Perform the following steps:
- Open the Nessus Web Client.
- Log in to the Nessus client with the user that you created during installation.
- Navigate to the Policies tab under the RESOURCES section on the home screen. This will list the preexisting policies created by all the users (which are only configured to be shared with everyone):
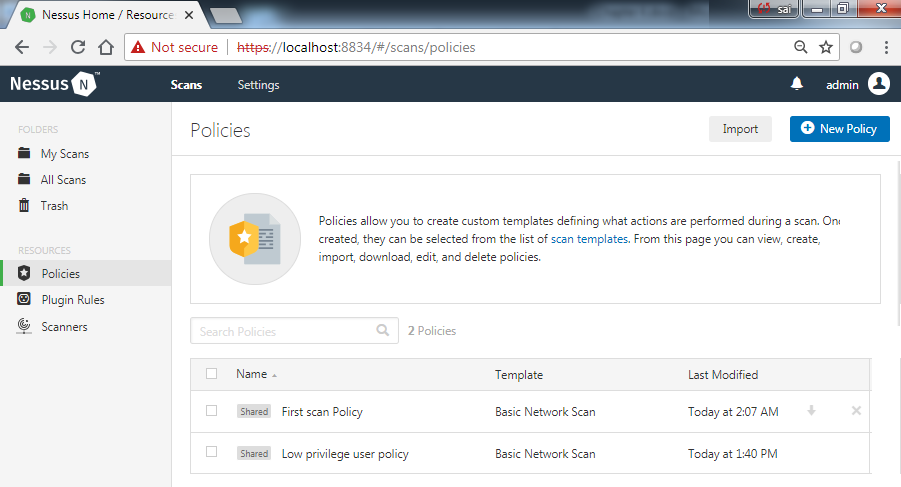
- You can choose from the existing policies or you can import a policy.
- If there is no existing policy that satisfies your requirements, you can create a new policy:
-
- If a user selects Advanced Scan, they can configure every parameter in the policy, thus defining the nature of the policy and whether it should be a network/web application/malware scan. The ASSESSMENTS menu makes it unique from other scan templates:
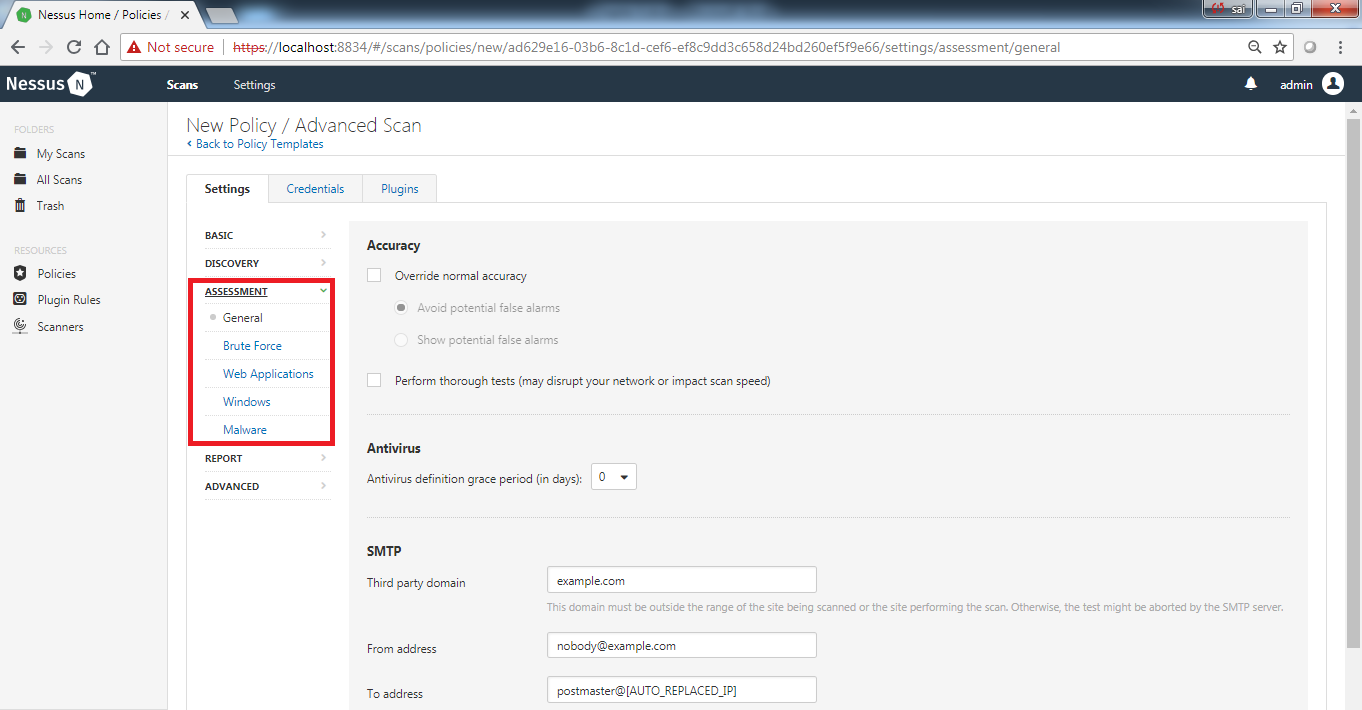
No other scan template can configure the plugins, except for Advanced Scan.
-
- The Badlock discovery template allows the user to check whether the remote Windows host is vulnerable to the Samba Badlock vulnerability:

-
- The Basic Network Scan template is used to perform a network-level port scan and identify service-level vulnerabilities with or without credentials for a remote host.
- The credential patch audit scan can be used to check the patch level of the remote host.
- The Drown detection template can be used to detect whether the remote host is vulnerable to a Drown attack:
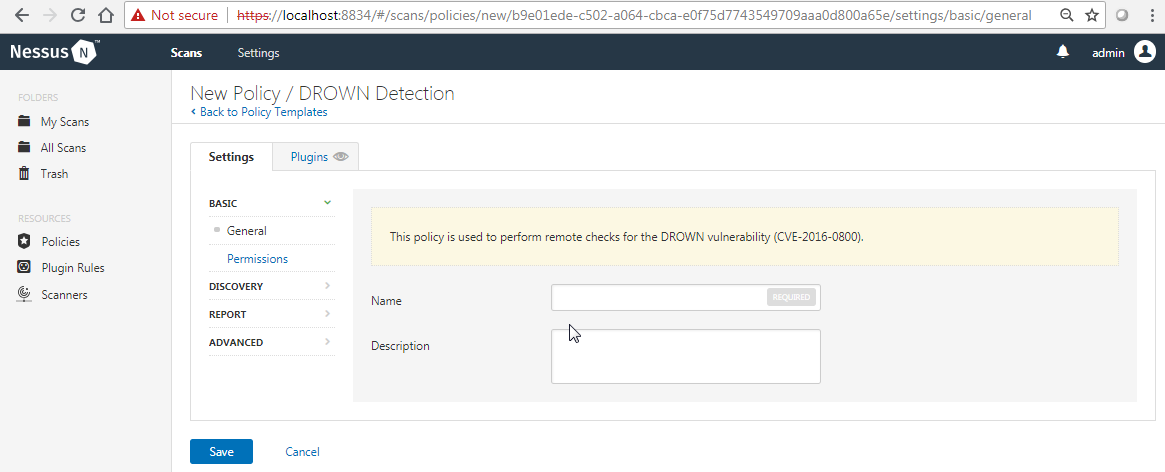
-
- The host discovery template is used to identify the live hosts from a large range or list of IP addresses, which are provided by the user.
- The Intel AMT Security Bypass scan template is used to identify whether the remote host is vulnerable to an Intel AMT Security Bypass:
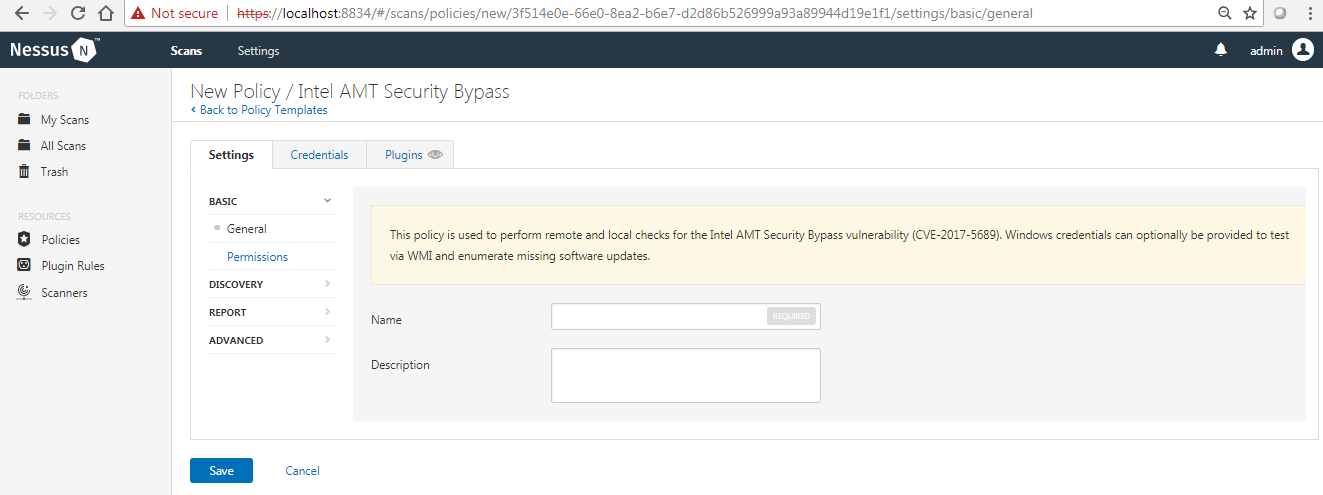
-
- The internal PCI network scan template is used to perform an ASV scan on the remote host in order to find out whether the host configuration is PCI-compliant or not.
- The malware scan template is used to perform a malware detection scan on Windows and Unix systems. This is better done when the credentials are provided.
- The policy compliance audit template can be used to perform a baseline configuration audit against an uploaded or preexisting Nessus audit file. We will see this recipe in future chapters.
- The Shadow Brokers Scan template is used to check whether the remote host is vulnerable to the attacks described in the Shadow Broker leaks:

-
- The Spectre, Meltdown, and WannaCry ransomware templates are used to verify whether those remote host is vulnerable to the respective attacks.
- The web application template is used to perform web application scans that are hosted on the remote host by providing remote HTTP authentication details.
- Once the specific template is selected, create the policy and save it, as shown in the How to manage Nessus policies recipe.
- Once the policy has been created, it is available for you to select for scanning under the user-created policies section of the Policies screen from the New Scan task:

- You can also select the policy on the go while creating a new scan by selecting the template and filling in the details.
