Inheritance ensures that every computer and user object in a domain, no matter which container it is stored in, is affected by Group Policy. Most policies have three configuration options: Not Configured, Enabled, or Disabled. Not Configured is the default state for most policy settings. If a policy is enabled, the policy is enforced and is applied to all users and computers that are subject to the policy either directly or through inheritance. If a policy is disabled, the policy is not enforced and is not applied to users and computers that are subject to the policy either directly or through inheritance.
You can change the way inheritance works in four key ways. You can:
Change link order and precedence
Override inheritance (as long as there is no enforcement)
Block inheritance (to prevent inheritance completely)
Enforce inheritance (to supersede and prevent overriding or blocking)
The sections that follow cover managing Group Policy inheritance using these techniques.
The order of inheritance for Group Policy goes from the site level to the domain level and then to each nested OU level. When multiple policy objects are linked to a particular level, the link order determines the order in which policy settings are applied. Linked policy objects are always applied in link ranking order. Lower-ranking policy objects are processed first, and then higher-ranking policy objects are processed.
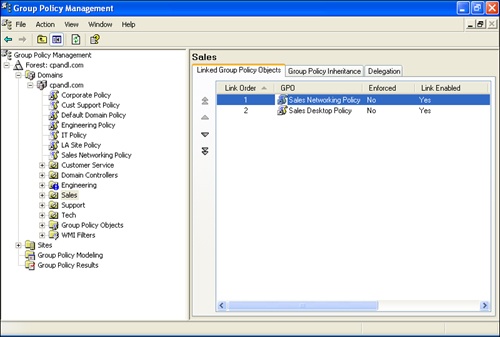
To see how this works, consider Figure 3-4. These policies will be processed from the lowest link order to the highest. The Sales Desktop Policy (with link order 2) will be processed before the Sales Networking Policy (with link order 1).
What effect does this have on policy settings? Because Sales Networking Policy settings are processed after Sales Desktop Policy settings, Sales Networking Policy settings have precedence and take priority. You can confirm this by clicking the Group Policy Inheritance tab (Figure 3-5).
The precedence order shows exactly how policy objects are being processed for a site, domain, or OU. As with link order, lower-ranking policy objects are processed before higher-ranking policy objects. Here the LA Site Policy (with precedence 7) will be processed first, and then Cust Support Policy (with precedence 6), and so on. Default Domain Policy is processed last, so any policy settings configured in this policy object are final and will override those of other policy objects (unless inheritance blocking or enforcing is used).
When multiple policy objects are linked at a specific level, you can easily change the link order (and thus the precedence order) of policy objects linked at that level. To do so, complete these steps:
In the GPMC, select the container for the site, domain, or OU with which you want to work.
In the right pane, the Linked Group Policy Objects tab should be selected by default. Select the policy object with which you want to work by clicking it.
Click the Move Link Up or Move Link Down buttons as appropriate to change the link order of the selected policy object.
When you are done changing the link order, confirm that policy objects are being processed in the expected order by checking the precedence order on the Group Policy Inheritance tab.
As you know, Group Policy settings are inherited from top-level containers by lower-level containers. If multiple policy objects modify the same settings, the order in which the policy objects are applied determines which policy settings take effect. Essentially, the order of inheritance goes from the site level to the domain level to the OU level. This means Group Policy settings for a site are passed down to domains, and the settings for a domain are passed down to OUs.
You can override policy inheritance in two key ways:
Disable an enabled (and inherited) policy. When a policy is enabled in a higher-level policy object, you can override inheritance by disabling the policy in a lower-level policy object. You thus override the policy that is enabled in the higher-level container. For example, if the user policy Prohibit Use Of Internet Connection Sharing On Your DNS Domain is enabled for a site, users in the site should not be able to use Internet Connection Sharing. However, if domain policy specifically disables this user policy, users in the domain can use Internet Connection Sharing. On the other hand, if the domain policy is set to Not Configured, that setting will not be modified and will be inherited as normal from the higher-level container.
Enable a disabled (and inherited) policy. When a policy is disabled in a higher-level policy object, you can override inheritance by enabling the policy in a lower-level policy object. By enabling the policy in a lower-level policy object, you override the policy that is disabled in the higher-level container. For example, if the user policy Allow Shared Folders To Be Published is disabled for a domain, users in the domain should not be able to publish shared folders in Active Directory® directory service. However, if the Support Team OU policy specifically enables this user policy, users in the Support Team OU can publish shared folders in Active Directory. Again, if the OU policy is set to Not Configured instead, the policy setting will not be modified and will be inherited as normal from the higher-level container.
Sometimes you will want to block inheritance so that no policy settings from higher-level containers are applied to users and computers in a particular container. When inheritance is blocked, only configured policy settings from policy objects linked at that level are applied. This means all GPOs from all high-level containers are blocked (as long as there is no policy enforcement).
Domain administrators can use inheritance blocking to block inherited policy settings from the site level. OU administrators can use inheritance blocking to block inherited policy settings from both the domain and the site level. Here are some examples of inheritance blocking in action:
Because you want a domain to be autonomous, you don’t want a domain to inherit any site policies. You configure the domain to block inheritance from higher-level containers. Because inheritance is blocked, only the configured policy settings from policy objects linked to the domain are applied. Blocking inheritance of site policy doesn’t affect inheritance of the domain policy objects by OUs, but it does mean that OUs in that domain will not inherit site policies either.
Because you want an OU to be autonomous, you don’t want an OU to inherit any site or domain policies. You configure the OU to block inheritance from higher-level containers. Because inheritance is blocked, only the configured policy settings from policy objects linked to the OU are applied. If the OU contains other OUs, inheritance blocking won’t affect inheritance of policy objects linked to this OU, but the child OUs will not inherit site or domain policies.
Note
By using blocking to ensure the autonomy of a domain or OU, you can ensure that domain or OU administrators have full control over the policies that apply to users and computers under their administration. Keep in mind also that the way blocking or enforcement is used depends largely on your organizational structure and how much control is delegated. Some organizations may choose to centrally manage Group Policy. Others may delegate control to divisions, branch offices, or departments within the organization. There is no one-size-fits-all solution. A balance between central management and delegation of control might work best.
Using the GPMC, you can block inheritance by right-clicking the domain or OU that should not inherit settings from higher-level containers and then selecting Block Inheritance. If Block Inheritance is already selected, selecting it again removes the setting. When you block inheritance in the GPMC, a blue circle with an exclamation point is added to the container’s node in the console tree, as shown in Figure 3-6. The notification icon provides a quick way to tell whether any domain or OU has the Block Inheritance setting enabled.
To prevent administrators who have authority over a container from overriding or blocking inherited Group Policy settings, you can enforce inheritance. When inheritance is enforced, all configured policy settings from higher-level policy objects are inherited and applied regardless of the policy settings configured in lower-level policy objects. Thus, enforcement of inheritance is used to supersede overriding and blocking of policy settings.
Forest administrators can use inheritance enforcement to ensure that configured policy settings from the site level are applied and prevent overriding or blocking of policy settings by both domain and OU administrators. Domain administrators can use inheritance enforcement to ensure that configured policy settings from the domain level are applied and prevent overriding or blocking of policy settings by OU administrators. Here are some examples of inheritance enforcement in action:
As a forest administrator, you want to ensure that domains inherit a particular site policy, so you configure the site policy to enforce inheritance. All configured policy settings from the site policy are thus applied regardless of whether domain administrators have tried to override or block policy settings from the site level. Enforcement of the site policy also affects inheritance for OUs in the affected domains. They will inherit the site policy regardless of whether overriding or blocking has been used.
As a domain administrator, you want to ensure that OUs within the domain inherit a particular domain policy, so you configure the domain policy to enforce inheritance. All configured policy settings from the domain policy are thus applied regardless of whether OU administrators have tried to override or block policy settings from the domain level. Enforcement of the domain policy also affects inheritance for child OUs within the affected OUs. They will inherit the domain policy regardless of whether overriding or blocking has been used.
Using the GPMC, you can enforce policy inheritance by expanding the container to which the policy is linked, right-clicking the link to the GPO, and then selecting Enforced. If Enforced is already selected, selecting it again removes the enforcement. In the GPMC, you can determine which policies are inherited and which policies are enforced in several ways:
Select a policy object anywhere in the GPMC, and then view the related Scope tab in the right pane (Figure 3-7). If the policy is enforced, the Enforced column under Links will have a Yes entry.
Select a domain or OU container in the GPMC, and then view the related Group Policy Inheritance tab in the right pane (Figure 3-8). If the policy is enforced, you’ll see an (Enforced) entry in the Precedence column.
Caution
Enforcing group policy inheritance dramatically affects the way Group Policy is processed and applied. By default, a site policy has the lowest precedence and as such is the first policy processed. Any of the other policy objects can override or block its settings because they are processed later. On the other hand, an enforced site policy can have the highest precedence and as such will be the last policy processed. This means that no other policy objects can override or block its settings.