
, where n1 := –(n2 + ··· + nr), that is, sP = tQ with s := n1s1 + ··· + nrsr and t := n1t1 + ··· + nrtr. If gcd(t, n) = 1, we have indP Q ≡ t–1s (mod n).
On the other hand, if S2, . . . , Sr are linearly independent or if gcd(t, n) > 1, then the lifted data fail to compute indP Q. In that case, we repeat the entire process by selecting new pairs (si, ti) and/or new points RM,1, . . . , RM,r.
This completes our description of the XCM. See Silverman [277] for further details. No rigorous or heuristic analysis of the running time of the XCM is available in the literature. Practical experience (reported in Jacobson et al. [139]) shows that the algorithm is rather impractical. The predominant cause for failure of a trial of the XCM is that the probability that the points S2, . . . , Sr are linearly dependent is amazingly low. Suitable choices of the curve CM help us to construct curves ε of low rank, but not low enough, in general, to render S2, . . . , Sr linearly dependent. Larger values of r are expected to increase the probability of success in each trial, but it is not clear how to handle the values r > 9. Nevertheless, the XCM is a radically new idea to solve the ECDLP. As Joseph Silverman [277] says, “some of the ideas may prove useful in future work on ECDLP”.
Exercise Set 4.5
| 4.24 | Let K be a field,
|
| 4.25 | We use the notations of the last exercise and assume that #μm = m, that is, either char K = 0 or p := char K > 0 is coprime to m. In this case, a generator of μm is called a primitive m-th root of unity. If
where the product runs over all primitive m-th roots of unity, is called the m-th cyclotomic polynomial (over K). Clearly, deg Φm(X) = φ(m) (where φ is Euler’s totient function).
|
| 4.26 |
|
