A malware analyst deals with hundreds of files every day. All the files on a system need to be categorized so that an analyst understands the potential damage that one file can do to the system. A malware analyst needs to be aware of the various file formats and how to identify them. In this chapter, you go through various kinds of files and learn how to identify their extensions and formats.
Visualizing a File in Its Native Hex Form

A text file created on Windows using Notepad

Opening the text file using Notepad++ Hex Editor plugin’s Hex View
The middle column in Figure 3-2 displays the file’s bytes in hex, and the corresponding right side displays the same hex value as ASCII printable characters, if it is printable. Hex character code ranges from 0–9 and A–F. If you check any character in the middle column, you see only characters in the hex range listed. Where are the binary 0s and 1s we were talking about earlier? A hex is an alternative representation of bits, like the decimal notation. In Figure 3-2, the hex value for the letter H is 0x48, which in decimal is 72 and in binary translates to 0100 1000. Hex editor shows the binary form in the form of a hex number so that it is more human-readable.
Today, most programmers do not need to deal with files at the hex or binary level. But a malware analyst needs to look deep into a malware sample and hence cannot stay away from understanding files in its native binary form, which is pretty much visualized in hex. As a malware analyst, reverse engineer, or a detection engineer, getting comfortable with hex is a must.
Hash: Unique File Fingerprint
There are millions of files in this world, and we need a way to uniquely identify it first. The name of the file can’t be used as its unique identifier. Two files on two different computers or even on the same computer can have the same name. This is where hashing comes in handy and is used in the malware analysis world to uniquely identify a malware sample.

Illustration of how the hash of a file is generated

Modifying a single byte in a file generates a different unique hash
The hash value of a malware file is what is used in the malware analysis world to identify and refer to it. As you will learn in later chapters, whenever you have a malware file, you generate its hash and then look it up on the Internet for analysis. Alternatively, if you only have the hash of a malware file, you can use it to get more information for further analysis.
The md5, sha1, and Sha256 Hashes Generated for the Same File
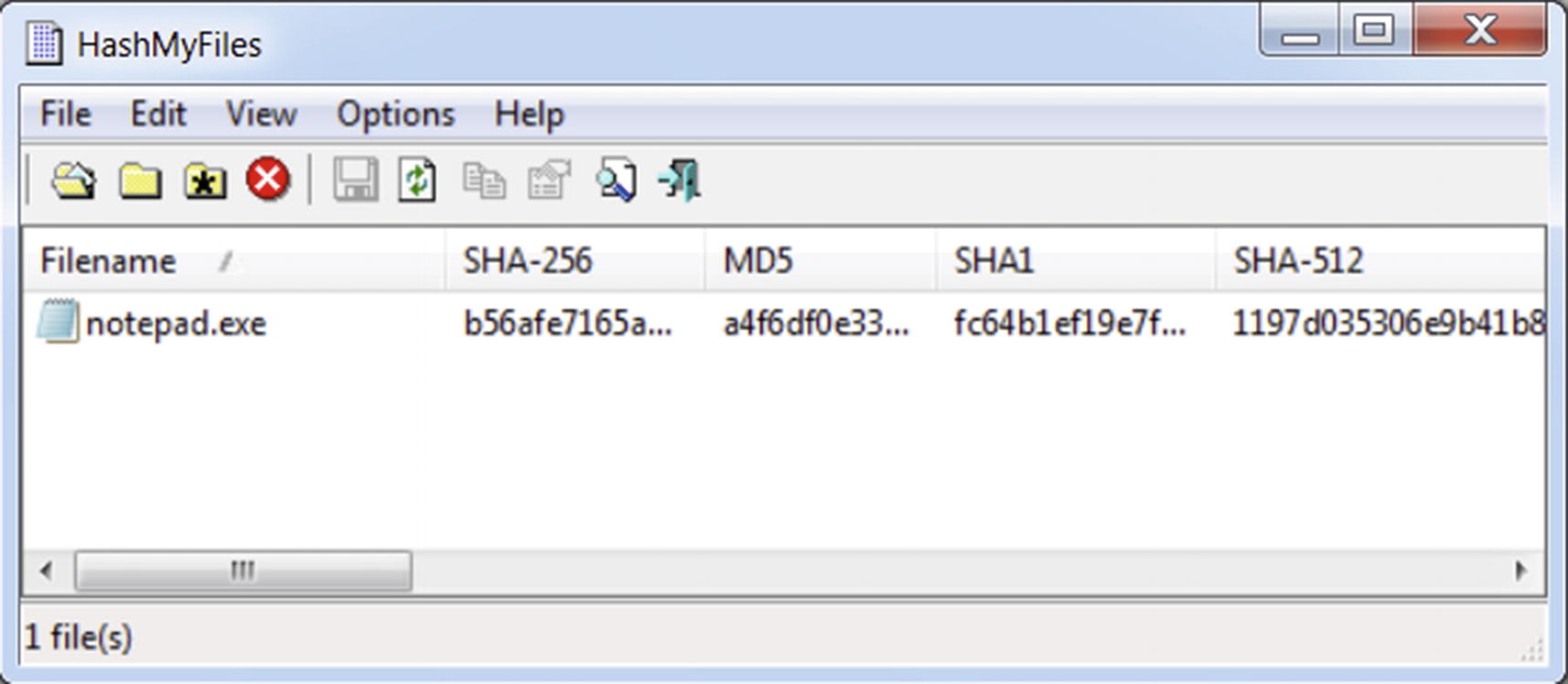
HashMyFiles tool that can generate md5, sha1, sha256 and other hashes for a file
. md5deep, sha1deep and sha256 Deep Command-Line Tools on Windows in Action
Identifying Files
There are two primary ways to identify files: file extensions and file format. In this section we go through each of these file identification techniques and list ways where some of these identification techniques can be used by malicious actors to fool users into running malware.
File Extension

Default file view on Windows with file extensions hidden

File extension visible for files, after disabling Extension Hiding
Some of the Known File Extensions and the File Type They Indicate
Extension | File Type |
|---|---|
Adobe Portable Document Format | |
.exe | Microsoft Executable |
.xslx | Excel Microsoft Office Open XML Format document |
.pptx | PowerPoint Microsoft Office Open XML Format document |
.docx | Word Microsoft Office Open XML Format document |
.zip | ZIP compressed archive |
.dll | Dynamic Link Library |
.7z | 7-Zip compressed file |
.dat | Data file |
.xml | XML file |
.jar | Java archive file |
.bat | Windows batch file |
.msi | Windows installer package |
File Association: How an OS Uses File Extensions
File association is a method by which you can associate a file type or extension to be opened by a certain application. Usually, a file extension is the file property that creates an association with an application on the system.

Windows unable to open a .pptx PowerPoint file without a file association for this particular extension
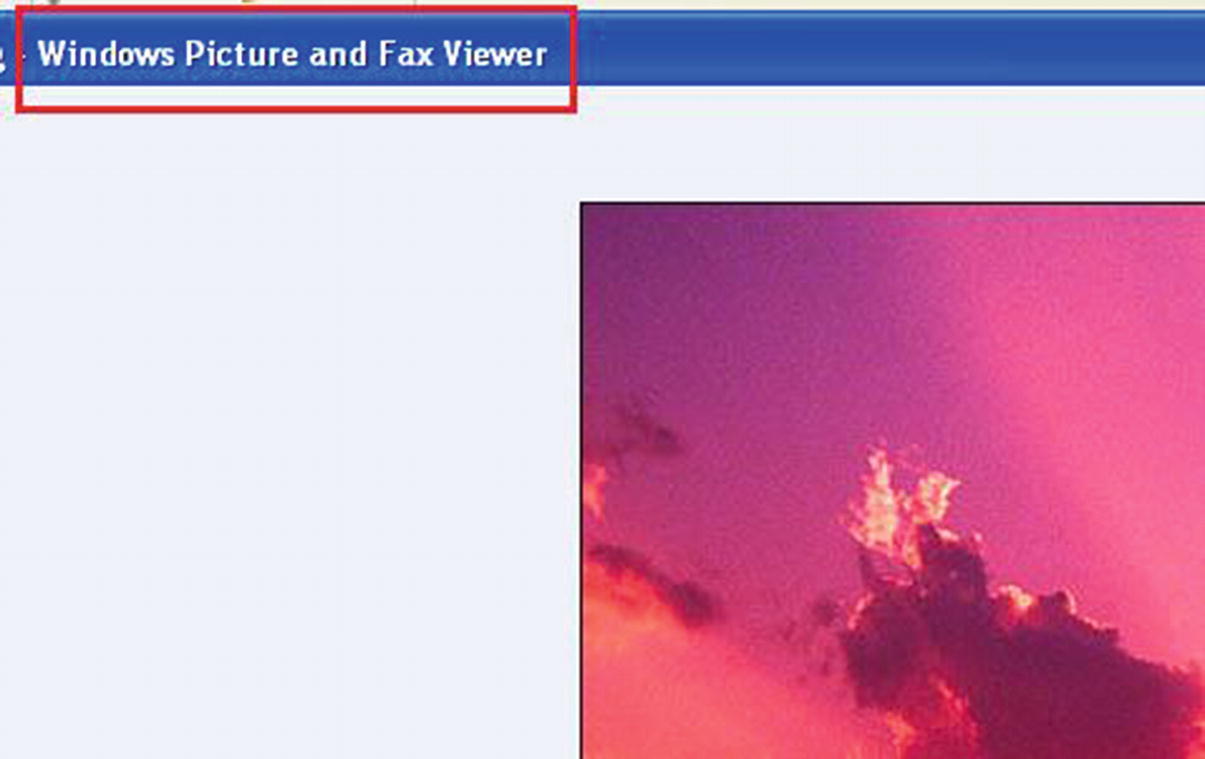
Windows displays an image file, whose extension .jpeg has a file association with an image viewer application on the system
Why Disable Extension Hiding?
When you analyze a piece of malware, viewing the extension gives you a quick overview of the type of file you are dealing with. Also, when the malware sample is run, it can create multiple files on the system, and the ability to view their extension helps you immediately figure out the type of files created by the malware on the system. Malware authors also use extension faking and thumbnail faking techniques to deceive users into clicking the malware (as explained in the next sections). Knowing the correct extension of a file can help thwart some of these malicious techniques.
Extension Faking

Malware executable file using extension faking by being craftily named by attackers with a fake .pdf extension suffix
Thumbnail Faking

Malware executable file with a fake .pdf thumbnail
Well-Known File Extensions
Popular file Extensions and the Corresponding Default Program Associated with It
Extension | Program |
|---|---|
.png, .jpeg, .jpg | Windows Photo Viewer |
Adobe Acrobat Reader | |
.exe | Windows loader |
.docx, .doc, .pptx, .xlsx | Microsoft Office tools |
.mp3, .avi, .mpeg | VLC Media Player |
File Extensions: Can We Rely on One Alone?
Can we rely on the extension of a file to decide the type of a file? The answer is no. For example, changing the file extension of a file with a .pptx extension to a .jpeg doesn’t change the type of the file from a Microsoft PowerPoint file to a JPEG image file. The file is still a PowerPoint file but with a wrong extension, with the contents of the file unchanged. You can still force Microsoft PowerPoint to manually force load this file despite the wrong extension.
As malware analysts, this issue is more amplified. Often, malware files are dropped on the system without readable names and an extension. Also, malware is known to fool users by dropping files in the system with a fake file extension to masquerade the real type of the file. In the next section, we introduce file formats, the foolproof way to identify the file type.
File Format: The Real File Extension

Magic bytes for executable file types. MZ(4d 5a in hex)
These magic bytes are not located randomly in the file. They are part of what is known as the file header . Every file has a structure or format that defines how data should be stored in the file. The structure of the file is usually defined by headers, which holds meta information on the data stored in the file. Parsing the header and the magic bytes is lets you identify the format or type of the file.
A file—audio, video, executable, PowerPoint, Excel, PDF document—each has a file structure of its own to store its data. This file structure is called a file format. Further parsing of the headers can help determine a file’s characteristics. For example, for Windows executable files, apart from the MZ magic bytes, parsing the header contents further past these magic bytes reveals other characteristics of the file. For example, the headers hold information on the file (e.g., whether it is a DLL, or an executable, or a sys file, whether it is 32- or 64-bit, etc.). You can determine the actual file extension of a file by determining its file format.
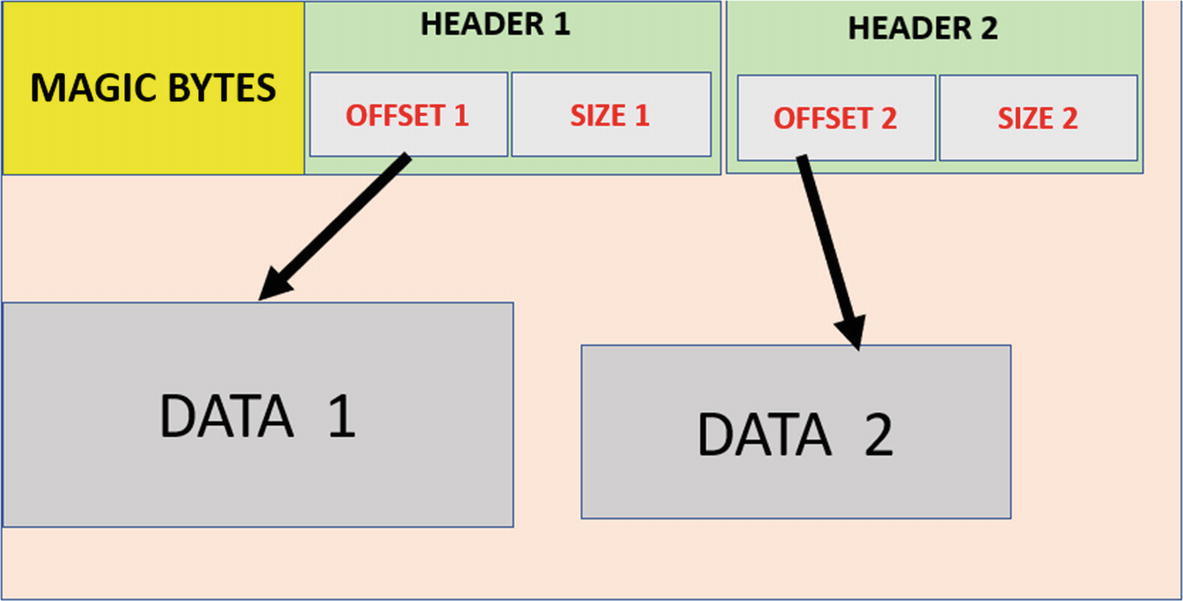
High-level overview of the structure and headers of a file
Popular Executable File Formats and Their Magic Bytes
OS | File Type/Format | Magic Bytes HEX | Magic Bytes ASCII |
|---|---|---|---|
Windows | Windows Executable | 4D 5A | MZ |
Linux | Linux Executable | 7F 45 4C 46 | .ELF |
Mach-O | Mach-O Executable | FE ED FA CE | …. |
Popular Nonexecutable File Formats and Their Magic Bytes
File Format/Type | File Extension | Magic Bytes HEX | Magic Bytes ASCII |
|---|---|---|---|
PDF Document | 25 50 44 46 | ||
Adobe Flash | .swf | 46 57 53 | FWS |
Flash Video | .flv | 46 4C 56 | FLV |
Video AVI files | .avi | 52 49 46 46 | RIFF |
Zip compressed files | .zip | 50 4B | PK |
Rar compressed files | .rar | 52 61 72 21 | rar! |
Microsoft document | .doc | D0 CF |
Identifying File Formats
While there are many tools to identify file formats, there are two prominent ones available. One is the file command-line tool in Linux, and the other is the TriD present as the trid command-line tool available on Windows, Linux, and macOS, or TriDNet if you prefer GUI. Both command-line tools take a path to the file as the argument from the command line and give out the verdict on the format of the file.
TriD and TriDNet
. trid.exe Command Line Tool Identifying the Format of a File
In Listing 3-3, trid.exe lists the potential file formats. For notepad.exe located on our analysis box, trid.exe reports with a 49.1% accuracy that it is an executable file compiled using Microsoft Visual C++. The greater the probability, the more likely it is that file format.
File Command-Line Tool
File Command Line Tool on Linux, Identifying the Format of an Executable File
Manual Identification of File Formats
In the previous section, we introduced magic bytes, file headers, and their structures, and using them to identify files manually. But with the presence of tools like TriD, it seems unnecessary to remember these file format details, and manually open a file using a hex editor to identify its format.

Using magic bytes to quickly and manually identifying the presence of files in other data like packet payloads
Summary
In this chapter, you learned about file extensions and file formats, as well as the structure, magic bytes, and headers that form the identity of a file format. Using freely available command-line tools, you can quickly identify the type of a malware file and set up the right analysis environment for the file based on its type. Knowledge of magic bytes helps you manually identify the presence of files in various data sources, such as packet payloads and packed files.

