Analyzing the Ergodic Secrecy Rates of Cooperative Amplify-and-Forward Relay Networks over Generalized Fading Channels
Annamalai Annamalai, Abiodun Olaluwe and Eyidayo Adebola, Prairie View A&M University, Prairie View, TX, USA
Wireless physical layer security approaches can prevent eavesdropping without upper layer data encryption. However, such techniques are hampered by time-varying wireless channel conditions and they are typically feasible only when the legitimate partners in the Wyner’s wire-tap channel model have an advantage over the source-eavesdropper channels. Node cooperation is an effective strategy to overcome this challenge and enhance the performance of secure wireless communications. This chapter addresses secure wireless communications of a source-destination pair with the help of multiple cooperating amplify-and-forward relays in the presence of one or more eavesdroppers. The role of channel fading is characterized in terms of average (ergodic) secure communication rates. Overall, this work establishes the utility of node cooperation for improving secure wireless communications and provides a unified analytical framework for assessing the ergodic secrecy rates of cooperative amplify-and-forward relay networks in a generalized fading environment with independent but non-identically distributed channel fading statistics.
Keywords
wireless physical layer security; secrecy capacity; cooperative wireless communications; fading channels
Information in this chapter
• Improving wireless physical layer security using cooperative relays
• Ergodic secrecy rates of cooperative amplify-and-forward relay networks
Introduction
The purpose of secure communications is to enable the legitimate destination node to successfully recover the source information, while keeping the eavesdroppers (wire-tappers) ignorant of this information as much as possible. In recent years, the issues of privacy and security concerns have taken on an increasingly important role in the design of tactical wireless networks owing to the broadcast nature of wireless transmissions and to growing proliferations of wireless sensors in military and homeland security applications.
Traditionally, security is viewed as an independent feature addressed above the physical layer, and all widely used cryptographic protocols (e.g., RSA and AES) are designed and implemented assuming the physical layer has already been established and provides an error-free link. In contrast with this paradigm, there exist both theoretical and practical contributions that support the potential of physical layer security ideas to significantly strengthen the security of wireless communication systems. This line of work was pioneered by Wyner, who introduced the wire-tap channel and established the possibility of creating perfectly secure communication links without relying on private (secret) keys [1]. But the impact of the seminal articles by Wyner and later by Csiszár and Körner [2] was limited in the 1980s, partly because practical wire-tap codes were not available then, but mostly because a strictly positive secrecy capacity in the classical wire-tap channel setup requires the legitimate receiver to have some advantage over the attacker in terms of channel quality. Almost at the same time, Diffie and Hellman [3] published the basic principles of public-key cryptography, which was to be adopted by nearly all contemporary security schemes.
Recently there has been a renewed interest in information-theoretic security (i.e., perfect secrecy), arguably due to the work of Maurer [4], who proved that even when the legitimate users (say Alice and Bob) have a worse channel than the eavesdropper (say Eve), it is possible for them to generate a secret key through public communication over an insecure yet authenticated channel. The advent of wireless communications, which is particularly susceptible to eavesdropping owing to the broadcast nature of the transmission medium, has also motivated a closer analysis of the secrecy potential of wireless networks. For instance, fading wire-tap channels were studied in [5–7] (also see references therein) while multiple-antenna wire-tap channels were investigated in [8,9] and references therein.
However, practical implementation issues associated with packing a large number of antenna elements on tiny (i.e., small form-factor) sensor/communication nodes suggest that cooperative relaying strategies may be simpler and perhaps more appropriate for improving the achievable secrecy rate in wireless sensor and ad-hoc networks. In this emerging wireless communication paradigm, a relay node may either amplify what it receives (in case of amplify-and-forward relaying protocol) or digitally decodes and re-encodes the source information (in case of decode-and-forward relaying protocol) before re-transmitting it to the destination node. Other variations of cooperative relaying strategies include opportunistic, incremental, variable-gain, and fixed-gain (either blind or semi-blind) relaying that are implemented based on the availability of channel side information (CSI) and the number of active participating nodes for information relaying. The cooperative relaying architecture also offers a modular and flexible solution to meet a prescribed design objective (e.g., secrecy rate, data rate, error rate, energy constraint, etc.) by enabling the source node to tap into the available resources of local neighboring nodes to increase its throughput, range, reliability, and covertness. However, theoretical contributions on the achievable ergodic secrecy rates of cooperative relay networks are rather limited (e.g., [10–13] and [26]). Therefore, development of a unified analytical framework for computing the ergodic secrecy rates of cooperative secure wireless communications in a myriad of fading environments is of both theoretical and practical interest. This is because it allows one to gain a better understanding as to how much the fundamental limit of secure communication rate can be improved by exploiting/mitigating channel effects via node cooperation as well as to study the impact of channel fading statistics (e.g., fade distribution, locations of the relays and the eavesdroppers) on the achievable ergodic secrecy rates. To the best of our knowledge, the ergodic secrecy rates of cooperative relay networks in generalized fading environments have not been studied previously. This might be attributed to the analytical difficulties associated with computing the statistical expectation of the logarithmic function with respect to the random variable that characterizes the fading channel, as well as finding the exact probability density function (PDF) of the end-to-end signal-to-noise ratio (SNR) for the amplify-and-forward cooperative relaying protocol.
Secure cooperative wireless communications
Improving wireless physical layer security using cooperative relays in a Gaussian channel
Suppose a source node S is transmitting information to the destination node D through an amplify-and-forward variable-gain relay R in the presence of an eavesdropper E as depicted in Figure 14.1.
Given the distances ![]() ,
, ![]() , and
, and ![]() , we may compute
, we may compute ![]() and
and ![]() via the cosine rule as
via the cosine rule as ![]() and
and ![]() . These distances will be utilized in the calculations of the mean link SNRs in a fading channel. The two angles shown in Figure 14.1 are also important to investigate the impact of relay/eavesdropper locations on the achievable secrecy rate.
. These distances will be utilized in the calculations of the mean link SNRs in a fading channel. The two angles shown in Figure 14.1 are also important to investigate the impact of relay/eavesdropper locations on the achievable secrecy rate.
It can be shown (in the context of information-theoretic wireless physical layer security) that mutual information between the source-destination and the source-eavesdropper links with cooperative amplify-and-forward (CAF) variable-gain relay in a Gaussian (non-fading) channel are given by (1) and (2), respectively:
![]() (1)
(1)
![]() (2)
(2)
where ![]() denotes the channel gain of link i-j while
denotes the channel gain of link i-j while ![]() and
and ![]() or
or ![]() correspond to the transmit power during the first phase and the second phase of cooperation, respectively. Hence the secrecy rate in the Gaussian channel with receiver-only channel state information is given by the difference between the mutual information between the source (Alice) and the legitimate receiver (Bob)
correspond to the transmit power during the first phase and the second phase of cooperation, respectively. Hence the secrecy rate in the Gaussian channel with receiver-only channel state information is given by the difference between the mutual information between the source (Alice) and the legitimate receiver (Bob) ![]() and the source (Alice) and the eavesdropper (Eve)
and the source (Alice) and the eavesdropper (Eve) ![]() :
:
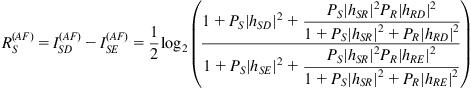 (3)
(3)
It is therefore evident that in a non-fading channel, there will be a positive secrecy rate if the condition (4) is satisfied:
![]() (4)
(4)
This result is interesting in that it might be possible to achieve a positive secrecy rate even when the channel quality between the Alice and Eve (i.e., eavesdropper channel) is better than Alice and Bob (i.e., main channel) by proper selection of the position of cooperative relay and the power allocation. The link between the source-relay provides an additional avenue to transmit secure information while the link between the relay and the legitimate destination node compensates the secret information loss at the source. But the secrecy rate is zero when ![]() without cooperative relay.
without cooperative relay.
If there are multiple J eavesdroppers, then the secrecy rate may be calculated as
![]() (5)
(5)
This is portrayed in the second expression in (3). It is also important to note that our study and network architecture is different from [13] since we do not assume that the source first transmits locally to a set of “trusted” cooperative relay nodes, which then convey the source information to the destination securely by finding suboptimal weights at the relays that maximize the secrecy rate under total power constraint. Moreover, their analysis does not take into account the deleterious effects of multipath fading. Similarly, the analysis and the results in [26] were restricted to a Gaussian (non-fading) channel.
Ergodic secrecy rates of cooperative amplify-and-forward relay networks
To the best of our knowledge, the ergodic secrecy rates of cooperative amplify-and-forward relay networks in generalized fading environments have not been studied previously. This might be attributed to the analytical difficulties associated with finding the exact PDF of the end-to-end SNR for the amplify-and-forward relaying protocol, as well as the evaluation of the statistical expectation of a logarithmic function with respect to the random variables that characterizes the fading channel.
In a recent work [14,15], we discovered an exponential-type integral representation for ln γ, γ > 0, in which the conditional fading SNR appears only in the exponent (i.e., thus facilitates the task of statistical averaging with respect to the PDF of SNR) and presented a novel moment generating function-(MGF) based analytical framework for calculating the ergodic capacities of cooperative relay networks under three distinct source-adaptive transmission policies in a myriad of fading environments. Details of the derivation of this exponential-type integral representation of the logarithmic function are provided in the appendix for completeness.
To facilitate the statistical averaging of (3) over the independent but non-identically distributed (i.n.d) fading SNR random variables, ![]() , we first re-write (3) (given N=1 and J=1) as:
, we first re-write (3) (given N=1 and J=1) as:
![]() (6)
(6)
Substituting ![]() in (6) and then invoking the exponential-type integral representation for logarithmic function (A.5), it is quite straightforward to show that the ergodic secrecy rate is given by
in (6) and then invoking the exponential-type integral representation for logarithmic function (A.5), it is quite straightforward to show that the ergodic secrecy rate is given by
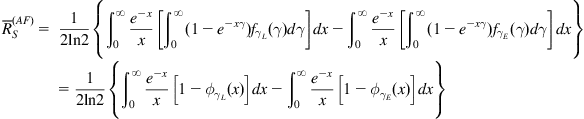 (7)
(7)
where ![]() and
and ![]() correspond to the MGF of
correspond to the MGF of ![]() and
and ![]() random variables, respectively (i.e., Laplace transform of their respective PDF of the end-to-end SNRs
random variables, respectively (i.e., Laplace transform of their respective PDF of the end-to-end SNRs ![]() ). But the evaluation of the exact MGFs of
). But the evaluation of the exact MGFs of ![]() and
and ![]() are known to be very cumbersome and an exact expression (but very complicated formula) is available only for the special cases of i.n.d Nakagami-m fading channels with positive integer fading severity indices (obviously, the special case of Rayleigh fading can be treated by setting the fading severity parameter m to unity). In [16,17], we have also found a highly accurate and efficient closed-form expression to approximate MGF of SNR for a dual-hop CAF relayed path in generalized fading environments. This solution is directly relevant and can be leveraged in this work for estimating the ergodic secrecy rates of cooperative secure communications in a myriad of fading environments. Mimicking the developments in [16,17], we obtain simple closed-form approximations for
are known to be very cumbersome and an exact expression (but very complicated formula) is available only for the special cases of i.n.d Nakagami-m fading channels with positive integer fading severity indices (obviously, the special case of Rayleigh fading can be treated by setting the fading severity parameter m to unity). In [16,17], we have also found a highly accurate and efficient closed-form expression to approximate MGF of SNR for a dual-hop CAF relayed path in generalized fading environments. This solution is directly relevant and can be leveraged in this work for estimating the ergodic secrecy rates of cooperative secure communications in a myriad of fading environments. Mimicking the developments in [16,17], we obtain simple closed-form approximations for ![]() and
and ![]() in a generalized fading environment with i.n.d. fading statistics corresponding to the distinct (spatially distributed) wireless links:
in a generalized fading environment with i.n.d. fading statistics corresponding to the distinct (spatially distributed) wireless links:
![]() (8)
(8)
![]() (9)
(9)
The MGF expressions shown above are very attractive, as they only require the knowledge of MGF of individual links in closed-form, which is readily available in the literature (e.g., [21] and [25 Table 3, p. 28]).
Computational results
In this section, selected numerical results are provided to demonstrate the efficacy of our analytical framework for assessing the ergodic secrecy rates of cooperative wireless communications in a generalized fading environment. Assuming a simple path-loss model, we can show that the mean received SNR of the wireless link i-j is given by
![]() (10)
(10)
where ![]() denotes the path-loss exponent, c is a constant (arbitrarily chosen to be
denotes the path-loss exponent, c is a constant (arbitrarily chosen to be ![]() in our case, unless stated otherwise),
in our case, unless stated otherwise), ![]() corresponds to the transmit power ratio such that
corresponds to the transmit power ratio such that ![]() , and
, and ![]() represents the transmit energy per bit over the noise spectral density ratio at the source node.
represents the transmit energy per bit over the noise spectral density ratio at the source node.
All the figures were generated using (7), (8), and (9), and we have also arbitrarily chosen ![]() ,
, ![]() with the two angles set to be
with the two angles set to be ![]() and
and ![]() (unless stated otherwise). In the instances where we investigate the effects of dissimilar fade distributions and/or mean signal strengths of the different links of the Wyner’s wire-tap channels, we have arbitrarily assumed (without any loss of generality) the fading parameters summarized in Table 14.1 for each of the distinct links identified in Figure 14.1. In Figure 14.2 we have assumed all links to be Rayleigh faded, while in Figure 14.3, Figure 14.5, and Figure 14.9 we have assumed Nakagami-m faded links.
(unless stated otherwise). In the instances where we investigate the effects of dissimilar fade distributions and/or mean signal strengths of the different links of the Wyner’s wire-tap channels, we have arbitrarily assumed (without any loss of generality) the fading parameters summarized in Table 14.1 for each of the distinct links identified in Figure 14.1. In Figure 14.2 we have assumed all links to be Rayleigh faded, while in Figure 14.3, Figure 14.5, and Figure 14.9 we have assumed Nakagami-m faded links.
Table 14.1
Fading Distributions for Different Links in a Cooperative Relay Network and Their Corresponding MGFs of Fading SNR
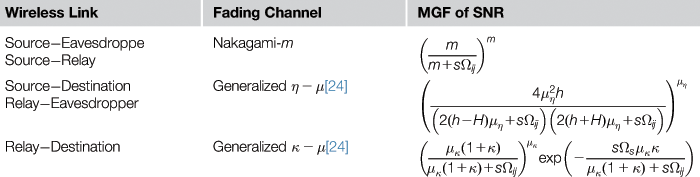
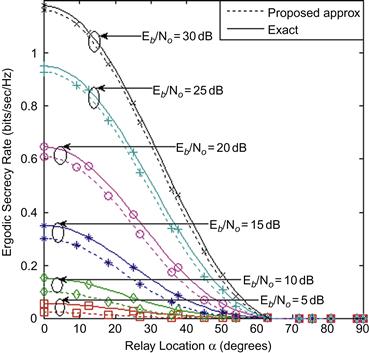
Figure 14.2 Ergodic secrecy rate of a CAF relay network (as illustrated in Figure 14.1) in Rayleigh fading plotted as a function of the relay location for several different values and equal power allocation during the two transmission phases (i.e., ![]() and
and ![]() ).
).
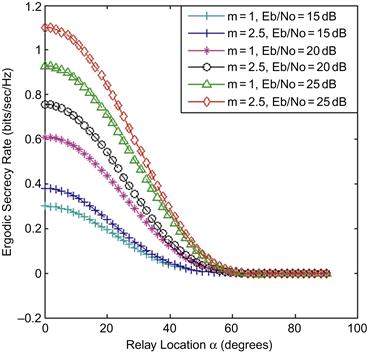
Figure 14.3 Impact of the fade distribution (i.e., fading severity parameter) on the ergodic secrecy rate of a CAF relay network when (i.e., ![]() and
and ![]() ).
).
Unless stated otherwise, the format 1 structure of the η-μ distribution is used [24]. Hence, the acceptable range of values of η is 0 < η < ∞ where η is the scattered-wave power ratio between the quadrature and in-phase components of each multipath cluster, while h and H are given as ![]() and
and ![]() respectively, and m denotes the Nakagami-m fading index. For the generalized η-μ distribution, we have arbitrarily selected the fading severity parameters as
respectively, and m denotes the Nakagami-m fading index. For the generalized η-μ distribution, we have arbitrarily selected the fading severity parameters as ![]() and
and ![]() . Moreover, the default κ-μ fading parameters are defined as
. Moreover, the default κ-μ fading parameters are defined as ![]() and
and ![]() , while
, while ![]() denotes the link mean SNR, which can be calculated with the aid of (10). In the following subsections we investigate the effects of different factors of both the channel and system parameters on the achievable secrecy rates of cooperative secure wireless communications.
denotes the link mean SNR, which can be calculated with the aid of (10). In the following subsections we investigate the effects of different factors of both the channel and system parameters on the achievable secrecy rates of cooperative secure wireless communications.
Tightness of the approximation for the MGF of SNR
In Figure 14.2 we show a comparison of the ergodic secrecy rate predicted using our proposed approximate MGF shown in (8) and (9) versus the exact expression for the half harmonic mean SNR of a two-hop relayed path given in [22, Eq. (52)] or [23, Eq. (5) and Table 1] for Rayleigh fading. It is apparent that our simple closed-form MGF formula can yield very accurate predictions of the ergodic secrecy rate over a wide range of ![]() values. The result is very encouraging in the sense that we may now use our closed-form MGF expressions (8)–(9) with a high confidence to predict the ergodic secrecy rate of CAF relay networks in a myriad of fading environments, especially for many practical settings and fading environments where a computationally stable expression for the MGF of half harmonic mean SNR is not available.
values. The result is very encouraging in the sense that we may now use our closed-form MGF expressions (8)–(9) with a high confidence to predict the ergodic secrecy rate of CAF relay networks in a myriad of fading environments, especially for many practical settings and fading environments where a computationally stable expression for the MGF of half harmonic mean SNR is not available.
Effects of fade distributions
In Figure 14.3, the ergodic secrecy rates of the CAF relay network illustrated in Figure 14.1 were calculated as a function of the relay node location in two different Nakagami-m channels. We found that the ergodic secrecy rate is greater in channels that experience less severe fading (i.e., higher values of the fading severity parameter m), especially when the locations of the eavesdropper and the cooperative relay nodes are fixed. It is also evident from Figure 14.2 and Figure 14.3 that an appropriate choice of the relay location could maximize the ergodic secrecy rate for a specified location of the eavesdropper node. Thus, we believe that further research in this direction might lead to some good design guidelines/principles for the selection of relay nodes that maximizes the ergodic secrecy rate metric. It is also important to highlight that this optimization metric represents a new paradigm to the cooperative wireless communication design by taking into account the physical layer security considerations in the formation of a cooperative wireless network. It is also fundamentally different from the prior works on CAF relay network optimization that were focused on maximizing the ergodic and/or outage capacity metrics.
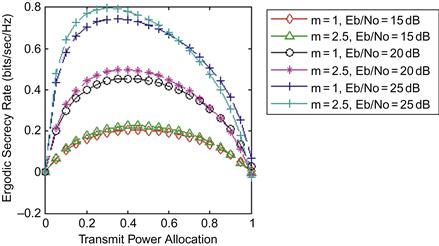
In order to buttress this effect, we also consider two additional scenarios as presented in Table 14.2; the resulting curves are plotted in Figure 14.4.
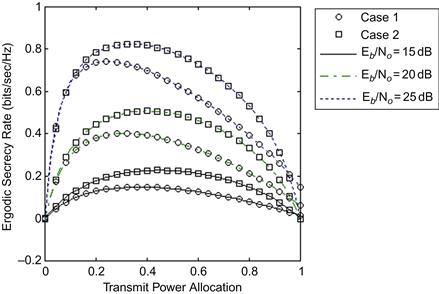
Figure 14.4 Ergodic secrecy rate of a CAF relay network versus transmit power allocation in two different fading environments (with ![]() , and
, and![]() ).
).
Figure 14.4 shows how different combinations of path fade distributions affect the ergodic secrecy rate of a CAF relay network when ![]() is fixed (i.e., the mean signal strengths are fixed and only fading severity parameters are altered for Case 1 and Case 2). It is observed that when the critical paths do not experience severe fading, the ergodic secrecy rate maximizes at a higher value transmit power allocation
is fixed (i.e., the mean signal strengths are fixed and only fading severity parameters are altered for Case 1 and Case 2). It is observed that when the critical paths do not experience severe fading, the ergodic secrecy rate maximizes at a higher value transmit power allocation ![]() than when the critical paths experience deep fades. Also, the ergodic secrecy rate dwindles faster when the channel experiences more severe fading. It is also good to note the shifting effect of this impact on the curves in the light of effect of the constituent components of equation (7). The second integral has a lower value at initial values of the allocated power, which makes the secrecy rate to climax early enough, but its value increases drastically as power allocation during the first transmission phase increases, forcing the secrecy rate to decline with it. It can be adjudged also that the fading conditions of the link between the relay-destination and relay-eavesdropper during the second phase of the transmission can affect the achievable secrecy rate.
than when the critical paths experience deep fades. Also, the ergodic secrecy rate dwindles faster when the channel experiences more severe fading. It is also good to note the shifting effect of this impact on the curves in the light of effect of the constituent components of equation (7). The second integral has a lower value at initial values of the allocated power, which makes the secrecy rate to climax early enough, but its value increases drastically as power allocation during the first transmission phase increases, forcing the secrecy rate to decline with it. It can be adjudged also that the fading conditions of the link between the relay-destination and relay-eavesdropper during the second phase of the transmission can affect the achievable secrecy rate.
Effects of transmit power allocation in distinct transmission phases
Our proposed MGF-based analytical framework for ergodic secrecy rate analysis can be readily used to facilitate an investigation of the optimal power allocation strategy that maximizes the ergodic secrecy rate of the CAF relay network depicted in Figure 14.1. Figure 14.5 depicts that there exists an optimal transmit power allocation during the two different transmission phases, which maximizes the ergodic secrecy rate. The optimal power allocation depends on a few factors, including the distance ratios between the source, relay, destination, and eavesdropper nodes as well as the channel fading statistics of the spatially distributed wireless links. However, we observed that the optimal power allocation does not appear to be very sensitive to the variations in the fading severity parameters when all the links have an identical fading severity index.
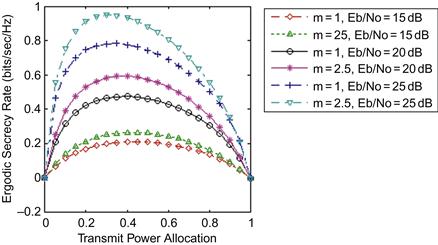
Figure 14.5 Ergodic secrecy rate of a CAF relay network (depicted in Figure 14.1 with ![]() and
and ![]() ) plotted as a function of transmit power allocation
) plotted as a function of transmit power allocation ![]() for several different
for several different ![]() values and Nakagami-m fading severity parameters.
values and Nakagami-m fading severity parameters.
In Figure 14.6, we have plotted the secrecy rate against the transmit power allocation when distinct wireless links are assumed to undergo different fading according to Table 14.1. The secrecy rate is calculated at different Nakagami-m indices for the source and eavesdropper, source and relay links, while other links are fixed at their default values. It is noticed that there is an increase in secrecy rates with increased transmit power allocation, but the secrecy rate decreases after an optimum transmit power allocation is exceeded. It is also observed that an increase in ![]() results in a corresponding increase in the ergodic secrecy rate. Comparison between Figure 14.5 and Figure 14.6 also reveals that the values of fading severity parameters of the source-eavesdropper and source-relay links have a noticeable impact on the achievable secrecy rate, although the optimal power allocation ratio seems to be less susceptible to these variations. This in turn suggests that coarse side information of the distance ratios between the source, relay, destination, and the eavesdropper nodes are probably sufficient to develop a simple rule of thumb for the “optimal power allocation” policy.
results in a corresponding increase in the ergodic secrecy rate. Comparison between Figure 14.5 and Figure 14.6 also reveals that the values of fading severity parameters of the source-eavesdropper and source-relay links have a noticeable impact on the achievable secrecy rate, although the optimal power allocation ratio seems to be less susceptible to these variations. This in turn suggests that coarse side information of the distance ratios between the source, relay, destination, and the eavesdropper nodes are probably sufficient to develop a simple rule of thumb for the “optimal power allocation” policy.
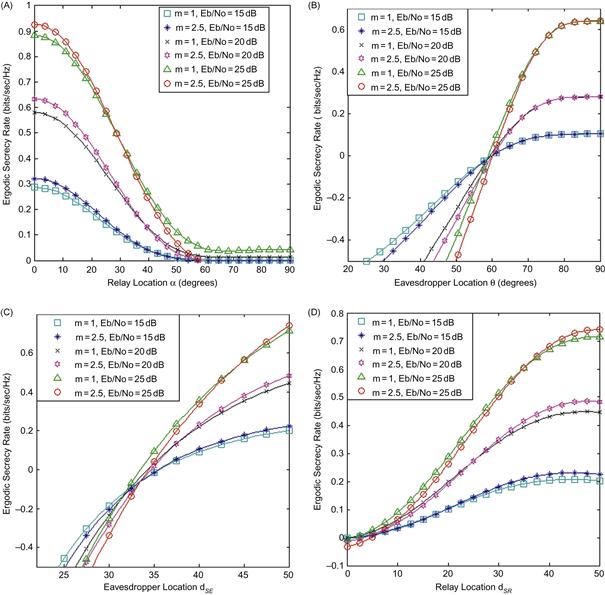
Effects of dissimilar mean signal strengths
The mean strengths of the signals received by the eavesdropper and the relay are characterized by the angles ![]() and
and ![]() and also the distances
and also the distances ![]() and
and ![]() . Hence an array of plots is presented in Figure 14.7 (a–d) to capture nicely how the ergodic secrecy rate varies in accordance with these four parameters. To generate these plots, we have assumed the channel fading parameters for various links as summarized in Table 14.1 and equal power allocation during the two transmission phases. As expected, the ergodic secrecy rate decreases with increasing value of the angle
. Hence an array of plots is presented in Figure 14.7 (a–d) to capture nicely how the ergodic secrecy rate varies in accordance with these four parameters. To generate these plots, we have assumed the channel fading parameters for various links as summarized in Table 14.1 and equal power allocation during the two transmission phases. As expected, the ergodic secrecy rate decreases with increasing value of the angle ![]() while an increase in any of the parameters
while an increase in any of the parameters ![]() ,
, ![]() , or
, or ![]() improves the ergodic secrecy rate. It is evident from Figure 14.7 (a) and Figure 14.7 (b) that the ergodic secrecy rate climaxes as α is closer to zero and plummets afterward, while this metric increases with a larger value of
improves the ergodic secrecy rate. It is evident from Figure 14.7 (a) and Figure 14.7 (b) that the ergodic secrecy rate climaxes as α is closer to zero and plummets afterward, while this metric increases with a larger value of ![]() . This is anticipated, as both the distances
. This is anticipated, as both the distances ![]() and
and ![]() increase with a larger value of
increase with a larger value of ![]() and α, respectively. For instance, the distance
and α, respectively. For instance, the distance ![]() is shortest when α=0, which coincidentally forms the shortest route path to the destination node. Moreover, in order to ensure positive secrecy we must choose the relay location at an angle below a certain value which, from Figure 14.7 (a), can be deduced to be approximately 60°. Figure 14.7 (b) and Figure 14.7 (c) also indicate that there would not be any secrecy if the eavesdropper is within a certain distance range and/or angle to the source node, irrespective of the transmit signal energy. Figure 14.7 (d) reveals the possibility of achieving a higher secrecy rate by increasing the relay distance coupled with increasing the transmit SNR if the relay angle is fixed. It is also important to note that secure communication is only possible when the secrecy rate is positive (i.e., negative ergodic secrecy rate in these plots simply indicates that the eavesdropper node has a “better” channel condition compared to the legitimate destination node, and thus secure wireless communication is not viable). Figure 14.7 (b) and Figure 14.7 (c) also suggest that the eavesdropper node is disadvantaged when its position is at angle
is shortest when α=0, which coincidentally forms the shortest route path to the destination node. Moreover, in order to ensure positive secrecy we must choose the relay location at an angle below a certain value which, from Figure 14.7 (a), can be deduced to be approximately 60°. Figure 14.7 (b) and Figure 14.7 (c) also indicate that there would not be any secrecy if the eavesdropper is within a certain distance range and/or angle to the source node, irrespective of the transmit signal energy. Figure 14.7 (d) reveals the possibility of achieving a higher secrecy rate by increasing the relay distance coupled with increasing the transmit SNR if the relay angle is fixed. It is also important to note that secure communication is only possible when the secrecy rate is positive (i.e., negative ergodic secrecy rate in these plots simply indicates that the eavesdropper node has a “better” channel condition compared to the legitimate destination node, and thus secure wireless communication is not viable). Figure 14.7 (b) and Figure 14.7 (c) also suggest that the eavesdropper node is disadvantaged when its position is at angle ![]() or when the distance
or when the distance ![]() (under the assumptions of the network topology considered herein). These parameters could also be a precursor to determining the threshold distance and/or angle at which to position or select the cooperating relay node in order to achieve a positive secrecy rate.
(under the assumptions of the network topology considered herein). These parameters could also be a precursor to determining the threshold distance and/or angle at which to position or select the cooperating relay node in order to achieve a positive secrecy rate.
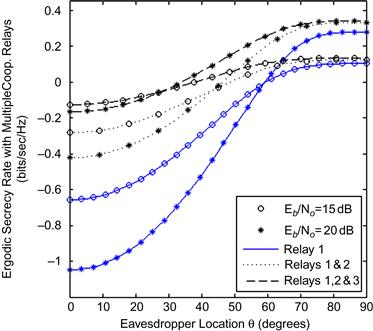
Effects of increasing number of cooperative relays
In the presence of multiple cooperating relays, the secrecy rate can be expressed as in (11) (instead of equation (6)):
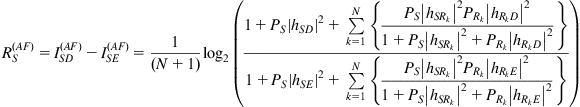 (11)
(11)
where N denotes the number of cooperating relays. Without any loss of generality, we assume that the fading parameters for various links are distributed according to Table 14.1 with m=1 for the links that are subject to Nakagami-m fading, while the source-relay distances and the relay location angles are assumed to be ![]() . Moreover, we arbitrarily assume an equal transmit power allocation strategy
. Moreover, we arbitrarily assume an equal transmit power allocation strategy ![]() such that
such that ![]() , where
, where ![]() corresponds to the transmit power allocation ratio during the first phase of cooperative transmission while
corresponds to the transmit power allocation ratio during the first phase of cooperative transmission while ![]() ,
, ![]() , and
, and ![]() denote power allocation ratios corresponding to the multiple cooperative relays during the second phase of transmission. It is evident from Figure 14.8 that the ergodic secrecy rate improves with increase in the angle
denote power allocation ratios corresponding to the multiple cooperative relays during the second phase of transmission. It is evident from Figure 14.8 that the ergodic secrecy rate improves with increase in the angle ![]() subtended by the eavesdropper as well as in the presence of multiple cooperative relays, subject to the prescribed transmit power allocation ratios during the distinct transmission phases. It is interesting to note that a positive secrecy rate is not achievable below a certain value of
subtended by the eavesdropper as well as in the presence of multiple cooperative relays, subject to the prescribed transmit power allocation ratios during the distinct transmission phases. It is interesting to note that a positive secrecy rate is not achievable below a certain value of ![]() while increasing the mean SNR of the links does have a significant positive impact on the achievable ergodic secrecy rate.
while increasing the mean SNR of the links does have a significant positive impact on the achievable ergodic secrecy rate.
Effects of increasing number of eavesdroppers
Figure 14.9 depicts the effects of varying the number of eavesdroppers where all the distinct channels are assumed to experience Nakagami-m fading. It can be observed that the ergodic secrecy rate reduces with the increasing number of eavesdroppers. This trend is expected as the ergodic secrecy rate is dictated by the “best” source-eavesdropper channel (see equation (5)). For example, there is a reduction in the secrecy rate from approximately 0.25 bits/sec/Hz to 0.15 bits/sec/Hz for m=2.5 and ![]() when the number of eavesdropper is increased from one to three.
when the number of eavesdropper is increased from one to three.
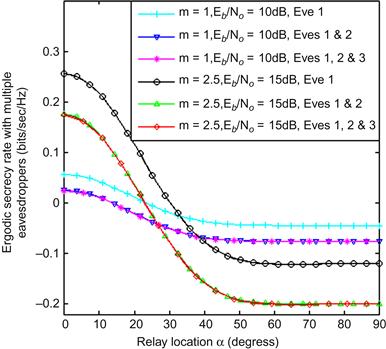
Figure 14.9 Ergodic secrecy rate of a CAF relay network (depicted in Figure 14.1 with multiple eavesdroppers at angles ![]() (Eve1),
(Eve1), ![]() (Eve2), and
(Eve2), and ![]() (Eve3)) plotted as a function of the relay location angle in a Nakagami-m environment and equal transmit power allocation policy (
(Eve3)) plotted as a function of the relay location angle in a Nakagami-m environment and equal transmit power allocation policy (![]() ).
).
Conclusion
In this chapter, we have demonstrated that cooperative relays can be exploited to enhance the wireless physical layer security of the classical Wyner wire-tap channel. We have also presented a unified analytical framework based on the MGF method to approximate the ergodic secrecy rates of cooperative amplify-and-forward variable-gain relay networks in a myriad of fading environments. Since the cooperative relaying architecture offers a flexible and a modular approach for increasing the ergodic secrecy rates (i.e., using physical layer security approaches) at a low cost but without requiring an antenna array, it is an attractive proposition for providing a “more secure” wireless communication (i.e., prevents eavesdropping) in wireless sensor networks without (or with only limited) upper layer data encryption. These results may be exploited to develop policies and/or algorithms for secure wireless communications.
It is also critically important to be able to accurately estimate the ergodic secrecy rates for other variations of the node-cooperation strategies (e.g., fixed-gain versus variable gain relays, “opportunistic” relaying, and decode-and-forward protocols) and these are recommended for future research. Further research and development of asymptotic closed-form approximations for the ergodic secrecy rates of cooperative relay networks are also highly desirable for system-level optimization. A comprehensive study on the impact of path correlations on the achievable ergodic secrecy rates of both non-cooperative and cooperative wireless networks are also of significant theoretical and practical interest, and is highlighted here to motivate further research in this direction.
Appendix
In this appendix, we outline the derivation of an “exponential-type” integral representation for the logarithmic function ln γ when γ > 0. Such a representation will facilitate the statistical averaging problem that is typically encountered in the average capacity analysis over fading channels, and therefore leads to a unified approach for calculating the ergodic capacity of cooperative amplify-and-forward relay networks in a myriad of fading environments. Utilizing [19, eq. (1.512.2)], we have
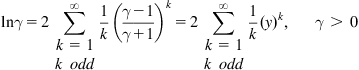 (A.1)
(A.1)
where ![]() . Substituting
. Substituting ![]() [19, eq. (3.381.4)] into (A.1), we obtain
[19, eq. (3.381.4)] into (A.1), we obtain
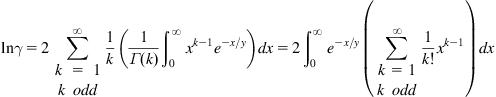 (A.2)
(A.2)
Recognizing that ![]() [19, eq. (1.411.2)], (A.2) can be re-stated as
[19, eq. (1.411.2)], (A.2) can be re-stated as
![]() (A.3)
(A.3)
Finally, using variable substitution![]() , we arrive at (A.4) after some routine algebraic manipulations:
, we arrive at (A.4) after some routine algebraic manipulations:
![]() (A.4)
(A.4)
It is also obvious from (A.4) that
![]() (A.5)
(A.5)
Incidentally, the second term in (A.5) is identical to [18, eq. (6)]. However, it should be emphasized that in Lemma 1 of [18, eq. (6)], the author indicated that his representation for (A.5) is valid only for ![]() instead of
instead of ![]() (from our derivation). In fact, if one starts the derivation with the power series for ln γ shown in [19, eq. (1.512.3)] (which was used in [18]), then the representation in (A.4) would be valid for any
(from our derivation). In fact, if one starts the derivation with the power series for ln γ shown in [19, eq. (1.512.3)] (which was used in [18]), then the representation in (A.4) would be valid for any ![]() . In this case, the resulting expression [18, eq. (6)] cannot be used for the ergodic capacity analysis of the optimal power and rate adaptation (OPRA) policy. Perhaps for this reason, [20] had abandoned the approach in [18] and attempted to develop yet another MGF-based method based on the Ei-transform to unify the analysis of ergodic capacities of CAF relay networks with different source adaptive transmission policies over generalized fading channels.
. In this case, the resulting expression [18, eq. (6)] cannot be used for the ergodic capacity analysis of the optimal power and rate adaptation (OPRA) policy. Perhaps for this reason, [20] had abandoned the approach in [18] and attempted to develop yet another MGF-based method based on the Ei-transform to unify the analysis of ergodic capacities of CAF relay networks with different source adaptive transmission policies over generalized fading channels.
References
1. Wyner AD. The wire-tap channel. Bell Syst Tech Journal. 1975;54(8):1355–1367.
2. Csiszár I, Körner J. Broadcast channels with confidential messages. IEEE Trans Inf Theory. 1978;IT-24(3):339–348.
3. Diffie W, Hellman M. New directions in cryptography. IEEE Trans Inf Theory. 1976;IT-22(6):644–654.
4. Maurer U. Secret key agreement by public discussion from common information. IEEE Trans Inf Theory. 1993;39(3):733–742.
5. Bloch M, Barros J, Rodrigues MRD, McLaughlin SW. Wireless information theoretic security. IEEE Trans Inf Theory. 2008;54(6):2515–2534.
6. Gopala PK, Lai L, El Gamal H. On the secrecy capacity of fading channels. IEEE Trans Inf Theory. 2008;54(10):4687–4698.
7. Liang Y, Poor V, Shamai S. Secure communication over fading channels. IEEE Trans Inf Theory. 2008;54(6):2470–2492.
8. Khisti A, Wornell G. The MIMOME channel. Proc 45th Annual Allerton Conference on Communication, Control and Computing; 2007; Monticello.
9. Oggier F, Hassibi B. The secrecy capacity of the MIMO wiretap channel. Proc IEEE International Symposium on Information Theory. Toronto; 2008 Jul. p. 524–28. Also appeared in IEEE Trans Information Theory 2011;57(8):4961-72.
10. Tekin E, Yener A. The general Gaussian multiple access and two-way wire-tap channels: Achievable rates and cooperative jamming. IEEE Trans Inf Theory. 2008;54(6):2735–2751.
11. Lai L, El Gamal H. The relay-eavesdropper channel: Cooperation for secrecy. IEEE Trans Info Theory. 2008;54(9):4005–4019.
12. Tang X, Liu R, Spasojevic P, Poor HV. The Gaussian wiretap channel with a helping interferer Toronto, Ontario, Canada: Proc IEEE ISIT; 2008 Jul.
13. Dong L, Han Z, Petropulu A, Poor V. Improving wireless physical layer security via cooperating relays. IEEE Trans Signal Processing. 2010;58(3):1875–1888.
14. Modi B, Annamalai A, Olabiyi O, Palat RC. Ergodic capacity analysis of cooperative amplify-and-forward relay networks over Rice and Nakagami fading channels. International Journal of Wireless & Mobile Networks. 2012;4(1):97–116.
15. Modi B, Olabiyi O, Annamalai A, Palat RC. Ergodic capacity analysis of cooperative amplify-and-forward relay networks over generalized fading channels with limited channel side-information. Wiley Journal on Wireless Communications and Mobile Computing; Published Online: August 1, 2013; DOI: 10.1002/wcm.2407.
16. Olabiyi O, Annamalai A. ASER analysis of cooperative non-regenerative relay systems over generalized fading channels. Proc 20th International Conference on Computer Communication and Networks; 2011 Aug; Maui. Also appeared in the International Journal of Computer Networks & Communications. 2012;4(6):1–20.
17. Olabiyi O, Annamalai A. Efficient symbol error rate analysis of cooperative non-regenerative relay systems over generalized fading channels. International Journal of Wireless & Mobile Networks. 2012;4(1):1–20.
18. Hamdi KA. Capacity of MRC on correlated Rician fading channels. IEEE Trans Communications. 2008;56:708–711.
19. Gradshteyn I, Ryzhik I. Table of integrals, series and products Academic Press 1995.
20. Renzo M, Graziosi F, Santucci F. Channel capacity over generalized fading channels: A novel MGF-based approach for performance analysis and design of wireless communication systems. IEEE Trans Veh Technol. 2010;59(1):127–149.
21. Simon MK, Alouini MS. Digital communication over fading channels 2nd ed. John Wiley & Sons 2005.
22. Anghel P, Kaveh M. Exact symbol error probability of a cooperative network in a Rayleigh-fading environment. IEEE Trans Wireless Communications. 2004;3(9):1416–1421.
23. Di Renzo M, Graziosi F, Santucci F. A unified framework for performance analysis of CSI-assisted cooperative communications over fading channels. IEEE Trans Communications. 2009;57:2551–2557.
24. Yacoub MD. The κ-μ distribution and the η-μ distribution. IEEE Antennas Propag Mag. 2007;49:68–81.
25. Annamalai A, Adebola E, Olabiyi O. Further Results on the Dirac delta approximation and the moment generating function techniques for error probability analysis in fading channels. International Journal of Computer Networks & Communications. 2013;5:1.
26. Zhang P, Yuan J, Chen J, Wang J, Yang J. Analyzing amplify-and-forward and decode-and-forward cooperative strategies in Wyner’s channel model. Proc IEEE Wireless Communications and Networking Conference 2009.