Depending on the version of OpenID being used (OpenID version 1 or 2), the request for user authentication will take one of two courses from a programmatic perspective. The code will either:
Redirect the user to the endpoint established in the previous step (OpenID v1)
or:
Obtain the authentication form markup from the provider endpoint and print it out to the screen for the user (OpenID v2)
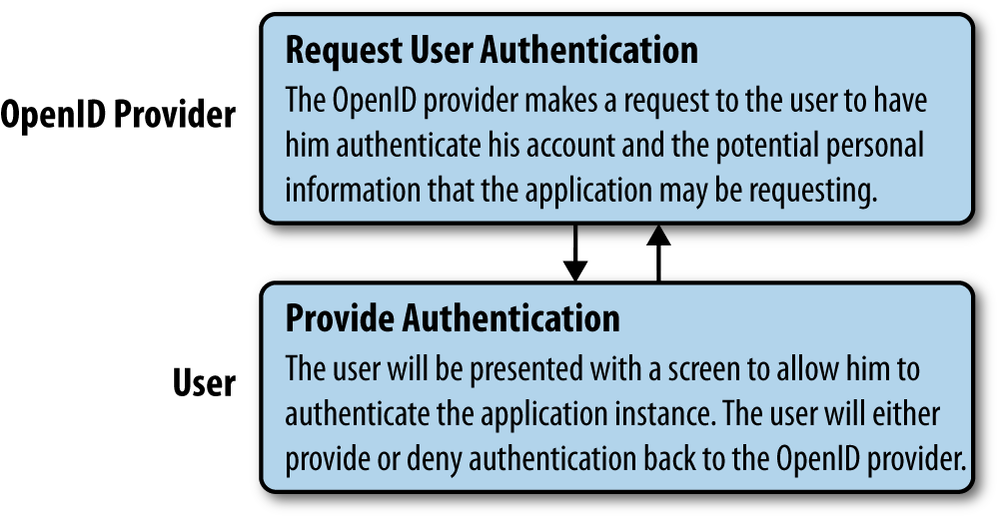
In both cases, the process that occurs between the relaying party and the user looks the same, as shown in Figure 11-3.
In general terms, the relaying party will display the authentication form to the user to have him authenticate herself against the OpenID provider (through either the form or redirect method).
When the relaying party establishes the request between the user and provider for authentication, the request will include a number of OpenID parameters, including those listed in Table 11-1.
Table 11-1. Authentication request parameters
Request parameter | Description |
|---|---|
| The OpenID namespace URI to be used. For instance, this should be http://specs.openid.net/auth/2.0 for OpenID 2.0 transactions. |
| The transaction mode to be used during the
authentication process. The possible values are If the
user should be able to interact with the OpenID provider, then
|
| |
| The local OpenID provider identifier. If http://specs.openid.net/auth/2.0/identifier_select is used as the identity, then the provider should choose the correct identifier for the user. |
| A handle for an association between the relaying party (implementing site) and the OpenID provider that should be used to sign the request. |
| The location where the user should be returned, with the OpenID response, after authentication has taken place. Many web-based providers require this field. If it is not included, it indicates that the relaying party does not want to return the user after authentication. |
| The URL pattern for the domain that the user should trust. For instance, *.mysite.com. Note, if |
The user, once presented with the form, will either authenticate or not. In either case, the user’s response will be returned to the relaying party. This response object that is returned will include the parameters listed in Table 11-2.
Table 11-2. Authentication response parameters
The relaying party and OpenID provider will then communicate with each other to complete the authentication process and provide the appropriate approval state.