These methods include the use of technological products for obtaining information about the client. One of these methods is by stalking the target on their social media accounts. Most targets will have active profiles on LinkedIn, Facebook, Twitter, Instagram, or Snapchat. Users on these platforms are so careless with their data that social engineers need not look far in many instances. Even after repeated warnings for people to change their privacy settings, it is more likely than not that the target's account will be visible to the public and thus anyone. Users have put out their entire lives to strangers and anything that can get a like is likely to be posted. Information that was once private is now put indiscriminately on public domains. This makes it even easier for a social engineer to collect the data available about the target. However, in some instances, the attacker might not be so fortunate either because the data given is too little or the account is set as private. This, therefore, requires the social engineer to create a fake account that matches the preferences and likes of the target. With this, a client may request the target to either become friends or follow them. Another common approach has been through the use of a fake account created in the name of someone known to the target. Close friends, relatives, and bosses at work have been used in many social engineering attacks with a high success rate.
The second commonly used technical social engineering method is a search on search engines. Search engines index many sites and some of these store user information collected from many sources and pooled together at a central place. There are special Google queries that can be used to mine information about people contained on websites. These will be discussed in detail in the next chapter about data gathering. An example is the following query:
"David Wilson" intitle:"curriculum vitae" "phone" "address" "email""
This is a very powerful query that can be used to unearth any information about a person called David Wilson. The query will make Google look for any website that has an entry by the name David Wilson and has titles such as curriculum vitae, phone, and address:
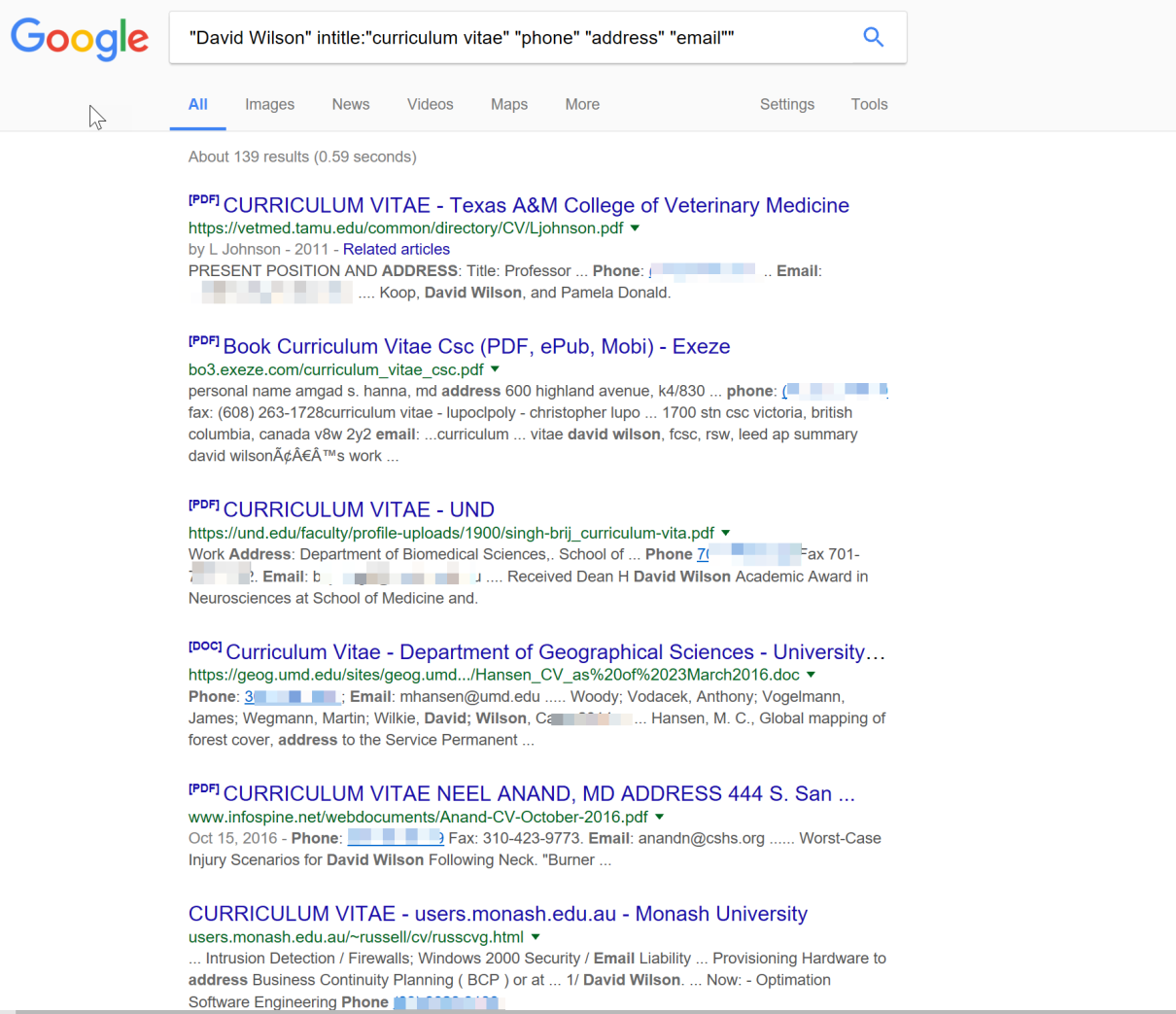
Many job boards that keep the data of job seekers keep the job seekers information in the public domain. Therefore, it will be easy to find a person called David Wilson from where personal details can be retrieved. This query might even bring up the resume of David Wilson if there is a site that has kept information about it:

A site known as Pipl (https://pipl.com) is one of the largest archives of information about a large number of people. For each person it has on its database, the site keeps the person's email address, social media accounts, phone number, and physical address. The site claims to have details of over three billion people:
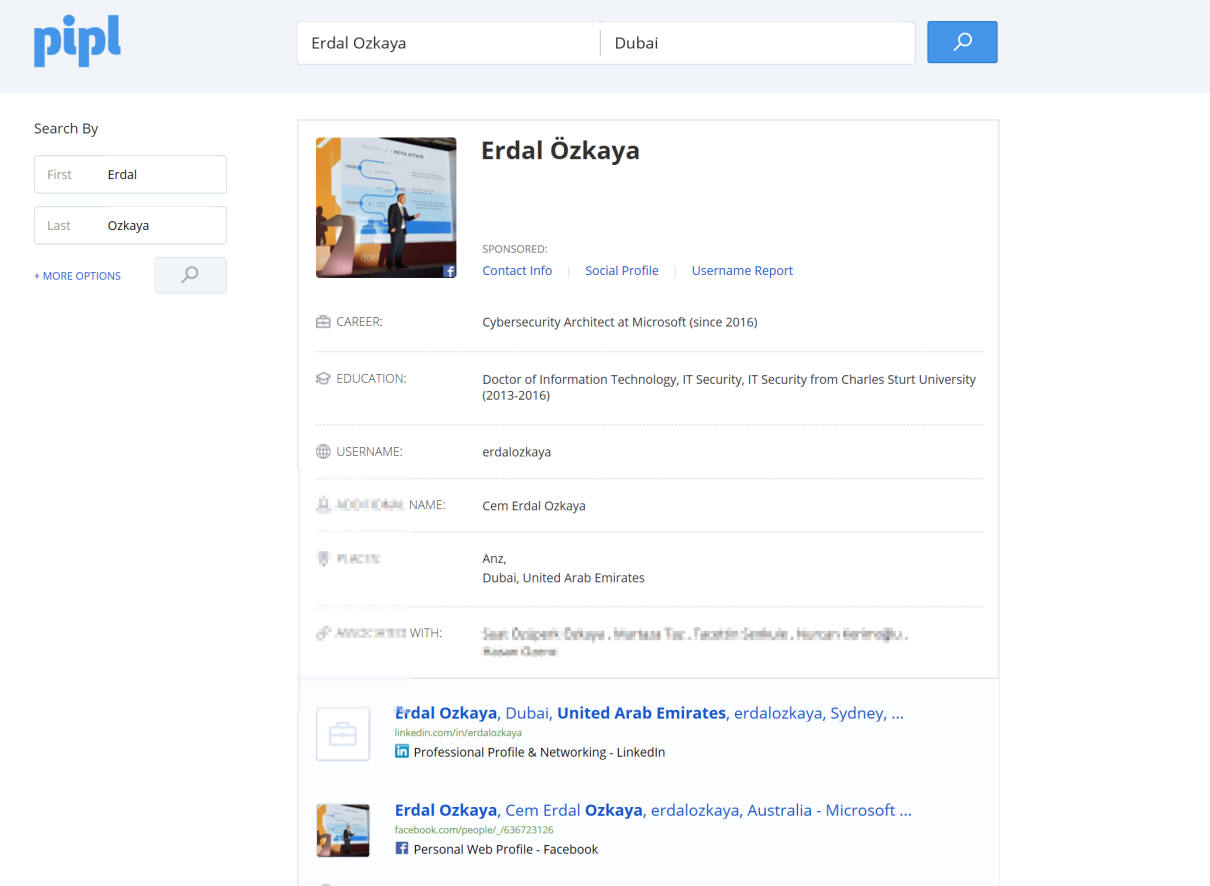
It is fast approaching half the human population on earth. This site is a goldmine for social engineers as they can find out rather personal information about their targets without much hassle. There are many other sites like it dishing out private information about people to anyone that requests such information. These sites have a wide source for these records, which include social platforms, data sold by third parties, data released by hackers, data stolen from other websites, and data in government agency websites. They keep updating their data as often as their sources can. Unfortunately, such sites are not illegal and therefore it is hard for anyone to compel such sites to have their data removed.
Another technical source of information that is still in use by social engineers is the use of telephones. This is commonly targeted at older people since they are easy to fool. The callers always claim to be from reputable companies or government agencies. They use enticing offers or grave threats to get the targets to send them some cash. There are reports of some callers that claim to be the police and threaten to arrest the targets if they do not send some amount of money within a certain period. Other people are also targeted and the greatest asset that social engineers have is some information about the target. Just knowing a target's bank account could be enough incentive to get the client to trust that it is the bank calling. They can use a bank account number to get the target to reveal even more data including social security numbers. When the targets come to the realization that it might not be the bank calling, it is normally too late. The social engineers will have enough information to plot an attack.
Data gathering is indeed tedious, lengthy, and tasking. It is, however, worth it. The amount of information gathered from the targets is vital in the planning of an attack. The best data gathering method is one that does not preempt the motive of the social engineer. Therefore, data gathering is done discreetly. Small chunks of information are pulled bit by bit and pooled together. With time, the social engineer will have more than enough information to profile a target. The social engineer will know more about a target's life than the target's family or spouse. This is the information that will determine the success of an attack. There are very many other data-gathering methods and tools that are used in this process. The ones that have been discussed have also not been discussed in depth. These will, however, be discussed in the following topic about data gathering. The chapter will identify all the methods and tools, describe them, and give examples of the use of each. At the end of the chapter, one will be proficient at collecting data about targets exactly as a social engineer does.
