The threat landscape is changing very quickly and most of the attacks use hyperlinks to initiate the attack and steal credentials, install malware, or exploit vulnerabilities. As discussed earlier, most of these links are sent through email (phishing attack). As illustrated in the following screenshot, there are different variants of the attack. The hacker enters through sending a well-crafted email to an innocent employee, who does not notice anything suspicious about the mail, clicks on the link to an untrusted location, which helps the attacker to establish a connection to the network via compromising the internet service.
With the exploit, they steal passwords and then expand within the network through different methods such as pass the hash:

If you are really not sure of the authenticity of an email and you really want to click the URL, or if you are visiting a website that you are not certain is secure, Microsoft helps by taking a systematic approach to disrupt these attacks by providing us tools such as Application Guard, to stop attackers from establishing a foothold on the local machine and blocking access to the rest of the corporate network.
For our context, keep in mind that Application Guard coordinates with Microsoft Edge to open that site in a temporary and isolated copy of Windows. In this case, even if the attacker's code is successful in attempting to exploit the browser, the attacker finds their code running in a clean environment with no interesting data, no access to any user credentials, and no access to other endpoints on the corporate network. The attack is completely disrupted.
As soon as the user is done, whether or not they are even aware of the attack having taken place, this temporary container is thrown away, and any malware is discarded along with it. There is no way for the attacker to persist on that local machine, and even a compromised browser instance has no foothold to mount further attacks against the company's network. After deletion, a fresh new container is created for future browsing sessions:

To enable application guard, you need a virtualization-enabled PC that runs Windows 10 (minimum 1607), then enable Hyper V (if not already enabled) through Start | Control Panel | Programs | Turn Windows features on or off:

After the restart to Turn Windows features on or off, enable Windows Defender Application Guard through ticking the checkbox:
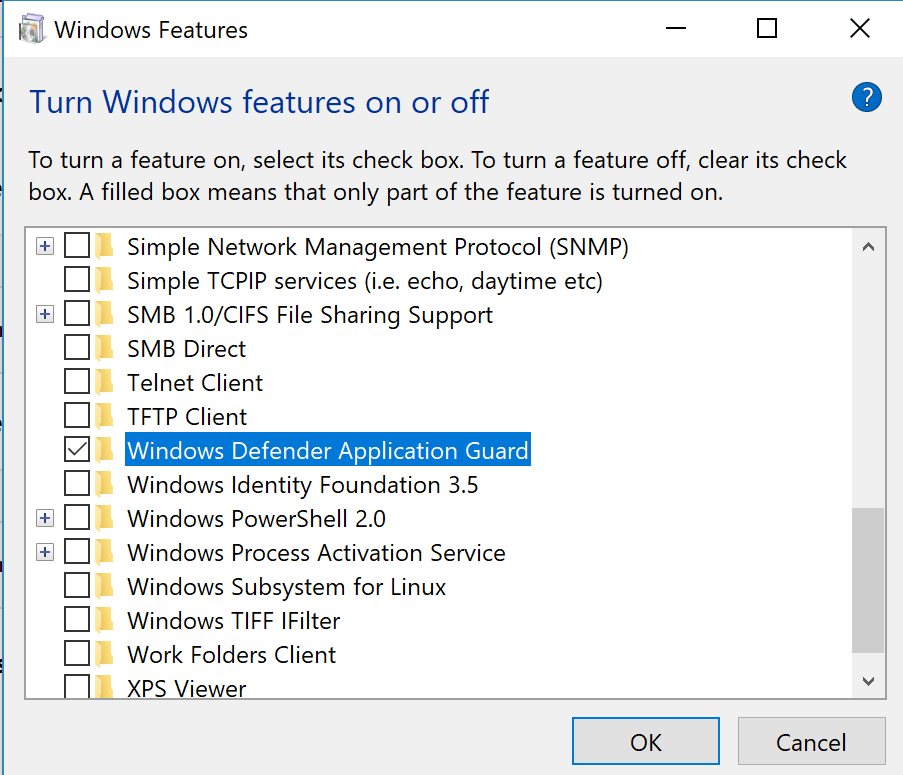
Of course, there are other ways to do this. You can find more information about Application Guard and how you can enable it at https://docs.microsoft.com/en-us/windows/security/threat-protection/device-guard/deploy-device-guard-enable-virtualization-based-security.

