A Conceptual Framework for Information Security Awareness, Assessment, and Training
Mohammad Hassanzadeh1, Narges Jahangiri2 and Ben Brewster3, 1Tarbiat Modares University, Tehran, Iran, 2Ministry of Education, Tehran, Iran, 3Sheffield Hallam University, Sheffield, UK
Information security has become a key issue. Human resources, including all people working with information technology, play a significant role in information security issues. The key factor for human resources in relation to information security is awareness about threats, challenges, and risks lurking in the information exchange environment. Improving staff awareness of information security should be one of the significant, permanent goals in an organization’s information security policies. This chapter investigates information security awareness in terms of knowledge, attitude, and behavior. Research was carried out using a survey method. To evaluate the information security awareness of staff, we developed nine components. Seven independent variables—gender, education level, IT awareness, working experience, occupation, field, and job category—were also selected for developing the conceptual model. Results showed that, among the investigated variables, gender, IT awareness, occupation field, and job category had significant correlations to information security awareness.
Keywords
information security; awareness; conceptual framework; training
Information in this chapter
• Dimensions of information security awareness
• The role of human factors in information security
Introduction
The increased advancement and integration of information and communication technology (ICT) applications within business processes have made ICT a significant part of management, supervision, and service delivery. Consequently, a large proportion of staff members’ organizational life is spent working with computerized information systems, thus shaping their information exchange environment (IEE). The IEE is constantly exposed to electronic and physical threats such as organized crime for the purpose of content defalcation, information flow monitoring, database disruption, and violation of intellectual property rights.
Despite security arrangements, the vulnerability of the IEE has increased as threats become more widespread and intricate. Because of this, information security has become a fundamental issue for businesses, organizations, and governments. Much of the increased emphasis on information security can be attributed to an increase in security breaches, many of which have resulted in significant losses for the affected enterprises. Effective countermeasures, technologies, and solutions usually exist for many of these breaches and contributing threats. However, in most cases they are not deployed correctly nor effectively [1]. This is because technological solutions cannot deal with all information security risks, and the people in the organizations are, in fact, the primary and most critical line of defense [2,3].
Traditionally, the primary focus has been on the technical aspects of information security, with less emphasis placed upon human resources and the people affected by and exposed to information security threats. However, this flawed reliance on technology seems to be changing; managers, security experts, and other decision makers are now increasingly focused on people rather than technology.
When it comes to “human factors,” there are various controls available related to training and awareness. No longer is just the technical security training of IT staff considered sufficient; information security awareness training and other awareness campaigns have become mandatory requirements for everyone [1]. This is proving to be a compulsory principle in international information security management system standards and the related codes of best practices [4–6].
People are the key factor in both the success and the failure of information security management in organizations. Every security breach or security problem is, in fact, frequently associated with human input, not only with technology. Any organization thinking of mitigating information security risks through purely technological countermeasures is likely to eventually fail [7]. In any type of organization, each and every employee should be convinced of and taught to contribute to and comply with information security rules, implementations, and controls in order to achieve successful and effective information security management [8,9]. Studies have shown that for employees to contribute in this way, they must be exposed to proper awareness education and other awareness mechanisms and tools on a regular basis [10,11]. They learn what is necessary for protection of information security as related to their particular roles and responsibilities [12–15].
An awareness of information security can lead to changes in behavior and an enhancement of suitable security activities, allowing people to be responsive with regard to information security and enabling a gradual cultural change within organizations [1,14–18]. Together with technical solutions for information security, it is necessary to make revisions to regulations and policies based on the new requirements of IEE and secure deployment of IT applications. It is also critical to promote information security awareness in organizations and society through training.
Background and literature
A large amount of information is stored and retrieved digitally with speed and precision. The development of networks and the digitization of documents have exposed knowledge repositories to various kinds of threats, theft, and destruction. One of the most important problems in the information era is protecting the security of information [1]. Since the 1980s, various standards have been developed for information security, such as: BS7799, ISO/IEC TR13335, and ISO/IEC 27001. Many organizations have implemented information security management systems (ISMS) to evaluate the security of their information systems. Since the start of the third millennium, various studies have dealt with the assessment and awareness of information security management. Maconachy et al. [19] considered important aspects of information security, placing specific focus on security services (availability, integrity, authentication, confidentiality and nonrepudiation), security countermeasures (technology, policy, practice, and people), and security status (transmission, storage, and processing) to achieve information security objectives.
Kruger and Kearney [14] assessed the information security awareness of users at an international gold mine company and discovered important factors regarding the different dimensions of information security awareness of users. They investigated information security awareness in three aspects: knowledge, attitude, and behavior. They also investigated several sub-areas including: adherence to policies, password secrecy, Internet and email safety, security of mobile equipment in information transmission, reporting of security related events, and suitable actions and consequences.
Chang and Lin [20] proved that organizational culture has a direct effect on information security culture. Some organizational factors, including cooperation, innovation, consistency, and effectiveness on the principles of information security (confidentially, integrity, availability, and accountability), were investigated. The findings indicated that organizational culture factors have a positive impact on information security settings. Taheri [21] proposed a conceptual framework for the human factors in information security systems. In this framework, the impact of factors such as top manager support, self-efficacy, skill, experience, awareness, and training users on information security were examined. Namjoo et al. [22] found that managerial information security awareness (MISA) is directly and positively related to managerial actions toward information security (MATI Security). Kritzinger and Smith [23] presented a conceptual view of an Information Security Retrieval and Awareness (ISRA) model for industry to enhance information security awareness among employees. They provided a common body of knowledge for information security suited to industry that would ensure that technical information security issues did not overshadow the nontechnical, human-related information security issues. The proposed common body of knowledge also focuses on both professionals and low-level users of information.
Shaw et al. [15], in an article titled “The Impact of Information Richness on Information Security Awareness Training Effectiveness,” divided information security awareness into three levels: conception, comprehension, and projection (similar to Kruger’s work). They investigated the richness of the information in online training based on hypertext, multimedia, and hypermedia by studying 250 Managerial Information Security (MIS) students using electronic education and concluded that there is a positive relationship between these levels. By enhancing information richness, information security awareness increased, such that the effect of hypermedia contents would be more than that of multimedia and hypertext contents. Nikrerk and Solms [17] indicated that the lack of “people knowledge” concerning information security is the main threat. It has become widely accepted that the establishment of an organizational subculture of information security is key to managing the human factors involved in information security.
Mete et al. [1] carried out an information security awareness project by training and subsequently auditing the effectiveness and success of this training. Each employee took part in information security training. Results showed the effectiveness of the project and the impact of human awareness on the success of information security management programs in all organizations, regardless of their size, location, culture, or type of business. Veiga and Eloff [18] found that components of information security, such as leadership and governance in an organization’s technology protection and operation, security policies, security program management, and user security management, influence information security behavior and develop information security culture.
Kruger et al. [16] found that the use of vocabulary tests to assess a security awareness level is beneficial. A significant relationship between knowledge of concepts (vocabulary) and behavior was observed. Regarding the background presented, the issue of information security awareness is one of nontechnical and human factors, although in organizational information security, less attention is paid to this issue than is paid to technical solutions. Within any organization, when authorities pay more attention to accurate programming, they can institutionalize good security behavior in employees and enhance the culture of information security [1]. By deploying a strategy of information security, organizations and commercial institutes can benefit from advantages such as [21]:
• Reduced possibility of inactivation of systems and programs (opportunity loss)
• Effective use of human and nonhuman resources within an organization (increased efficiency)
• Reduction of the costs of data loss and information by harmful viruses or security holes (protection of valuable data)
It should be noted that the cost of preventing a security problem is always much less than the cost of recouping the resulting losses.
Human factors and information security
As the literature has indicated, technology, people, and processes are three dimensions that have been identified as critical success factors for information security strategy deployment [1]. Physical access and control of IT systems are examples of the technological aspects that provide support for others. These systems usually provide services that are vital for the definition of access controls. Security processes indicate how companies conduct themselves in formal and informal manners. This is demonstrated throughout the company and includes all procedures, routine activities, trends, and instructions, as well as interactions with customers, suppliers, and commercial partners. Even the plans required for the discovery of any critical situation are included. Eventually, human factors define the development of people, in line with organizational systems and processes. Of course, human factors are usually ignored, perhaps because they are not measurable and cannot be quantified [21].
Investigations into the erroneous use of IT emphasize the role of human factors in information security deficits. In security plans for information systems, the human factor is usually considered as the core component [14]; even if all technical arrangements and security policies are developed and well established, lack of user awareness may make all technical solutions ineffective [13,15]. However, users with security awareness will significantly reduce security risks in the workplace [13–15], improve the safe information behavior of users, and provide a foundation for the enhancement of information security effectiveness throughout the organization [24,14,17,15,18].
Information security learning continuum
Rather than being viewed as a product, the components that make up information security mean that it is more suitable to instead treat it as an organizational process. Each component has its own weight and function. An element should not be considered more than what it is; nor should another parameter be neglected or underestimated just because a particular aspect of information security (e.g., hardware security) is being dealt with. However, new emergent technologies bring with them new and often unique threats. What must we do to effectively utilize technologies and prevent direct or indirect threats? Undoubtedly, direct users of these technologies have very important roles and can be considered as the front line of defense [2,3]. According to the National Institute of Science and Technology (NIST) definition, the IT security-learning continuum of users is divided into levels of awareness, training, and education (NIST, SP 800-50).
The IT security learning continuum (NIST, SP 800-50) provides a visual representation of how education in regards to information security can disseminated to users. Learning at the first level begins with awareness and training for all employees and then builds upon this through information security literature that relates information security to user’s roles and responsibilities in regards to IT systems. This then evolves through special education and experience delivered by information security specialists (NIST, SP 800-16).
Awareness
Security awareness efforts are designed to change behavior or reinforce good security practices. The purpose of awareness presentations is simply to focus attention on security. They focus on reaching a broad audience, often using attractive packaging techniques. Awareness presentations are intended to help individuals to recognize IT security concerns and respond accordingly. In an awareness presentation, the learner simply receives information; this is in contrast to a training environment, where the learner has a more active role. A few examples of IT security awareness materials and activities include:
Training
The NIST Special Publication 800-16 (p. 16–17) states with regard to training: “The ‘Training’ level of the learning continuum strives to produce relevant and needed security skills and competencies by practitioners of functional specialties other than IT security (e.g., management, systems design and development, acquisition, auditing).” The most significant difference between training and awareness is that training seeks to teach knowledge and skills that allow a person to perform a specific function and enhance job performance, while awareness seeks to focus an individual’s attention on an issue or set of issues. However, the skills acquired during training are built upon a foundation of awareness—in particular, upon security basics and literacy material. A training curriculum does not necessarily lead to a formal degree from an institution of higher learning; however, a training course may contain much of the same material found in a course that a college or university includes in a certificate or degree program (NIST, SP 800-16).
Education
The NIST Special Publication 800-16 (p. 17–18) says regarding education: “The ‘Education’ level integrates all of the security skills and competencies of the various functional specialties into a common body of knowledge, adds a multidisciplinary study of concepts, issues, and principles (technological and social), and strives to produce IT security specialists and professionals capable of vision and pro-active response.”
Education is an essential aspect of the human factors that influence information security management within any organization. When human factors, such as education are not considered, technical solutions have little impact on information security management [14,23]. Education incorporates other human factors including the provision of training and the increasing of awareness in the development of effective information security management [12,13,25,14,15,1].
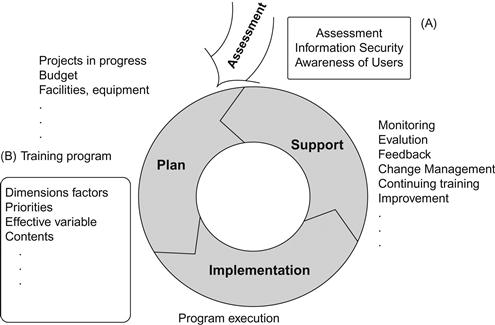
Generally, an effective security structure must be composed of both technical and functional elements in order to have mutual impact on the risks that are developed due to omissible information. Because of the increasing speed of technological changes, the need for flexible security measures is felt more than ever before. These rapid changes increase the requirements for accurate management of omissible information and employee awareness about that management. Remedies and methods of using it should be part of security policies along with suitable policy-making. Employees who work with vital information must know the concept of omissible information security. If we consider security education and awareness as a part of our job, we feel more responsibility regarding our role and tasks, which results in a reduction of information security risks. The overall strategy of information security awareness and training for users is presented in Figure 6.1.
Dimensions of information security awareness
The weak security behavior of users (for example, security errors, lack of accuracy, lack of attention) has played a part in many security events [13–15]. Increased security awareness on the part of end users can lead to the emergence of a security culture and, in turn, the creation of increased security competence. Although there is no single method for programming security awareness that is compatible with all situations across all organizational and human levels, determining a specific method for implementing a security awareness program based on security awareness dimensions is necessary for every organization [15].
Many organizations are aware of the importance of implementing a program for informing employees about information security [15]. For these programs to be successful, it is important that employees reach acceptable levels in three dimensions of awareness about security risks. These three dimensions are: knowledge, attitude, and behavior [14,15].
Knowledge
The first step for securing an organization is to be able acquire knowledge of and also track the security risks of the working environment. Knowledge means identifying the presence of a threat and developing an awareness of it. The advantages of forming an accurate image of an environmental security threat can be enhanced by optimizing observation and security awareness perception [15].
Attitude
To have enough knowledge about occurring security events and their impact is not helpful in isolation. A positive attitude is needed for this knowledge to be used effectively. If users reach a sufficient level of perception regarding information security, it can prove beneficial to both them and the organization [14].
Behavior
Behavior is the third dimension of security awareness. In this dimension, when employees develop good security behaviors and habits, a strong information security culture within the organization is established. Timely decisions can be made through preparation, projection, and behavior. The ultimate objective of an effective program of security awareness is making the users prepared to react to potential security risks [15]. Prevention is better than treatment. In order to prevent security risks, end users must be able to predict and deal with future security attacks.
A field study
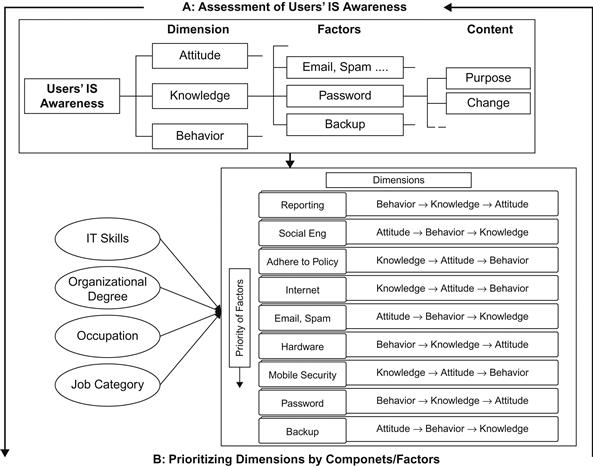
Here we report findings of applied research. User information security awareness was assessed in nine categories: email, spam, and attachments; backup; passwords; social engineering; mobile security; malware (e.g., viruses, worms, and Trojans); Internet, reporting security events; and adherence to organizational policies. These nine were assessed in three dimensions: knowledge, attitude, and behavior. The relationship and values of seven independent variables were investigated. The independent variables include: gender, job experience, education, familiarity with IT, professional field, occupation, and job category. Data was collected via a questionnaire based on relevant subject literature and the ideas of experts. The questionnaire consisted of 70 questions that were grouped into nine factors of information security awareness in three dimensions of information security (knowledge, attitude, and behavior). The results were expressed in the Likert scale, where 1 represents “strongly disagree” and 5 represents “strongly agree.” The questionnaires were manually distributed and collected.
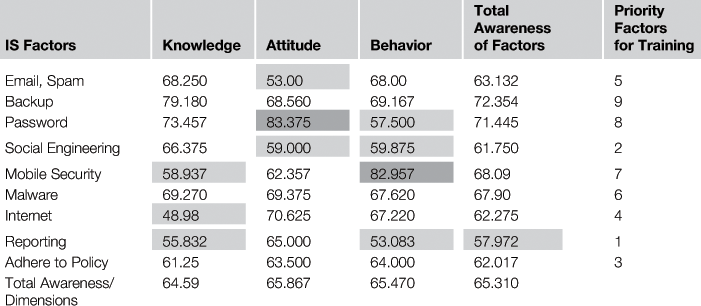
The research sample was selected from employees of a financial organization estimated to consist of 1400 staff distributed across branches all over the country. We selected a sample of the population via random sampling. Five hundred employees were selected. Of the 530 questionnaires distributed, 500 questionnaires were returned and also qualified for investigation. During distribution of the questionnaires, the participants received verbal and written explanations about the subject of the questionnaire and its importance within the organization. Normality of distribution was justified using a Kolmogorov-Smirnov test. The validity of the questionnaire was confirmed by expert practitioners of information security affairs and by using Cronbach‘s Alpha Coefficient (0.8452). The scores and priorities of elements in each of the three components are presented in Table 6.1. (Percentage)
Table 6.1
Results of the Evaluation of Information Security User Awareness (Percentage)
![]() 10-59: Unsatisfying-action required
10-59: Unsatisfying-action required ![]() 60-79: Monitor-action potentially required
60-79: Monitor-action potentially required ![]() 80-100: Unsatisfying-no need for action.
80-100: Unsatisfying-no need for action.
As Table 6.1 shows, the total information security awareness of employees, analyzed in the three dimensions (knowledge, attitude, and behavior) was average. Employees were lower in knowledge than in the other two dimensions (attitude and behavior). An employee’s attitude toward information security was more positive and effective than exhibited behaviors regarding security considerations would suggest. An awareness score of less than 60 was indicated as unsatisfactory, suggesting that action was required. Cases where the score was between 60 and 80 indicated the need for more attention and monitoring. In areas where the score was higher than 80, no action was required. The average total information security awareness of employees was 65.31, indicating that the organizational managers and information security authorities should begin a comprehensive effort to create a suitable program, based on research results, to enhance employee information security awareness.
The last column identifies the priority of factors in an education program. Among these factors, the need to educate and consider reporting was ranked higher than other factors. The need to educate and consider password and backup factors was ranked lower than other factors. The priorities of factors calling for further attention and training are shown in Table 6.1. In order to test the results, Kramer and Spearman’s correlation coefficient was used. The results are shown in Table 6.2.
Table 6.2
Correlation Coefficient Between the Independent Variables and the Dependent Variable (Information Security Awareness)

As shown in Table 6.2, the correlation between demographic and organizational variables was not considerable. Despite this, some of the variables do show correlation with information security awareness components (in particular, IT skills and job category). Based on the detailed results of interconnectivity of variables, a conceptual framework was prepared to articulate the basic components of a training program on information security awareness in organizations.
The proposed framework is composed of two steps. The first step deals with users’ information security awareness in three dimensions: knowledge, attitude, and behavior. The conclusions from the assessment phase can be used for prioritizing the factors and their dimensions in regard to demographic and organizational factors. In turn, priorities obtained in the second phase can be functionalized in the assessment phase. As shown in Figure 6.2, the priorities of dimensions in each factor are varied. Improving employee awareness can be achieved through the required dimensions and the priority of the determined factors of information security.
As depicted in the framework, the components for each individual task differ. For example, reporting needs to be trained by prioritizing behavior first, then knowledge, and then attitude, but backup needs to be enhanced by prioritizing attitude first, then behavior, and then knowledge. Making appropriate policies for information security requires considering the organization’s overall priorities and formulating the policies accordingly. By doing this, the objectives of creating a good information security policy can be reached.
Concluding remarks
Most organizations invest in technical solutions to providing information security while investing little in the human aspects of information security. This is because there is no appropriate estimation of the information security awareness of staff members in organizations. IT managers should consider nontechnical and human factors in information security, such as enhancing employees’ awareness of it. For this purpose, it is valuable to evaluate employees’ awareness of and training in information security concepts and behaviors. The conceptual framework proposed in this chapter draws on the prioritization of three key dimensions (knowledge, attitude, and behavior) relevant to each factor. This framework could be a starting point for articulating and improving users’ awareness of information security as well as designing an education program for use in organizations.
References
1. Mete E, Erdem U, Saban E. The positive outcomes of information security awareness training in companies. Information Security Technical Report. 2009;14:223–229.
2. Tipton HF, Krause M. Information security management handbook Auerbach Publications 2007.
3. IT Governance Institute. Information security governance: Guidance for information security managers ITGI Publishing 2008.
4. Scholtz T. Structure and content of an enterprise information security architecture. Gartner Res 2006; January 23.
5. International Organization for Standardization. ISO/IEC 27001: ISO; 2005.
6. Wood CC. Information security policies made easy Penta Safe Security Technologies 2002.
7. Mitnick KD, Simon WL. The art of deception John Wiley & Sons, Inc 2003.
8. Ashenden D. Information security management: A human challenge? Elsevier Information Security Technical Report 2008;13:195–212.
9. Williams P. In a ‘trusting’ environment, everyone is responsible for information security. Elsevier Information Security Technical Report 2008;13:207–215.
10. Lacey D. Managing the human factor in information security: how to win over staff and influence business managers. Wiley.com; 2011.
11. Gehringer EF. Choosing passwords: security and human factors. In: ISTAS’02 International Symposium on Technology and Society; 2002. p. 369–373.
12. Thomson ME, Von Solms R. Information security awareness: Educating your users effectively. Information Management & Computer Security. 1998;6(4):167–173.
13. Wilson M, Hash J. Building an IT security awareness and training program National Institute of Standards and Technology 2003;20–79 sp800-50.
14. Kruger HA, Kearney WD. A prototype for assessing information security awareness. Computer & Security. 2006;25:289–296.
15. Shaw RS, Charlie C, Harris, Albert, Huang H. The impact of information richness on information security awareness training effectiveness. Computer & Education. 2009;52:93–100.
16. Kruger HA, Drevin L, Steyn T. A vocabulary test to assess information. Information Management & Computer Security Journal. 2010;18(5):316–319.
17. Nikrerk JF, Solms V. Information security culture: a management perspective. Computer & Security. 2009;5:142–144.
18. Veiga AD, Eloff JHP. A framework and assessment instrument for information security culture. Computer & Security. 2010;29(2):196–200.
19. Maconachy V, Schou CD, Ragsdale D, Welch D. A model for information assurance: An integrated approach. Workshop on Information Assurance and Security 2001 Jun:5–6 United States Military Academy; West Point, NY.
20. Chang E, Lin CS. Exploring organizational culture for information security management. Industrial Management & Data Systems. 2007;107:1–10.
21. Taheri M. The role of human factors in the security of information systems [thesis] Tehran, Iran: Tarbiat Modares University, IT management, Dept; 2007.
22. Namjoo C, Dan K, Goo J. Knowing is doing: An empirical validation of the relationship between managerial information security awareness and action. Information Management & Computer Security. 2008;16:484–485.
23. Kritzinger E, Smith E. Information security management: An information security retrieval and awareness model for industry. Computer & Security. 2008;27:224–231.
24. Stanton JM, et al. Analysis of end user security behaviors. Computers & Security. 2005;24.2:124–133.
25. Wilson M, et al. IT security training requirements: A role- and performance-based model National Institute of Standards and Technology 2003;22–26 sp800-16.
Further Reading
1. Shaw SC, Charlie C, Chen RS. Mitigating information security risks by increasing user security awareness: case study of an information security awareness system. IT, Learning, and Performance Journal. 2002;24:132–133.