Perform the following steps:
- To confirm bind shell backdoor detection, open Command Prompt in Windows and type the following command:
telnet 192.168.103.129 1524

- Upon execution, the user directly gets logged in to the remote machine without providing any authentication:

- To confirm the privilege of the user, we will use the standard Linux command id to confirm the vulnerability:
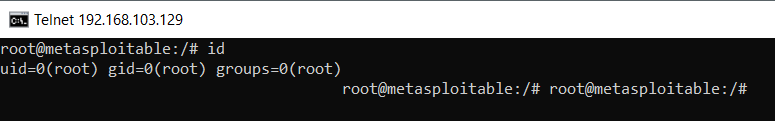
This command displays the UID and GID as 0, which represents a root user, and so we can confirm that the vulnerability is critical as it allows any remote user to log in to the machine without any authentication. This means that the vulnerability can be confirmed.
- For SSL v2 and SSL v3, we can identify the version running by using the Poodle confirmation script by Nmap, as only SSL v3 is vulnerable to Poodle. Open Nmap in Command Prompt.
- Enter the following command to identify whether the remote server is vulnerable to an SSL Poodle attack:
Nmap -sV –script ssl-poodle -p 25 192.168.103.129
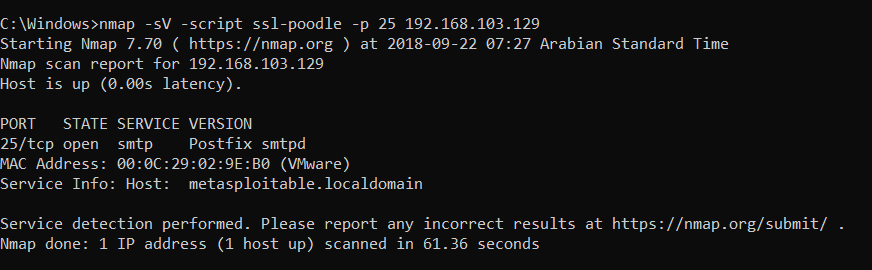
As Nmap has not displayed any results, let's check for the ssl-enum-ciphers script:
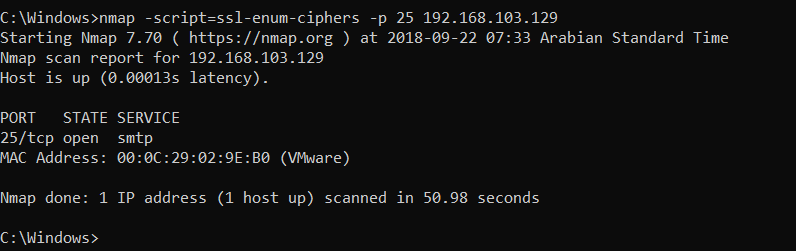
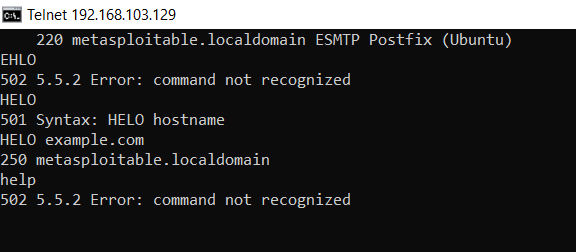
Even the enum-ciphers script has not returned any result, so we can conclude that Nmap was unable to negotiate with the port using SSL ciphers. Hence, we can mark the vulnerability as a false positive. We can also confirm the same by using Telnet on port 25 if a similar response is received. This means that port 25 is running on a non-SSL clear text protocol and the plugin has reported a false positive for the same:
- To confirm the Apache default files, access the URLs mentioned by Nessus in the vulnerability output section:

- Open the browser and type http://192.168.103.129:8180/tomcat-docs/index.html into the address bar:

This displays the default documentation folder, confirming the existence of the default files on the server. This shows that the vulnerability can be confirmed.
