Before we get into any technical details about privilege escalation, let's first get a basic understanding of privileges. The literal dictionary meaning of the word privilege is a special right, advantage, or immunity granted or available only to a particular person or group. When it comes to the computing world, privileges are something that are managed by the operating system. There might be ten users on a single system, but not all may have the same level of privileges. As per security best practices, the principle of least privilege is often followed. That means each user is assigned only those bare-minimum privileges that are absolutely essential to perform their tasks. This principle helps eliminate the possibility of the abuse of unnecessary, excessive privileges.
In the context of security assessments, privilege escalation becomes an important factor. Let's assume you have managed to successfully exploit a vulnerability in a remote system and got SSH access. However, your actions are restricted because the user you have compromised doesn't have high privileges. Now, you would certainly want to have the highest level of privileges so that you can explore various aspects of the compromised system. Privilege escalation would elevate privileges of a normal user to that of the user with the highest privileges. Once done, you have complete control over the compromised system.
To understand some basics of how privileges work, the following diagram shows various protection rings:
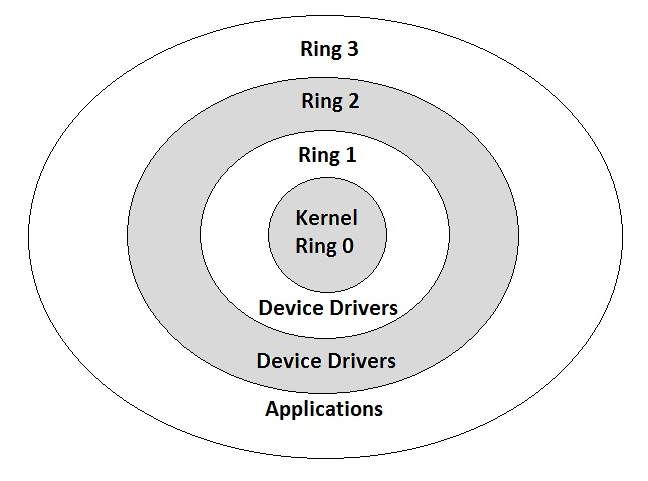
This diagram shows four rings:
- Ring 0: Belongs to the kernel of the operating system and has the highest privileges.
- Ring 1 and Ring 2: Mostly used by the device drivers that interface between the operating system and various hardware devices. These rings certainly have good privileges but less than Ring 0.
- Ring 3: Where most of our end applications operate. They have the lowest privileges.
So, in the case of privilege escalation, if you want to exploit an application vulnerability and get access to Ring 3, then you need to find a way to elevate privileges to higher rings. In a Windows environment, a user with the highest privileges is commonly referred to as an administrator, while in a Linux environment, a user with highest privileges is referred to as root.
