Administrative template files describe where registry-based policy settings are stored in the registry. Administrative template files, typically referred to as .adm files, do not affect the actual policy processing by the administrative templates client-side extension (CSE). The .adm files affect only the display of the policy settings in the Group Policy Object Editor snap-in. If the .adm file is removed from a Group Policy object (GPO), the settings corresponding to the .adm file will not appear in the Group Policy Object Editor.
The .adm files are Unicode text files that enable a user interface to allow you to modify registry-based policy settings using the Group Policy Object Editor. After a setting that is established using the .adm files is configured within the Group Policy Object Editor, the setting information is stored in the Registry.pol file located in the Group Policy Template (GPT) for the GPO. The actual policy settings are stored in the Registry.pol file, so the .adm file can be removed from the GPO, but the setting remains in the Registry.pol file and continues to apply to the appropriate target computer or user.
More than 1300 administrative template settings are available, and administrators can add hundreds more custom settings.
Every Windows 2000, Windows XP, and Windows Server 2003 computer comes with some default .adm files. These files are used to create the default interface under the Administrative Templates portions of a GPO. The standard .adm files are listed in Table 14-1.
Table 14-1. Standard .adm Files
.adm Template | Features |
|---|---|
Common.adm | Policy settings for the user interface common to Windows NT 4.0 and Windows 9x. Designed to be used with System Policy Editor (Poledit.exe). |
Conf.adm | Policy settings for configuring Microsoft NetMeeting®. Conf.adm is loaded by default in Windows 2000 Server, Windows XP, and Windows Server 2003. (It is not available on Windows XP 64-Bit Edition and the 64-bit versions of the Windows Server 2003 family.) |
Inetcorp.adm | Policy settings for dial-up, language, and control over Temporary Internet Files settings. |
Inetres.adm | Policy settings for configuring Microsoft Internet Explorer. Inetres .adm is loaded by default in Windows 2000 Server, Windows XP, and Windows Server 2003. |
Policy settings for additional Internet properties: autocomplete, display settings, and some advanced settings. | |
System.adm | Policy settings for configuring the operating system. System.adm is loaded by default in Windows Server 2000, Windows XP, and Windows Server 2003. |
Windows.adm | Policy settings for the user interface options specific to Windows 9x. Designed to be used with System Policy Editor (Poledit.exe). |
Winnt.adm | Policy settings for the user interface options specific to Windows NT 4.0. Designed to be used with System Policy Editor (Poledit.exe). |
Wmplayer.adm | Policy settings for configuring Microsoft Windows Media® Player. Wmplayer.adm is loaded by default in Windows XP and Windows Server 2003. It is not available on Windows XP 64-Bit Edition and the 64-bit versions of the Windows Server 2003 family. |
Wuau.adm | Policy settings for configuring Windows Update. Wuau.adm is loaded by default in Windows 2000 Service Pack 3 (SP3), Windows XP Service Pack 1 (SP1), and Windows Server 2003. |
The .adm files that ship with Windows Server 2003, Windows XP Professional, and Windows 2000 Server are located in the %windir%inf folder.
Additional .adm files are available for security settings, Internet Explorer, Microsoft Office, and more. Some applications also come with their own .adm files to help centralize administration and customization of the application. Table 14-2 lists the current Office 2003 and Internet Explorer .adm files that you can obtain from the Office Administration Kit and the Windows Server 2003 Resource Kit.
Table 14-2. Office 2003 and Internet Explorer .adm Files
Office Template | Features |
|---|---|
Aer_1033.adm | Microsoft Office 2003 Application Error Reporting client configuration. |
Access11.adm | Microsoft Access 2003 settings. |
Dw20.adm | Old Office Application Reporting configuration file, replaced with Aer_1033.adm. |
Excel11.adm | Microsoft Excel 2003 settings. |
Fp11.adm | Microsoft FrontPage® 2003 settings. |
Gal11.adm | Microsoft Clip Organizer settings. |
Inf11.adm | Microsoft InfoPath™ 2003 settings. |
Instlr11.adm | Microsoft Windows Installer settings. |
Office11.adm | Common Office 2003 settings. |
Onent11.adm | Microsoft OneNote® 2003 settings. |
Microsoft Outlook® 2003 settings. | |
Ppt11.adm | Microsoft PowerPoint® 2003 settings. |
Pub11.adm | Microsoft Publisher 2003 settings. |
Word11.adm | Microsoft Word 2003 settings. |
Internet Explorer Template | Features |
Aaxa.adm | Data Binding settings. |
Chat.adm | Microsoft Chat settings. |
Inetesc.adm | Microsoft Internet Explorer Enhanced Security Configuration settings. |
Oe.adm | Microsoft Outlook Express Identity Manager settings. Use this to prevent users from changing or configuring identities. |
Sp1shell.adm | Active Desktop settings. |
Subs.adm | Offline Pages settings. |
Wmp.adm | Windows Media Player, Radio Toolbar, and Network Settings customizations. |
Acquiring an .adm file is only the first step in the process of updating the registry on a target computer or user account. You must then properly insert it into the GPO structure. You do this by importing the .adm file into the GPO that will target the computer or user accounts. The settings that are established in the .adm file will show up when the GPO is edited in the Group Policy Object Editor, allowing the policy to be configured. Several default .adm files are imported into every standard GPO, however, which creates the default administrative template section under both Computer Configuration and User Configuration.
Every new GPO has default Administrative Template sections. These sections are created by three or more .adm files, depending on the operating system you are working with. The following is a list of the default .adm files associated with each operating system:
Windows 2000: Conf.adm, Inetres.adm, System.adm. (Wuau.adm is also installed on computers running Windows 2000 SP3 or later.)
Windows XP Professional: Conf.adm, Inetres.adm, System.adm, Wmplayer.adm. (Wuau.adm is also installed on computers running Windows XP Professional SP1 or later.)
Windows Server 2003: Conf.adm, Inetres.adm, System.adm, Wmplayer.adm, Wuau.adm.
Each successive version of an operating system has more features that need to be controlled. Windows XP includes an .adm file to control Windows Media Player. Windows Server 2003 added a new .adm file for controlling the Windows Update and Software Update Service (SUS) features. From version to version, the standard .adm files have changed slightly.
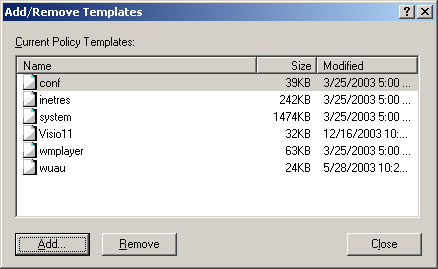
Before you add or remove any .adm files, you can view a list of the default .adm files used with all new GPOs created on a Windows Server 2003 computer Figure 14-1.
If you want to use a particular .adm file to configure some policy settings in a GPO, you must import it into the GPO. The following tips will help the import process go smoothly:
Make sure that the syntax of the .adm file is correct. If it is incorrect, you will receive an error message during the import process indicating that an error was recognized within the .adm file.
A single .adm file can contain both computer and user registry–based settings. The Group Policy Object Editor handles the separation of the two sections when it displays the GPO with the new .adm template inserted.
You can store the .adm file anywhere you want before you import it into the GPO. During the import procedure, you can browse for the file on the local computer or on the network.
After you import an .adm file into a GPO, it is available to be configured in that GPO only. If you want the .adm file settings to be available for a different GPOs, you must import the .adm file into each GPO.
The importing of the .adm file makes a copy of the file in the GPO structure stored in the SYSVOL of the domain controllers. The .adm file is copied into the Adm subfolder under the correct GPO folder represented by the GPO GUID.
Let’s look at an example in which you need to add the Visio11.adm template to a GPO named OFFICE11. The Visio11.adm template is currently located on the desktop of the computer from which you are editing the GPO. To add the template, complete these steps after opening the OFFICE11 GPO in the Group Policy Object Editor:
Right-click the Administrative Templates node under the Computer Configuration section of the GPO and then choose Add/Remove Templates.
In the Add/Remove Templates dialog box, click Add.
In the Policy Templates dialog box, select Desktop in the left pane.
Select the Visio11.adm file in the list. Click Open. You will see the Add/Remove Templates dialog box with the Visio11.adm file listed, as shown in Figure 14-2.
Click Close.
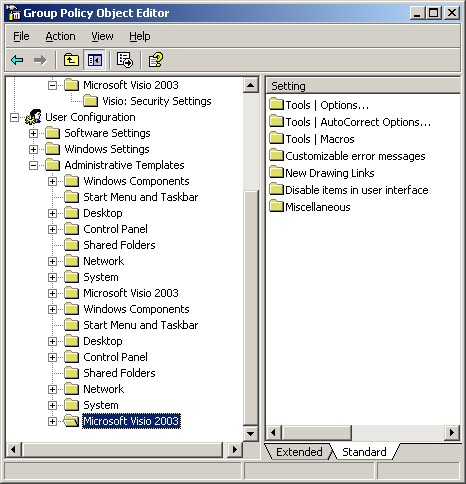
After the .adm file has been imported to the GPO, you can see the Microsoft Visio node and policy settings in the GPO, as shown in Figure 14-3.
Sometimes you might need to remove an .adm file from a GPO. This removes any settings from the Group Policy Object Editor that were created by the .adm file.
Note
If a policy was configured using the settings in the .adm file before the .adm file was removed from the GPO, the policy setting will still be active in the GPO. The policy settings are stored not in the .adm file but in the Registry.pol file. You should modify all settings made using the .adm files as needed before you remove the .adm files from the GPO. For more information about the Registry.pol file, see Chapter 13.
Much like our example of adding an .adm file to a GPO, we will now walk through an example of removing an .adm file. To remove the Visio11.adm file from the OFFICE11 GPO, complete these steps:
Right-click the Administrative Templates node under the Computer Configuration section of the GPO and then choose Add/Remove Templates.
In the Add/Remove Templates dialog box, select the Visio11.adm template in the list of templates and then click Remove. The template is removed from the list.
Click Close.
Over time you will make changes to the custom .adm files that you have implemented within your GPOs. Built-in controls are available that help update new versions of the.adm files. To make this process easier, it is best to have a dedicated workstation for creating and modifying GPOs.
The default behavior of controlling updated .adm files ensures that the latest version of the files are located in the GPT for the GPO. There are two aspects to how .adm files are updated and referenced. First, the .adm file timestamp is referenced. The timestamp of the local .adm file in the %windir%Inf folder is compared to the .adm file in the GPT. If the local .adm file is newer than the GPT version, the local .adm file is copied to the GPT, replacing the current .adm file in the GPT. Second, the Group Policy Object Editor uses the .adm file from the GPT to create the interface within the Administrative Templates nodes within the GPO.
Two GPO settings control this behavior:
Turn Off Automatic Updates Of ADM Files
Always Use Local ADM Files For The Group Policy Editor
This GPO setting can be found at the following location: User ConfigurationAdministrative TemplatesSystemGroup Policy. This policy controls whether the timestamps of the two .adm files are compared and the latest one placed in the GPT. By default, the timestamp is compared and the newer .adm file is placed in the GPT.
When this policy is set to Enabled, the .adm file timestamps are not checked for newer versions, so the GPT is not updated. When this policy is set to Disabled, the .adm files are checked, and if the .adm file from the local computer performing the administration has a newer timestamp, the .adm file stored in the GPT of the GPO is updated.
This GPO setting can be found at the following location: Computer ConfigurationAdministrative TemplatesSystemGroup Policy. This policy controls which .adm file is used to create the interface of the GPO when edited. By default, the .adm file that is stored in the GPT is used.
When this policy is set to Enabled, the .adm files from the local computer are used. The results can be undesirable if the local .adm files are updated without your knowledge.
When this policy is set to Disabled, the .adm files from the GPT of the GPO are used. This creates a safer environment for version control and ensures that all policies can be viewed consistently from any computer.
Here are some tips for working with .adm files.
If the saved GPO contains registry settings for which there is no corresponding .adm file, these settings will not appear in the Group Policy Object Editor. They will still be active, however, and will be applied to users or computers targeted by the GPO.
Because of the importance of timestamps to .adm file management, you should not edit the standard .adm files. If a new policy setting is required, create a custom .adm file.
The GPMC controls the .adm files in a much different manner when it creates HTLM reports, uses Group Policy Modeling, and generates Group Policy Results.
Windows XP Professional does not support the Always Use Local ADM Files For Group Policy Editor policy setting. Therefore, if your GPO administrative computer is a Windows XP Professional computer, you must use the .adm files stored in the GPT.
Each operating system or service pack release includes a superset of the .adm files provided by earlier releases, including policy settings specific to earlier versions of the operating system. For example, the .adm files provided with Windows Server 2003 include all policy settings for all earlier versions of Windows, including settings relevant only to Windows 2000 or Windows XP Professional. This means that merely viewing a GPO from a computer with the new release of an operating system or service pack effectively upgrades the .adm files for that GPO. Because later releases are a superset of previous .adm files, this typically does not create problems (as long as the .adm files being used have not been edited).
In some situations, an operating system or service pack release includes a subset of the .adm files that were provided with earlier releases, potentially resulting in policy settings no longer being visible to administrators when they use Group Policy Object Editor. However, the policy settings remain active in the GPO. Any active (either Enabled or Disabled) policy settings are not visible in Group Policy Object Editor. Because the settings are not visible, an administrator cannot easily view or edit them. To work around this issue, you must become familiar with the .adm files included with each operating system or service pack release before using Group Policy Object Editor on that operating system. You must also keep in mind that the act of viewing a GPO is enough to update the .adm files in the GPT when the timestamp comparison determines that an update is appropriate.
To plan for such potential issues in your environment, it is recommended that you do one of the following:
Define a standard operating system/service pack for all viewing and editing of GPOs, making sure that the .adm files being used include the policy settings for all platforms in your enterprise.
Use the Turn Off Automatic Updates Of ADM policy setting for all Group Policy administrators to make sure that .adm files are not overwritten in the SYSVOL by any Group Policy Object Editor session, and make sure that you are using the latest .adm files from Microsoft.
Policies are registry-based settings that can be fully managed by administrators and Group Policy. They are also referred to as true policies. In contrast, registry-based settings that are configured by users or are set as a default state by the operating system at installation are referred to as preferences.
True policies are stored under approved registry keys. These keys are not accessible by users, so they are protected from being changed or disabled. The four approved registry keys are shown in Table 14-3.
Table 14-3. Approved Registry Key Locations for Group Policy Settings
Computer-Based Policy Settings | User-Based Policy Settings |
|---|---|
HKLMSoftwarePolicies | HKCUSoftwarePolicies |
HKLMSoftwareMicrosoftWindowsCurrentVersionPolicies | HKCUSoftwareMicrosoftWindowsCurrentVersionPolicies |
Preferences are registry-based settings that are located in registry keys other than the approved registry keys listed in Table 14-3. Users can typically change their preferences at any time. For example, users can decide to set their wallpaper to a different bitmap. Most users are familiar with setting preferences through the operating system or application user interface.
You can create custom .adm files that set registry values outside of the approved registry keys. When you do create these preferences, you only ensure that a given registry key or value is set in a particular way. These preferences are not secured as true policies are; users can access these settings and modify them. Another issue with preferences is that the settings persist in the registry. The only way to alter preferences is to configure them using the .adm file or to manually update the registry.
In contrast, true policy settings have access control list (ACL) restrictions to prevent users from changing them, and the policy values are removed when the GPO that set them goes out of scope (when the GPO is unlinked, disabled, or deleted). For this reason, true policies are considered to be policy settings that can be fully managed. By default, the Group Policy Object Editor shows only true policy settings that can be fully managed. To view preferences in the Group Policy Object Editor, you click the Administrative Templates node, click View, click Filtering, and then clear Only Show Policy Settings That Can Be Fully Managed.
Note
To learn more about controlling policies and preferences using the Group Policy Object Editor, see Chapter 3.
True policy settings take priority over preferences, but they do not overwrite or modify the registry keys used by the preferences. If a policy setting is deployed that conflicts with a preference, the policy setting takes precedence over the preference setting. If a conflicting policy setting is removed, the original user preference setting remains intact and configures the computer.