In order to give a clear picture of the different terms related to social engineering attacks, here a taxonomy for the classification of social engineering attacks is presented in the following figure. The rest of this section describes this detailed classification of social engineering attacks:
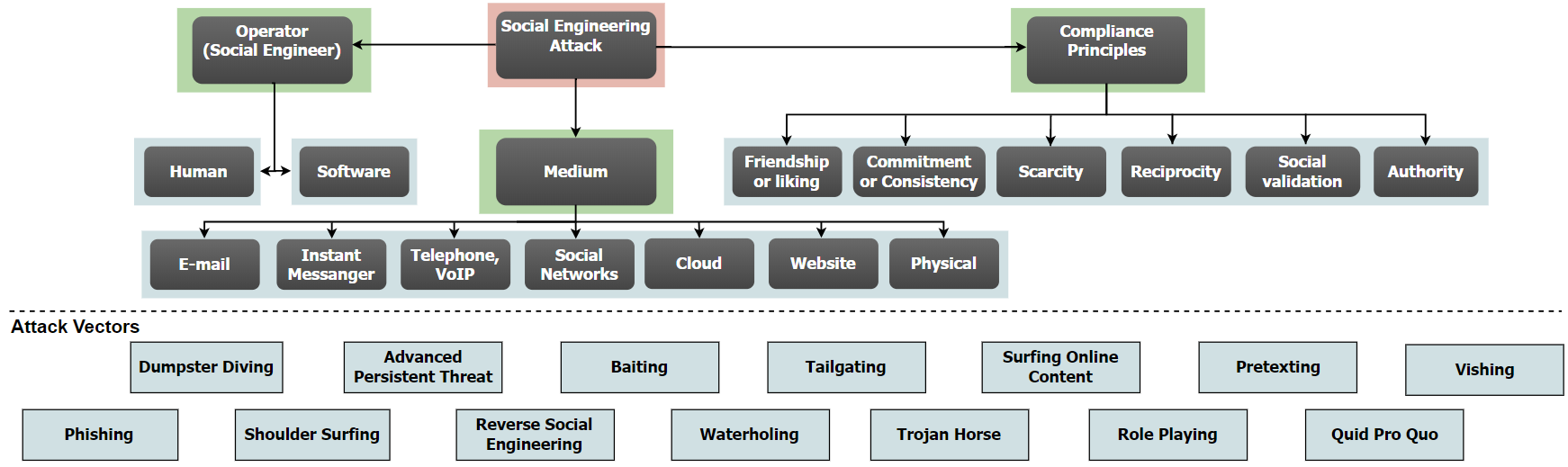
The classification is based on three main categories—medium, operator (social engineer), and compliance principles.
As is shown in the Social engineering attack life cycle figure in the Social engineering attacks life cycle section, the attacks can be performed through the following mediums, refer to point 9 under the References section. :
- Email is the most common medium for phishing and reverse social engineering attacks.
- Instant messaging applications are gaining popularity among social engineers as tools for phishing and reverse social engineering attacks. They can also be used easily for identity theft to exploit a trustworthy relationship.
- Telephone, voice over IP (VoIP) are common attack mediums for social engineers to make their victim deliver sensitive information.
- Social networks offer a variety of opportunities for social engineering attacks. Given their potential for creating fake identities and their complex information-sharing model, they make it easy for attackers to hide their identities and harvest sensitive information.
- Cloud services can be used to gain situational awareness of a collaboration scenario. Attackers may place a file or software in a shared directory to make the victim hand information over.
- Websites are most commonly used to perform waterholing attacks. Furthermore, they can be used in combination with emails to perform phishing attacks (for example, sending an email to a potential customer of a bank that contains a link to a malicious website that looks just like the bank's original website).
Social engineering attacks can be conducted by two types of operators (social engineers)—human or software. Although humans are always behind any kind of attack, due to the lower capacity in conducting the attack compared with the attacks conducted by software, different automated tools are used in social engineering. The professional social engineer has a number of tools at his/her disposal, refer to point 10 under the References section. Some examples of these kinds of tools are the following:
- Computer-based (Maltego, social engineer toolkit (SET))
- Phone (burner phones, caller ID spoofing)
- Physical (cameras, GPS trackers, lock picking, recording)
For examples of compliance principles refer to:
Once the compliance principles, techniques, and medium have been selected, the attack vector can be set up and the social engineer can continue with the actual attacking phase.
Social engineering attacks come in many different forms and can be performed anywhere where human interaction is involved. The following are the most common forms of social engineering attack techniques:
