- Programming Social Applications
- Dedication
- Preface
- 1. Social Application Container Core Concepts
- What Is a Social Application Container?
- Implementing Proprietary Versus Open Standards
- The Embedded Application: Building in a Black Box
- Embedded Application Security
- The External Application: Integrating Social Data Outside the Container
- Application Views
- Application Permission Concepts
- Client-Side Versus Server-Side Applications
- When Good Applications Go Bad
- Application Model Case Studies
- Quick-Start Tips
- 2. Mapping User Relationships with the Social Graph
- The Online Social Graph
- Applying the Real-Life Social Graph Online
- Sharing Private User Data: Opt-in Versus Opt-out
- Understanding Relationship Models
- Relationships Versus Entities
- Building Social Relevance: Exploring the Facebook Social Graph
- Defining Entity Likes and Dislikes Through the OpenLike Protocol
- Conclusion
- 3. Constructing the Foundation of a Social Application Platform
- 4. Defining Features with OpenSocial JavaScript References
- What You’ll Learn
- Including the OpenSocial Feature JavaScript Libraries
- Dynamically Setting the Height of a Gadget View
- Inserting Flash Movies in Your Gadget
- Displaying Messages to Your Users
- Saving State with User Preferences
- Setting Your Gadget Title Programmatically
- Integrating a Tabbed Gadget User Interface
- The Basic Gadget
- Creating a Tab from Markup
- Creating a Tab from JavaScript
- Getting and Setting Information About the TabSet
- Aligning tabs
- Showing and hiding tabs
- Obtaining the parent container
- Obtaining the currently selected tab
- Obtaining all tabs
- Removing a tab
- Setting the selected tab
- Swapping tab positions
- Getting and setting information about a tab
- Getting the callback of a tab
- Obtaining the content container
- Obtaining the tab position
- Obtaining the tab name
- Obtaining the tab label
- Extending Shindig with Your Own JavaScript Libraries
- Putting It All Together
- 5. Porting Applications, Profiles, and Friendships
- What You’ll Learn
- Evaluating OpenSocial Container Support
- Core Components of the OpenSocial Specification
- Cross-Container Development and Porting
- Porting Applications from Facebook to OpenSocial
- Personalizing Applications with Profile Data
- The Person Object
- Person Data Extraction Methods
- Fields Available Within the Person Object
- opensocial.Person.Field.ABOUT_ME
- opensocial.Person.Field.ACTIVITIES
- opensocial.Person.Field.ADDRESSES
- opensocial.Person.Field.AGE
- opensocial.Person.Field.BODY_TYPE
- opensocial.Person.Field.BOOKS
- opensocial.Person.Field.CARS
- opensocial.Person.Field.CHILDREN
- opensocial.Person.Field.CURRENT_LOCATION
- opensocial.Person.Field.DATE_OF_BIRTH
- opensocial.Person.Field.DRINKER
- opensocial.Person.Field.EMAILS
- opensocial.Person.Field.ETHNICITY
- opensocial.Person.Field.FASHION
- opensocial.Person.Field.FOOD
- opensocial.Person.Field.GENDER
- opensocial.Person.Field.HAPPIEST_WHEN
- opensocial.Person.Field.HAS_APP
- opensocial.Person.Field.HEROES
- opensocial.Person.Field.HUMOR
- opensocial.Person.Field.ID
- opensocial.Person.Field.INTERESTS
- opensocial.Person.Field.JOB_INTERESTS
- opensocial.Person.Field.JOBS
- opensocial.Person.Field.LANGUAGES_SPOKEN
- opensocial.Person.Field.LIVING_ARRANGEMENT
- opensocial.Person.Field.LOOKING_FOR
- opensocial.Person.Field.MOVIES
- opensocial.Person.Field.MUSIC
- opensocial.Person.Field.NAME
- opensocial.Person.Field.NETWORK_PRESENCE
- opensocial.Person.Field.NICKNAME
- opensocial.Person.Field.PETS
- opensocial.Person.Field.PHONE_NUMBERS
- opensocial.Person.Field.POLITICAL_VIEWS
- opensocial.Person.Field.PROFILE_SONG
- opensocial.Person.Field.PROFILE_URL
- opensocial.Person.Field.PROFILE_VIDEO
- opensocial.Person.Field.QUOTES
- opensocial.Person.Field.RELATIONSHIP_STATUS
- opensocial.Person.Field.RELIGION
- opensocial.Person.Field.ROMANCE
- opensocial.Person.Field.SCARED_OF
- opensocial.Person.Field.SCHOOLS
- opensocial.Person.Field.SEXUAL_ORIENTATION
- opensocial.Person.Field.SMOKER
- opensocial.Person.Field.SPORTS
- opensocial.Person.Field.STATUS
- opensocial.Person.Field.TAGS
- opensocial.Person.Field.THUMBNAIL_URL
- opensocial.Person.Field.TIME_ZONE
- opensocial.Person.Field.TURN_OFFS
- opensocial.Person.Field.TURN_ONS
- opensocial.Person.Field.TV_SHOWS
- opensocial.Person.Field.URLS
- Extending the Person Object
- Capturing the User Profile
- Using Friendships to Increase Your Audience
- Putting It All Together
- 6. OpenSocial Activities, Sharing, and Data Requests
- 7. Advanced OpenSocial and OpenSocial Next
- What You’ll Learn
- Data Pipelining
- OpenSocial Templating
- A Few More Tags: The OpenSocial Markup Language
- Localization Support with Message Bundles
- The OpenSocial REST API Libraries
- OpenSocial Next: Areas of Exploration
- OpenSocial and Distributed Web Frameworks
- Putting It All Together
- 8. Social Application Security Concepts
- What You’ll Learn
- Hosting Third-Party Code Through iframes
- A Secure Approach: The Caja Project
- Why Use Caja?
- Attack Vectors: How Caja Protects
- Setting Up Caja
- Cajoling Scripts from the Command Line
- Running Caja from a Web Application
- Running Caja with an OpenSocial Gadget
- Using JSLint to Spot JavaScript Issues Early
- Playing in the Caja Playground
- Tips for Working in a Caja Environment
- A Lighter Alternative to Caja: ADsafe
- ADsafe Versus Caja: Which One Should You Use?
- How to Implement ADsafe
- Putting It All Together
- Conclusion
- 9. Securing Social Graph Access with OAuth
- Beyond Basic Auth
- The OAuth 1.0a Standard
- OAuth 2
- OAuth 2 Workflow
- Implementation Example: Facebook
- Implementation Example: Requesting More User Information in the Facebook OAuth Process
- Implementation Example: End-User Experience
- Tips for Debugging Request Issues
- Conclusion
- 10. The Future of Social: Defining Social Entities Through Distributed Web Frameworks
- What You’ll Learn
- The Open Graph Protocol: Defining Web Pages As Social Entities
- Activity Streams: Standardizing Social Activities
- WebFinger: Expanding the Social Graph Through Email Addresses
- OExchange: Building a Social Sharing Graph
- PubSubHubbub: Content Syndication
- The Salmon Protocol: Unification of Conversation Entities
- Conclusion
- 11. Extending Your Social Graph with OpenID
- The OpenID Standard
- Do I Already Have an OpenID? How Do I Sign Up for One?
- The OpenID Authentication Flow
- OpenID Providers
- Bypassing Domain Discovery Errors in OpenID
- OpenID Extensions
- Simple Registration Extension
- Attribute Exchange Extension
- Attribute exchange types: Addresses
- Attribute exchange types: Audio and video greetings
- Attribute exchange types: Date of birth
- Attribute exchange types: Email
- Attribute exchange types: Images
- Attribute exchange types: Instant messaging
- Attribute exchange types: Name
- Attribute exchange types: Telephone
- Attribute exchange types: Websites
- Attribute exchange types: Work
- Attribute exchange types: Other personal details and preferences
- Provider Authentication Policy Extension
- Extensions Currently Under Development
- Implementation Example: OpenID
- Common Errors and Debugging Techniques
- Conclusion
- 12. Delivering User-Centric Experiences with Hybrid Auth
- The OpenID OAuth Hybrid Extension
- When Should I Use OpenID Versus Hybrid Auth?
- The OpenID OAuth Hybrid Auth Flow
- Implementation Example: OpenID, OAuth, and Yahoo!
- Application Setup: Getting Your OAuth Keys for the Hybrid Auth Process
- Implementing Hybrid Auth Using PHP
- Implementing Hybrid Auth Using Python
- Conclusion
- A. Web Development Core Concepts
- Glossary
- Index
- About the Author
- Colophon
- Copyright
Taking a 180-degree turn from the follower model, the connection model focuses on personal, singular interactions with other people or objects. To this end, implementers typically allow users to generate highly detailed and rich profile systems and tie them to other groups, organizations, and movements.
This model focuses on shared social experiences rather than the quick dissemination of information to large groups. Users of this model tend to share many of the most important events of their lives—both good and bad—with their friends via text, photos, and videos.
Facebook is an ideal example of this model type. The meat of the site is constructed around its users’ social profiles, which allows individuals to reach out and share pieces of information with one another and interact on a very personal level.
Although the Facebook news feed acts as a global push mechanism to share information with all of your friends, the true advantage for most active users is on the personal level. When you post items to your Wall, your friends may comment, providing a shared social experience. People who do not use Facebook simply as a feed mechanism for cross-posting between multiple services (such as Twitter) can use the site to develop highly engaging social experiences with friends, family, coworkers, or even strangers.
Between constructs such as direct messaging, status comments, groups, pages, applications, and more, Facebook offers users the opportunity to build a comprehensive profile and interact with people on a personal level.
People who are actively engaged in Facebook are looking for different things from the service than they would from Twitter, and in fact, casual Facebook users often comment that they “don’t get” Twitter. This is because the two services reach their audiences in very different ways.
Since a connection model usually contains a vastly complex and detailed amount of user information and personalization settings, privacy is often one of the most important priorities for implementers. Normal implementations tend to include layered privacy settings that allow users to display different pieces of information to different people, or to hide some data altogether by setting it to private. In addition, users generally have the option to hide the majority of their profiles from people they have not included in their circle of friends.
While sites built on this model usually have a strict security policy in place, it’s still very difficult to secure social data and shared information. This is especially true if you have an embedded application environment where third-party developers can build an application that accesses the profile information of users who have added it.
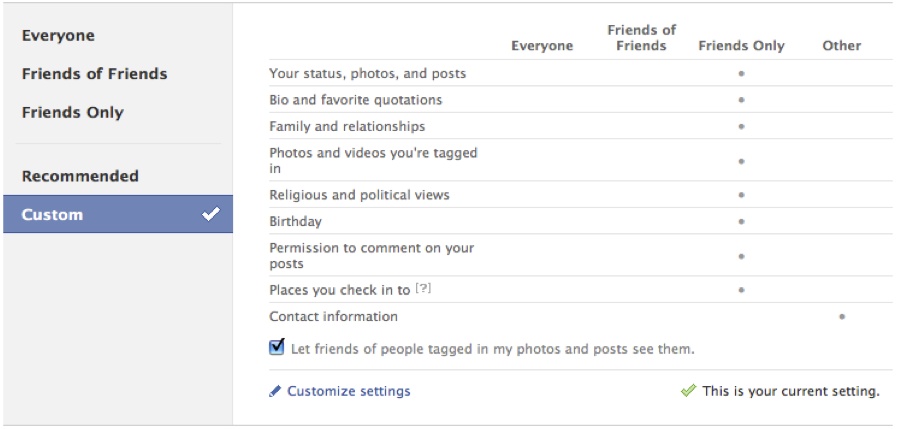
Another issue is that privacy settings within this type of model can become convoluted, especially when the application offers a high degree of customization. For example, Facebook has a number of security pages, like those shown in Figure 2-2, which are just a small portion of the full security features that are actually available on the site. With this kind of complexity, users can quickly become confused and misunderstand settings, making it easy for them to inadvertently allow unwanted parties to obtain access to their privileged data.
-
No Comment