Once the open ports are identified on the discovered live hosts, we can perform vulnerability scanning. A vulnerability scan detects and identifies known issues of the software and tools installed on a host such as older version of software in use, vulnerable protocols enabled, and default passwords. It is difficult to perform this activity manually; hence this phase needs to be performed using automated tools that identify the open ports and try various exploits on the ports to identify whether the particular process/software using the port is vulnerable to the exploit based on the process. Some of the tools used to perform vulnerability scanning are Nessus, OpenVas, and Qualys.
The following screenshot shows a sample host scanned for vulnerabilities using OpenVas. You can see that the output shows the list of vulnerabilities the host is affected:
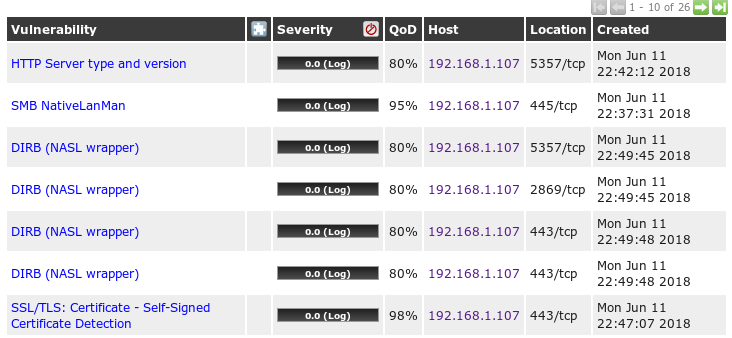
In this course, we will further introduce you to various recipes on how to scan a host for vulnerabilities using Nessus, and how to customize these scans to obtain specific and fewer false-positive results.
