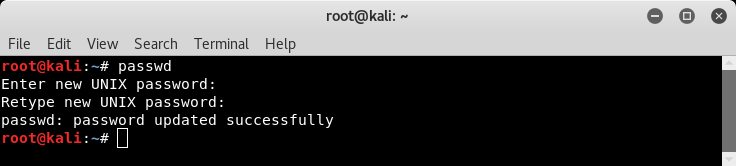
The default credentials in order to access Kali Linux are username:root and password:toor. However, after the first login, it is important to change the default credentials and set a new password. A new password can be set using the passwd command as shown in the following screenshot:
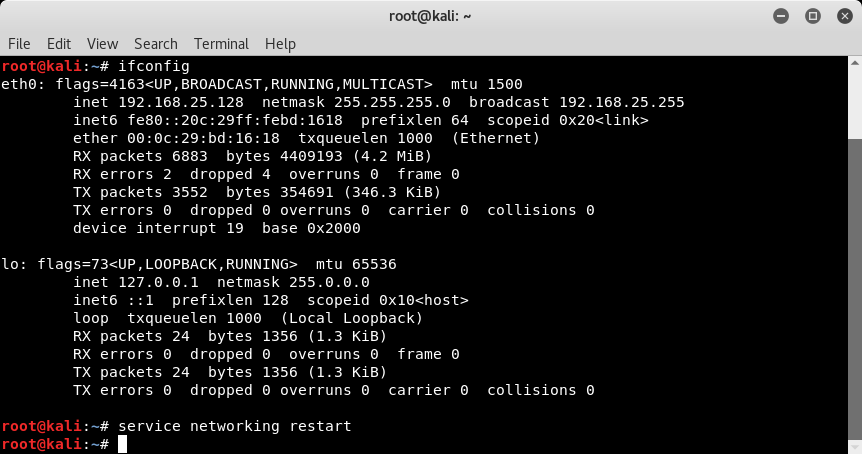
Kali Linux is comprehensively used for network and application penetration testing. So it is important that Kali Linux is connected to the network as a standalone Kali installation wouldn't be of much use. The first step in ensuring network connectivity is checking whether Kali has a valid IP address. We can use the ifconfig command as shown in the following screenshot and confirm the IP address allocation:
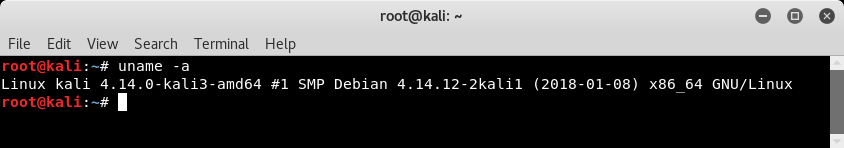
Now that we have changed the default credentials and also affirmed network connectivity, it's now time to check the exact version of our Kali installation. This includes the exact build details, including kernel and platform details. The uname -a command gives us the required details as shown in the following screenshot:
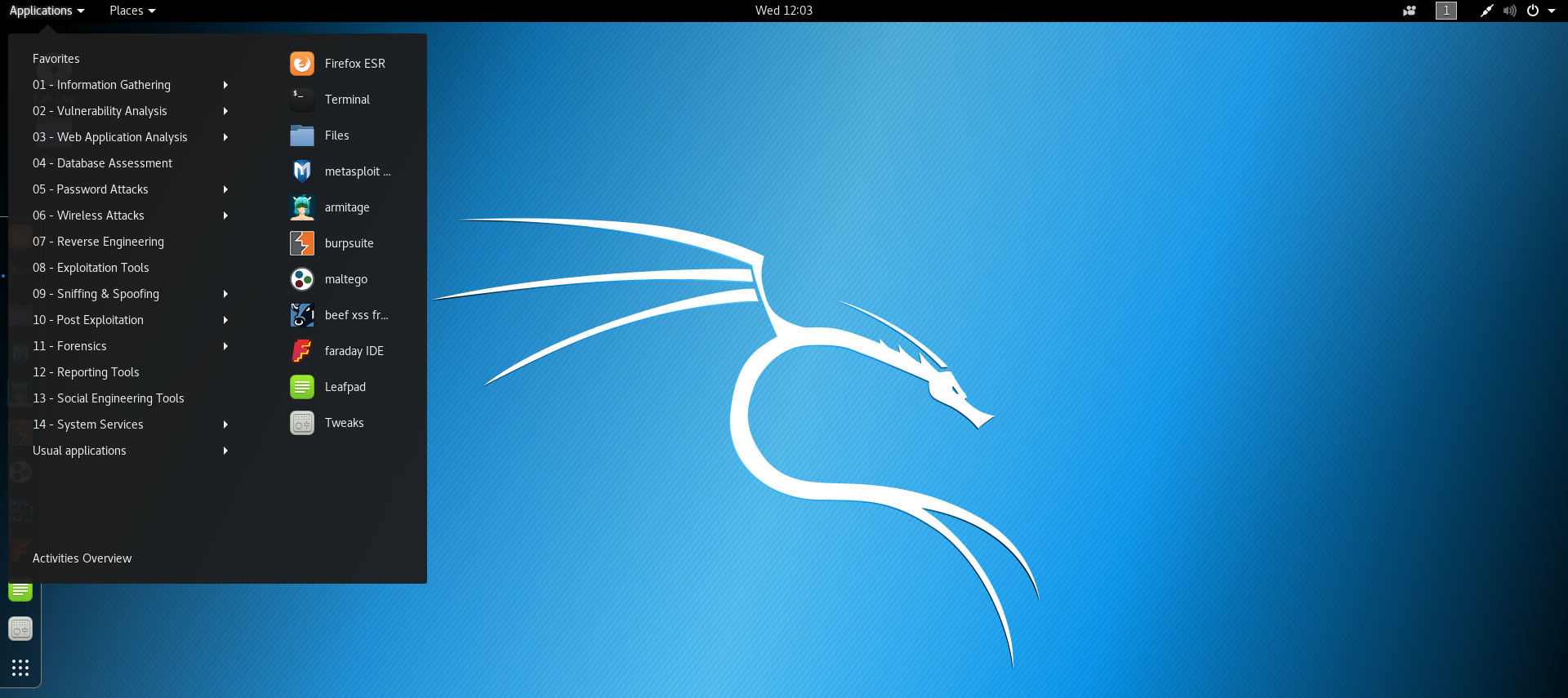
Kali Linux is a complete penetration testing distribution with tools assisting in all phases of the penetration testing lifecycle. Upon clicking the Applications menu, we can see all the available tools distributed across various categories as shown in the following screenshot:
Kali Linux comes with tons of useful tools and utilities. At times, we are required to make changes in the configuration files of these tools and utilities. All the tools and utilities are located in the /usr/bin folder as shown in the following screenshot:

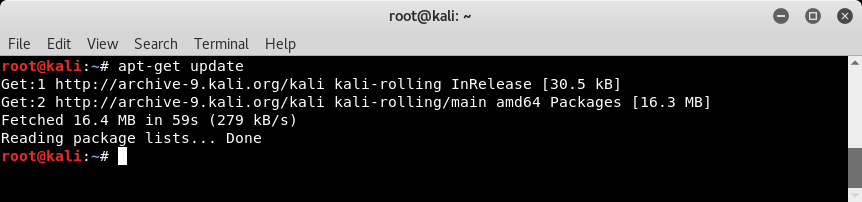
Kali Linux uses several online repositories to provide software installations and updates. However, these repository sources must be updated on a regular basis. This can be achieved using the apt-get update command as shown in the following screenshot:
Kali Linux also gets major build updates on a regular basis. In order to upgrade to the latest available build, the apt-get upgrade command can be used as shown in the following screenshot:

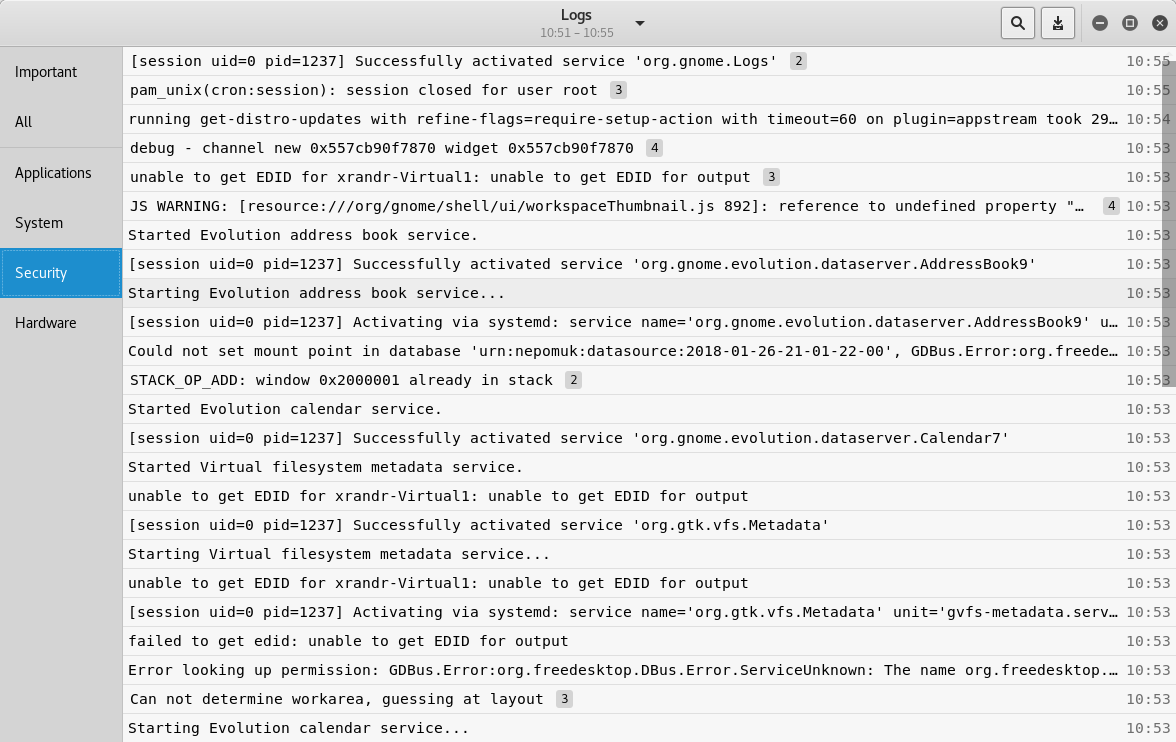
Kali Linux generates and stores various types of log, such as application, system, security, and hardware. These logs can be useful for debugging and tracing events. Logs can be viewed by opening the Logs application located at Applications | Usual Applications | Utilities | Logs, the result is shown in the following screenshot: