Server hardening consists of creating a baseline for the security on your servers in your organization. The default configurations of a Windows Server 2003 computer are not designed with security as the primary focus. Rather, a default installed computer is designed for communication and functionality. To protect your servers, you must establish solid and sophisticated security policies for all types of servers in your organization.
In this section, we will discuss the basic security baseline for a member server that is running in a Windows Server 2003 Active Directory domain. We will also discuss the best-practice security configurations in the security templates, starting with the generic best practices that apply to most member servers in the organization. We will then move on to the specific types of member servers, as well as domain controllers. We will discuss which services, ports, applications, and so forth need to be hardened for different server roles, and compare this to the baseline security for simple member servers.
You must establish a baseline of security for all members servers before creating additional security templates and policies to tailor security for specific types of servers. One of the most important aspects of applying hardening settings to member servers is developing the OU hierarchy that will support the security template and policies that you develop. You must also understand the various levels of security that are routinely used to develop and deploy security to all servers.
The only way to efficiently and successfully deploy security to the different server roles in your enterprise is to design Active Directory to support those roles. The design should not only provide an efficient method to deploy security, but it should also organize the computer accounts into OUs for easier management and troubleshooting.
Although Active Directory design is extremely flexible, you must consider a number of factors when organizing servers into OUs based on server role. The first factor is Group Policy application. For example, if you have two server roles that each need different security policy settings, you should separate the computer accounts into different OUs. The second factor is administration of the computer accounts within Active Directory. Even though you have only two different server roles, you might have two different administrators controlling the same type of server role. This might force you to have OUs not only for server roles, but also for server roles based on the administrator in charge.
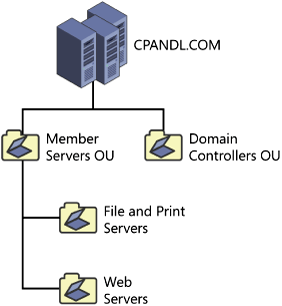
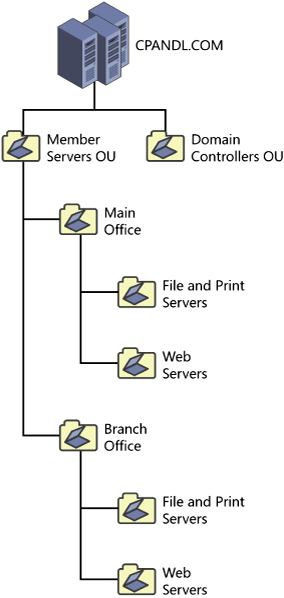
Figure 5-7 illustrates an OU structure that does not consider location or administrative needs but does consider server roles. Figure 5-8 illustrates an OU structure that has a different set of administrators for the Main Office and Branch Office, where each office also has the same types of server roles.
Figure 5-8. An OU structure that considers location and administrative needs as well as server roles
Tip
OUs are also commonly organized by physical location—for example, the Main Office and Branch Office model. For more information on organizing OUs based on GPO deployment, see Chapter 4.
Member server security environments are based on the operating systems of the clients and servers in your enterprise. Legacy clients and servers can’t take advantage of the robust features and functions that Active Directory provides, such as Group Policy, Kerberos, and other security features. As the operating systems of domain members rise to levels that support all Active Directory functions and features, it becomes possible to raise the overall security for the enterprise and thus create a solid security environment.
There are three different security environment levels typically found in an enterprise environment:
Legacy Client. When you have a mixed operating system environment of new and older versions, you must provide adequate security that will not constrain the operation of legacy clients. This is the lowest security level, but it needs to be that way for communication to occur and legacy applications to work properly. This business environment might include legacy clients such as Windows 95, Windows 98, or Windows NT 4.0 Workstation. You should limit this environment to having only Windows 2000 Server and Windows Server 2003 domain controllers. You should not support Windows NT 4.0 Server domain controllers, although you can have Windows NT Server computers configured as member servers.
Enterprise Client. This security level removes the legacy operating systems and uses only those that support the features and functions that Active Directory offers. This includes clients running Windows 2000 Professional and Windows XP Professional. These clients all support Group Policy, Kerberos authentication, and new security features that the legacy clients don’t support. The domain controllers must be Windows 2000 Server or later. There will not be any Windows NT Server computers, even as member servers.
High Security. This security level is basically the same as for Enterprise Client—it changes only the level of security that is implemented. This level enhances security standards so that all computers conform to stringent security policies for both clients and servers. This environment might be constrictive enough that loss of functionality and manageability occurs. However, this must be acceptable because the higher security levels are a good tradeoff for the functionality and manageability that you are losing.
This section will cover some common security settings that apply to standard member servers in the domain. These settings are best created in a GPO that is then linked to the top-level server OU. In Figure 5-7 or Figure 5-8, this would be the Member Servers OU.
Table 5-7 provides a full list of security settings for a member server.
Table 5-7. Security Settings for Member Servers
Security Setting | Legacy Client Configuration | Enterprise Client Configuration | High Security Configuration |
|---|---|---|---|
Auditing | |||
Account Logon Events | Success Failure | Success Failure | Success Failure |
Account Management | Success Failure | Success Failure | Success Failure |
Directory Service | Success Failure | Success Failure | Success Failure |
Logon Events | Success Failure | Success Failure | Success Failure |
Object Access | Success Failure | Success Failure | Success Failure |
Policy Change | Success | Success | Success |
Privilege Use | No Auditing | Failure | Success Failure |
Process Tracking | No Auditing | No Auditing | No Auditing |
System Events | Success | Success | Success |
User Rights | |||
Access this computer from the network | Not Defined (Use defaults) | Not defined (Use defaults) | Administrators, Authenticated Users |
Act as part of the operating system | Not Defined (Use defaults) | Not Defined (Use defaults) | Revoke all security groups and accounts |
Add workstations to domain | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators |
Adjust memory quotas for a process | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators, NETWORK SERVICE, LOCAL SERVICE |
Allow log on locally | Administrators, Backup Operators, Power Users | Administrators, Backup Operators, Power Users | Administrators, Backup Operators, Power Users |
Allow log on through Terminal Services | Administrators, Remote Desktop Users | Administrators, Remote Desktop Users | Administrators |
Change the system time | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators |
Debug programs | Revoke all security groups and accounts | Revoke all security groups and accounts | Revoke all security groups and accounts |
Deny access to this computer from the network | ANONYMOUS LOGON; Built-in Administrator, Guests; SUPPORT_388945a0; Guest; all NON-Operating System service accounts | ANONYMOUS LOGON; Built-in Administrator, Guests; SUPPORT_388945a0; Guest; all NON-Operating System service accounts | ANONYMOUS LOGON; Built-in Administrator, Guests; SUPPORT_388945a0; Guest; all NON-Operating System service accounts |
User Rights | |||
Deny log on as a batch job | Guests; Support_388945a0; | Guest Guests; Support_388945a0; | Guest Guests; Support_388945a0; Guest |
Deny log on through Terminal Services | Built-in Administrator; Guests; Support_388945a0; Guest; all NON-operating system service accounts | Built-in Administrator; Guests; Support_388945a0; Guest; all NON-operating system service accounts | Built-in Administrator; Guests; Support_388945a0; Guest; all NON-operating system service accounts |
Enable computer and user accounts to be trusted for delegation | Not Defined (Use defaults) | Not Defined (Use defaults) | Revoke all security groups and accounts |
Force shutdown from a remote system | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators |
Generate security audits | Not Defined (Use defaults) | Not Defined (Use defaults) | NETWORK SERVICE, LOCAL SERVICE |
Impersonate a client after authentication | Not Defined (Use defaults) | Not Defined (Use defaults) | Local Service; Network Service |
Increase scheduling priority | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators |
Load and unload device drivers | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators |
Lock pages in memory | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators |
Log on as a batch job | Not Defined (Use defaults) | Not Defined (Use defaults) | Revoke all security groups and accounts |
Manage auditing and security log | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators |
Modify firmware environment values | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators |
Perform volume maintenance tasks | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators |
Profile single process | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators |
Profile system performance | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators |
Remove computer from docking station | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators |
Replace a process level token | Not Defined (Use defaults) | Not Defined (Use defaults) | LOCAL SERVICE, NETWORK SERVICE |
Restore files and directories | Not Defined (Use defaults) | Administrators | Administrators |
Shut down the system | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators |
Synchronize directory service data | Not Defined (Use defaults) | Not Defined (Use defaults) | Revoke all security groups and accounts |
Take ownership of files or other objects | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators |
Security Options | |||
Accounts: Guest account status | Disabled | Disabled | Disabled |
Accounts: Limit local account use of blank passwords to console logon | Enabled | Enabled | Enabled |
Audit: Audit the access of global system objects | Disabled | Disabled | Disabled |
Audit: Audit the use of Backup and Restore privilege | Disabled | Disabled | Disabled |
Audit: Shut down system immediately if unable to log security audits | Disabled | Disabled | Enabled |
Devices: Allow undock without having to log on | Disabled | Disabled | Disabled |
Devices: Allowed to format and eject removable media | Administrators | Administrators | Administrators |
Devices: Prevent users from installing printer drivers | Enabled | Enabled | Enabled |
Devices: Restrict CD-ROM access to locally logged—on user only | Not Defined (Use defaults) | Not Defined (Use defaults) | Enabled |
Security Options | |||
Devices: Restrict floppy access to locally logged—on user only | Not Defined (Use defaults) | Not Defined (Use defaults) | Enabled |
Devices: Unsigned driver installation behavior | Warn but allow installation | Warn but allow installation | Warn but allow installation |
Domain controller: Allow server operators to schedule tasks | Disabled | Disabled | Disabled |
Domain controller: LDAP server signing requirements | Not Defined (Use defaults) | Not Defined (Use defaults) | Require Signing |
Domain controller: Refuse machine account password changes | Disabled | Disabled | Disabled |
Domain member: Digitally encrypt or sign secure channel data (always) | Disabled | Enabled | Enabled |
Domain member: Digitally encrypt secure channel data (when possible) | Enabled | Enabled | Enabled |
Domain member: Digitally sign secure channel data (when possible) | Enabled | Enabled | Enabled |
Domain member: Disable machine account password changes | Disabled | Disabled | Disabled |
Domain member: Maximum machine account password age | 30 days | 30 days | 30 days |
Domain member: Require strong (Windows 2000 or later) session key | Enabled | Enabled | Enabled |
Interactive logon: Do not display last user name | Enabled | Enabled | Enabled |
Interactive logon: Do not require CTRL+ALT+DEL | Disabled | Disabled | Disabled |
Interactive logon: Message text for users attempting to log on | This system is restricted to authorized users. Individuals attempting unauthorized access will be prosecuted. If unauthorized, terminate access now! Clicking on OK indicates your acceptance of the information in the background. | This system is restricted to authorized users. Individuals attempting unauthorized access will be prosecuted. If unauthorized, terminate access now! Clicking on OK indicates your acceptance of the information in the background. | This system is restricted to authorized users. Individuals attempting unauthorized access will be prosecuted. If unauthorized, terminate access now! Clicking on OK indicates your acceptance of the information in the background. |
Interactive logon: Message title for users attempting to log on | IT IS AN OFFENSE TO CONTINUE WITHOUT PROPER AUTHORIZATION | IT IS AN OFFENSE TO CONTINUE WITHOUT PROPER AUTHORIZATION | IT IS AN OFFENSE TO CONTINUE WITHOUT PROPER AUTHORIZATION |
Interactive logon: Number of previous logons to cache (in case domain controller is not available) | 1 | 0 | 0 |
Interactive logon: Prompt user to change password before expiration | 14 days | 14 days | 14 days |
Interactive logon: Require Domain Controller authentication to unlock workstation | Enabled | Enabled | Enabled |
Interactive logon: Smart card removal behavior | Not Defined (Use defaults) | Lock Workstation | Lock Workstation |
Microsoft network client: Digitally sign communications (always) | Disabled | Enabled | Enabled |
Microsoft network client: Digitally sign communications (if server agrees) | Enabled | Enabled | Enabled |
Microsoft network client: Send unencrypted password to third-party SMB servers | Disabled | Disabled | Disabled |
Microsoft network server: Amount of idle time required before suspending session | 15 minutes | 15 minutes | 15 minutes |
Microsoft network server: Digitally sign communications (always) | Disabled | Enabled | Enabled |
Microsoft network server: Digitally sign communications (if client agrees) | Enabled | Enabled | Enabled |
Microsoft network server: Disconnect clients when logon hours expire | Enabled | Enabled | Enabled |
Network access: Do not allow anonymous enumeration of SAM accounts | Enabled | Enabled | Enabled |
Network access: Do not allow anonymous enumeration of SAM accounts and shares | Enabled | Enabled | Enabled |
Network access: Do not allow storage of credentials or .NET Passports for network authentication | Enabled | Enabled | Enabled |
Network access: Let Everyone permissions apply to anonymous users | Disabled | Disabled | Disabled |
Network access: Named Pipes that can be accessed anonymously | None | None | None |
Network access: Remotely accessible registry paths | SystemCurrent ControlSetControlProductOptions; SystemCurrent ControlSetControlServer Applications; SoftwareMicrosoftWindows NTCurrentVersion | SystemCurrent ControlSetControlProductOptions; SystemCurrent ControlSetControlServer Applications; SoftwareMicrosoftWindows NTCurrentVersion | SystemCurrent ControlSet ControlProduct-Options; SystemCurrent ControlSetControlServer Applications; SoftwareMicrosoftWindows NTCurrentVersion |
Network access: Remotely accessible registry paths and sub-paths | SystemCurrent ControlSetControlPrintPrinters ________________ SystemCurrent ControlSetServicesEventlog ________________ SystemCurrent ControlSetServicesEventlog SoftwareMicrosoftOLAP Server ________________ SoftwareMicrosoftWindows NTCurrentVersionPrint ________________ SoftwareMicrosoftWindows NTCurrentVersionWindows ________________ SystemCurrent ControlSetControlContentIndex ________________ | SystemCurrent ControlSetControlPrintPrinters ________________ SystemCurrent ControlSetServicesEventlog ________________ SystemCurrent ControlSetServicesEventlog SoftwareMicrosoftOLAP Server ________________ SoftwareMicrosoftWindows NTCurrentVersionPrint ________________ SoftwareMicrosoftWindows NTCurrentVersionWindows ________________ | SystemCurrent ControlSetControlPrintPrinters ________________ SystemCurrent ControlSetServicesEventlog ________________ SystemCurrent ControlSetServicesEventlog SoftwareMicrosoftOLAP Server ________________ SoftwareMicrosoftWindows NTCurrentVersionPrint ________________ SoftwareMicrosoftWindows NTCurrentVersionWindows ________________ |
Network access: Remotely accessible registry paths and sub-paths | SystemCurrent ControlSetControlTerminal Server ________________ SystemCurrent ControlSetControlTerminal ServerUserConfig ________________ SystemCurrent ControlSetControlTerminal ServerDefaultUser Configuration ________________ SoftwareMicrosoftWindows NTCurrentVersionPerflib ________________ SystemCurrent ControlSetServicesSysmonLog | SystemCurrent ControlSetControlContentIndex ________________ SystemCurrent ControlSetControlTerminal Server ________________ SystemCurrent ControlSetControlTerminal ServerUserConfig ________________ SystemCurrent ControlSetControlTerminal ServerDefaultUser Configuration ________________ SoftwareMicrosoftWindows NTCurrentVersionPerflib ________________ SystemCurrent ControlSetServicesSysmonLog | SystemCurrent ControlSetControlContentIndex ________________ SystemCurrent ControlSetControlTerminal Server ________________ SystemCurrent ControlSetControlTerminal ServerUserConfig ________________ SystemCurrent ControlSetControlTerminal ServerDefault User Configuration ________________ SoftwareMicrosoftWindows NTCurrentVersionPerflib ________________ SystemCurrent ControlSetServicesSysmonLog |
Network access: Restrict anonymous access to Named Pipes and Shares | Enabled | Enabled | Enabled |
Network access: Shares that can be accessed anonymously | None | None | None |
Network access: Sharing and security model for local accounts | Classic—local users authenticate as themselves | Classic—local users authenticate as themselves | Classic—local users authenticate as themselves |
Network security: Do not store LAN Manager hash value on next password change | Enabled | Enabled | Enabled |
Network security: LAN Manager authentication level | Send NTLMv2 responses only | Send NTLMv2 response only/refuse LM | Send NTLMv2 response only/refuse LM and NTLM |
Network security: LDAP client signing requirements | Negotiate signing | Negotiate signing | Negotiate signing |
Network security: Minimum session security for NTLM SSP based (including secure RPC) clients | No minimum | Enabled all settings | Enabled all settings |
Network security: Minimum session security for NTLM SSP based (including secure RPC) servers | No minimums | Enabled all settings | Enabled all settings |
Recovery console: Allow automatic administrative logon | Disabled | Disabled | Disabled |
Recovery console: Allow floppy copy and access to all drives and all folders | Enabled | Enabled | Disabled |
Shutdown: Allow system to be shut down without having to log on | Disabled | Disabled | Disabled |
Shutdown: Clear virtual memory page file | Disabled | Disabled | Enabled |
System cryptography: Force strong key protection for user keys stored on the computer | User is prompted when the key is first used | User is prompted when the key is first used | User must enter a password each time they use a key |
System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing | Disabled | Disabled | Disabled |
System objects: Default owner for objects created by members of the Administrators group | Object creator | Object creator | Object creator |
System objects: Require case insensitivity for non-Windows subsystems | Enabled | Enabled | Enabled |
System objects: Strengthen default permissions of internal system objects (such as Symbolic Links) | Enabled | Enabled | Enabled |
System settings: Optional subsystem | None | None | None |
Event Log | |||
Maximum application log size | 16,384 KB | 16,384 KB | 16,384 KB |
Maximum security log size | 81,920 KB | 81,920 KB | 81,920 KB |
Maximum system log size | 16,384 KB | 16,384 KB | 16,384 KB |
Prevent local guests group from accessing application log | Enabled | Enabled | Enabled |
Prevent local guests group from accessing security log | Enabled | Enabled | Enabled |
Prevent local guests group from accessing system log | Enabled | Enabled | Enabled |
Retention method for application log | As needed | As needed | As needed |
Retention method for security log | As needed | As needed | As needed |
Retention method for system log | As needed | As needed | As needed |
System Services | |||
Alerter | Disabled | Disabled | Disabled |
Application Layer Gateway Service | Disabled | Disabled | Disabled |
Application Management | Disabled | Disabled | Disabled |
ASP.NET State Service | Disabled | Disabled | Disabled |
Automatic Updates | Automatic | Automatic | Automatic |
Background Intelligent Transfer Service | Manual | Manual | Manual |
Certificate Services | Disabled | Disabled | Disabled |
MS Software Shadow Copy Provider | Manual | Manual | Manual |
Client Service for Netware | Disabled | Disabled | Disabled |
ClipBook | Disabled | Disabled | Disabled |
Cluster Service | Disabled | Disabled | Disabled |
COM+ Event System | Manual | Manual | Manual |
COM+ System Application | Disabled | Disabled | Disabled |
Computer Browser | Automatic | Automatic | Automatic |
Cryptographic Services | Automatic | Automatic | Automatic |
DHCP Client | Automatic | Automatic | Automatic |
DHCP Server | Disabled | Disabled | Disabled |
Distributed Link Tracking Client | Disabled | Disabled | Disabled |
Distributed Link Tracking Server | Disabled | Disabled | Disabled |
Distribution Transaction Coordinator | Disabled | Disabled | Disabled |
DNS Client | Automatic | Automatic | Automatic |
DNS Server | Disabled | Disabled | Disabled |
Error Reporting Service | Disabled | Disabled | Disabled |
Event Log | Automatic | Automatic | Automatic |
Fax Service | Disabled | Disabled | Disabled |
File Replication | Disabled | Disabled | Disabled |
File Server for Macintosh | Disabled | Disabled | Disabled |
FTP Publishing | Disabled | Disabled | Disabled |
Help and Support | Disabled | Disabled | Disabled |
HTTP SSL | Disabled | Disabled | Disabled |
Human Interface Device Access | Disabled | Disabled | Disabled |
IAS Jet Database Access | Disabled | Disabled | Disabled |
IIS Admin Service | Disabled | Disabled | Disabled |
IMAPI CD–Burning COM Service | Disabled | Disabled | Disabled |
Indexing Service | Disabled | Disabled | Disabled |
Infrared Monitor | Disabled | Disabled | Disabled |
Internet Authentication Service | Disabled | Disabled | Disabled |
Internet Connection Firewall (ICF)/Internet Connection Sharing (ICS) | Disabled | Disabled | Disabled |
Intersite Messaging | Disabled | Disabled | Disabled |
IP Version 6 Helper Service | Disabled | Disabled | Disabled |
IPSec Policy Agent (IPSec Service) | Automatic | Automatic | Automatic |
Kerberos Key Distribution Center | Disabled | Disabled | Disabled |
License Logging Service | Disabled | Disabled | Disabled |
Logical Disk Manager | Manual | Manual | Manual |
Logical Disk Manager Administrative Service | Manual | Manual | Manual |
Message Queuing | Disabled | Disabled | Disabled |
Message Queuing Down Level Clients | Disabled | Disabled | Disabled |
Message Queuing Triggers | Disabled | Disabled | Disabled |
Messenger | Disabled | Disabled | Disabled |
Microsoft POP3 Service | Disabled | Disabled | Disabled |
MSSQL$UDDI | Disabled | Disabled | Disabled |
MSSQLServerADHelper | Disabled | Disabled | Disabled |
.NET Framework Support Service | Disabled | Disabled | Disabled |
Netlogon | Automatic | Automatic | Automatic |
NetMeeting Remote Desktop Sharing | Disabled | Disabled | Disabled |
Network Connections | Manual | Manual | Manual |
Network DDE | Disabled | Disabled | Disabled |
Network DDE DSDM | Disabled | Disabled | Disabled |
Network Location Awareness (NLA) | Manual | Manual | Manual |
Nework News Transport Protocol (NNTP) | Disabled | Disabled | Disabled |
NTLM Support Provider | Automatic | Automatic | Automatic |
Performance Logs and Alerts | Manual | Manual | Manual |
Plug and Play | Automatic | Automatic | Automatic |
Portable Media Serial Number | Disabled | Disabled | Disabled |
Printer Server for Macintosh | Disabled | Disabled | Disabled |
Print Spooler | Disabled | Disabled | Disabled |
Protected Storage | Automatic | Automatic | Automatic |
Remote Access Auto Connection Manager | Disabled | Disabled | Disabled |
Remote Access Connection Manager | Disabled | Disabled | Disabled |
Remote Administration Service | Manual | Manual | Manual |
Remote Desktop Helper Session Manager | Disabled | Disabled | Disabled |
Remote Installation | Disabled | Disabled | Disabled |
Remote Procedure Call (RPC) | Automatic | Automatic | Automatic |
Remote Procedure Call (RPC) Locator | Disabled | Disabled | Disabled |
Remote Registry Service | Automatic | Automatic | Automatic |
Remote Server Manager | Disabled | Disabled | Disabled |
Remote Server Monitor | Disabled | Disabled | Disabled |
Remote Storage Notification | Disabled | Disabled | Disabled |
Remote Storage Server | Disabled | Disabled | Disabled |
Removable Storage | Manual | Manual | Manual |
Resultant Set of Policy Provider | Disabled | Disabled | Disabled |
Routing and Remote Access | Disabled | Disabled | Disabled |
SAP Agent | Disabled | Disabled | Disabled |
Secondary Logon | Disabled | Disabled | Disabled |
Security Accounts Manager | Automatic | Automatic | Automatic |
Server | Automatic | Automatic | Automatic |
Shell Hardware Detection | Disabled | Disabled | Disabled |
Simple Mail Transport Protocol (SMTP) | Disabled | Disabled | Disabled |
Simple TCP/IP Services | Disabled | Disabled | Disabled |
Single Instance Storage Groveler | Disabled | Disabled | Disabled |
Smart Card | Disabled | Disabled | Disabled |
SNMP Service | Disabled | Disabled | Disabled |
SNMP Trap Service | Disabled | Disabled | Disabled |
Special Administration Console Helper | Disabled | Disabled | Disabled |
System Event Notification | Automatic | Automatic | Automatic |
Task Scheduler | Disabled | Disabled | Disabled |
TCP/IP NetBIOS Helper Service | Automatic | Automatic | Automatic |
TCP/IP Print Server | Disabled | Disabled | Disabled |
Telephony | Disabled | Disabled | Disabled |
Telnet | Disabled | Disabled | Disabled |
Terminal Services | Automatic | Automatic | Automatic |
Terminal Services Licensing | Disabled | Disabled | Disabled |
Terminal Services Session Directory | Disabled | Disabled | Disabled |
Themes | Disabled | Disabled | Disabled |
Trival FTP Daemon | Disabled | Disabled | Disabled |
Uninterruptible Power Supply | Disabled | Disabled | Disabled |
Upload Manager | Disabled | Disabled | Disabled |
Virtual Disk Service | Disabled | Disabled | Disabled |
Volume Shadow Copy | Manual | Manual | Manual |
WebClent | Disabled | Disabled | Disabled |
Web Element Manager | Disabled | Disabled | Disabled |
Windows Audio | Disabled | Disabled | Disabled |
Windows Image Acquisition (WIA) | Disabled | Disabled | Disabled |
Windows Installer | Automatic | Automatic | Automatic |
Windows Internet Name Service (WINS) | Disabled | Disabled | Disabled |
Windows Management Instrumentation | Automatic | Automatic | Automatic |
Windows Management Instrumentation Driver Extensions | Manual | Manual | Manual |
Windows Media Services | Disabled | Disabled | Disabled |
Windows System Resource Manager | Disabled | Disabled | Disabled |
Windows Time | Automatic | Automatic | Automatic |
WinHTTP Web Proxy Auto—Discovery Service | Disabled | Disabled | Disabled |
Wireless Configuration | Disabled | Disabled | Disabled |
WMI Performance Adapter | Manual | Manual | Manual |
Workstation | Automatic | Automatic | Automatic |
World Wide Publishing Service | Disabled | Disabled | Disabled |
Note
Account Policies, which include Password Policy, Account Lockout Policy, and Kerberos Policy, are not specified in the member servers security baseline outlined here. This is because Account Policies must be defined at the domain level in Active Directory, while the member servers security baseline is defined in GPOs linked to OUs where member servers are found. For best practices concerning domain Account Policies, see "Account Policies" under "Sections of the Security Template" earlier in this chapter, and also refer to the Windows Server 2003 Security Guide described in the "Windows Server 2003 Security Guide" sidebar.
For a member server to function on the network with other computers, specific ports must be opened. Table 5-8 presents a list of those critical ports. As we investigate specific server roles, additional ports will need to be added to ensure the server functions properly.
Table 5-8. Ports for Member Servers
Port | Description |
|---|---|
137 (NetBIOS name service) | Used by the browse master service. This must be open for WINS and browse master servers. |
138 (NetBIOS datagram service) | Must be open to accept inbound datagrams from NetBIOS applications such as the Messenger service or the Computer Browser service. |
139 (NetBIOS session service) | Must be closed unless you run applications or operating systems that need to support Windows networking (SMB) connections. If you run Windows NT 4.0, Windows Millennium Edition, Windows 98, or Windows 95, this port must be open on your servers. |
445 (CIFS/SMB server) | Used by basic Windows networking, including file sharing, printer sharing, and remote administration. |
3389 (Remote Desktop Protocol) | Must be open if you are using Terminal Services for application sharing, remote desktop, or remote assistance. |
Domain controllers are the heart of any environment that runs Active Directory. These computers must be stable, protected, and available to provide the key services for the directory service, user authentication, resource access, and more. If there is any loss or compromise of a domain controller in the environment, the result can be disastrous for clients, servers, and applications that rely on domain controllers for authentication, Group Policy, and the LDAP directory.
Not only should these domain controllers be hardened with security configurations, they must also be physically secured in locations that are accessible only to qualified administrative staff. If domain controllers are stored in unsecured locations due to limitations of the facility (such as in a branch office), you should apply additional security configurations to limit the potential damage from physical threats against the computer.
Along the same lines as the Member Server hardening guidelines, domain controllers also have different levels of security based on the environment in which they are deployed. These levels are the same as those defined in the "Member Servers" section in this chapter: Legacy Client, Enterprise Client, and High Security.
Security settings that apply specifically to domain controllers are best created in a GPO that is then linked to the Domain Controllers OU. The settings for domain controllers should be based on those we reviewed in the earlier "Member Servers" section. Of course, a domain controller also has additional functions or features compared to a member server, and this requires additional open ports and security configuration. You must review the security settings list to ensure that you are not restricting a key feature for your domain controller.
Table 5-9 lists the settings that differ from those specified in Table 5-7. In other words, the baseline security settings for domain controllers as outlined below should be incrementally added to the baseline security settings for member servers described previously.
Table 5-9. Security Settings for Domain Controllers
Security Setting | Legacy Client Configuration | Enterprise Client Configuration | High Security Configuration |
|---|---|---|---|
User Rights | |||
Access this computer from the network | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators, Authenticated Users, ENTERPRISE DOMAIN CONTROLLERS |
Add workstations to domain | Administrators | Administrators | Administrators |
Allow log on locally | Administrators | Administrators | Administrators |
Allow log on through Terminal Services | Administrators | Administrators | Administrators |
Change the system time | Administrators | Administrators | Administrators |
Enable computer and user accounts to be trusted for delegation | Not Defined (Use defaults) | Not Defined (Use defaults) | Administrators |
Load and unload device drivers | Administrators | Administrators | Administrators |
Restore files and directories | Administrators | Administrators | Administrators |
Shutdown the system | Administrators | Administrators | Administrators |
Security Options | |||
Network security: Do not store LAN Manager hash value on next password change | Disabled | Enabled | Enabled |
System Services | |||
Distributed File System | Automatic | Automatic | Automatic |
DNS Server | Automatic | Automatic | Automatic |
File Replication | Automatic | Automatic | Automatic |
Intersite Messaging | Automatic | Automatic | Automatic |
Kerberos Key Distribution Center | Automatic | Automatic | Automatic |
Remote Procedure Call (RPC) Locator | Automatic | Automatic | Automatic |
More Info
For more information on hardening domain controllers in different enterprise environments, see the Windows Server 2003 Security Guide found at http://www.microsoft.com/downloads/details.aspx?FamilyID=8a2643c1-0685-4d89-b655-521ea6c7b4db&displaylang=en.
Domain controllers are responsible for specific functions, as seen in the different settings listed in Table 5-9. Many of these different security template settings are due to required services to authenticate users and maintain consistency of the Active Directory database between other domain controllers. Table 5-10 lists additional ports that you must open for domain controllers.
Table 5-10. Ports for Domain Controllers
Ports | Description |
|---|---|
88 (Kerberos) | The Kerberos protocol is used by Windows 2000 and later operating systems to log on and retrieve tickets for accessing other servers. |
123 (NTP) | This port provides time synchronization for network clients using the Network Time Protocol (NTP). |
This port allows RPC clients to discover the ports that the RPC server is listening on. | |
389 (LDAP) | This port the primary way that clients access Active Directory to obtain user information, e-mail addresses, services, and other directory service information. |
464 (Kerberos Password Changes) | This port provides secure methods for users to change passwords using Kerberos. |
636 (LDAP over SSL) | This port is needed if LDAP will use SSL to provide encryption and mutual authentication for LDAP traffic. |
3268 (Global Catalog) | This port provides the means for clients to search Active Directory information that spans multiple domains. |
3269 (Global Catalog over SSL) | This port is needed because the Global Catalog uses SSL to provide encryption and mutual authentication for Global Catalog traffic. |
File and print servers are responsible for resource storage and controlling access to these resources throughout the enterprise. These servers house the company’s documents, trade secrets, financial data, and much more. If these computers are not protected, the entire company might be in jeopardy. These computers must be stable, protected, and available to provide users and applications access to resources stored on these computers.
Like the domain controllers, these servers must be physically protected. If someone were to get hold of a file server, they could potentially use other tools to gain access to the resources on the server. You should take action to protect against this.
Table 5-11 lists security settings for file and print servers that differ from the settings in the Member Servers section earlier in the chapter. In other words, the baseline security settings for file and print servers as outlined here should be incrementally added to the baseline security settings for member servers described previously. These settings are best created in a GPO that is then linked to the OU that contains the file servers.
Table 5-11. Security Settings for File and Print Servers
Security Setting | Legacy Client Configuration | Enterprise Client Configuration | High Security Configuration |
|---|---|---|---|
Security Options | |||
Microsoft network server: Digitally sign communications (always) | Disabled (Print Servers only) | Disabled (Print Servers only) | Disabled (Print Servers only) |
System Services | |||
Distributed File System | Disabled | Disabled | Disabled |
File Replication | Disabled | Disabled | Disabled |
Print Spooler | Automatic (Print Servers only) | Automatic (Print Servers only) | Automatic (Print Servers only) |
More Info
For more information on hardening file and print servers in different enterprise environments, see the Windows Server 2003 Security Guide found at http://www.microsoft.com/downloads/details.aspx?FamilyID=8a2643c1-0685-4d89-b655-521ea6c7b4db&displaylang=en.
Microsoft Internet Information Services (IIS) is the service that provides Web services on a Windows server. Web servers must be properly secured from malicious attackers, while still allowing legitimate clients to access intranet or public Web sites hosted on the server.
IIS is not installed by default on the Windows Server 2003 family of servers, and when you do install IIS, it installs in "locked" mode—a highly secure mode that protects IIS against threats. Beyond the best-practice security settings presented in this section for IIS, be sure to protect your Web servers by monitoring security using some form of intrusion detection system, and by implementing proper incident response procedures.
Security settings for Web servers are best created in a GPO that is then linked to the OU that contains the Web servers. Table 5-12 lists only the settings that differ from those in the Table 5-7. In other words, the baseline security settings for Web servers as outlined here should be incrementally added to the baseline security settings for member servers described previously.
Table 5-12. Security Settings for Web Servers
Security Setting | Legacy Client Configuration | Enterprise Client Configuration | High Security Configuration |
|---|---|---|---|
User Rights | |||
Deny access to this computer from the network | ANONYMOUS LOGON; Built-in Administrator; Support_ 388945a0; Guest; all NON-Operating System service accounts | ANONYMOUS LOGON; Built-in Administrator; Support_ 388945a0; Guest; all NON-Operating System service accounts | ANONYMOUS LOGON; Built-in Administrator; Support_ 388945a0; Guest; all NON-Operating System service accounts |
System Services | |||
HTTP SSL | Automatic | Automatic | Automatic |
IIS Admin Service | Automatic | Automatic | Automatic |
World Wide Web Publishing Service | Automatic | Automatic | Automatic |
More Info
For more information on hardening Web servers in different enterprise environments, see the Windows Server 2003 Security Guide found at http://www.microsoft.com/downloads/details.aspx?FamilyID=8a2643c1-0685-4d89-b655-521ea6c7b4db&displaylang=en.
Web servers should have limited ports available, to reduce their exposure to attacks from the local network and the Internet. The fewer the ports that are open, the better. Table 5-13 is a list of additional ports that you will need to open for Web servers.
Table 5-13. Ports for Web Servers
Ports | Description |
|---|---|
80 (HTTP) | The standard HTTP port for providing Web services to users. This can be easily changed and is not required. If you do change the port for HTTP, be sure to add that new port to this list and configure that setting within IIS. |
443 (HTTPS) | Allows HTTP to have a higher level of security that provides integrity, encryption, and authentication for Web traffic. |