Lesson 13. Manage System Resources
Goals
![]() Explore and understand the macOS file layout
Explore and understand the macOS file layout
![]() Discover common system files, their location, and their purpose
Discover common system files, their location, and their purpose
![]() Manage font resources
Manage font resources
It is not unusual for a macOS system volume to contain well over 100,000 folders and 500,000 files just to support the operating system and its applications. As you can imagine, the number of items in a user’s home folder varies widely, depending on the user, but even the most frugal of users has thousands of items in the home folder. With this many files on hand, attempting to explore and fully comprehend the macOS file layout may seem like a monumental task. The contrary is true, however: the macOS system files are streamlined and organized in an easy-to-understand layout that is easy to manage and provides strong security.
This lesson focuses on the composition and organization of the files and folders that make up macOS. In this lesson, you, acting as an administrator, will use the file layout to strategically allocate resources. The exercises in this lesson specifically discuss management of font resources, because they are one of those most commonly modified by users. However, many of the same management techniques can be used for other system resources.
Reference 13.1 About macOS File Resources
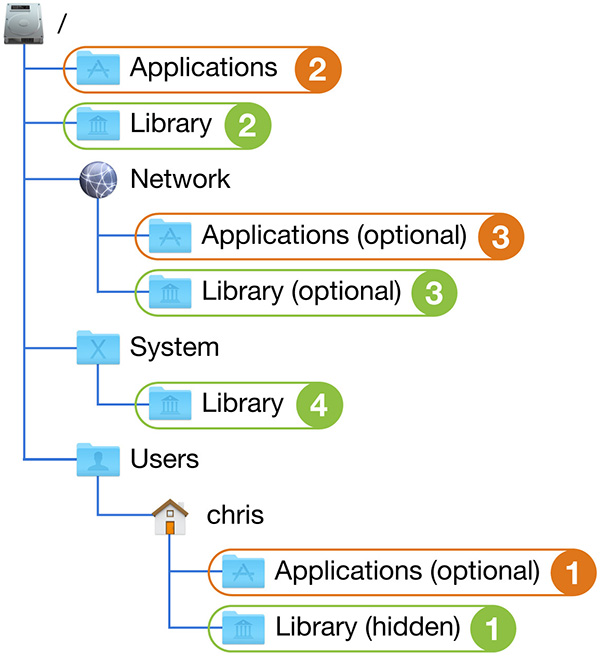
The macOS system layout is designed to strike a balance between ease of use and advanced functionality. For the basic user, looking at the root (beginning) of the file system from the Finder reveals only four default folders: Applications, Library, Users, and System.
The contents of these four folders represent all that most users, and many administrators, ever need to access. Yet when advanced users look at the system root from Terminal, they see many more items that the Finder would normally hide. Thus, the complexity and flexibility of a UNIX operating system remains accessible to those users who require it.

Here are descriptions of the default system root folders you see from the Finder:
![]() Applications—Often called the local Applications folder, this is the default location for applications available to all local users. Only administrator users can make changes to the contents of this folder.
Applications—Often called the local Applications folder, this is the default location for applications available to all local users. Only administrator users can make changes to the contents of this folder.
![]() Library—Often called the local Library folder, this is the default location for ancillary system and application resources available to all users of the system. Once again, only administrator users can make changes to the contents of this folder.
Library—Often called the local Library folder, this is the default location for ancillary system and application resources available to all users of the system. Once again, only administrator users can make changes to the contents of this folder.
![]() System—This folder contains resources required by the operating system for primary functionality. With System Integrity Protection (SIP) enabled by default in macOS, no user or process can make any changes to most of the content of the System folder. Although you can disable SIP, giving administrator users write access to the System folder, this is strongly discouraged because it introduces an unnecessary security risk. All properly created third-party macOS software, including hardware drivers, can function outside of the System folder. Details regarding SIP are covered later in this lesson.
System—This folder contains resources required by the operating system for primary functionality. With System Integrity Protection (SIP) enabled by default in macOS, no user or process can make any changes to most of the content of the System folder. Although you can disable SIP, giving administrator users write access to the System folder, this is strongly discouraged because it introduces an unnecessary security risk. All properly created third-party macOS software, including hardware drivers, can function outside of the System folder. Details regarding SIP are covered later in this lesson.
![]() Users—This is the default location for local user home folders. Lesson 6, “Manage User Home Folders,” covers this topic in greater detail.
Users—This is the default location for local user home folders. Lesson 6, “Manage User Home Folders,” covers this topic in greater detail.
About Library Resources
All macOS-specific system resources can be found in the various Library folders throughout the system volume. A system resource can be generally categorized as any resource that is not a general-use application or user file. That’s not to say that applications and user data can’t be found in the Library folders. On the contrary, the Library folder is designed to keep both user and system resources organized and separated from the items you use every day. This keeps the /Applications folder and user home folders free from system resource clutter.
Opening any of the Library folders reveals several dozen categories of items. It is not necessary to explore every possible Library item, but you should be familiar with several system resources:
![]() Application Support—This folder can be found in both the user and local Library folders. Any ancillary data needed by an application may end up in this folder. For example, it often contains help files or templates for an application. Once again, application resources are placed here to keep the /Applications folders tidy.
Application Support—This folder can be found in both the user and local Library folders. Any ancillary data needed by an application may end up in this folder. For example, it often contains help files or templates for an application. Once again, application resources are placed here to keep the /Applications folders tidy.
![]() Extensions—Also called kernel extensions, these items are found only in the system and local Library folders. Extensions are low-level drivers that attach themselves to the kernel, or core, of the operating system. Extensions provide driver support for hardware, networking, and peripherals. Extensions load and unload automatically, so there is little need to manage them, as is common in other operating systems. Extensions are covered in greater detail in Lesson 24, “Troubleshoot Peripherals.”
Extensions—Also called kernel extensions, these items are found only in the system and local Library folders. Extensions are low-level drivers that attach themselves to the kernel, or core, of the operating system. Extensions provide driver support for hardware, networking, and peripherals. Extensions load and unload automatically, so there is little need to manage them, as is common in other operating systems. Extensions are covered in greater detail in Lesson 24, “Troubleshoot Peripherals.”
![]() Fonts—Found in every Library folder, fonts are files that describe typefaces used for both screen display and printing. Font management is covered later in this lesson.
Fonts—Found in every Library folder, fonts are files that describe typefaces used for both screen display and printing. Font management is covered later in this lesson.
![]() Frameworks—Found in every Library folder, frameworks are repositories of shared code used among different parts of the operating system or applications. Frameworks are similar to extensions in that they load and unload automatically, so again, there is little need to manage these shared code resources. You can view your Mac computer’s currently loaded frameworks from the /Applications/Utilities/System Information application.
Frameworks—Found in every Library folder, frameworks are repositories of shared code used among different parts of the operating system or applications. Frameworks are similar to extensions in that they load and unload automatically, so again, there is little need to manage these shared code resources. You can view your Mac computer’s currently loaded frameworks from the /Applications/Utilities/System Information application.
![]() Keychains—Found in every Library folder, keychains are used to securely store sensitive information, including passwords, certificates, keys, Safari AutoFill information, and notes. Keychain technology is covered in Lesson 7, “Manage Security and Privacy.”
Keychains—Found in every Library folder, keychains are used to securely store sensitive information, including passwords, certificates, keys, Safari AutoFill information, and notes. Keychain technology is covered in Lesson 7, “Manage Security and Privacy.”
![]() LaunchDaemons and LaunchAgents—Both items can be found in the local and system Library folders, and LaunchAgents can also be found in users’ Library folders. These launch items are used to define processes that start automatically via the launchd process. macOS uses many background processes, which are all started by launchd. Further, every single process is a child of the launchd process. LaunchAgents are for processes that need to start up only when a user is logged in, whereas LaunchDaemons are used to start processes that always run in the background, even when no users are logged in. More about launchd can be found in Lesson 26, “Troubleshoot Startup and System Issues.”
LaunchDaemons and LaunchAgents—Both items can be found in the local and system Library folders, and LaunchAgents can also be found in users’ Library folders. These launch items are used to define processes that start automatically via the launchd process. macOS uses many background processes, which are all started by launchd. Further, every single process is a child of the launchd process. LaunchAgents are for processes that need to start up only when a user is logged in, whereas LaunchDaemons are used to start processes that always run in the background, even when no users are logged in. More about launchd can be found in Lesson 26, “Troubleshoot Startup and System Issues.”
![]() Logs—Many system processes and applications archive progress or error messages to log files. Log files can be found in every local Library folder and also the /var/log folder. Technically, an application or process can save log files to any writable location, but the previously mentioned folders are the defaults. You can view log files using the /Applications/Utilities/Console application.
Logs—Many system processes and applications archive progress or error messages to log files. Log files can be found in every local Library folder and also the /var/log folder. Technically, an application or process can save log files to any writable location, but the previously mentioned folders are the defaults. You can view log files using the /Applications/Utilities/Console application.
![]() PreferencePanes—PreferencePanes can be found in any Library folder. These items are used by the System Preferences application to provide interfaces for system configuration. Using System Preferences is covered in Lesson 2, “Set Up and Configure macOS.”
PreferencePanes—PreferencePanes can be found in any Library folder. These items are used by the System Preferences application to provide interfaces for system configuration. Using System Preferences is covered in Lesson 2, “Set Up and Configure macOS.”
![]() Preferences—Preferences, found in both local and user libraries, are used to store system and application configuration settings. In other words, every time you configure a setting for any application or system function, it is saved to a preference file. Because preferences play such a critical role in system functionality, they are often the cause of software problems. Troubleshooting preference files is covered in Lesson 18, “Manage and Troubleshoot Applications.”
Preferences—Preferences, found in both local and user libraries, are used to store system and application configuration settings. In other words, every time you configure a setting for any application or system function, it is saved to a preference file. Because preferences play such a critical role in system functionality, they are often the cause of software problems. Troubleshooting preference files is covered in Lesson 18, “Manage and Troubleshoot Applications.”
![]() Startup Items—Found in only the local and system Library folders, these are precursors to LaunchAgents and LaunchDaemons. macOS no longer supports these legacy Startup Items. In fact, you will have Startup Items only if you’ve installed third-party software that has not been updated to work with macOS Sierra.
Startup Items—Found in only the local and system Library folders, these are precursors to LaunchAgents and LaunchDaemons. macOS no longer supports these legacy Startup Items. In fact, you will have Startup Items only if you’ve installed third-party software that has not been updated to work with macOS Sierra.
About Resource Hierarchy
Library folders, and thus system resources, are located in each of the four domain areas: user, local, network, and system. Segregating resources into four domains provides increased administrative flexibility, resource security, and system reliability. Resource domains allow for administrative flexibility, because you can choose to allocate certain resources to all users or just specific users. Using resource domains is also more secure, because standard users can add resources only to their own home folder and cannot access other users’ resources. In addition, resource domains are more reliable, because in most cases you don’t have to make changes to the core system functionality to provide more services.
Tip
The quickest way to reveal a user’s Library folder is to manually go to the folder in the Finder. While holding down the Option key, choose Go > Library to reveal the hidden folder. You can learn more about hidden items in Lesson 12, “Use Hidden Items, Shortcuts, and File Archives.”
The four system resource domains are, in order:
![]() User—Each user has his or her own Library folder in the home folder for resources. When resources are placed here, only the user has access to them. The user’s Library folder is hidden by default to prevent users from accidentally making changes that could be detrimental. However, you can still find many thousands of items in this folder, because many applications and processes continue to rely on this location for resources. Also, users can have their own Applications folder within their home folder, provided they create the folder and name it, precisely, Applications.
User—Each user has his or her own Library folder in the home folder for resources. When resources are placed here, only the user has access to them. The user’s Library folder is hidden by default to prevent users from accidentally making changes that could be detrimental. However, you can still find many thousands of items in this folder, because many applications and processes continue to rely on this location for resources. Also, users can have their own Applications folder within their home folder, provided they create the folder and name it, precisely, Applications.
![]() Local—Both the root Applications and root Library folders are part of the local resource domain. This is why they are known as the local Applications and local Library folders. Any resources placed in these two folders are available to all local user accounts. By default, only administrator users can make changes to local resources.
Local—Both the root Applications and root Library folders are part of the local resource domain. This is why they are known as the local Applications and local Library folders. Any resources placed in these two folders are available to all local user accounts. By default, only administrator users can make changes to local resources.
![]() Network—macOS can access system resources in a Library folder and applications in an Applications folder residing on a network file share. Administrators must configure an automounted share to enable the Network resource domain. Configuring automounted shares is beyond the scope of this guide.
Network—macOS can access system resources in a Library folder and applications in an Applications folder residing on a network file share. Administrators must configure an automounted share to enable the Network resource domain. Configuring automounted shares is beyond the scope of this guide.
![]() System—Finally, the system domain encompasses all the items necessary to provide core system functionality. This includes an application folder located at /System /Library/CoreServices. Many hidden items at the root of the system volume also make up the system resource domain, but the only one you see in the Finder is the /System /Library folder. Again, with SIP in Sierra, no user or process can modify most of the System folder, with the exception of /System/Library/User Template.
System—Finally, the system domain encompasses all the items necessary to provide core system functionality. This includes an application folder located at /System /Library/CoreServices. Many hidden items at the root of the system volume also make up the system resource domain, but the only one you see in the Finder is the /System /Library folder. Again, with SIP in Sierra, no user or process can modify most of the System folder, with the exception of /System/Library/User Template.
With four different domains containing resources, a strong likelihood exists for overlap in resources, meaning there may be multiple copies of similar resources available to the system and user at any given time. The system is designed to handle this by searching for resources from the most specific (those in the user domain) to the least specific (those in the system domain). The following graphic represents the order in which resource contention is resolved from the user’s home folder (1) to the System folder (4).
If multiple similar resources are discovered, the system uses the resource most specific to the user. For example, if multiple versions of the font Times New Roman are found—one in the local Library and one in the user’s Library—the system uses the copy of the font in the user’s Library. In other words, resources in the user’s home folder take first priority, thus trumping all other resource locations.
About Application Sandbox Containers
Application sandbox containers add a bit more complexity to file-system organization but greatly enhance the security of running applications. Sandboxed applications are designed in such a way that they are allowed access only to the specific items they need to function. Because application sandboxing is a recent addition to macOS, many legacy applications do not take advantage of this technology. However, most applications built into macOS and all applications from the Mac App Store are created as sandboxed applications.
As the term sandbox implies, these applications are allowed to “play” only in their specific area. These areas are special folders that are referred to as containers. The system manages the content of these containers to ensure that an application is not allowed access to any other items in the file system. In other words, sandboxed applications are more secure because they are allowed access only to the items in their own containers.
Users can also allow a sandboxed application access to other files outside the container, but they must do so by opening the item in the application. In other words, the specific action of a user opening a document outside of an application’s container is the only way a sandboxed application is allowed access outside of its container.
Application containers can be found in the user’s Library folder. Specifically, the ~/Library/Containers folder contains individual application containers. When a sandboxed application starts up the first time, the system automatically creates a container folder for the application, named with its bundle identifier. The bundle identifier is used for development purposes to identify an application by its creator and application title. For example, the container folder for Notes is ~/Library/Containers/com.apple.Notes.
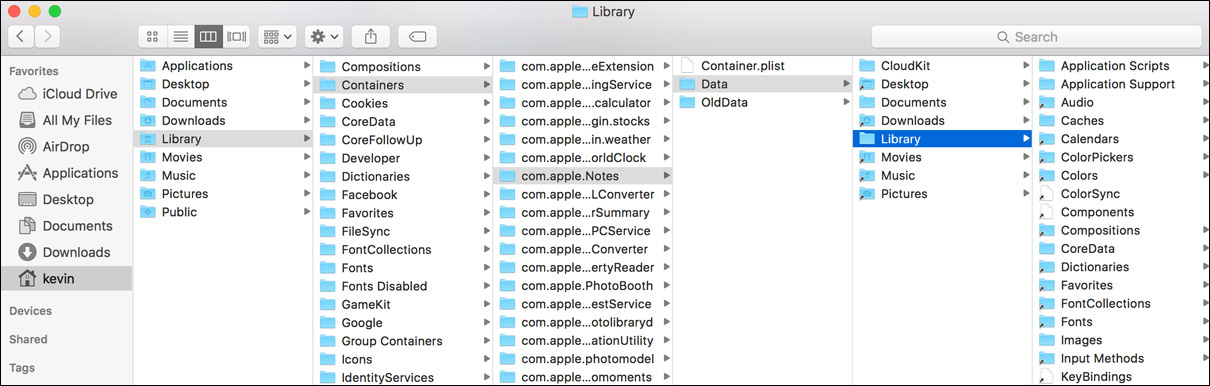
The root content of an application container is a property list file containing application information, a Data folder, and possibly an OldData folder. The Data folder is the application’s current active container. Any OldData folder you might find contains previously used application items. The content of the Data folder mostly mimics the user’s home folder, but with one key distinction: it contains only the items that the application is allowed to access. Thus, in the Data folder you will find only items specific to the application’s function or items the user has explicitly opened in the application.
Items created and managed by the sandboxed application are the only original items in the container Data folder. As covered previously in this lesson, common resource folders used by an application include Application Support and Preferences. If the user has enabled iCloud Drive, you may also find a CloudKit folder for maintaining items stored in iCloud.
Items that originated from other applications or a user’s file-opening action are represented as symbolic links that point to the original item outside of the container. The system automatically creates these symbolic links when the user opens an item in the sandboxed application. By representing external items this way, an original item can stay where the user wants it while also being accessible to a sandboxed application that can see only its own container.
About Application Group Containers
Although a user can explicitly allow sandboxed applications to access specific files beyond the application’s container, the secure design of sandboxing prevents applications from doing this automatically for themselves. As you can imagine, this keeps applications from automatically taking advantage of each other’s resources. Thus, in order to facilitate sharing application resources automatically, developers of sandboxed applications can request that the system create a shared application group container.
Application group containers can also be found in the user’s Library folder. Specifically, the ~/Library/Group Containers folder contains shared application containers. When a sandboxed application starts up the first time and requests access to share application resources, the system automatically creates a group container folder for the application, named with its bundle identifier.
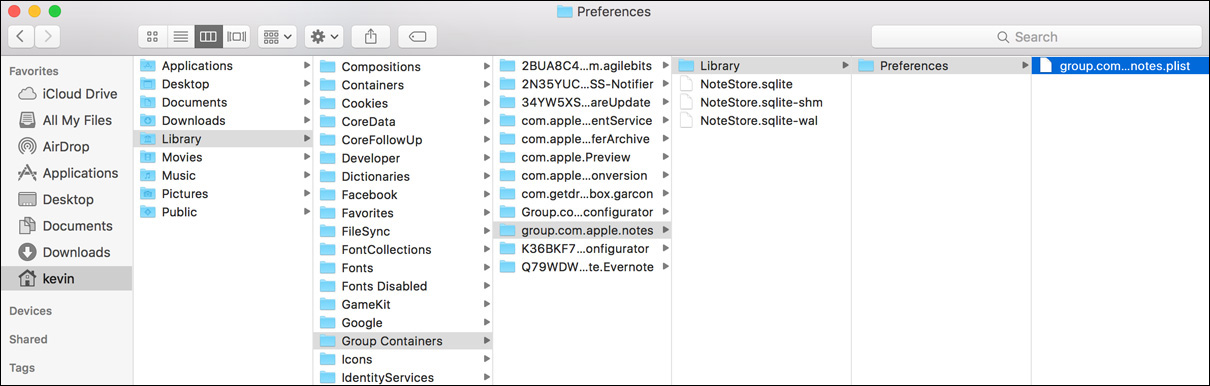
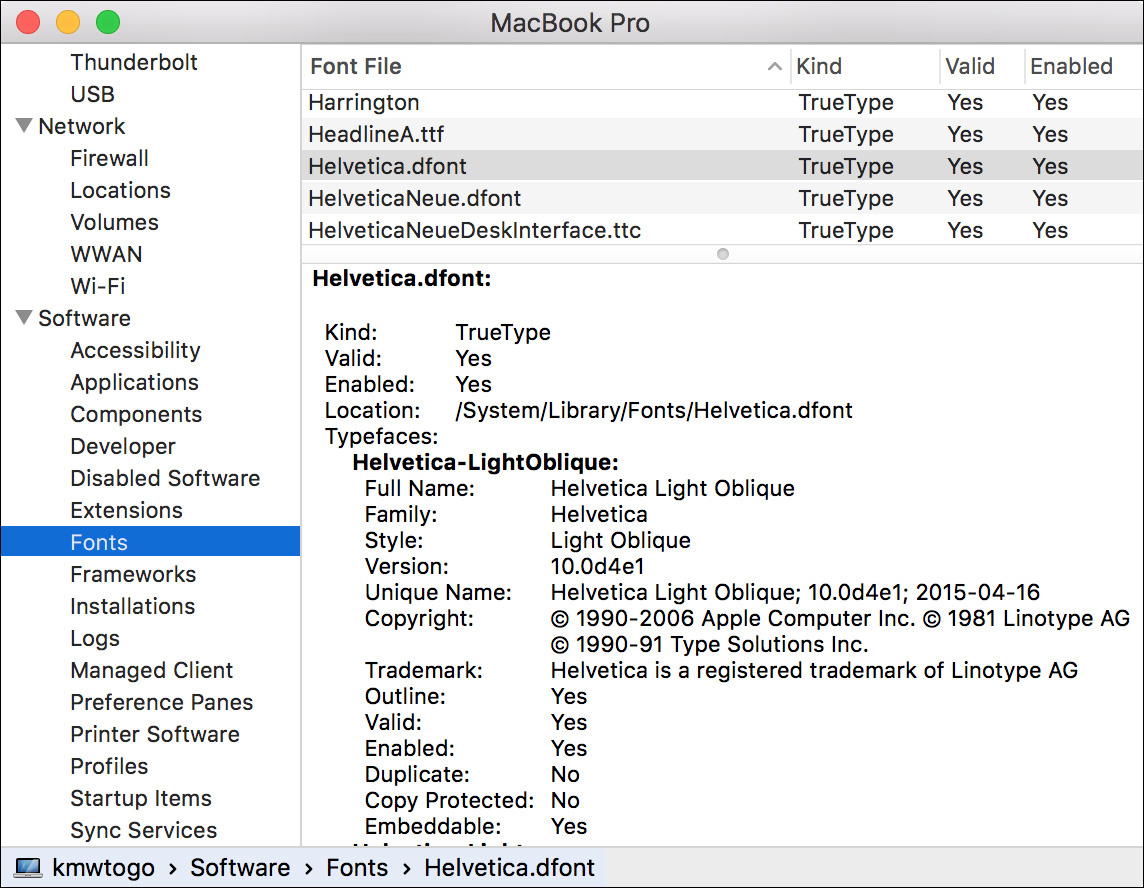
Unlike application sandbox containers that simulate an entire user’s home folder, application group containers hold only items to be shared between applications. Again using the Notes application as an example, in the previous screenshot you can see the NoteStore database and notes property list file. In this specific instance, the Notes data is shared so that other applications can access user note entries. The system controls access to this via a security mechanism to ensure that only Apple-verified processes can access the user’s Notes database.
Troubleshoot System Resources
System resource issues are rare, and they are generally easy to identify. You may occasionally see an error message calling out an issue with a specific item, but you may also experience a situation where the item appears to be missing. In some cases, the system resource in question may actually be missing, but many times the system ignores a system resource if it determines that the resource is in some way corrupted. The solution for both of these situations is to replace the missing or suspect item with a known working copy.
When troubleshooting system resources, remember to heed the resource domain hierarchy. Using fonts as an example, you may have loaded a specific version of a font in the local Library, as required by your workflow to operate properly. In spite of this, a user may have loaded another version of the same font in his or her home folder. In this case, the system loads the user’s font and ignores the font you installed. Therefore, this user may experience workflow problems even though it appears that he or she is using the correct font.
Tip
If fonts are missing from within applications but appear to be properly installed, remember to check Font Book—the font may be temporarily disabled. Font Book is covered later in this lesson.
Logging in with another account on the Mac is always a quick way to determine whether the problem is in the user’s home folder. You can also use /Applications/Utilities /System Information to list active system resources. System Information always shows the file path of the loaded system resources, so it’s easy to spot resources that are loading from the user’s Library.
Reference 13.2 About System Integrity Protection
OS X El Capitan 10.11 and later releases include System Integrity Protection (SIP) to further enhance the security of Mac computers. In a nutshell, SIP prevents improper modification of core macOS system items and processes. SIP does this by acting as a meta-permission that prevents write access to system items and processes.
Historically, UNIX systems like macOS have allowed users and processes with root (or System Administrator) access to bypass system permissions. Thus, as covered in Lesson 11, “Manage Permissions and Sharing,” any user or process with root access could essentially modify any item on the system volume. Further, processes running as root are normally allowed to modify the memory stores of any running process.
As a default on macOS, any administrator can install software that can potentially request root access. Because many users don’t think twice before authenticating an installer or update, an administrator user could easily install malware that could take advantage of root access. This is why, from a security perspective, root access is a significant risk factor.
However, with SIP enabled by default on macOS, users and processes with root are not allowed to modify core system items and processes. Therefore, with SIP enabled, macOS itself is secured from malicious or malformed software that may attempt to breach security mechanisms by modifying system items.
System items protected by SIP include the following folders: /System, /bin, /sbin, and /usr. Almost everything inside these folders is protected, with a few exceptions. The two most prominent exceptions are two folders that are occasionally used by administrators for local customization: /System/Library/User Template and /usr/local. Core applications included with macOS, like System Preferences, are also protected by SIP. This is why repairing system permissions is not necessary with OS X El Capitan or later.
More Info
The full list of items protected by SIP can be found in the following text configuration file: /System/Library/Sandbox/rootless.conf. The file itself is obviously protected by SIP as well.
Verify System Integrity Protection
You can test SIP yourself by attempting to modify the permissions of one of these protected folders. For example, the following screenshot shows an administrator attempting to modify the permissions of the /System folder. Note in the screenshot that the security lock icon is open, indicating that this administrator user should have rights to modify the item’s permissions, but SIP intervenes.
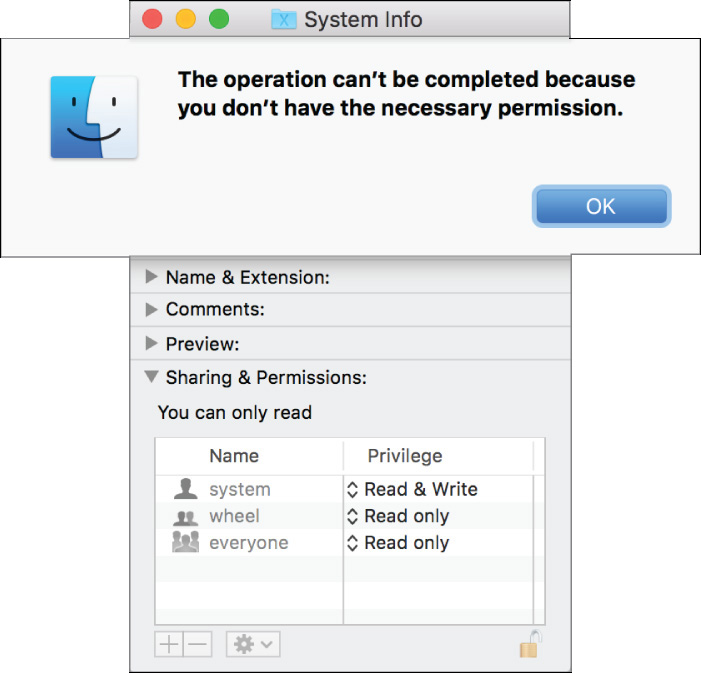
Bypass System Integrity Protection
Because SIP introduces significant new system behavior, older third-party software may not be compatible with this change. Specifically, any software that relies on non-Apple items installed or stored in any of the SIP-protected locations will likely be nonfunctional in macOS Sierra. In fact, during the upgrade to El Capitan or macOS Sierra, the installer will remove any non-Apple items from the SIP-protected locations. Specifically, the items are moved to /Library/SystemMigration/History/Migration-UUID/QuarantineRoot/, where “UUID” is a unique identifier number.
Older peripheral and printer driver software is the most likely to be impacted by SIP. If you discover that a third-party product is impeded by SIP, the best solution is to contact the developer to provide a version compatible with macOS Sierra. If the developer can’t get his or her act together in a timely fashion, then you can bypass SIP, but this approach is not recommended or trivial.
SIP can be temporarily bypassed by starting from another, non-SIP-protected system; this includes macOS Recovery systems and systems prior to OS X El Capitan 10.11. You could also place a macOS Sierra system in target disk mode and then connect to another Mac running a previous version of OS X. These methods all allow you to modify a non-SIP-protected system volume. After you’ve made your changes, restart the Mac back to the macOS Sierra system and your changes should remain.
You can also permanently disable SIP by using the csrutil command when started from macOS Recovery. When SIP is disabled via this command, the setting is saved to the Mac’s firmware. Thus, any SIP-compatible system running on this modified Mac will have SIP disabled. Obviously, returning to macOS Recovery to reenable SIP should be attempted as soon as possible.
Note
Setting a computer firmware password, as detailed in Lesson 8, “Manage Password Changes,” can prevent unauthorized bypassing of the Mac computer’s system volume, thus ensuring an SIP-protected-system remains protected by the SIP rules.
Reference 13.3 Manage Font Resources
An excellent way to experience the system resource domain hierarchy is by managing fonts. macOS has advanced font-management technology that enables an unlimited number of fonts using nearly any font type, including bitmap, TrueType, OpenType, and all PostScript fonts.
As mentioned, fonts are installed in the various Font folders located in the Library folders throughout the system. A user can manually install fonts by dragging them into the ~/Library/Fonts folder. Further, administrators can install fonts for all users by dragging them into the /Library/Fonts folder. This flexible font system allows administrators to better control font usage. For example, a font vendor’s licensing model may only grant specific access for an individual user.
More Info
Every Mac system includes a wealth of high-quality fonts for many different languages. For the most recent list of fonts included with macOS, see Apple Support article HT206872, “Fonts included with macOS Sierra.”
Install Fonts via Font Book
macOS does include a rather nice font-management tool, /Applications/Font Book, which automatically installs fonts for you. Font Book can also be used to organize fonts into more manageable collections, enable or disable fonts to simplify font lists, and resolve duplicate fonts.
Note
Third-party font-management tools, such as Extensis Suitcase Fusion or Universal Type Server, interrupt Font Book and take over font management for the system.
By default, when a user double-clicks a font in the Finder, Font Book opens and displays a preview of the font. When the user clicks the Install Font button, Font Book automatically copies the font into the Fonts folder in the user’s Library folder.
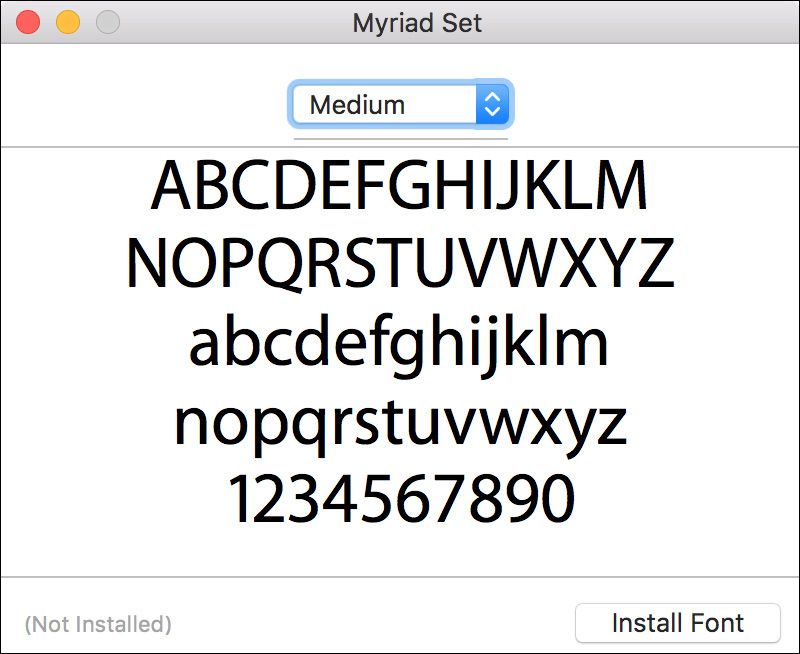
Font Book, by default, automatically validates a font before installing and enabling it. This helps prevent font problems by making sure the font file isn’t compromised. Thus, installing fonts via Font Book is favored over manual installation via the Finder.
When a new font is installed, the Font Book main window appears with the font preview at right. Manually opening Font Book also opens the main window. To preview any currently installed font, click it in the list of fonts. If you want to install additional fonts without leaving the Font Book application, you can do so by clicking the Add (+) button in the Font Book toolbar.
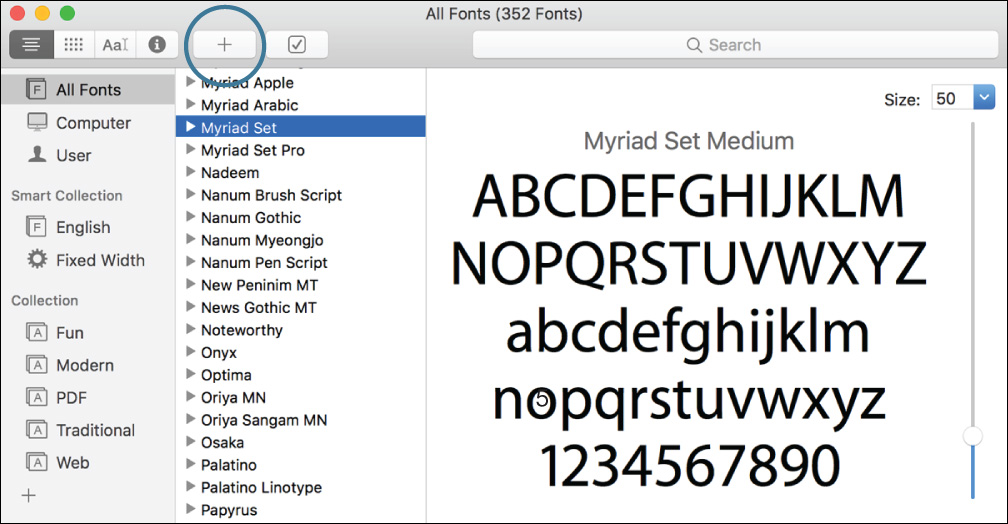
The previous screenshot shows a computer with additional nonsystem fonts installed. As you can see at the top of the first column in Font Book, you can sort by All Fonts, Computer, or User fonts. With Font Book open, you can adjust the default install location for fonts by choosing Font Book > Preferences. If you are an administrator user, you can choose to install fonts to the local Library folder by choosing Computer from the pop-up menu. Close the Font Book Preferences dialog after you have made your selections.
Note
You may need to restart some applications to take advantage of recently added fonts.
Note
You will be prompted to authenticate as an administrator in order to install fonts for all users on the computer.
Disable Fonts via Font Book
If you, or the application you’re using, have difficulties choosing fonts from a large list, you can temporarily disable fonts within Font Book by selecting a font and then clicking the Enable/Disable button (it appears as a selected or deselected checkbox) in the toolbar. Disabled fonts appear dimmed in the font list, with “Off” shown next to their name. To enable the font, select it again and click the same checkbox button at the bottom of the font list.
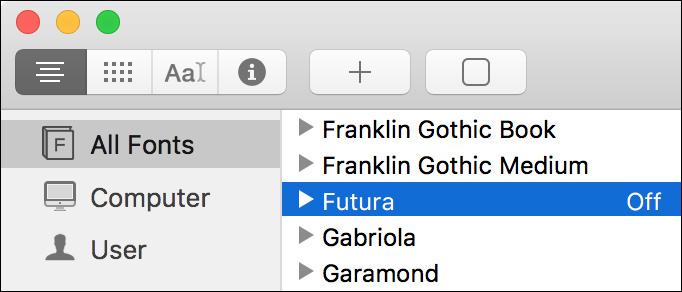
Tip
In Font Book you can also enable, disable, or remove fonts by selecting them from the list and then using secondary-click (Control-click) to reveal a pop-up menu, allowing you to manage the selected font(s).
Fonts that have multiple copies on your Mac show a small dot next to their name in the font list. You can automatically disable duplicate fonts with Font Book by choosing Edit > Look for Enabled Duplicates.
If you feel the need to remove a font, select it from the font list and then press Delete. A summary dialog appears, reminding you that continuing will move the selected fonts to the Trash. If you are sure this is what you want to do, click Remove. Remember, however, that you can always disable a font instead of deleting it entirely.
Note
With SIP enabled, you can’t remove system fonts required by macOS.
Resolve Font Issues via Font Book
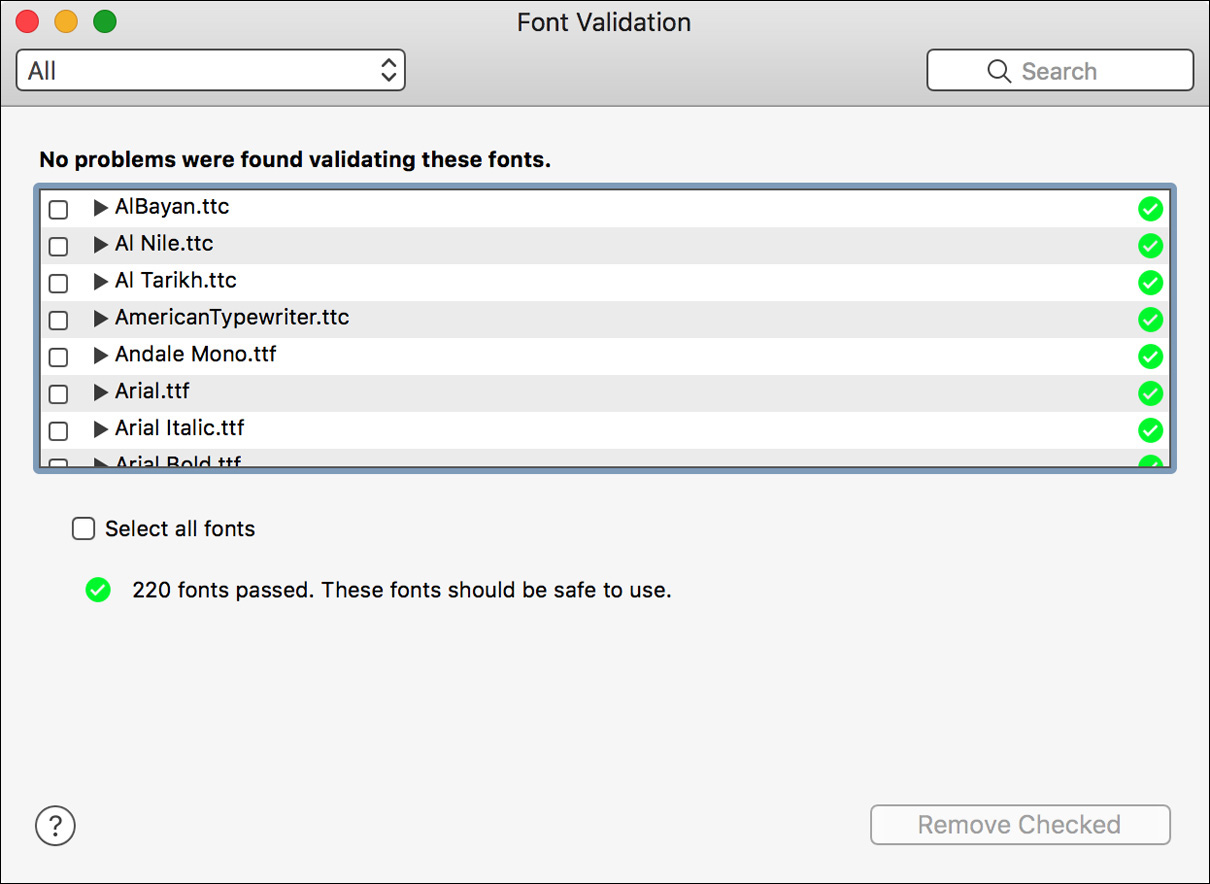
If you’re having font issues, you can identify problem fonts by forcing Font Book to revalidate all the fonts on your Mac. To do this, select a single font in the Font list, and then press Command-A to select all the fonts. Choose File > Validate Fonts to start the validation process.
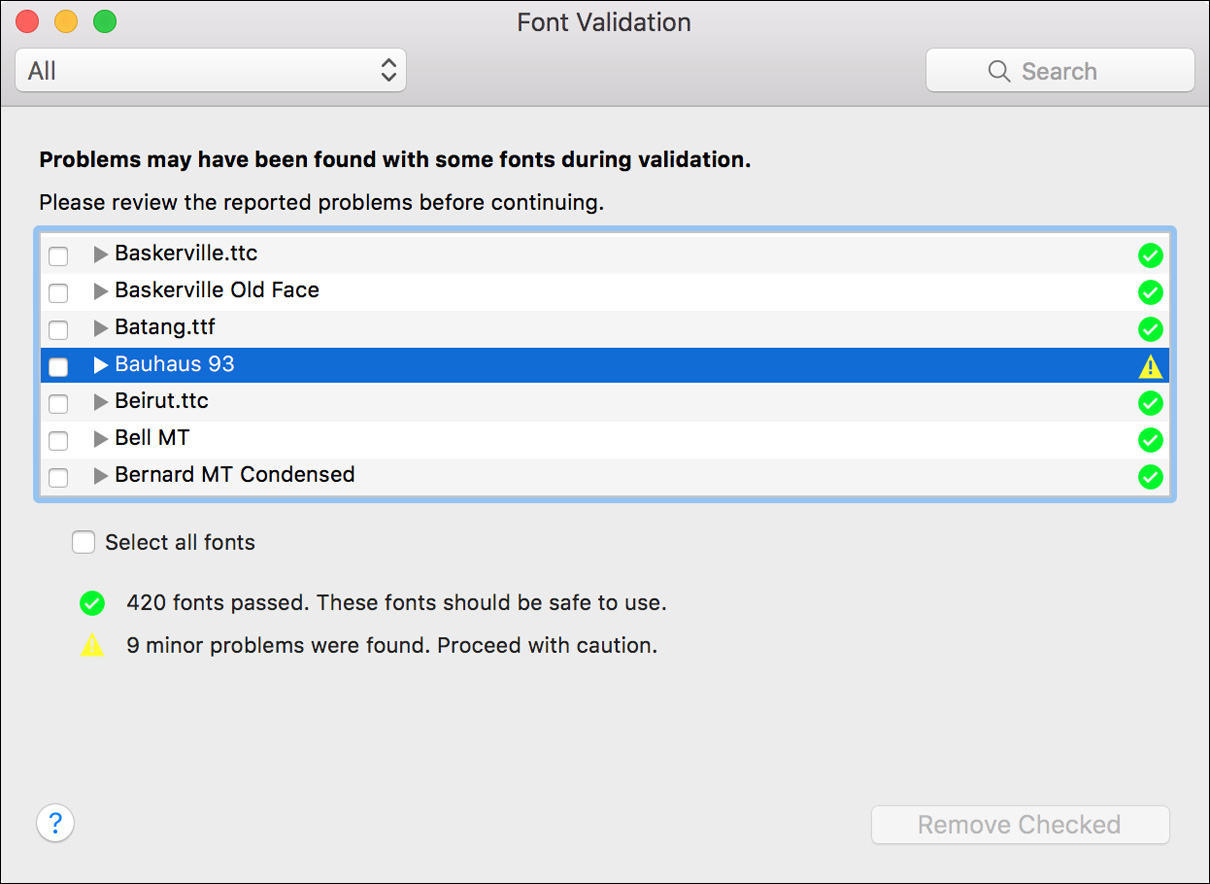
The Font Validation window opens and scans all the selected fonts. This window shows any problem font with a status indicator (exclamation mark icon) to the right of the font’s name. To view details about a font issue, click the disclosure triangle to the left of the font name. To remove a problem font, select the checkbox next to its name and then click the Remove Checked button.
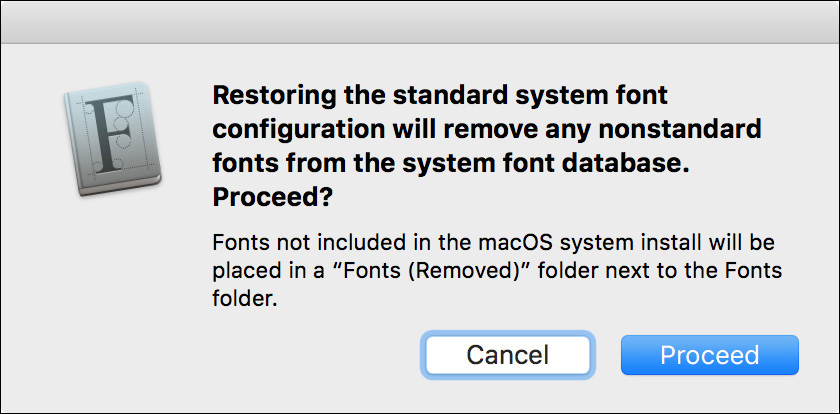
If you’re still having problems with fonts, a final option in Font Book is to restore all the system fonts to the defaults for macOS. To do this, choose File > Restore Standard Fonts. A dialog appears, verifying your choice. Click Proceed to remove third-party fonts from macOS.
Exercise 13.1 Manage Font Resources
![]() Prerequisite
Prerequisite
![]() You must have created the Local Admin (Exercise 2.1, “Configure a New macOS System for Exercises,” or Exercise 2.2, “Configure an Existing macOS System for Exercises”) and Chris Johnson (Exercise 5.1, “Create a Standard User Account”) accounts.
You must have created the Local Admin (Exercise 2.1, “Configure a New macOS System for Exercises,” or Exercise 2.2, “Configure an Existing macOS System for Exercises”) and Chris Johnson (Exercise 5.1, “Create a Standard User Account”) accounts.
In this exercise, you will remove a font from /Library/Fonts, where it is available to all users, and install it in a single user’s Fonts folder.
Remove a Font
You can use Font Book to watch what happens when you move a font to the Trash.
1 Verify that no users have fast user switching sessions active. If any users other than Chris are logged in, log them out.
2 If necessary, log in as Chris Johnson.
3 Open the Font Book application, which is located in the /Applications folder.
4 Locate Andale Mono in the Font column.
5 In the Finder, navigate to the folder /Library/Fonts. If Macintosh HD is not displayed on Chris’s desktop, you can find it in the Computer view, available by choosing Go menu > Computer (or pressing Command-Shift-C and then opening Macintosh HD > Library > Fonts).
6 To verify your location, choose View menu > Show Path Bar.
Make sure the path bar at the bottom of the window matches the following screenshot (although the rest may not match unless you are in column view):
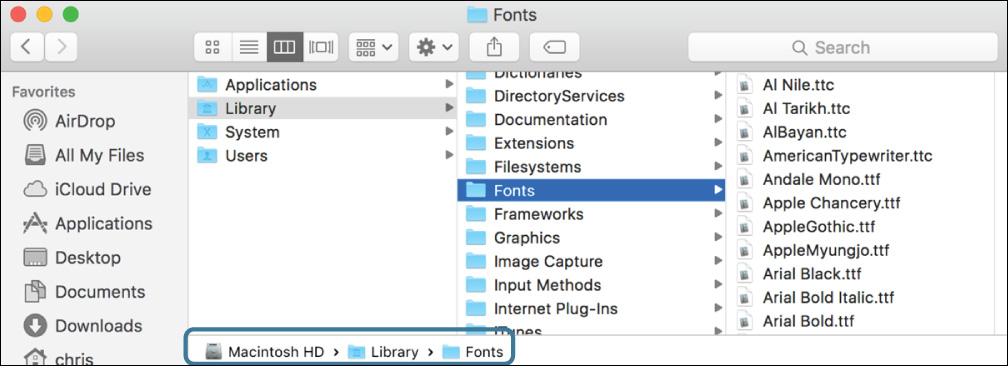
The path bar includes the volume name in the path, so the unix path /Library/Fonts is displayed as “Macintosh HD > Library > Fonts.” The fonts in this folder are available to all users on the system.
7 Locate the file Andale Mono.ttf.
8 Drag Andale Mono.ttf to the desktop. As you drag, a cursor with a green badge with a plus sign on it appears attached to the pointer. This indicates that the file will be copied rather than moved.
This will be your backup copy of the Andale Mono font.
9 Move the original Andale Mono.ttf file from /Library/Fonts to the Trash. To do so, you have to authenticate as Local Admin (password: ladmin, or whatever you chose when you created the account).
10 Click the Font Book window to make it the active application.
The Andale Mono font is no longer listed in the Font Book window. Font Book shows a real-time display of all the fonts in the system search path.
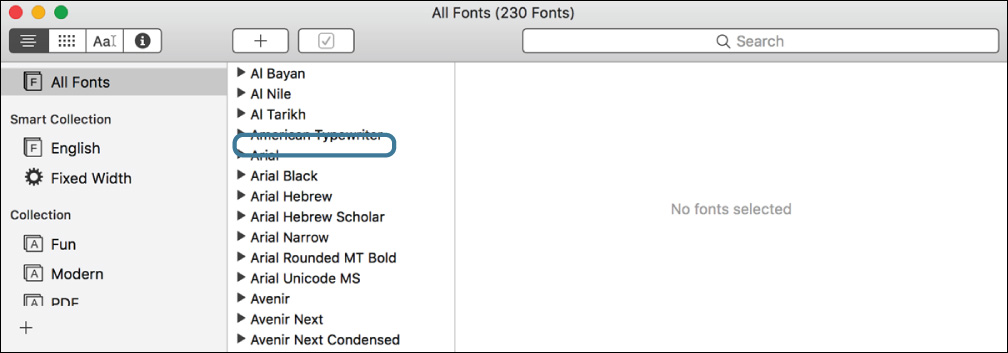
Add a Font for Only One User
You can use Font Book to install a font that only one user of the computer can use.
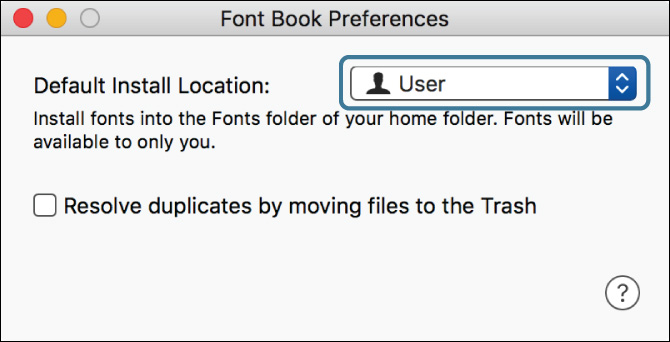
1 In the Font Book application, choose Font Book menu > Preferences (Command-Comma).
2 Ensure that Default Install Location is set to User.
3 Close Font Book Preferences.
4 Switch to the Finder, and double-click Andale Mono.ttf on the desktop.
This opens Andale Mono.ttf in Font Book, which shows a preview of the font and gives you the option to install it.
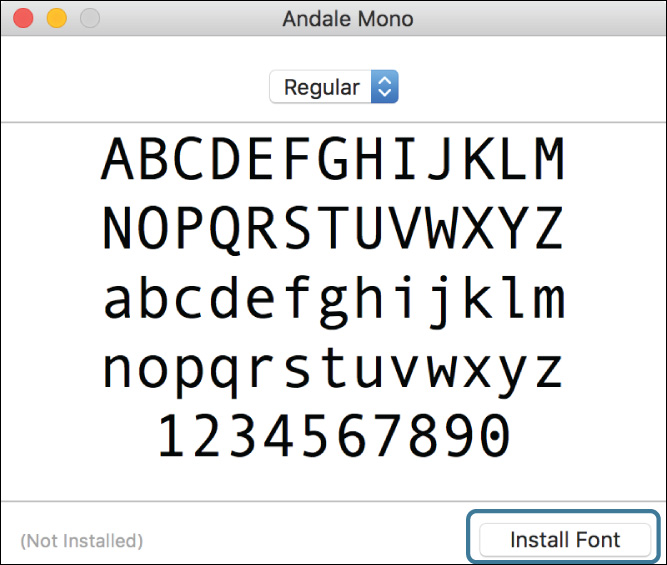
5 Click Install Font.
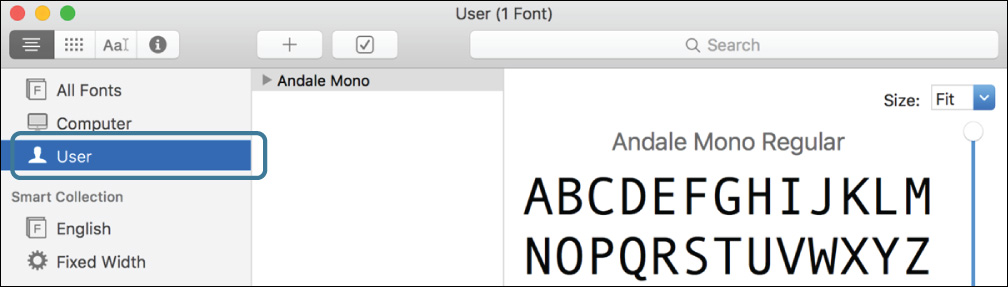
6 If necessary, select User from the sidebar.
Andale Mono is the only font installed in Chris’s user account.
7 Select All Fonts from the sidebar.
Since this shows all available fonts, including those installed just for the current user as well as those installed computerwide, Andale Mono is back in the list.
8 Control-click on Andale Mono, and choose “Show in Finder” from the shortcut menu.
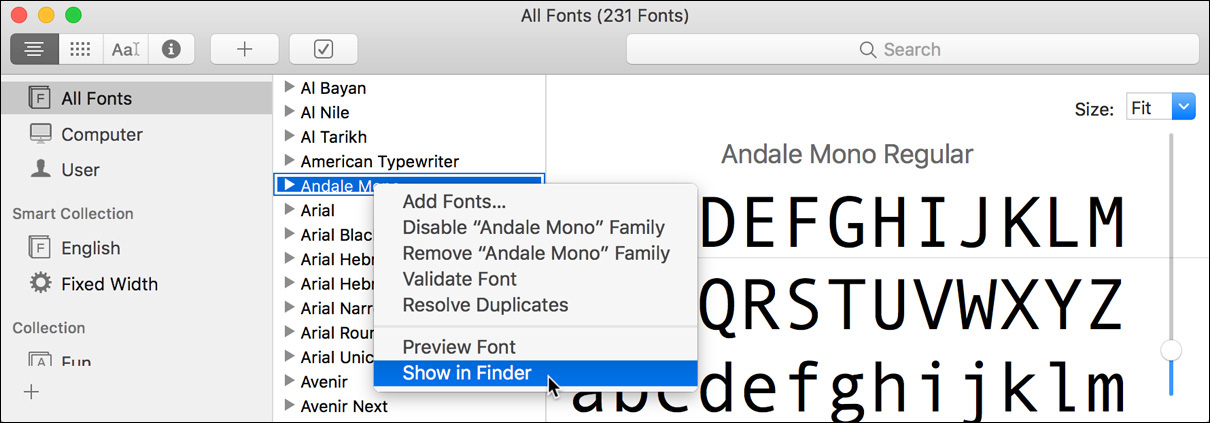
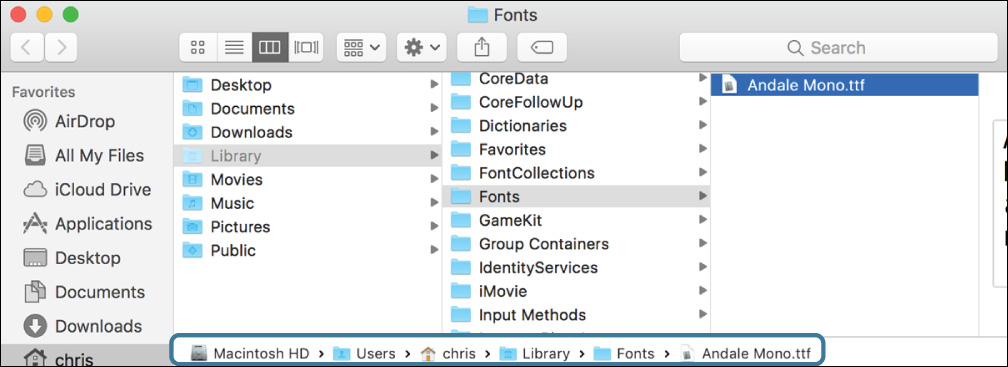
The Finder opens a window displaying the font file. Its path bar shows that it is located in the Fonts folder in Chris’s user library, variously referred to as ~/Library/Fonts, /Users/chris/Library/Fonts, and Macintosh HD > Users > chris > Library > Fonts. It is the only font installed there.
Confirm the Font Is Unavailable to Other Users
If you log in as a different user, even an administrator, you don’t have access to the fonts in Chris’s Fonts folder.
1 Use fast user switching to switch to the Local Admin account.
2 Open the Font Book application, and look for the Andale Mono font.
Notice that Andale Mono is not visible in Font Book for the Local Admin account. At this time, you could add Andale Mono to this account, just as you added it to Chris’s account earlier. You would have to copy the font file to a location that Local Admin can access.
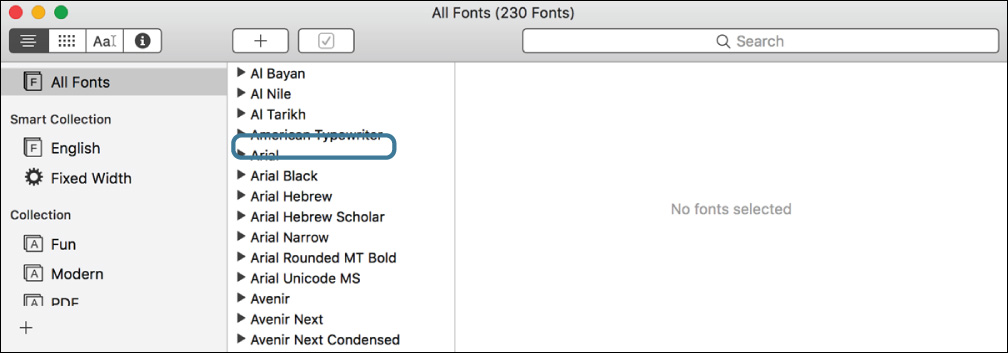
3 Quit Font Book.
Validate Fonts
Since you have changed your font configuration, you will use Font Book to check your new setup.
1 Use fast user switching to switch back in to the Chris Johnson account.
2 In the Font Book window, select All Fonts in the sidebar, click any font in the Font column, and then press Command-A to select all the fonts.
3 Choose File menu > Validate Fonts.
Font Book reads and validates all the font files, checking for any corruption.
4 When the validation scan finishes, quit Font Book.
5 Log out as Chris Johnson.
Test System Integrity Protection
Unlike the user and local libraries, the system library cannot be modified, even by using administrator rights.
1 Log back in as Local Admin.
2 In the Finder, navigate to /System/Library/Fonts.
3 Find the file Apple Color Emoji.ttc, and drag it to the Trash.
If you can’t find this file, make sure you’re in the correct Library/Fonts folder. You need to be in the one in the System folder for this part of the exercise.
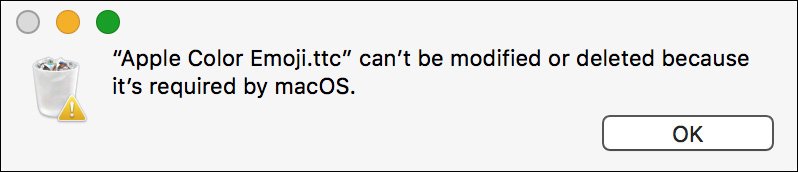
A dialog appears indicating that the file cannot be modified or deleted.
4 With Apple Color Emoji.ttf selected, choose File menu > Get Info (Command-I).
5 If necessary, expand “Sharing & Permissions.”
6 Click the small lock, and authenticate as Local Admin.
7 Try to change the privilege level for everyone to “Read & Write.”
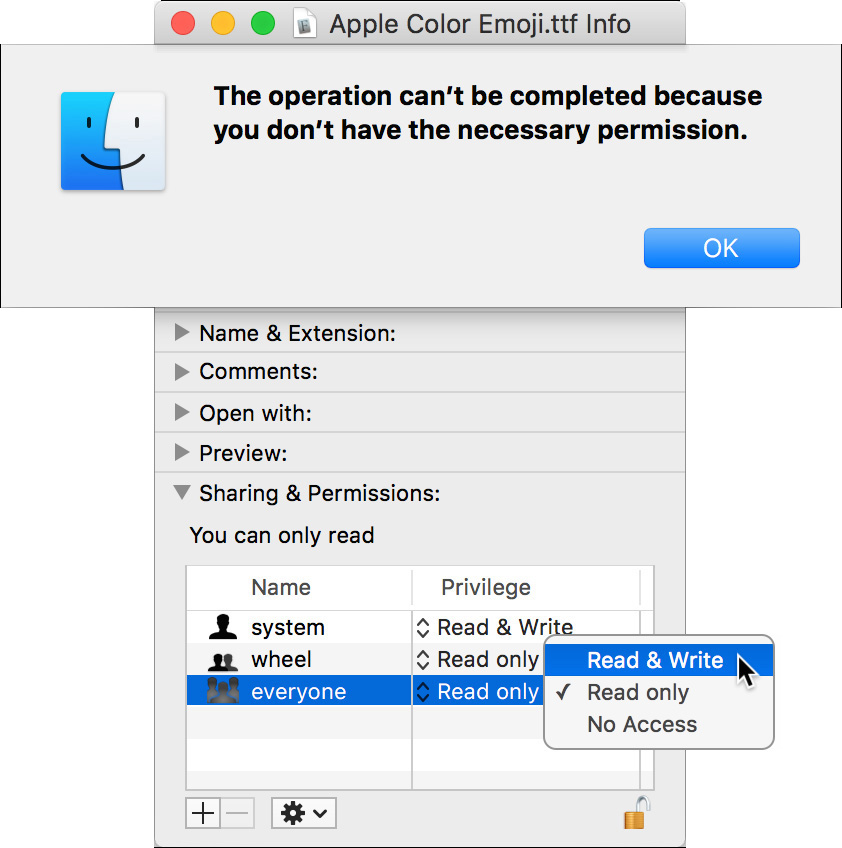
Even though you have authenticated as an administrator, a dialog appears indicating that you don’t have the necessary permission.
8 Dismiss the dialog, and close the Info window.
9 If you want, you can try other methods to make modifications in the /System folder, but System Integrity Protection will block all of your attempts.
10 Log out as Local Admin.