User management is an essential part of any business application. Microsoft Dynamics CRM 2015 provides out-of-the-box support for user management and security. If you are using Microsoft Dynamics CRM 2015 on premise, a user can be added to Microsoft Dynamics CRM 2015 after being added in Active Directory. In the case of Microsoft Dynamics CRM 2015, online users can be managed using Office 356 portal.
Access to the Microsoft Dynamics CRM 2015 application can be managed using an entity called Security Role. Once a user is added to Microsoft Dynamics CRM 2015 he should have at least one security role or should be part of the owner team (the owner team should have at least one security role assigned). User security is handled in Microsoft Dynamics CRM 2015 in three ways:
- Role-based security
- Record-based security
- Field-level security
Note
You can refer to https://msdn.microsoft.com/en-us/library/gg309524.aspx to get more information about the CRM 2015 security model.
Role-based security is handled by security roles, which are basically a grouping of a set of privileges and five access levels. Privileges define which action a user can perform on a specific entity; for example, we can configure whether a user can create an account entity record or not. Access level defines up to what level the user can perform a particular action on a specific entity; for example, if a user can read data created by himself, created under his business unit, from a child business unit of his business unit, or from the organization level.
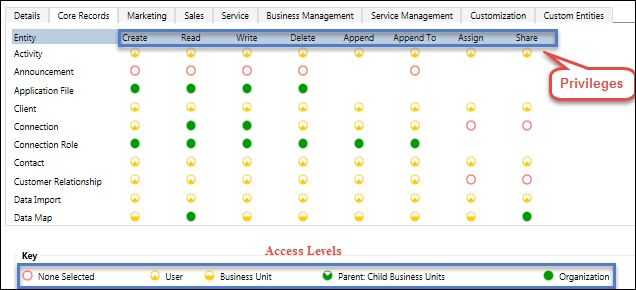
Record-based security is used to control security for specific entity records using access rights. Access rights work on the basis of privileges only, so an access right will only work if users have appropriate privileges on a specific entity; for example, a user can only access a record that is shared with him if he has read privileges.
Field-level security allows us to control specific field security on the basis of the field level security profile. In field-level security, we can define read, create, and update access to a particular field in which the field level security is enabled. In Microsoft Dynamics CRM 2015 we can enable field-level security for both system and custom fields. We will cover field-level security in detail in a later chapter.
For our training solution application, we are going to use the following three security roles:
|
Name |
Description |
|---|---|
|
Sales Person, Sales Manager |
To create and manage training requests and execute training programs |
|
System Customizer |
To implement any changes in training solutions |
|
System Administrator |
For the power admin user |
Note
You can refer to https://technet.microsoft.com/en-us/library/hh699698.aspx to get more details on Microsoft Dynamics CRM 2015 security management.
