Malware is just like any other software. It goes through the same stages of development that regular software does. Malware development now uses development models that are no less than what’s employed by software companies around the world. With dedicated development teams and QA process, they’ve got it all.
At the same time, malware is no different from regular software when it comes to targeting its victims: they want to make sure they can run on as many end-user devices as possible without any hiccups. Malware authors always like to make sure their malware can impact a larger mass for a better return on investment. To make sure this happens, they write malware targeting various operating systems: Windows, macOS, Linux, and Android. The target devices for malware have also expanded from desktops and laptops to servers, cellphones, SCADA devices, POS devices, and IoT devices.
But whatever platform the malware is written to target, whatever languages they are developed in, whatever devices they end up running on, the basic components of almost all malware can be segregated into a few major components. In this chapter, we briefly go through these major high-level components that make up malware. We also cover how malware, once developed, is forced out and distributed to its victims.
Malware Components
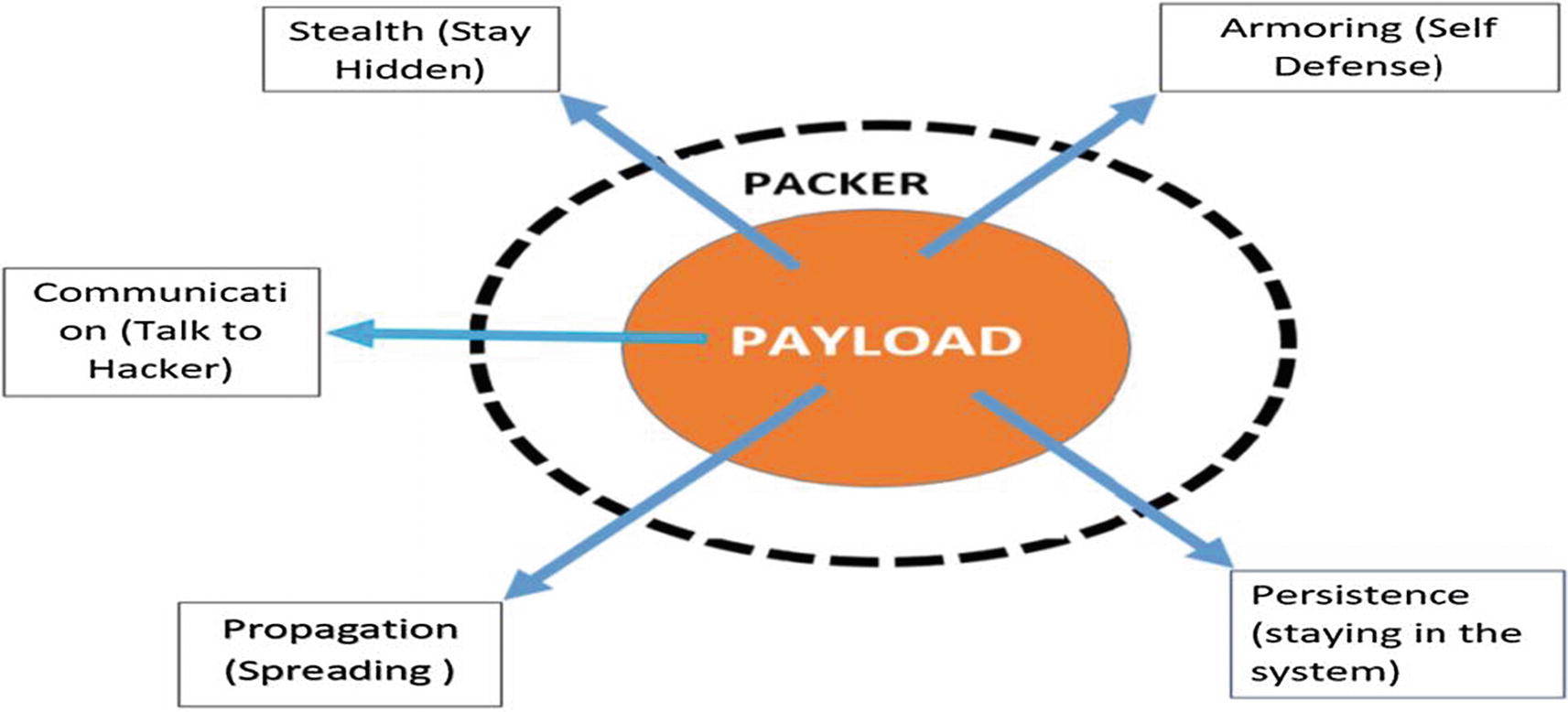
High-level description of the various components that make malware
The components can be divided into payload, packer, persistence, armoring, stealth, communication, and propagation. In the next few sections, we briefly describe each of these components. In the next set of chapters, we thoroughly cover these components and introduce you to both static and dynamic analyses of these malware components using various analysis tools.
Payload
Payload is the most important and mandatory component of malware. A malware infection happens with the aid of multiple binaries, either executable or non-executable, that are used in a sequence or combination to fully achieve the goal of its attacker. Each of these individual binaries in this chain of binaries can be described as a payload. But in truth, the term payload is used for that piece in the chain that holds and runs the functionality that implements the true intent of the attacker.
As a malware analyst, while we inspect malware or malware infection, we get to see all these multiple binaries in this chain. The name given to malware and the classification of the type of malware is based on the main payload and not all the side pieces in the chain.
Password stealer (PWS): Steals passwords from browsers, FTP clients, and the victim’s other login credentials and so forth
Banking malware: Developed to steal banking credentials
Ransomware: Encrypts victim’s sensitive data and resources and extorts ransom from the victim to free these resources back to the victim
Adware: Displays unwanted advertisements to victims
Point of Sale malware: Steals credit card information from systems linked to POS devices
For each of the payloads, we categorized the malware based on the payload. There might have been other smaller payloads as well, but we didn’t consider them while classifying the malware. Some of the smaller payloads are droppers, downloaders, wipers, and so forth. We talk more about identifying payloads and classifying the malware in Chapter 15.
Packer
A packer is an outer layer around the payload that compresses and obfuscates it. A packer can be used by both clean software and malware. The usual goal of a packer is to compress a software; but the indirect effect of compression is obfuscation, because of which static analysis and static signatures from antivirus fail to detect packed malware since the inner payload is no longer visible. So, we can also say that malware use packers to conceal the payload and hence their true intention.
While reverse engineering malware, you need to remove this outer layer to see the actual payload or functionality of the malware. This method of removing the packer outer layer code is called unpacking. Unpacking algorithms are implemented in antivirus software that attempts to unpack packed binaries. But today there are thousands of packers, and hence it is difficult for antivirus vendors to write that many unpackers.
We talk about packers and unpacking in Chapter 7. In Part 5, we talk about various unpacking tricks that you can use.
Persistence
Any malware aims to run more than just once on a victim’s machine. It wants to always run and stay in the system and sustain reboots and multiple logins. The techniques with which malware survives reboot is called persistence.
Banking malware aims to steal banking credentials wants to make sure that it is up and running always so that it can steal the credentials from the browser whenever a user opens the browser and logs in to their banking websites.
RAT malware monitors a victim’s activities and uploads the information to its attacker, can only do so if it is up and running (all the time) when the user logs in and uses the system.
Ransomware may not only want to encrypt existing files on the system, but also new files that are created by the user after reboot.
On Windows, malware mainly persists by tampering the registries most of the time, which contain configuration keys and settings that are related to system boot and startup programs. We cover persistence in Chapter 8.
Communication
Most malware wants to communicate with the attacker. The reason could be anything from uploading stolen data to receiving commands from the attacker. Malware talks to the attacker through command-and-control (C2C/CnC/C2) servers. The CnC communication was simple a decade ago, consisting of IRC chat or simple HTTP communication. But with advancements in network detection products like IDS, IPS, and next-gen firewalls, interception of malware communication became easy, which has led malware to resort to more complex communication mechanisms like using HTTPS, DNS tunneling, domain generation algorithms (DGA), TOR, and so forth. We cover this topic in detail in Chapter 9.
Propagation
Malware wants to spread to as many devices as possible not just to get a higher victim footprint, but also for other reasons like in the case of APTs where the real machine they are targeting is located somewhere else on the network. An example of this malware is Autorun Worms, which used USB flash drives to spread from one machine to another, giving it the ability to jump across air-gapped machines. Another example is the infamous Wannacry malware, which used the Eternal Blue Exploit to propagate through the network and infect other machines.
Another such propagation mechanism is PE file infection, which is used by viruses or file infectors where the virus hijacks the execution flow of another clean PE executable file, by inserting its own code into the file, which results in the virus’s code getting executed each time the host PE file executes, after which it infects more such clean files on the system, thereby spreading itself. If an infected executable is copied from the victim to a healthy machine and executed there, it infects other clean executables in the healthy machine too.
Malware can also propagate over the network misusing various protocols like SMB and shared folders. Attackers and malware are also known to exploit default credentials used by various networking software to spread across machines. Malware is known to spread over the network by exploiting vulnerabilities in networking software, like the way WannaCry malware did. We cover a lot of these topics in Chapter 9.
Armoring
Malware does not want to be detected by anti-malware products, and it does not want malware analysts to analyze it. Armoring is used by malware to protect themselves from both detection and analysis. Anti-debugging, anti-antivirus, VM detection, sandbox detection, and analysis tool detection are among the various armoring techniques employed by malware.
For example, to analyze malware, analysts use VMs which have various analysis tools like Process Hacker, OllyDbg, IDA Pro, Wireshark, ProcMon, and so forth installed on the system. Inside a VM, it is not just the VM that leaves traces on the system that lets a malware figure that it is inside one, but malware also tries to search for the presence of any analysis tools installed in the system. When it does detect that it is inside an analysis environment, the malware might exit or exhibit benign behavior to fool analysts.
It’s not only a malware analyst but also anti-malware products like antiviruses and sandboxes that pose a threat to malware. Antiviruses can be detected by their files, processes, and registry entries on the system. Most sandboxes are run inside VMs. So, sandboxes can be identified by figuring out the presence of the VM and certain sandbox related artifacts from the system memory. Malware can behave differently and benignly in the presence of this security software to avoid detection by them.
To break and dissect such armored malware, security researchers reverse engineer malware using which they can skip and jump across armoring related code used by the malware. Alternatively, using binary instrumentation, one can write tools that can automate the detection of such armoring code and skip such code to get the malware to execute its real code. We cover both topics in Part 5 and Part 6.
Stealth
Malware needs to hide on the system so that the user does not detect its presence in plain sight. It’s equally important for malware to hide from anti-malware software. Other than ransomware, most malware prefers to operate in stealth mode. Stealth is a high priority for banking trojans, RATS, and other malware. Stealth mechanisms can range from simple techniques like altering file properties that make it hidden to more complex techniques like infecting other clean programs on the system, code injection, process hollowing, and rootkits. We cover the various stealth techniques and rootkits in Chapter 10 and Chapter 11.
Distribution Mechanisms
Malware attackers need to make sure that they can’t be traced back while they are distributing their malware.
The distribution mechanism should be effective in delivering malware and infecting the target machine.
In case of targeted campaigns where the infection is intended for a country, or a region, or a corporation, the distribution mechanism must make sure it doesn’t infect other victims apart from the intended target(s).
The distribution mechanism should be able to bypass cybersecurity products, that are both network and host-based.
Most of the distribution mechanisms are heavily dependent on social engineering. Email is one such social engineering delivery mechanism, the oldest and still the most effective one used by attackers with the help of spam and, in other cases, even targeted emails. A lot of malware infections happen because of users clicking the links in malicious emails. Another kind of delivery technique is drive-by download, where the malware infection happens without the victim’s knowledge.
Physical delivery: This kind of delivery mechanism uses USB flash drives and hard drives that are shared across machines to propagate themselves and infect new machines.
Delivery over websites: A malware may be hosted on a website, and the victim is infected when the victim visits such websites. The link to these malicious websites is distributed using emails or by using compromised legitimate websites or even advertisements (malvertising is covered later in this chapter). The malicious website may host malware or exploit kits, which can infect a victim without their knowledge and without needing any kind of interaction from them. We cover exploit kits in detail later in this chapter.
Delivery over email: This is the oldest and probably the most used technique. Malware can be directly sent over email. We can also have a combination of this technique and technique (2), where the emails can contain links to malicious websites. Also, malicious attachments in Microsoft Office documents, PDFs, and scripts can be sent over email, which can function as a trojan downloader and download other malware and secondary payloads.
Let’s now go through some of these well-known delivery techniques that are based on the three categories.
Exploits and Exploit Kits
Programmers often commit mistakes while they code, which manifests as bugs in their programs. Some of the bugs can be serious, though, where an attacker can misuse these bugs to take control of the program and then the system. Such kinds of bugs are called vulnerabilities . If the vulnerable program is hosted on a server, compromising the program can lead to compromise of the server too.

The process of exploiting a vulnerability to take control of the process
These days most of the exploits are responsible for downloading and executing malware.
Any kind of software or program can have a vulnerability and can be exploited. This ranges from web servers like Apache and Nginx to SMTP servers like Postfix. Also, everyday applications that we use in our PCs are known to have vulnerabilities. This includes web browsers like Internet Explorer, Firefox, and Chrome; browser plugins like Adobe Flash and Silverlight; PDF readers like Adobe Acrobat and Foxit; and Microsoft Office tools like Microsoft Word, vulnerabilities have been found in the OS kernel for Windows and Linux as well. In the next few sections, we explain some of the terminologies related to vulnerabilities in the security world.
Common Vulnerabilities and Exposures (CVE)
When a new vulnerability is discovered, it can be reported to certain organizations that provide the vulnerability a common name, also called CVE-ID or CVE names, based on a fixed naming convention, and then add the information to a common database that holds details about all publicly disclosed vulnerabilities. As an exercise, you can visit www.cvedetails.com and search for any known vendor/software that you know of, such as Internet Explorer, and it should show you the list of vulnerabilities disclosed for it. Go through some of the reported vulnerabilities to get a feel of how a vulnerability is described in the CVE database. Do note that the CVE database only holds info on publicly disclosed vulnerabilities.
Patches: Fixing Vulnerabilities
A lot of programs have vulnerabilities, and the good guys need to identify and fix them before the bad guys start exploiting them. Security researchers actively try to discover existing vulnerabilities in software. They do it for many reasons. Some of them because they want to give back to the community and improve the security posture of programs and computers. Others for the lucrative bug bounties in the form of $$$. Some others for fame. When they do find a vulnerability, they have multiple directions they can go from there. Some of them release public posts describing the vulnerability. In other cases, the researcher can privately contact the software vendor to safely disclose the vulnerability to prevent its misuse by attackers.
In either case, the vendor responds by fixing the vulnerability by providing new versions of the affected components in their vulnerable software. These fixes provided by the vendor are called software patches. Software patches usually arrive as software updates to our system. Most of the time, software vendors try to create and release patches for vulnerabilities as soon as they learn of it. But the turnaround time from being informed about a vulnerability to creating and releasing a patch can sometimes take from a few days to a few months. In this period, if details of the vulnerability are leaked to the public, attackers can write exploits targeting the vulnerability and attack and exploit users. Therefore, safe disclosure of a newly discovered vulnerability from security researchers to the vendor is important.
Discovering new vulnerabilities is a hot and lucrative field. Researchers who find new vulnerabilities and report them to the vendor are offered cash bounties for their secure disclosure of the vulnerability. But it’s not just researchers who search for vulnerabilities. Attackers are also known to search for vulnerabilities to use them to attack and exploit other machines. Even researchers are known to sell vulnerabilities and exploits on the market to buyers who are willing to pay the right price for it.
Zero-Day
You learned that when a vulnerability is discovered, and the vendor is informed about it, they usually release software patches via software updates to fix the vulnerability. But again, the vendor can only release patches for vulnerabilities it knows about.
Zero-day vulnerabilities are present in software that is not patched/fixed. A vendor might still know about the vulnerability and not have fixed it, or it might not know about the existence of a vulnerability in its software, but if it is not patched/fixed, it is called zero-day. If an attacker discovers a zero-day vulnerability, it gives him an advantage since they can now attack and exploit users who are using that vulnerable software.
How Attackers (Mis)Use Exploits
Most of the vulnerabilities exist due to a lack of input validation by programs. It means the input provided to the program is not validated in the program. As an example, let’s say a program expects a name as input, which expects a sequence of alphabets, but if the user inputs a number and if the program doesn’t validate that it holds only alphabets, it ends up accepting invalid input leading to unintended consequences.
Various programs take various kinds of inputs in various ways. A web server takes input in the form of HTTP requests that are processed by its backend code, which can be written using various frameworks and languages like Ruby, Django, Python, NodeJS, and so forth. Similarly, an end user like us who browse the Internet accepts input in various programs we use, for example, as an HTML webpage when we browse the Internet using browsers like Internet Explorer, Chrome, and Firefox. If an attacker knows what kind of software is available in a target machine, and knows the various vulnerabilities available in this software, he can craft a special input containing an exploit that can target these vulnerabilities.
Let’s see how an attacker can attack a victim who is running a web server. Before attacking a web server, the attacker finds out if the victim is running a web server and, if so, the name of the web server software. He also tries to figure out the exact version of the web server software. The attacker can obtain this information either from passively probing the server over the network for fingerprint info or using any publicly disclosed documentation or info from the Internet. Knowing the software and version details, the attacker can now try to obtain a list of any known vulnerabilities in this web server software that are not patched yet, after which he can craft and send an exploit to the web server by creating and sending a specially crafted HTTP request to it.
But it can be a bit tricky while attacking a regular desktop user like us. In a server, it has publicly exposed software like web servers that communicate and interact with the general public over the network and hence is easily reachable by attackers. But it’s not the same for regular desktop users. We don’t run any publicly exposed web server software or any other kind of services that others can directly talk to from any location in the world. So, to deal with end users, attackers have come up with a new delivery mechanism called exploit kits using which they can exploit and infect end users like us. We discuss exploit kits in the next section.
Exploit Kit
Servers on the Internet have services and software exposed to the general public, which attackers can directly connect and communicate with. This direct communication lets hackers initiate the attack against servers, sending them exploits, and taking control of the server. But attackers don’t have a direct communication path to the computers of end users since their computers are hidden behind their home network gateways.
To exploit and infect end users, attackers must reverse their strategy to a waiting game . They must place baits and traps on the Internet using malicious servers and wait for unsuspecting users to contact these malicious servers of the attackers, to infect them.
Some of the other problems that attackers might face while placing these traps are that it may not work for many reasons. One of the main reasons being the attacker’s inability to find the accurate version of the software from which traffic is coming from the user. Another problem is that the software from which the user is communicating with the attacker’s trap server might not be vulnerable. To fill all these gaps, attackers developed exploit kits.
Exploit Kit Components
An exploit kit is not a single exploit but is a box of exploits in which various combinations of exploits are placed, targeting vulnerabilities in various software and their versions. There is no fixed software that all end users use to contact the Internet. For example, end users might contact a malicious website over the network using various browsers like Internet Explorer, Chrome, Firefox, Safari, Edge, and so forth. They might use different software versions of these browsers. But the exploit kit has this covered because it holds within itself exploits that are written not just for various software and browsers, but all for multiple versions of this software.
The exploit kit might be located on multiple web servers hosted by the attacker. But the delivery of an exploit from the exploit kit to a victim user doesn’t happen via direct communication from the malicious website hosting the exploit/exploit kit. Instead, it usually happens via an intermediate page called the landing page.
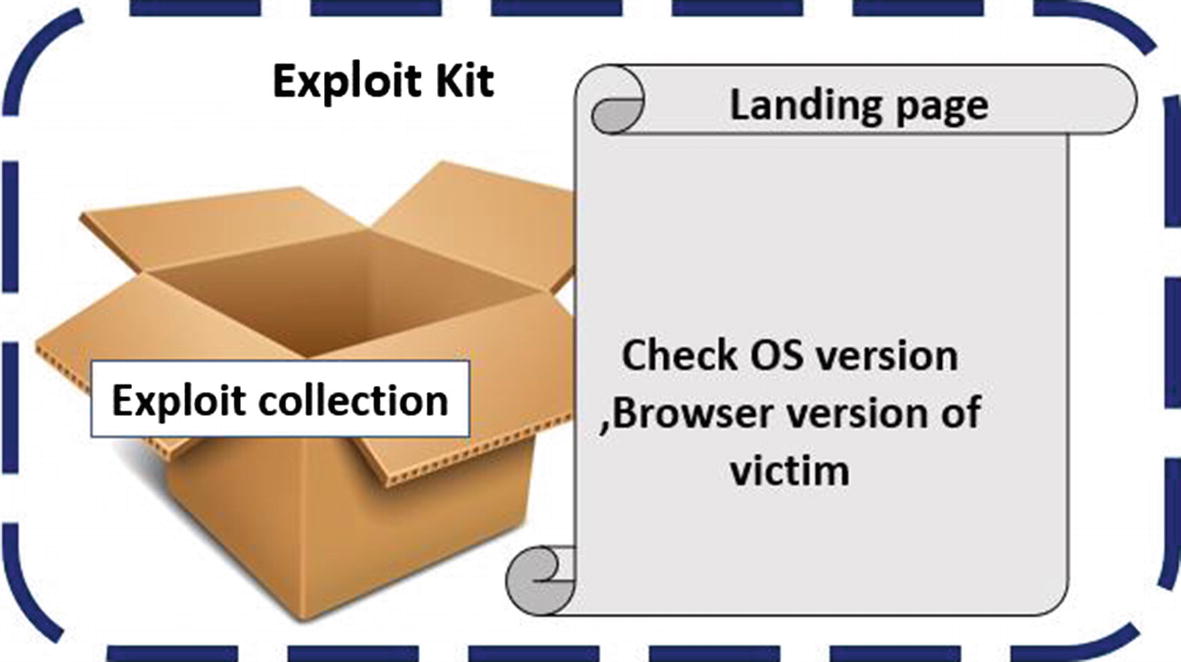
The landing page is the face of an exploit kit acting as a filter for user requests
Exploit Kit Flow
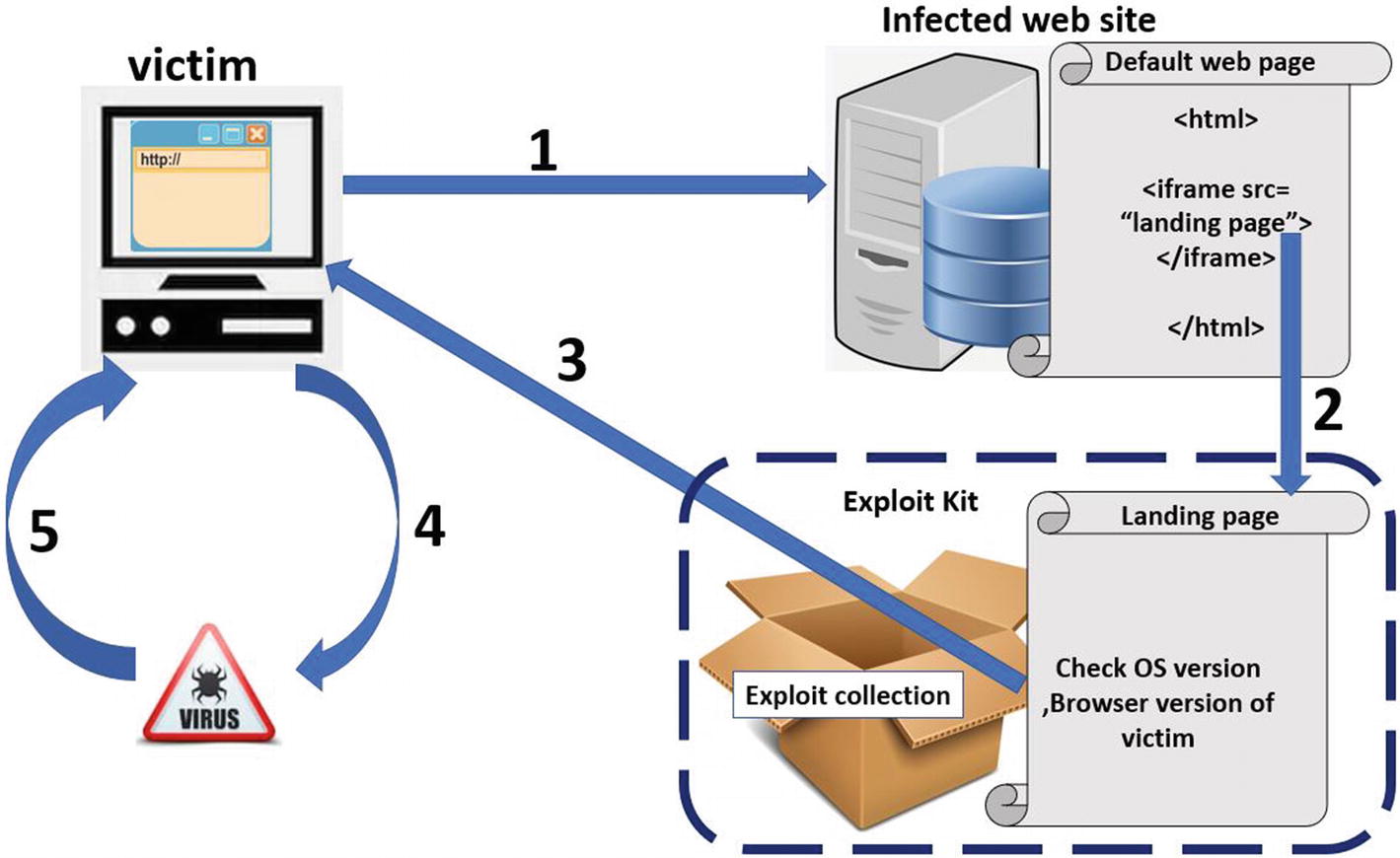
The flow of an exploit kit which finally downloads malware after exploitation
- 1.
A victim visits a malicious website whose server is under the control of an attacker. The malicious site might be a website that belongs to the attacker that contains and returns malicious content to anyone visiting the website. Or the more likely and common scenario is that it is a popular website whose server which might have been hacked and taken over by an attacker, and whose actual clean content has been tampered and modified to now return malicious content.
But how does an attacker hack and take over another popular clean website? Websites are written using many web-based frameworks and programming languages, which have a long history of vulnerabilities. Multiple vulnerabilities have also been discovered in web server software like Apache, Nginx, and IIS as well. Attackers target the vulnerabilities on these web server software by exploiting them and take control of these servers. Also, a lot of web server software is misconfigured where administrators set up the server with default login credentials like admin/admin123, which attackers can brute force or easily guess to login to these web servers and take control of them.
Now that the attacker has control of the web server, they tamper and modify the contents of the website, which was previously serving clean web pages. After tampering by the attacker, the web pages contain malicious content, aimed at attacking and infecting users who visit that website.
One of the common malicious content added to website pages are hidden iframes, which use hyperlinks to point to the landing page of the exploit kit. Such malicious iframe injection into web pages have been discovered in many well-known sites like news sites, entertainment sites, which usually have a huge number of visitors. These hidden iframes, though part of the webpage, are not visible and don’t change the aesthetics or the visual structure of the page, thereby going unnoticed.
- 2.
When end users like us visit the infected website, the hidden iframe which has been added to the returned webpage automatically contact the landing page and load its malicious code. The irony lies in the fact that the victim’s browser visits and loads the content of the landing page without needing the user to click anything on the landing page. Also, the landing page contents are not visible in the browser to the user since it is loaded inside the hidden iframe.
- 3.
The landing page runs its JavaScript code, which figures out various details about the user and the software/browser, which has contacted the website, as explained earlier in this section. After retrieving this information, if it figures that the browser is vulnerable, it picks up a suitable exploit that has been written for the vulnerable browser and returns it to the user.
- 4.
The exploit is delivered to the victim’s vulnerable browser as a part of the returned web page, which, when loaded by the web browser, is processed and exploits a vulnerability in the browser. Upon successful exploitation, the exploit code is executed, and it now has control of the browser. This is illustrated in Figure 6-2, where after successful exploitation, the CPU instruction pointer be reset to execute the exploit code.
- 5.
As a continuation of step 4, the executed exploit code now carries out other tasks, which mainly includes contacting other malicious servers on the Internet hosted by the attacker to download malware onto the victim’s computer and running them.
Exploit Kit as Malware Delivery Mechanism
Now the most important phase from the previous section was in step 5 of the exploitation phase. An exploit on its own is a small piece of code and is largely useless functionality wise. An attacker most often wants to do a lot more damage on a victim’s machine, which isn’t possible by the exploit, which is why the exploit is no more than an initial attack vector and a delivery mechanism only.
Once the exploit manages to run its code, its code contacts another malicious server on the Internet to download an actual malware payload from the attacker, which it then executes, completing the full cycle of infection, thereby fulfilling its duty as a very effective and stealthy malware delivery mechanism.
Exploit Kit Case Study
There were dozens of exploit kits created by various attacker groups. Most of the exploit kits were prevalent between 2016 and 2018. The most popular exploit kits were RIG, Sundown, Blackhole, and Magnitude, and so forth.
www.malware-traffic-analysis.net/ is a great site that tracks exploit kits currently prevalent in the market. Let’s analyze one such exploit kit in action, using Sample-6-1.txt from the samples repo, which tracks the Magnitude exploit kit, downloading Cerber ransomware.

Loading a PCAP file into Fiddler by dragging and dropping it on the Desktop Icon
Fiddler lists the various HTTP packets from the PCAP in a very intuitive manner, combining HTTP requests and responses. Exploit kits target vulnerable browsers and browser plugins, after which it sends an exploit.

HTTP communication shows a successful exploitation and malware download
Spam
An example spam mail trying to phish for information from the user
Invoice
Refunds
Lottery/awards
Mail from colleague/boss/manager
Message from friend/spouse
There are many variants of Spam Mails that aim to gather information and install malware onto the victim machine. Some of these are phishing, whaling, spear phishing, clone phishing, and so forth. We encourage you to search the web and read about these techniques to gain a general understanding of what additional features/info these spam variants add to regular spam emails.
Infected Storage Devices
Infected storage devices are a popular way to spread malware. This technique is especially useful for devices that are air-gapped (not connected to a network). This delivery mechanism brought the infamous Stuxnet malware that wreaked havoc on Iran’s nuclear program.
This mechanism was more popular earlier when the Internet was not the main source of data exchange between users, and when USB drives, CD drives, and hard drives were the most common ways to share data. But how does this method work?
Windows OS provides a mechanism in which when a disk or storage device like a USB stick or CD drive is connected, the OS automatically runs a fixed script called autorun.inf in the attached storage device (if present). This feature was provided for user convenience, like autoplaying a movie on inserting a DVD into a DVD player. Also, another common use of this feature was in software installation CDs that automatically run the installer program when the CD is inserted.
Sample autorun.inf file That Executes a malware.exe File in the Storage Medium
When a disk drive with an autorun.inf file is inserted into a computer, the OS executes the autorun.inf commands, which runs malware.exe, which is present in the same disk drive.
The autorun feature has since been disabled by Microsoft in Windows 7 and also has in older versions of XP and Vista via software updates. But the IT industry, healthcare industry, and various other enterprises and small businesses still run old versions of Windows OS that still have this feature enabled, making them susceptible to this malware delivery mechanism.
Alternatively, malware doesn’t necessarily have to use the autorun feature to spread across air-gapped systems. Malware already running on infected systems can wait for a USB or disk drive to be connected to the system, after which it can copy itself to the disk drive. The USB drive, when shared with other users and used by other users on their systems, might result in these other users accidentally clicking these samples, thereby infecting their systems.
Malvertising
Online advertising is one of the most well-known ways in which businesses can reach consumers. Big ad players like Google make sure that these ads are read and clicked by millions of users. Ads act as revenue for many websites. Ads are a lucrative addition to website content. When a user visits a website which holds ads, the ads are downloaded and displayed to the user.
Malvertising is a delivery mechanism where the very same ads which previously carried benign advertisements are now misused by attackers to carry malicious content. Malicious actors can compromise the vendor who provides these ads so that they can replace and modify genuine ads with their malicious content. There are other cases where the ad provider doesn’t verify if the advertising content provided to them is clean or malicious as well and end up accepting ads from attackers, which reach millions of users.
The malicious content in ads can vary from direct links to websites hosting malware to links pointing at an exploit kit landing page or other compromised websites.
Drive-by Download
A drive-by download is a malware distribution method in which malware is downloaded and run on the victim’s device without the knowledge and consent of the victim. The first technique that comes to our minds when we think about this delivery mechanism is an exploit kit, which downloads and installs malware without the user’s knowledge. But there is another use case as well.
Have you searched the Internet or seen ads for tools that claim to clean your pc and boost the speed of your PC? If you did see them and install these tools, it is very likely that you also installed certain other kinds of malware. A lot of such tools on the Internet are packaged along with some sort of malware, where if you install the primary tool, the malware piggybacking on the same tool installer also install itself, and it does all of it without informing the user of the presence of a secondary software/malware along with the tool. This is primarily used by adware and spyware, which usually piggyback on other tools to install themselves on victim machines without their consent.
Downloaders
A malware infection chain is usually made up of a set of malicious binaries that aim to infect the system. But the malware infection usually starts with a primary malicious program called the downloader. It is a generic piece of malware, which is usually the first piece of malware delivered to the victim. The main task of the downloader is to download the main malware or Payload from the attacker. Downloaders can arrive in various forms, such as .exe PE files, Microsoft Word documents, PDF documents, scripting files, and so forth.
Direct Login via Weak Authentication
A lot of tools come with default credentials, which need to be changed during the initial setup, but a lot of times, IT staff forget this step while deploying such tools.
Some tools don’t have any credentials set up by default and need to be set up during the initial setup, a step that is often forgotten.
Users of these tools use weak passwords along the lines of admin/admin123 and so forth, which are easily guessable by attackers. Attackers are known to brute force various such weak password combinations to break into such servers. For example, a lot of ssh accounts are known to use such weak, guessable default passwords leaving an extremely easy path for attackers to enter the system and infect it with malware.
Some tools don’t have any authentication scheme setup. The authentication method should be set up during installation because it is often forgotten.
With weak or no authentication in place, attackers are constantly on the lookout scouring the Internet for such weak servers into which they can easily login. After logging-in into these servers, the attackers can download malware directly using tools like wget, which are natively available on the system and execute the malware. Attackers also commonly automate the entire previous process using bots and crawlers, thereby speeding up the entire process and constantly looking out for new misconfigured servers on the Internet.
A good read of one such malware infection that was delivered via misconfigured docker service on the web can be found in the blog post “Container Malware: Miners Go Docker Hunting in the Cloud.”
Shared Folders

Windows Explorer shows shared folders of other PCs connected on the network
A folder, once shared, is visible to other users over the network. By default, in newer versions of Windows, you can’t view the shared folders of another remote machine without authenticating yourself to the machine with the credentials of that machine. But there are times when users and even system administrators end up sharing their folders on the network without requiring remote users to authenticate themselves to view these folders, all the while not realizing the consequences this can have.
This takes an even worse turn when users share folders and enable write permissions to them, basically allowing anyone over the network to write files into the shared folder. Malware is known to scan for other PCs on the network by searching for shared folders that have write access. On finding such shared folders, they copy themselves into these shared folders. Alternatively, malware might also try to steal user/admin domain credentials using which it tries to access shared folders on other machines on the networks.
In some cases, the malicious files the malware copy into the shared folders might get executed on the remote machine when a user on the remote machine finds a new file he doesn’t recognize and clicks on it to see what it does. To deceive users on these remote machines into clicking their malicious dropped files, they usually end up sharing malicious Word documents and PDF files, which are more likely to be clicked by the user.
Uses the sc.exe command-line tool that registers a service. You learned this command in the “Malware as Windows Services” section in Chapter 5. The same command can register a service on a remote machine, as shown in Listing 6-2.
sc.exe \<Remote_Machine> create newservice binpath= C:PathToShared_Malware.exe start= auto obj= <username> password= <password>Listing 6-2sc.exe to Register Service on a Remote Computer
We can catch the issue of this command while dynamically analyzing malware by using tools like ProcMon. To figure out if the malware is propagating over the network. It is important to differentiate if the malware is trying to register a service on the local machine or the remote machine. We can figure this out from the parameters of the preceding command, where it references the remote machine using double backslashes \<Remote_Machine>.
You can figure out if the malware issues these APIs by using APIMiner and API logging sandboxes. To differentiate if the API creates a service on the remote or the local machine, we need to inspect the parameters passed to these APIs.
Uses the PsExec tool. We can catch this command while dynamically analyzing the malware using tools like ProcMon.
Summary
Malware is no different from regular software and is developed using the same development techniques employed by various IT vendors around the world. In this chapter, we went through the various components and features that form malware, which gives malware the stealthy and resilient function that it needs. But creating malware is just one part of the job. Malware needs to be delivered to the victim. We also covered the various distribution mechanisms that are used by attackers to deliver and infect victim devices.
