Computers running Windows 2000 or later can use Automatic Updates to maintain the operating system. Automatic Updates is an automatic distribution and installation mechanism for critical updates, security updates, update rollups (which include other updates), and service packs (which provide a comprehensive collection of updates). You can use Automatic Updates in conjunction with Windows Update Service to maintain Office, Microsoft Exchange, Microsoft SQL Server™, and hardware drivers.
Automatic Updates has a client/server architecture. The client component resides on a local computer and is responsible for downloading and installing updates. The server component resides on a remote computer and is the source from which updates are obtained. Many aspects of this client/server process can be configured and optimized for specific environments. You can do the following:
Optimize the way updates are downloaded and installed
Immediately install updates or schedule installation
Block access to Windows Updates
Designate the server to use for updates
Policy settings for Automatic Updates are found under Computer ConfigurationAdministrative TemplatesWindows ComponentsWindows Update and under Configuration, Administrative Templates, Windows Components, Windows Update. The sections that follow discuss policy settings and configuration options related to these tasks. Many of the Windows Update policies are designed for either Windows XP Professional SP2 and later or Windows Server 2003 SP1 and later, so be sure to check the compatibility details in the Explain Text.
Although you can configure Automatic Updates separately for each computer in your organization, it makes much more sense to manage this feature for groups of computers through Group Policy. Using Group Policy, you can designate a specific Automatic Updates configuration for all computers in a site, domain, or OU. Any time you need to modify the way Automatic Updates is used, you can modify the appropriate policy settings in one location and be sure the new settings will be applied to all computers as appropriate when policy is refreshed.
To specify whether and how computers receive updates, you use Configure Automatic Updates under Computer ConfigurationAdministrative TemplatesWindows ComponentsWindows Update. Using the basic Disabled or Enabled settings, you can either prevent or allow the use of Automatic Updates. Here are some guidelines:
With production servers or other types of critical servers, you might want to disable Configure Automatic Updates to prevent automatic installation of updates and thus allow only updates to be downloaded and installed manually. Requiring manual installation on production servers is often a good idea because you might want to test updates in development servers beforehand.
With most end-user computers and member servers, you should enable Configure Automatic Updates and then choose a specific update technique that either allows immediate installation or schedules the installation for an appropriate time. Because some installations of some updates require a reboot afterward, you’ll often want to schedule installation.
You can disable Automatic Updates by completing the following steps:
Access the GPO you want to work with. Access Computer ConfigurationAdministrative TemplatesWindows ComponentsWindows Update.
Double-click Configure Automatic Updates.
Select Disabled and then click OK.
Note
When automatic updates are disabled, you are not notified about updates. You can, however, download updates manually from the Windows Update Web site (http://windowsupdate.microsoft.com/).
You can enable and configure Automatic Updates by completing the following steps:
Access the GPO you want to work with. Access Computer ConfigurationAdministrative TemplatesWindows ComponentsWindows Update.
Double-click Configure Automatic Updates.
Select Enabled and then choose one of the following options in the Configure Automatic Updating list (Figure 6-10):
2 - Notify For Download And Notify For Install. Windows notifies the current user before retrieving any updates. If the user elects to download the update, she still has the opportunity to accept or reject the update. Accepted updates are installed. Rejected updates are not installed, but they remain on the system so they can be installed later.
3 - Auto Download And Notify For Install. This is the default option. Windows retrieves all updates at a configurable interval (called the detection frequency) and then prompts the user when the updates are ready to be installed. The user can then accept or reject the update. Accepted updates are installed. Rejected updates are not installed, but they remain on the system so they can be installed later.
4 - Auto Download And Schedule For Install. Updates are downloaded automatically at a configurable interval (called the detection frequency) and then installed according to a specific schedule, which can be once a day at a particular time or once a week on a particular day and at a particular time.
5 - Allow Local Admin To Choose Setting. The local administrators can configure Automatic Updates on a per-computer basis through the Automatic Updates tab of the System utility. Local administrators cannot, however, disable Automatic Updates through the System utility.
If you elected to schedule the update installation, select a Scheduled Install Day. Choose 0 to allow updates to be installed on any day of the week. To choose a specific installation day, choose 1 to install updates on Sunday, 2 to install updates on Monday, and so on.
If you elected to schedule the update installation, select a Scheduled Install Time. The default value is 03:00 (3 A.M.). Choose 0 to allow updates to be installed on any day of the week. To choose a different installation time, choose an appropriate value. Keep in mind that the time is set using a 24-hour clock, where values from 00:00 to 11:00 are A.M. and values from 12:00 to 23:00 are P.M.
When you are ready to continue, click OK.
By default, all types of updates are installed only when the system is shut down and restarted. Some updates, however, can be installed immediately without interrupting system services or requiring system restart. To allow immediate installation of updates that do not interrupt system services or require a restart, double-click Allow Automatic Updates Immediate Installation. Select Enabled and then click OK.
By default, only computer administrators receive update notification. To allow any user logged on to a computer to receive update notifications as appropriate for the Automatic Updates configuration, double-click Allow Non-Administrators To Receive Update Notifications. Select Enabled and then click OK.
When you’ve configured Automatic Updates for auto download and install, the Automatic Update process works like this:
Automatic Updates checks for updates automatically, according to the detection frequency. It then downloads the available updates.
With notify user installs, Automatic Updates notifies the user that an update is available. If the computer needs to be restarted, the user is prompted.
With scheduled installs, Automatic Updates schedules the install. If the computer needs to be restarted, the computer is restarted automatically by default.
You can control the automatic download and installation process in each of these steps through Group Policy. The sections that follow detail how to do this.
When you configure Automatic Updates to automatically download updates, it does so according to the interval called the detection frequency. By default, this interval is 22 hours, meaning computers will check for updates approximately every 22 hours. To ensure that many computers don’t use exactly the same interval, Windows uses an offset of minus zero to minus 20 percent. As a result, computers using the default interval check for updates anywhere between 18 and 22 hours. If you want to use a different interval, you can do so by completing the following steps:
Access the GPO you want to work with. Access Computer ConfigurationAdministrative TemplatesWindows ComponentsWindows Update.
Double-click Automatic Updates Detection Frequency.
Select Enabled and then use the combo box provided to set the desired detection frequency interval (Figure 6-11). The range of acceptable values is 1 hour to 22 hours.
Click OK.
With notify user installs, the user is notified that an update is available for installation when update download is complete and is given the option to install the update. If the user elects not to install the update at that time, Windows updates the Shut Down Windows dialog box to include an Install Updates And Shutdown option. This option is selected by default to give users another opportunity to install updates before shutting down their computers.
For user computers and member servers, you typically want the Install Updates And Shutdown option to be selected by default during shutdown of the operating system. On production servers or other critical servers, however, you might not want this behavior to be automatic. For example, you might want updates to be tested prior to installation on development or other test servers. In this case, you might want to do the following:
Hide the Install Updates And Shutdown option. If you don’t want this option to be available in the Shut Down Windows dialog box, enable Do Not Display ‘Install Updates And Shutdown’ Option under Computer ConfigurationAdministrative TemplatesWindows ComponentsWindows Update. The Install Updates And Shutdown option will be hidden from view and users will not be able to select it.
Make sure the Install Updates And Shutdown option isn’t selected by default. If you don’t want this option to be the default, enable Do Not Adjust Default Option under Computer ConfigurationAdministrative TemplatesWindows ComponentsWindows Update. The Install Updates And Shutdown option will not be the automatic default. The default will be the last shutdown option chosen by the user.
When a restart is required after a scheduled automatic update, the computer installs the updates according to the schedule and then restarts the computer if necessary after a 5-minute delay. To see how this works, consider the following example. You’ve scheduled Automatic Updates to install at 5 A.M. every Thursday. The system must be restarted to complete updates installed at 5 A.M. on Thursday. The computer is restarted at 5:05 A.M.
Through Group Policy, you can control the restart process in several ways. If you want to use a different restart delay, double-click Delay Restart For Scheduled Installations under Computer ConfigurationAdministrative TemplatesWindows ComponentsWindows Update. Select Enabled, set the restart delay using the combo box provided, and then click OK. For example, if you want to restart the computer after a 15-minute delay, you can set the restart value to 15, as shown in Figure 6-12.
Note
The acceptable restart delay values are from 1 to 30 minutes. A value of 1 is the closest you can get to an immediate restart after install.
You can also prevent Auto-Restart after a scheduled install if a user is logged on. To do this, double-click No Auto-Restart For Scheduled Automatic Updates Installations under Computer ConfigurationAdministrative TemplatesWindows ComponentsWindows Update. Select Enabled and then click OK. If you enable No Auto-Restart For Scheduled Automatic Updates Installations, the computer does not automatically restart after installing updates that require a restart if a user is currently logged on. Instead, Automatic Updates notifies the user that a restart is needed and waits until the computer is restarted. Restarting the computer enforces the updates.
Note
If you set No Auto-Restart For Scheduled Automatic Updates Installations to Disabled or Not Configured, the computer restarts automatically after a scheduled install. The restart delay in this case is 5 minutes.
Other policy settings you might find useful for controlling restarts are as follows:
Re-prompt for Restart With Scheduled Installations. When Automatic Updates is configured for scheduled installation of updates, this setting ensures that the logged-on user is prompted again after a set interval if a restart was previously postponed. If the setting is disabled or not configured, the default re-prompt interval of 10 minutes is used.
Reschedule Automatic Updates Scheduled Installations. This setting specifies the amount of time that Automatic Updates waits after system startup before proceeding with a scheduled installation that was previously missed.
In rare instances, you might not want users in a domain or OU to be able to use Automatic Updates. For example, if computers are used in a lab or kiosk setting only, you might want to disable Automatic Updates completely; you do this through Group Policy at the domain or OU level.
More typically, however, you disable Automatic Updates for individual local machines rather than at the domain or OU level. For example, if a computer used in a lab or kiosk setting should not be updated, you can disable Automatic Updates completely through the local machine policy (as long as you are configuring a standalone machine or there are no overriding site, domain, or OU policy settings for a machine that is a member of a domain).
You block access to Automatic Updates using Remove Access To Use All Windows Update Features under User ConfigurationAdministrative TemplatesWindows ComponentsWindows Update. Select Enabled and then click OK. When you enable this setting, all Windows Update features are removed. Users are blocked from accessing Windows Update, and automatic updating is completely disabled.
The Windows Update process is designed so that updates are downloaded over the Internet by default. This process works fine when your organization has a few dozen computers, but when your organization has hundreds or thousands of computers, this process is very inefficient. When you have many computers to maintain, a better way to obtain updates is to use a central update server to host updates from the Microsoft Update Web sites. You can then use this update service to automatically update computers on your network. Thus, rather than having hundreds or thousands of computers downloading the same or similar updates over the Internet, you have a single designated server that downloads updates for the organization. Client computers in the organization then connect to this server to obtain updates. Statistics about the updates are then delivered back to this server or a specifically designated statistics server in the organization. This means you can have a one-server or two-server update configuration.
To configure your site, domain, or OU to use a single update server, complete the following steps:
Configure a Windows server as an application server running IIS. The server should be running Windows 2000 Server SP3 or Windows Server 2003 and must have access to the Internet over port 80.
DNS must be set up appropriately to allow internal access to the server by its fully qualified domain name.
Access the GPO you want to work with. Access Computer ConfigurationAdministrative TemplatesWindows ComponentsWindows Update.
Double-click Specify Intranet Microsoft Update Service Location.
Select Enabled and then type the fully qualified domain name of the update server in both boxes, as shown in Figure 6-13.
Click OK.
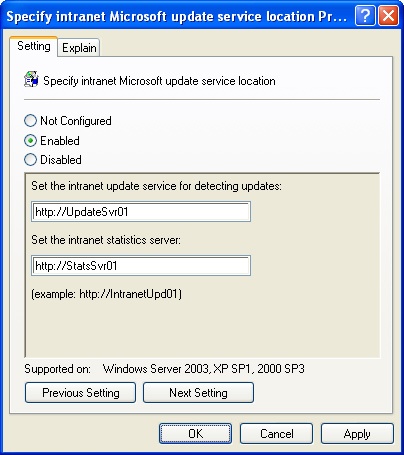
To configure your site, domain, or OU to use an update server and a statistics server, complete the following steps:
Configure two Windows servers as application servers running IIS. The servers should be running Windows 2000 Server SP3 or Windows Server 2003. The update server must have access to the Internet over port 80.
DNS must be set up appropriately to allow internal access to the servers by their fully qualified domain name.
Access the GPO you want to work with. Access Computer ConfigurationAdministrative TemplatesWindows ComponentsWindows Update.
Double-click Specify Intranet Microsoft Update Service Location.
Select Enabled and in the Set The Intranet Update Service box, type the fully qualified domain name of the update server (Figure 6-14).
In the Set The Intranet Statistics Server box, type the fully qualified domain name of the statistics server.
Click OK.