User Group Policy loopback processing mode is a policy setting you can use to maintain a computer’s configuration regardless of who logs on. Loopback processing mode configures the user policy settings based on the computer rather than on the user. When this policy setting is enabled, one set of user settings applies to all users who log on to the computer. Because this policy setting targets computer accounts, it is a powerful tool and ideally suited for closely managed environments such as servers, terminal servers, classrooms, public kiosks, and reception areas.
Note
When you enable the policy setting for loopback processing mode, you must ensure that both the computer and user portions of the GPO are enabled.
The loopback policy is set in the Group Policy Object Editor snap-in by using the following policy setting:
Computer SettingsAdministrative TemplatesSystemGroup PolicyUser Group Policy loopback processing mode
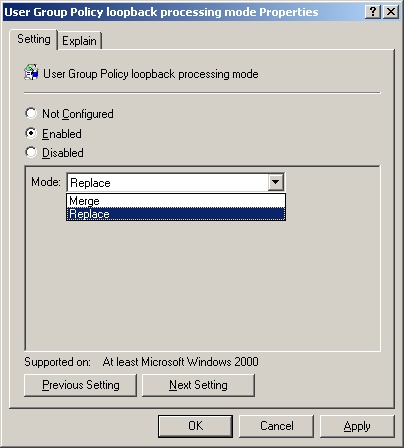
As shown in Figure 12-1, when you enable this policy you can select one of two loopback processing modes: Replace or Merge.
In Replace mode, the list of GPOs and their settings for the user account is not used. Instead, the GPO list for the user is entirely replaced by the GPO list that was obtained for the computer at startup, and the User Configuration settings from the GPO that has the loopback setting configured are applied to the user account instead. This means that when loopback processing in Replace mode is enabled, policy is processed as follows:
The computer settings in the GPOs for the computer account are applied.
The user settings in the GPOs for the user account are ignored.
The user settings in the GPOs for the computer account are applied.
As a best practice, you might use Replace mode when you have computers that are exposed to the public—for example, if you have a computer that is located in the reception area of your company’s corporate office or a public kiosk that you provide somewhere within your office or company. When the public has access to the computer, you want to lock down the interface completely to ensure that the user cannot run operating system tools or other potentially dangerous applications on the computer.
Here are some best practices when using loopback processing in Replace mode:
Create Software Restriction Policies that limit available applications to what the public user needs.
Remove the entire shell except for Microsoft® Internet Explorer.
Remove the user’s ability to gain access to features and functions by pressing
Ctrl+Alt+Del.
Disable the ability to right-click and access shortcut menus.
Remove the Shutdown menu option and button.
In Merge mode, the list of GPOs and settings for the user is gathered during the logon process. Then the list of GPOs and settings for the computer is gathered. Next, the list of GPO settings for the user account that are contained within the GPO with the loop-back setting enabled is added to the end of the GPO settings originally compiled for the user account. As a result of this appending of the user settings, the GPO settings that were obtained from the GPO with the loopback setting configured will have higher precedence. Therefore, when loopback processing in Merge mode is enabled, policy is processed as follows:
Computer settings in the GPOs for the computer account are applied.
User settings in the GPOs for the user account are applied.
User settings in the GPOs for the computer account are applied, taking precedence over user settings in the GPOs for the user account.
Although Merge mode offers great control, it still allows many of the individual user GPO settings to affect the logon environment. Merge mode is appropriate for settings such as student labs, Terminal Services sessions, and classrooms. With Merge mode, you can control many of the environment features that are security risks while still providing users with their desktops, applications, and other features that allow them to perform their job functions.
Here are some best practices when using loopback processing in Merge mode:
When you are testing and validating the use of the loopback feature, it will usually be obvious whether the correct settings are being applied. The difficulty arises when the correct settings are not being applied. Remember that when you are using Replace mode, none of the user settings from the GPOs affecting the user are applied, only user settings in the GPOs affecting the computer. Therefore, if you see any of the user settings coming through that you specifically did not configure in the GPO in which loopback processing has been enabled, the GPO in which loopback processing is enabled is most likely not being applied at all. Here are some possible reasons for this:
The computer account is not in the correct OU to receive the GPO settings.
The user or computer (or both) settings have been disabled for the GPO that has the loopback policy configured.
The GPOs have not replicated properly to all of the domain controllers.
The GPO containing the loopback policy has been filtered to not include the computer account you are targeting.
Another option for troubleshooting the application of loopback policy is to use the Group Policy Modeling Wizard or the Group Policy Results Wizard in the Group Policy Management Console (GPMC). The Group Policy Modeling Wizard allows you to evaluate a scenario for a particular computer account and user account based on specific GPO settings and criteria. This includes the ability to model the effects of loopback processing, as shown in Figure 12-2.
The Group Policy Results Wizard offers real-time evaluation of an existing user and computer account. After you run the wizard, you are presented with a summary of the settings that should be applied to both accounts. These results will indicate which policies were applied, the policy setting configuration, and which GPO the policy came from. If you run the wizard and learn that the loopback policy should be applied to the computer but hasn’t been, you must evaluate the list of potential problems that are listed above. If the wizard indicates that no loopback setting is configured, you must determine where the GPO is linked and where the computer account is located.