Group Policy applies only to users and computers. Group Policy settings are divided into two categories: Computer Configuration, which contains settings that apply to computers, and User Configuration, which contains settings that apply to user accounts. Each category can be divided further into three major classes of settings, each of which contains several subclasses of settings:
Software Settings. For automated deployment of new software and software upgrades. Also used for uninstalling software.
Windows Settings. For managing key Windows settings for both computers and users, including scripts and security. For users, you can also manage Remote Installation Services, Folder Redirection, and Microsoft Internet Explorer maintenance.
Administrative Templates. For managing registry settings that configure the operating system, Windows components, and applications. Administrative templates are implemented for specific operating system versions.
The Group Policy management tools provide access to these three top-level classes of settings and make use of a number of extensions that provide the functionality necessary to configure Group Policy settings. As we discussed previously, there are two types of Group Policy: Local Group Policy and Active Directory–based Group Policy. Local Group Policy applies to the local machine only, and there is only one local GPO per local machine. Active Directory–based Group Policy, on the other hand, can be implemented separately for sites, domains, and OUs. When you want to work with Group Policy, you can do so at the local machine level using the Local Security Policy tool or within Active Directory using the GPMC. The sections that follow examine the key techniques you’ll use to access GPOs with these tools and to manage policy settings.
Note
You manage the Group Policy settings for domain controllers using the Domain Controller Security Policy tool (as long as the domain controllers are part of the Domain Controllers OU). For more information on managing Group Policy for domain controllers and the Domain Controller Security Policy tool, see the section in Chapter 1 titled "Working with Linked GPOs and Default Policy."
To work with Local Group Policy, you must use an administrator account. In a domain, you can use an account that is a member of the Enterprise Admins, Domain Admins, or the Administrators domain local group. In a workgroup, you must use an account that is a member of the local Administrators group.
You can access Local Group Policy in several ways. The fastest way is to type the following command at the command prompt:
gpedit.msc /gpcomputer:"%computername%"This command starts the Group Policy Object Editor in an MMC and tells the Group Policy Object Editor to target the local computer. Here, %ComputerName% is an environment variable that sets the name of the local computer and must be enclosed in double quotation marks as shown. You can also access Local Group Policy in the Group Policy Object Editor snap-in by completing the following steps:
Click Start, Run. In the Run dialog box, type mmc in the Open field, and then click OK.
Choose Add/Remove Snap-In from the File menu in the main window. In the Add/Remove Snap-In dialog box, click Add.
In the Add Standalone Snap-In dialog box, click Group Policy Object Editor, and then choose Add. This starts the Group Policy Wizard.
The Select Group Policy Object page is displayed with the Local Computer selected as the Group Policy Object target. Click Finish.
In the Add Standalone Snap-In dialog box, click Close. Then, in the Add/Remove Snap-In dialog box, click OK.
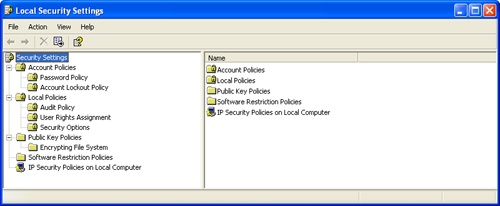
If you want to work only with security settings in Local Group Policy, you can use the Local Security Policy console, shown in Figure 2-3. Click Start, Programs or All Programs, Administrative Tools, and then select Local Security Policy.
In Group Policy Object Editor and Local Security Policy, you can configure security settings that apply to users and the local computer itself. Any policy changes you make are applied to that computer the next time Group Policy is refreshed. The settings you can manage locally depend on whether the computer is a member of a domain or a workgroup, and they include the following:
Account policies for passwords, account lockout, and Kerberos
Local policies for auditing, user rights assignment, and security options
Event logging options for configuring log size, access, and retention options for the application, system, and security logs
Security restriction settings for groups, system services, registry keys, and the file system
Security settings for wireless networking, public keys, and Internet Protocol Security (IPSec)
Software restrictions that specify applications that aren’t allowed to run on the computer
You configure Local Group Policy in the same way that you configure Active Directory–based group policy. To apply a policy, you enable it and then configure any additional or optional values as necessary. An enabled policy setting is turned on and active. If don’t want a policy to apply, you must disable it. A disabled policy setting is turned off and inactive. The enforcement or blocking of inheritance can change this behavior, as detailed in the section titled "Managing Group Policy Inheritance" in Chapter 3.
Often you’ll want to access Local Group Policy on a remote machine. For example, if you are logged on to EdsPC, you might want to see how Group Policy is configured locally on JohnsPC. To access Local Group Policy on another computer, you use the Group Policy Object Editor snap-in.
One way to do this is to type the following command at the command prompt:
gpedit.msc /gpcomputer:"RemoteComputer"where RemoteComputer is the host name or fully qualified DNS name of the remote computer. The remote computer name must be enclosed in double quotation marks, such as:
gpedit.msc /gpcomputer:"corpsvr04"or
gpedit.msc /gpcomputer:"corpsvr04.adatum.com"You can also access Local Group Policy on a remote computer by completing the following steps:
Click Start, Run. In the Run dialog box, type mmc in the Open field, and then click OK.
Choose Add/Remove Snap-In from the File menu in the main window. In the Add/Remove Snap-In dialog box, click Add.
In the Add Standalone Snap-In dialog box, click Group Policy Object Editor, and then choose Add. This starts the Group Policy Wizard.
The Select Group Policy Object page is displayed. Click Browse.
In the Browse For A Group Policy Object dialog box, click the Computers tab, select Another Computer, and then click Browse again.
In the Select Computer dialog box, type the name of the computer whose local group policy you want to access, and click Check Names. When you have the right computer, click OK twice and then click Finish.
In the Add Standalone Snap-In dialog box, click Close. Then, in the Add/Remove Snap-In dialog box, click OK.
Repeat steps 2 through 7 as necessary to add other local computers whose policy you want to manage remotely. When you are finished, click File, Save As, and then use the Save As dialog box to save your custom MMC.
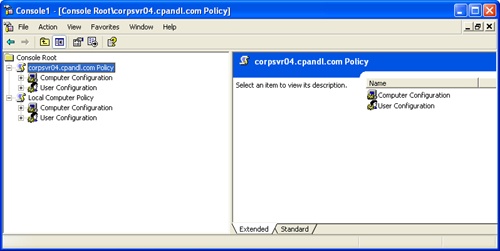
As Figure 2-4 shows, when you work with Local Group Policy through the Group Policy Object Editor snap-in, the nodes of the console root reflect the computers to which you are connected. In this example, the MMC is connected to a remote computer, CORPSVR04, and the local computer.
The best way to manage Active Directory–based Group Policy is with the GPMC, which you must download and install. You can use the GPMC to manage policy settings in accordance with your administrative privileges. The account you use must be a member of the Enterprise Admins or Domain Admins group or must have been delegated permissions to work with specific aspects of Group Policy. When you work with the Enterprise Admins and Domain Admins groups, keep the following in mind:
Members of Enterprise Admins can manage policy settings for the specific forest of which they are a member. For example, if the user account WilliamS is a member of the Enterprise Admins group in the cpandl.com forest, WilliamS can manage the policy settings for any child domain in the cpandl.com domain as well as the parent domain (cpandl.com). This means he can manage the policy settings for tech.cpandl.com, cs.cpandl.com, and cpandl.com.
Members of Domain Admins can manage policy settings for the specific domain of which they are a member. For example, if the user account WilliamS is a member of the Domain Admins group in the tech.cpandl.com domain, WilliamS can manage the policy settings for the tech.cpandl.com domain. He cannot manage policy settings for cs.cpandl.com or cpandl.com. He can manage the policy settings for other domains only if he has Domain Admins privileges in those domains (or Enterprise Admins privileges for the forest).
When you work with delegated administrative permissions, keep in mind that the account has only the specific permissions that were delegated. Delegated permissions for Group Policy include permission to manage Group Policy links, generate RSoP for the purposes of logging, and generate RSoP for planning purposes. The sections that follow discuss how to install and use the GPMC. You’ll learn techniques for delegating administration later in the chapter in the section titled "Delegating Privileges for Group Policy Management."
The GPMC provides an integrated interface for working with policy settings. You can install this console on computers running Windows Server 2003 or Windows XP Professional Service Pack 1 with QFE 326469 or later (if the Microsoft .NET Framework is also installed). Because the .NET Framework in turn requires Internet Explorer version 5.01 or later, the minimum required components for working with GPMC are as follows:
Microsoft Internet Explorer 5.01 or later. Internet Explorer 6.0 SP1 or later is recommended. Computers running Windows XP Professional SP1 or Windows Server 2003 have Internet Explorer 6.0 or later installed already.
.NET Framework. Computers running Windows XP Professional do not have the .NET Framework installed by default. Computers running Windows Server 2003 have the .NET Framework installed by default.
GPMC with SP1 or later. Computers running Windows XP Professional or Windows Server 2003 do not have the GPMC installed by default. The GPMC is available as a download only (as of this writing).
Note
Although you can use the GPMC to manage Group Policy on Windows Server 2003 and Windows 2000, you cannot install the GPMC on computers running Windows 2000 or earlier. Only Windows XP Professional and Windows Server 2003 are compatible with the extensions used by this console.
The key steps for downloading and installing the .NET Framework and the GPMC are as follows:
Download the .NET Framework 1.1 or later from Microsoft at www.microsoft.com/downloads/. The installer file is named Dotnetfx.exe. Download Dotnetfx.exe and then double-click it to start the installation process.
Because the GPMC installation process updates the MMC, you must close any console-based tools that are running before you install the GPMC. If you don’t do this, you’ll see a warning when you try to run the installer telling you that the GPMC cannot be installed until you close the consoles that are open.
Download the GPMC with SP1 or later from the Microsoft Download Center at www.microsoft.com/downloads/. The installation package is Gpmc.msi. Double-click this file to start the installation process.
Caution
Before installing the GPMC, you should think carefully about how you will manage Active Directory–based Group Policy. Installing the GPMC changes the way a computer works with Group Policy, and afterward you can manage Active Directory–based Group Policy only via the GPMC. This is, of course, a per-computer issue, and you have the option of using the existing Group Policy tools or installing and using the GPMC on other computers.
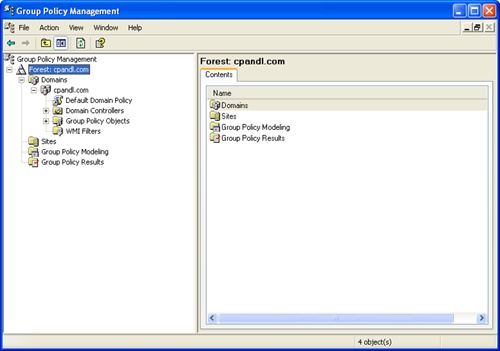
You can run the GPMC from the Administrative Tools menu. Click Start, Programs or All Programs, Administrative Tools, and then Group Policy Management Console. As shown in Figure 2-5, the left pane of the GPMC has two top-level nodes by default: Group Policy Management (the console root) and Forest (a node representing the forest to which you are currently connected, which is named after the forest root domain for that forest). When you expand the Forest node, you see the following nodes:
Domains. Provides access to the policy settings for domains in the forest being administered. You are connected to your logon domain by default; you can add connections to other domains. If you expand a domain, you can access Default Domain Policy, the Domain Controllers OU (and the related Default Domain Controllers Policy), and GPOs defined in the domain.
Sites. Provides access to the policy settings for sites in the related forest. Sites are hidden by default.
Group Policy Modeling. Provides access to the Group Policy Modeling Wizard, which helps you plan policy deployment and simulate settings for testing purposes. Any saved policy models are also available.
Group Policy Results. Provides access to the Group Policy Results Wizard. For each domain to which you are connected, all the related GPOs and OUs are available to work with in one location.
Note
GPOs found in domain, site, and OU containers in the GPMC are actually GPO links and not the GPOs themselves. The actual GPOs are found in the Group Policy Objects container of the selected domain. It is also helpful to note that the icons for GPO links have a small arrow at the bottom left, similar to shortcut icons.
The GPMC is designed to work with multiple forests, domains, and sites. When you start the GPMC for the first time, you are connected to your logon domain and forest. You can connect to additional forests by completing the following steps:
Start the GPMC by clicking Start, Programs or All Programs, Administrative Tools, and then Group Policy Management Console. Or type gpmc.msc at a command prompt.
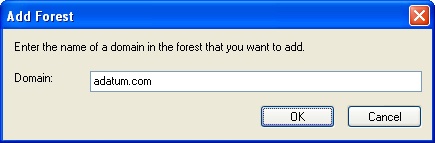
Right-click the Group Policy Management node in the console tree, and then select Add Forest.
In the Add Forest dialog box (shown in Figure 2-6), type the name of a domain in the forest to which you want to connect, and then click OK. As long as there is an external trust to the domain, you can establish the connection and obtain forest information—even if you don’t have a forest trust with the entire forest.
From now on, when you start Group Policy Management Console, the additional forest should be listed.
The GPMC doesn’t show the available sites by default. If you want to work with the sites in a particular forest, follow these steps:
Start the GPMC by clicking Start, Programs or All Programs, Administrative Tools, and then Group Policy Management Console. Or type gpmc.msc at a command prompt.
Expand the entry for the forest you want to work with, right-click the related Sites node, and then select Show Sites.
In the Show Sites dialog box (shown in Figure 2-7), select the check boxes for the sites you want to work with and clear the check boxes for the sites you don’t want to work with. Click OK.
From now on, when you start the GPMC, the additional site or sites should be listed.
In the GPMC, you can view the domains to which you are connected on a per-forest basis. You are connected to your logon domain and forest by default. To work with other domains in a particular forest, follow these steps:
Start the GPMC by clicking Start, Programs or All Programs, Administrative Tools, and then Group Policy Management Console. Or type gpmc.msc at a command prompt.
Expand the entry for the forest you want to work with, and then expand the related Domains node by double-clicking it.
If the domain you want to work with isn’t listed, right-click the Domains node in the designated forest, and then select Show Domains. Then in the Show Domains dialog box, select the check boxes for the domains you want to work with and clear the check boxes for the domains you don’t want to work with. Click OK. From now on, when you start the GPMC, the additional domain or domains should be listed.
When you start the GPMC, the console connects to Active Directory running on the domain controller that is acting as the PDC emulator for your logon domain and obtains a list of all GPOs and OUs in that domain. It does this using LDAP to access the directory store and the Server Message Block (SMB) protocol to access the Sysvol. If the PDC emulator isn’t available for some reason, such as when the server is down or otherwise offline, the GPMC displays a prompt so you can choose to work with policy settings on the domain controller to which you are currently connected or on any available domain controller. If you want to force the GPMC to work with a domain controller other than PDC, you can configure this manually as well. This process is referred to as setting the domain controller focus.
You can choose the domain controller to work with on a per-domain basis by completing the following steps:
Start the GPMC by clicking Start, Programs or All Programs, Administrative Tools, and then Group Policy Management Console. Or type gpmc.msc at a command prompt.
Expand the entry for the forest you want to work with, and then expand the related Domains node by double-clicking it.
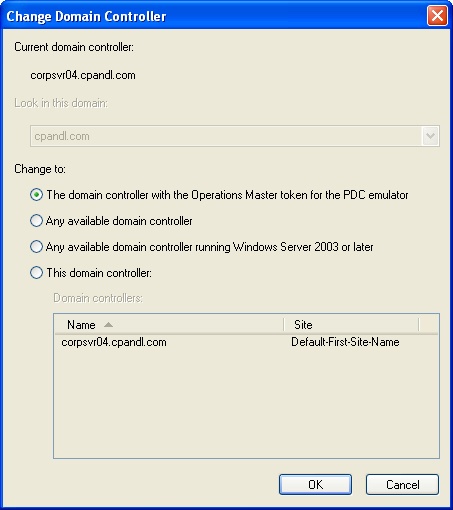
Right-click the domain for which you want to set the domain controller focus, and then select Change Domain Controller to open the Change Domain Controller dialog box shown in Figure 2-8.
The domain controller to which you are currently connected is listed under Current Domain Controller. Use the following Change To options to set the domain controller focus, and then click OK.
The Domain Controller With The Operations Master Token For The PDC Emulator. Choose this option if you aren’t connected to the PDC Emulator for some reason and want to try to establish a connection with this server at this time. For example, if the PDC Emulator was offline for maintenance and is now online, you might want to try to reconnect with it.
Any Available Domain Controller. Choose this option to connect to any available domain controller running Windows 2000 or later. Use this option if you don’t need to work with a domain controller running a specific version of the Windows server operating system.
Any Available Domain Controller Running Windows Server 2003 Or Later. Choose this option if you need to work with a domain controller that is running Windows Server 2003 or later.
This Domain Controller. Choose this option and then make a selection in the Domain Controllers panel if you want to work with a specific domain controller. The site where each domain controller resides is listed as well so that you can work with a domain controller in a particular site if necessary.