Creating a new GPO is a separate process from linking that GPO to an Active Directory site, domain, or OU. When you choose to create a new GPO with the Create And Link A GPO Here option in the GPMC, a new GPO (with its component GPC and GPT parts) is created and the GPO is linked to the currently focused container object. As with the GPC and GPT, a lot happens behind the scenes during GPO link creation.
Like the GPC for a GPO, sites, domains, and OUs are represented in the directory as a type of container object. When you link a GPO to a site, domain, or OU, a link reference is inserted into the gPLink attribute on that container object. The link reference includes the full LDAP path for the GPC portion of the GPO as well as a status flag. Here is an example:
LDAP://cn={E6AD4E44-5D5D-42E1-A49F- FF50F03249E9},cn=policies,cn=system,DC=cpandl,DC=com;0
If more than one GPO is linked to a particular container object, the gPLink attribute contains a bracket-delimited ([]) list of the LDAP DNs for all GPOs linked to that container. Each LDAP DN has its own status flag, as shown in the following example:
[LDAP://cn={E6AD4E44-5D5D-42E1-A49F-FF50F03249E9},cn=policies,cn=system, DC=cpandl,DC=com;0][LDAP://cn={E8E47CF6-8643-45C8-9E13-0A392C0A3E8B}, cn=policies,cn=system,DC=cpandl,DC=com;0][LDAP://cn={F9D36F52-E28D-4D54-87DB- 9DFFBE9EAB73},cn=policies,cn=system,DC=cpandl,DC=com;0]
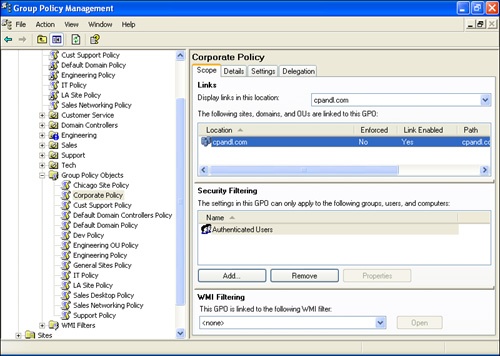
As you can see, three GPOs are linked to this container object. Each bracketed DN points to the GPC for a particular GPO, and within each reference is a numeric flag value at the end, delimited by a semicolon from the DN. The flag lists the current state of the link; it can have different values, depending on the options you’ve chosen for the link. Link states are controlled by the administrator from the GPMC, on the Scope tab for a GPO, as shown in Figure 13-7.
The gpLink flag tracks the enabled and enforced state of the link, as described in Chapter 3. The combination of enforced and enabled states on a link controls the flag value that appears within the gPLink list. Table 13-4 shows the possible values of this flag.
Note
When you disable a link, an enforcement setting of Yes is simply ignored until the link is enabled again. Also, disabling a link on an active GPO can have the same effect as moving the computers or users to a different scope of management from that GPO. That is, when the link is disabled, the GPO no longer applies to computers and users that were processing it, and any settings provided by that GPO are undone, if supported. See Chapter 3 for details.
The order of the link entries is also important because it reflects the rank order of the links. Lower-ranking policy objects are processed before higher-ranking policy objects. With the gPLink attribute, the lower-priority links go at the beginning of the list of DNs and the higher-priority links go at the end of the list of DNs. The link order reflected in the previous example is as follows:
Link Order 3: [LDAP://cn={E6AD4E44-5D5D-42E1-A49F-FF50F03249E9},cn=policies, cn=system,DC=cpandl,DC=com;0]
Link Order 2: [LDAP://cn={E8E47CF6-8643-45C8-9E13-0A392C0A3E8B},cn=policies, cn=system,DC=cpandl,DC=com;0]
Link Order 1: [LDAP://cn={F9D36F52-E28D-4D54-87DB-9DFFBE9EAB73},cn=policies, cn=system,DC=cpandl,DC=com;0]
Here the GPO with the first link reference (and a link order of 3) is processed first, giving it the lowest link order and the lowest precedence. The GPO with the second link reference (and a link order of 2) is processed next. The GPO with the third link reference (and a link order of 1) is processed last, giving it the highest link order and the highest precedence.
You should not edit the gPLink attribute directly. You should always use the GPMC to change the state of a GPO link. That said, you can use ADSI Edit to view the gPLink attribute for a domain or OU container object by following these steps:
Click Start, select Run, type adsiedit.msc in the Open box, and then click OK.
Double-click the Domain naming context and then double-click the node for the domain you want to work with, such as DC=Cpandl,DC=Com.
Right-click the container object for the domain or OU you want to work with, and then select Properties.
In the Properties dialog box, scroll down to the gPLink attribute and double-click it to show the current contents.
Site objects are not stored in the Domain naming context. They are stored in the Configuration naming context within a forest. Therefore, you must connect to the Configuration naming context to view site objects and their gPLink properties. Follow these steps:
In ADSI Edit, double-click the Configuration naming context and then double-click the configuration node for the domain you want to work with, such as CN=Configuration,DC=Cpandl,DC=Com.
Double-click CN=Sites. Right-click the container object for the site you want to work with, and then select Properties.
In the Properties dialog box, scroll down to the gPLink attribute and double-click it to show the current contents.
In addition to the gPLink attribute, there is one other attribute of interest on container objects when it comes to Group Policy Processing: the gPOptions attribute. The gPOptions attribute is a flag that gets set whenever block inheritance is enabled for that container.
In addition to the gPLink attribute, another important attribute of container objects that concerns Group Policy Processing is gPOptions. The gPOptions attribute is a flag that is set whenever block inheritance is enabled for that container.
Block inheritance lets you control which upstream GPOs are processed by essentially specifying that any GPOs linked to containers upstream of the blocked container will not apply. When block inheritance is set on a container object, the value of the gPOptions attribute on that container is set to 1. If block inheritance is not set, the attribute is either 0 or <Not Set>.
It might be obvious, but it’s important to note that security filtering and delegation of a GPO is set on the GPO object itself—or, more precisely, on its component GPC and GPT objects, as described earlier in the chapter. Security does not reside within the GPO link. As a result, you might have a single GPO linked to multiple containers but the security filtering applied to that GPO will apply equally across all containers to which it is linked. This can cause some confusion if you are reusing a GPO for multiple containers but need different security filtering or delegation for each one. You essentially need to set all of the security filtering or delegation you need across all links on the GPO and ensure that no group memberships have overlapping scopes of management that materially alter the desired behavior.