In the previous chapters, Erdal Ozkaya has described the cyber kill chain; that is, a process diagram developed by Lockheed Martin to better understand how threat actors prepare and execute cyber-attacks. The key is to understand how threat actors operate to better build an effective defense strategy. The first phase for many cyber-attacks is the reconnaissance or short recon phase. The term reconnaissance comes originally from the military, and means to identify useful intelligence about the enemy's location, intention, combat plan, and anything else that could be relevant to infiltration, gaining a technical advantage, or preparing for combat against them.
In cyberspace, the recon phase follows the same principles, but it is focused on identifying patterns in user behavior to find the right set of loopholes. In this phase, the threat actor seeks to gain in-depth knowledge of the target. This typically not only includes basic information, such as the location of their headquarters, but far more personal information such as hierarchy diagrams, pictures of employee badges, document templates, building blueprints, financial information, and insights into individual employees. The threat actor then takes the gathered intelligence and builds a graph view of it. This allows the threat actor to identify the weakest link, and allows them to prepare a sophisticated and targeted cyberattack.
Make no mistake, many times the first wave of targeted employees are not the C-level executives, but are more likely to be the employee who recently shared that they are open to a new career opportunity on a professional network, or the trainee who shared how frustrated they are because of the long working hours. These employees are more likely to open a targeted phishing email than the freshly-appointed Chief Technology Officer (CTO). That's why it is important to understand that, while building defense measurements for high-value assets might make sense in some cases, it is critical to have a cyber security framework in place that covers the protection, detection, and reaction to cyber-attacks regardless of whether it's the identity, email, or endpoint of the Chief Executive Officer (CEO) or the sales representative. This is true because threat actors view the gathered intelligence, not by hierarchy but in a graph, and then identify within that the weakest link:
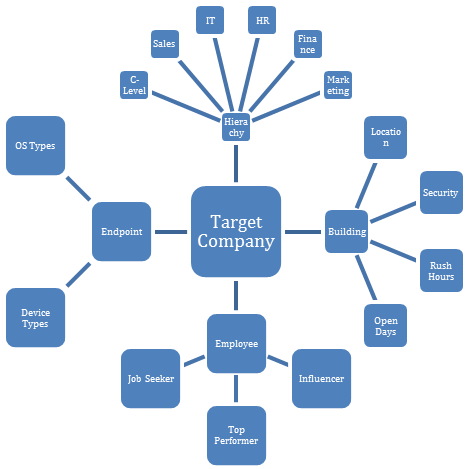
Imagine yourself as a threat actor. On the one hand, you have identified the email address of the Chief Information Security Officer (CISO), and, on the other, the email address of the newly-appointed junior sales representative. Who are you more likely to send a targeted phishing e-mail to? In most cases, it will be the junior sales representative, not because of the actual person but because, many times, organizations provide an extra level of security and awareness training for executives, making it less likely to succeed with a phishing email. Therefore, it is important, as a security professional, to not only assume there will be a breach, but also assume that the personal data of almost all employees inside the organization is floating around on the internet.
