Investigating Radicalized Individual Profiles through Fuzzy Cognitive Maps
Babak Akhgar1, Fahimeh Tabatabayi2, Petra Saskia Bayerl3, Samir M.R. Nasserzadeh4 and Andrew Staniforth5, 1Sheffield Hallam University, Sheffield, UK, 2MehrAlborz University, Tehran, Iran, 3Erasmus University, Rotterdam, The Netherlands, 4University of Tehran, Tehran, Iran, 5North East Counter Terrorism Unit, West Yorkshire Police, West Yorkshire, UK
The use of cyberspace to disseminate radical materials and messages has become the predominant method used by extremists to recruit and radicalize individuals to their cause. The phenomenon of online radicalization is increasing, presenting pressing security concerns. In direct response to the emerging threats and risks arising from online radicalization, global efforts are being made to monitor and disrupt contemporary cyber avenues of terrorist recruitment. Individuals, particularly young computer-literate males, are becoming self-radicalized through access to sophisticated online materials promoting and justifying extreme views and actions. The detection of these self-radicalized individuals is challenging. This chapter outlines a computational approach based on Fuzzy Cognitive Maps (FCMs) for the identification of radicalized individuals online. The model aims to inform and support the classification of individual profiles to tackle terrorist activities in the future.
Keywords
radicalization process; online self-radicalization; radicalized individual profiles; Fuzzy Cognitive Maps (FCM); causal relationships
Information in this chapter
• Review of current models on radicalization: How can it happen?
• Overview of analysis methods for online radical profiles
• Fuzzy Cognitive Mapping as an approach to model causality in online radicalization
Introduction
The openness and freedom of the Internet unfortunately supports “self-radicalization,” that is, the radicalization of individuals without direct input or encouragement from others. The role of the Internet in both radicalization and the recruitment into terrorist organizations has therefore become a growing source of concern. The Internet allows individuals to find people with shared views and values and to access information to support their radical beliefs and ideas. The unregulated and ungoverned expanse of the Internet knows no geographical boundaries, thus creating a space for radical activists to connect across the globe. This is especially problematic as the easy access to like-minded people helps to normalize radical ideas such as the use of violence to solve problems [1,2].
Yet, solving the issue of radicalization by simple processes (e.g., the suggestion of “cleaning up” the Internet) is impossible [3]. Part of the problem is that claims that terrible things are happening on extremist websites and in Internet chat-rooms are difficult to verify [1,4]. Consequently, many of the current policy proposals to address this security challenge are either unrelated to the issue or lack a sound empirical basis. We argue that this requires an alternative and more comprehensive approach that takes the complex nature of the problem into account and that can be integrated into any policy aimed at tackling online radicalization.
Identifying radicalized individuals is a complex task. There is still scant research in this field, and the automatic and semi-automatic models presented thus far are not capable of identifying individuals and their profiles in a comprehensive manner. In this chapter we introduce Cognitive Maps and Web mining as techniques for an alternative approach to the classification of online radicalized individuals. In the first part of this chapter, we review current models on the radicalization process, which provide the basis for the modeling of online radicalization. The second part of the chapter outlines the use of data mining and artificial intelligence methods in this context.
The radicalization process: How can it happen?
In a recent review on the radicalization process, Christmann [5] identified eight important models or perspectives on the subject of the radicalization process:
1. Marc Sageman’s four-stage process
2. Taarnby’s eight-stage recruitment process
3. The Prevent Pyramid, developed by the Association of Chief Police Officers (ACPO)
4. The New York Police Department’s four-stage radicalization process
6. Wiktorowicz’s al-Muhajiroun model
7. McCauley and Moskalenko’s 12 mechanisms of political radicalization
Marc Sageman’s four-stage process
According to Sageman [6], the radicalization process progresses in four steps that reinforce each other. The process commences with “moral outrage,” which is then “interpreted in a specific way” by the person (e.g., through interactions on online forums). The third step demands that radical ideas “resonating with own personal experiences” are supported by interactions with like-minded people. These ideological groups give the inividual and other groups further self-confidence by justifying their ideologies, actions, and beliefs. In the final step, individuals may be “mobilized through a network” [7]. Although called a four-stage model, these stages are not necessarily considered as sequential.
Taarnby’s eight-stage recruitment process
Drawing heavily on Sageman’s [8,9] work, Taarnby [10] outlines the structure of a recruitment process in eight stages:
1. Individual alienation and marginalization
3. A process of radicalization
4. Meeting and associating with like-minded people
5. Gradual seclusion and cell formation
6. Acceptance of violence as a legitimate political means
The prevent pyramid
In the Prevent Pyramid, developed by the Association of Chief Police Officers (ACPO), radicalization is described as a gradual change from being part of a broad base of sympathizers to becoming an active terrorist [11]. What is notable in this model is a linear development across four tiers (see Table 35.1). This linear view stands in contrast to other authors such as Bartlett, Birdwell, and King [12], who believe that radicalization is an unforseeable and non-linear phenomenon.
Table 35.1
| Tiers | Level of Radicalization | Description |
| Tier 1 | All members of the community (Universal approach) | Wider community; unclear how broad this group actually is |
| Tier 2 | The vulnerable (Targeted approach) | Not committing any violent acts, but providing tacit support to the top of the pyramid |
| Tier 3 | Moving toward extremism (Interventionist approach) | Support group; larger group than the group who belongs to the 4th tier |
| Tier 4 | Actively breaking the law (Enforcement approach) | Active terrorists; relatively few in number |
The New York police department’s four-stage radicalization process
The New York Police Department (NYPD) [13] proposed a four-stage process from pre-radicalization to jihadization. This model is based on the systematic examination of eleven in-depth case studies of “Al Qa’ida-influenced radicalization and terrorism.” Details of the four phases are presented in Table 35.2.
Table 35.2
The NYPD Four-Stage Radicalization Process
| Stages of the Process | Description of the Stages |
| Pre-radicalization | A person’s life situation before radicalization creates a vulnerability to radicalization (“at risk” group; comparable to Tier 3 in the Prevent Pyramidal model). |
| Self-identification | Beginning of association with like-minded individuals and adoption of the ideology as their own. A “cognitive opening” acts as a catalyst in this stage. Individuals leave their previous beliefs and are ready to accept new idealogies. |
| Indoctrination | Intensifying of individuals’ beliefs, and finally, whole-hearted adoption of the ideology. This stage is faciliated by a “spiritual sanctioner” and association with like-minded people to deepen the beliefs (comparable to Tier 3 in the Prevent Pyramidal model). |
| Jihadization | The operational phase in which members may carry out acts of violence and terrorist attacks. |
Gill’s pathway model
Gill [14] proposed a pathway model for an individual’s development across four key stages on the way to becoming a suicide bomber. The stages are summerized in Table 35.3.
Table 35.3
| Stages of the Process | Description |
| Broad socialization process | Exposure to propaganda that tends toward violence |
| Catalysts | Catalysts motivate joining an extremist organization |
| Pre-existing ties to aid recruitment | Kinship and friendship ties faciliate recruitment phase |
| Suicide bombers | Internalization of the group’s norms and values |
Wiktorowicz’s al-Muhajiroun model
Wiktorowicz [15] focused on the role that social influences play in leading a person to join a radicalized Islamic group. He proposed his model in a four-stage process from cognitive opening to socialization, as shown in Table 35.4.
Table 35.4
Wiktorowicz’s al-Muhajiroun Model
| Stage of the Process | Description |
| Cognitive opening | Where a person can gain new ideas and world views |
| Religious seeking | Where a person seeks meaning through a religious framework |
| Frame alignment | Where the public representation offered by the radical group “makes sense” to the seeker and attracts the initial interest |
| Socialization | Where a person experiences religious instruction that facilitates indoctrination, identity-construction, and value changes |
McCauley and Moskalenko’s 12 mechanisms of political radicalization
Instead of suggesting a process model, McCauley and Moskalenko [11] identified twelve “mechanisms” of political radicalization. These mechanisms operate across three levels: individual, group, and “the mass.” The mechanisms are listed in Table 35.5.
The staircase to terrorism
Moghaddam [16] offers a sophisticated “multi-causal approach” with the aim “to understand suicide terrorism [foregoing] the pathway metaphor in favour of the analogy of a narrowing ‘staircase to terrorism’” ([5] p. 16). The model is composed of three levels, but suggests to focus on the individual (dispositional factors), organizations (situational factors), and the environment (socio-cultural, economic, and political forces). The radicalization process progresses in six steps using the metaphor of a staircase (see Table 35.6). As Christmann [5] explains the model, “Moghaddam’s metaphor is of a staircase housed in a building where everyone lives on the ground floor, but where an increasingly small number of people ascend up the higher floors, and a very few reach the top of the building to carry out a terrorist act.”
Table 35.6
| Description | |
| Ground floor | Psychological interpretation of material conditions |
| First floor | Perceived options to fight unfair treatment |
| Second floor | Displacement of aggression |
| Third floor | Moral engagement |
| Fourth floor | Categorical thinking and the perceived legitimacy of the terrorist organization |
| Fifth floor | The terrorist act and sidestepping inhibitory mechanisms |
A psychological model for the process of radicalization by Davis et al.
A variety of additional theories to the ones reviewed by Christmann [5] strive to depict the extremism and the radicalization process. Biological theories, for instance, address age and gender-related factors affecting vulnerability to radicalization (e.g., [17,18]. Social theories consider the effects of deprivation and segregation, political crises, social bands and networks, and the role of religion [5,19], while psychological theories refer to the attributes forming the terrorist personality through a review of pathological processes.
Integrating multiple case studies, Davis, Atran, Sageman, and Rijpkema [20] developed a psychological model for the process of radicalization. Their model considers three aspects:
1. Radicalization as changing moral priorities
2. Cognitive dissonance and individual radicalization
3. Vicarious cognitive dissonance and network radicalization
The model thus focuses on the relationship between ideas and behaviors at both the individual and the network levels. The assumptions of this social-cognitive model can be summarized as follows (cp. [20]:
• There is no reliable demographic pattern describing those who become radicalized; instead, highly developed group bonds seem important precursors of collective radical action.
• A sophisticated ideological basis for radical action is not a necessary precursor of radical action, and violent networks are not distinguishable from the communities they are embedded within by a special sense of moral outrage.
• A formal process of recruitment and “brainwashing” is not a necessary feature of radicalization.
• The pathway to violence is typically a gradual one, on both individual and collective levels.
The central concept of this model is that cognitive dissonance occurs across networks of individuals observing each other, demonstrating how radicalization may spread through networks [19].
The suite of models designed to better understand the phenomenon of radicalization covers a broad range of perspectives. While the complexity of addressing the security challenges of radicalization are shown in the sheer number of models, they also provide evidence that our collective understanding of the radicalization process remains far from perfect. Still, the models do share common traits. For example, there appears to be strong recognition in all models that becoming involved in violent extremism through radicalization is a process: it does not happen all at once. Similarly, the idea that there is a simple psychological profile to describe terrorists has been abandoned. Reviewing the models, it becomes clear that there have been substantial steps forward to understanding the development of individuals into terrorists. Still, the inconsistencies across models also demonstrate that immense gaps in understanding of the radicalization process remain and that considerably more research is required to identify the factors that influence online radicalization.
Investigating radical online profiles: A short overview of existing methods
Nowadays all prominent extremist groups have established at least one form of presence on the Internet [21]. The increasing sophistication and interactivity of extremists online has led to considerable challenges in detecting radical online content; among them the coverage of content, the often ephemeral nature of the content, and the diversity of data formats. The rise of social media has increased the challenge only further [21,22]. Accordingly, robust methods are needed to identify radical online profiles. A number of methods have been suggested over the last years to tackle this task. Table 35.7 provides a short summary of existing approaches based on general Web mining methods. Table 35.8 summarizes approaches specializing in online radicalization.
Table 35.7
Overview of General Web Mining Methods
| Method | Description of the Method | Sources |
| Resource mobilization | The process of securing control over resources needed for collective action such as communications, money, information, human assets, and specialized skills | [23] |
| Web harvesting (or Web mining/Web farming) | The process of gathering and organizing unstructured information from pages and data on the Web using manual, semi-automatic, or automatic approaches to harvesting Web content in specific domains. | [21,24] |
| Web content harvesting | This approach is concerned with the specific content of documents such as HTML files, images, and email messages. Since such documents are scattered throughout the Web, the approach aims to exploit the semantic of known structures and to map these to a data model. | [25–27] |
| Web structure harvesting (Web link analysis) | This technique is based on the analysis of hyperlink structures and is used to discover hidden relationships among Web communities. The approach takes advantage of popular links from other sources, which point to a certain Web entity (i.e., Web pages, HTML or XML tags). As an important indicator, it uses the popularity and the frequency of visitors of the page. | [28,29] |
| Web usage harvesting | This harvesting technique uses data about usage patterns of Web pages (i.e., IP addresses, page references, the date and time of use) recorded and stored by Web servers to investigate, track, and evaluate user behavior and Web structures. | [30,31] |
Table 35.8
Overview of Methods for the Mining of Online Radicalized Profiles



1The average of the lengths of the shortest paths between all pairs of nodes in a network.
2The number of links that actually exist among node i’s neighbors over the possible number of links among these neighbors.
3The probability that an arbitrary node has exactly k links.
4“Degree is defined as the number of direct links a node has. ‘Popular’ nodes with high degree scores are the leaders, experts, or hubs in a network. It has been shown that these popular nodes can be a network’s ‘Archilles’ Heel,’ whose failure or removal will cause the network to quickly fall apart.”
5“Betweenness of a node is defined as the number of geodesics (shortest paths between two nodes) passing through it. Nodes with high betweenness scores often serve as gatekeepers and brokers between different communities.”
6“Closeness is the sum of the length of geodesics between a particular node and all the other nodes in a network.”
7“Fisheye view is a kind of nonlinear magnification technique. It maintains the same screen size by magnifying the region surrounding the focus while compressing the distant regions without losing the global structure of the network.”
8“Fractal view identifies a focus’s context based on its associations with other nodes. It enhances the view of focus and its context by reducing less relevant information.”
Fuzzy cognitive mapping of factors for self-radicalization as an alternative approach
Our approach is based on Cognitive Mapping (CM). CMs are a means to visualize the causal relationships between concepts in a particular domain. In our approach, we employ Fuzzy Cognitive Maps (FCMs), as they also provide feedback mechanisms to support decision-making. In the following, we detail the application of FCMs as a promising approach for the modeling, identification, and extraction of factors affecting online behavior of radicalized individuals or groups and the simulation of e-radicalization.
Methodological background
From an artificial intelligence perspective, FCMs constitute neuro-fuzzy systems, which are able to incorporate expert knowledge. This is a soft computing technique, which is capable of dealing with complex situations representing how humans reason about a domain [36,37].
The most pronounced features of FCMs are their flexibility in system design, model, and control as well as the possibility for comprehensive operation and abstractive representation of behaviors within complex systems. FCMs are signed graphs, which capture cause-effect relationships in an integrated system. The nodes of the graph (also referred to as concepts) represent the key factors and attributes of the modeled system such as inputs, outputs, states, events, actions, goals, and trends. Variables that cause a change are called Cause Variables, while those that undergo the effect of the change in the cause variable are called Effect Variables. Signed weighted arcs describe the causal relationships among nodes in the graph. The causal relationships link nodes to each other in either a positive or a negative way. If the relationship is positive, an increase or decrease in a cause variable results in a change of the effect variable(s) in the same direction. The weight in the signed arc determines the degree of causality (i.e., change) between the linked concepts. The resulting graph of nodes and arcs provides a clear representation of how concepts influence each other and how high the degree of influence is [36,38–40].
FCM nodes are named concepts forming the set of C={C1, C2, ... ,Cn}. Arcs (Cj, Ci) are oriented and represent causal links between concepts, i.e., they indicate in which way concept Cjinfluences concept Ci. Arcs are elements of the set ![]() . Weights of arcs are associated with a weight value matrix Wn×n, in which each element of the matrix wji∈ [−1,1] ∪R, such that if (Cj, Ci)∉A, then wji=0 – the weights for excitation (respectively inhibition) causal links from concept Cj to concept Ciare wji> 0 (respectively wji<0). The proposed methodology framework assumes that [−1, 1] is a fuzzy bipolar interval, in which bipolarity represents a positive or negative relationship [37,41].
. Weights of arcs are associated with a weight value matrix Wn×n, in which each element of the matrix wji∈ [−1,1] ∪R, such that if (Cj, Ci)∉A, then wji=0 – the weights for excitation (respectively inhibition) causal links from concept Cj to concept Ciare wji> 0 (respectively wji<0). The proposed methodology framework assumes that [−1, 1] is a fuzzy bipolar interval, in which bipolarity represents a positive or negative relationship [37,41].
In every cycle, the value ith of each concept Ci is computed. By combining the impacts of all concepts related to a concept Ci and by squashing the overall impact using a barrier function f, we obtain the following rule for determining the value of Ci after each new cycle:
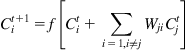
where ![]() and
and ![]() are the values of concept i at times t+1 and t respectively, Wjiis the weight value of the directed interconnection from concept j to concept i, and f is the barrier function used to restrict the concept value into the range [0,1] [36,42–44].
are the values of concept i at times t+1 and t respectively, Wjiis the weight value of the directed interconnection from concept j to concept i, and f is the barrier function used to restrict the concept value into the range [0,1] [36,42–44].
In general, the design of FCMs requires experts who have knowledge of the modeled domain and at the same time knowledge about the FCMs formalism. However, since even medium-sized models involve a large number of parameters such as concepts and weights, it is often difficult to obtain satisfactory performance and accuracy. At times, a group of experts is used to design a FCM. In this case, additional parameters such as credibility coefficients for each individual expert need to be estimated, which adds to the complexity of the design process [37]. Also, experts are not always able to express their expertise in explicit terms.
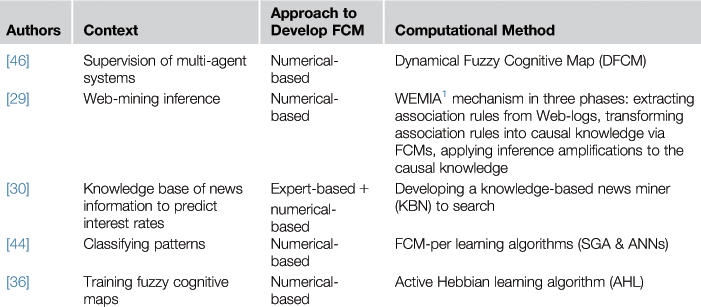
Therefore, new ways of capturing knowledge, such as learning algorithms, have been defined to improve the capabilities of FCMs [36,45]. In this method, not only casual relations between nodes, but also the strength of each edge, is determined based on historical data, which is extracted by computational procedures. During the learning process, the weight of edges in an FCM are modified to find the desired connection matrix. The values of all edges connected to a node will be modified as soon as the value of a concept changes, allowing the model to behave in a dynamic manner [45]. The value of this method for the development of FCMs for the Web has been demonstrated in several studies. Table 35.9 provides some examples.
Application of FCMs for the analysis of the online radicalization process
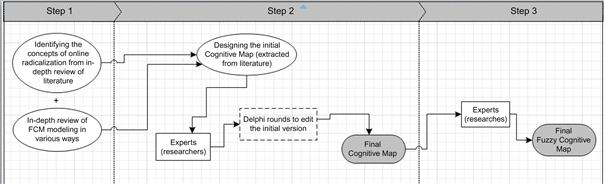
We used the clear benefits of FCMs to develop a new mathematical method to enable the causal modeling of self-radicalization processes. This new CM is based on mapping factors known to encourage or discourage individuals to become self-radicalized. The factors are chosen based on reviews of the empirical literature. Table 35.10 provides an overview of important influencing factors established through a literature review of nearly twenty journal papers, reports, and working papers. This table can be used as direct input for the development of FCMs to model online radicalization. The development of FCMs is conducted in three steps, which are outlined in Figure 35.1.
Table 35.10
Factors Affecting Online Self-Radicalization
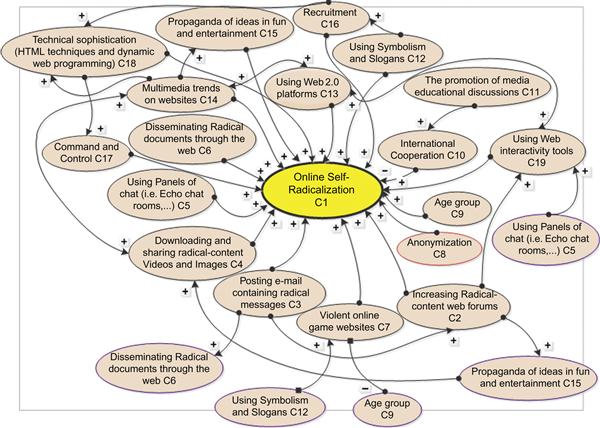
| Online Self-Radicalization Factors (Concepts) (C1) | Polarity (+/−) No relation | Authors |
| Increasing radical-content Web forums (C2) | + | [1,35,47–49] |
| Posting e-mail containing radical messages (C3) | + | [1,35,50–53] |
| Downloading and sharing radical-content videos and images (C4) | + | [1,35,54–58] |
| Using panels of chat (i.e., echo chatrooms) causes creation of homogeneous groups (C5) | + | [1,59,35,50,53,52,47,49] |
| Disseminating radical documents through the Web (i.e., a variety of instructional materials, ideologies, and propaganda) (C6) | + | [1,35,54–56,58,60] |
| Violent online games websites (C7) | + | [35,56,49] |
| Anonymization (the Internet creates an anonymous sphere to depersonalize participants (C8) | +/No relation | [5,47,49] |
| Age group and gender (youth are more vulnerable than adults) (C9) | +/No relation | [61,56] |
| Strengthening international inter-agency cooperation (C10) | − | [57,60,48] |
| The promotion of media educational discussions (C11) | − | [56] |
| Using symbolism and slogans (to attract younger users) (C12) | + | [62,56] |
| Using Web 2.0 platforms; i.e., social networks and video platforms (in order to approach younger users) (C13) | + | [35,53,56] |
| Multimedia trends on the websites (C14) | + | [7,47,58] |
| Propaganda on the Internet to attract youth (“Dehumanizing ideas wrapped in fun and entertainment” ) (C15) | + | [62,60,48,49] |
| Recruitment and training (C16) | + | [62,21,58] |
| Command and control (C17) | + | [21,58] |
| Technical sophistication (basic HTML techniques, advanced HTML, and dynamic Web programming used to enable users to remain anonymous) (C18) | + | [57,58] |
| Web interactivity tools (one-to-one interactivity, community-level interactivity, transaction-level interactivity) (C19) | + | [47,57,58] |
Our FCM-approach considers variables determining alternative paths for online radicalization as well as the relationships among the variables. Each mutual relationship can include one linguistic fuzzy weight, which determines the accuracy of the expert choice. For each relationship, planners should answer the following question during the modeling: How strongly, do you believe, is the causal relationship between variable (X) and variable (Y)? The influence of one concept on another is interpreted as a linguistic variable taking values in the universe U=[−1,1], for which its term set T(influence) could be: T(influence)={negatively strong, negatively medium, negatively weak, zero, positively weak, positively medium, positively strong} [39]. For our purposes, we define the quantity space of the weight relationships Q(w) as the set: Q(w): {Undefined; Weak; Moderate; Strong} assuming the following order for Q(w): {Weak<Moderate<Strong} [63].
The resulting FCM represents the belief planners share with regard to the existence of certain relationships, yet not the magnitude of the change a variable may undergo because of its causal relationship with all connected variables. To aggregate the answers collected from experts, the Mamdani fuzzy operator is applied [64,65]. Aggregating the expert judgments with the aid of the fuzzy toolbox in the MATLAB software, a signed, directed CM of online self-radicalization results. An example for such a graph, based on the information in Table 35.10, is shown in Figure 35.2.
Conclusion
The world in which we now live is increasingly interconnected and interdependent. The tremendous growth in Internet use and mobile connectivity has provided widespread security concerns from government and security agencies. While the Internet has provided positive advances in communications, there remains a small number of individuals who seek to destroy our democratic values by harnessing the power and influence of the Internet to progress their own extremist causes. Innovative approaches are needed to identify and prevent online radicalization and activities that may lead to insecurity.
As the tools of radicalization are increasingly being disseminated via the Internet, security practitioners are seeking techniques to recognize the common profiles of self-radicalized individuals and indications of radicalization to prevent those vulnerable to radicalization from adopting extremist views and to pursue those who seek to harm others. In this chapter, we present Fuzzy Cognitive Maps as an approach for the modeling and visualization of causal relationships among factors affecting online radicalization. With their sound mathematical underpinnings, Fuzzy Cognitive Maps created in this rigorous fashion allow analysts to confidently assess the causes of self-radicalization. They can further support the development of better strategies to prevent online self-radicalization. This serves to provide security practitioners with better opportunities to protect the communities they serve from the threats arising from individuals radicalized online.
References
1. Institute for Strategic Dialogue. I. f. Radicalisation: The role of the Internet: A working paper of the Ppn. Institute for Strategic Dialogue. n.d.
2. Zhou Y, Reid E, Qin J, Chen H, Lai G US. Domestic Extremist Groups on the Web: Link and Content Analysis. Intelligent Systems. 2005;20(5):44–51.
3. Stevens T, Neumann R. Countering Online Radicalisation A Strategy for Action London: ICSR; 2009.
4. Pantucci R, Rubin H. A Typology of Lone Wolves: Preliminary Analysis of Lone Islamist Terrorists London: ICSR; 2011.
5. Christmann K. Preventing religious radicalisation and violent extremism: A systematic review of the research evidence. Youth Justice Board for England and Wales 2012.
6. Sageman M. Leaderless Jihad Terror Networks in the 21st Century Philadelphia, Pennsylvania: University of Pennsylvania Press; 2008.
7. Tabatabayi F, Nasserzadeh SMR, Yates S, Akhgar B, Lockely E, Fortune D From local to global: Community-based policing and national security. Akhgar B, Yates S, editors. In: Strategic Intelligence Management: National Security Imperatives and Information and Communications Technologies. Elsevier; 2013. p. 85–92.
8. Sageman M. Understanding Terror Networks Philadelphia: University of Pennsylvania Press; 2004.
9. Sageman M. A Strategy for Fighting International Islamist Terrorists. Ann Am Acad Pol Soc Sci. 2008;618(1):223–231.
10. Taarnby M. Recruitment of Islamist Terrorists in Europe: Trends and Perspectives. Danish Ministry of Justice 2005.
11. McCauley C, Moskalenko S. Mechanisms of political radicalization: pathways toward terrorism. Terrorism and Political Violence. 2008;20(3):415–433.
12. Bartlett J, Birdwell J, King M. The Edge of Violence. Demos 2010.
13. NYPD. Radicalisation in the West: The Homegrown Threat. New York; 2007.
14. Gill P. Suicide Bomber Pathways Among Islamic Militants. Policing: A Journal of Policy and Practice. 2008;4(2):414–422.
15. Wiktorowicz Q. Joining the Cause:Al-Muhajiroun and Radical Islam. The Roots of Radical Islam, Department of International Studies, Rhodes College, 2004.
16. Moghaddam FA. From the terrorists’ point of view: Toward a better understanding of the staircase to terrorism. In: Stritzke WGK, Lewandowsky S, Denemark D, Clare J, Morgan F, eds. Terrorism and Torture: An Interdisciplinary Perspective New York, United States: United States of America by. Cambridge University Press 2009;10624.
17. Bakker E. Jihadi terrorists in Europe, their characteristics and the circumstances in which they joined the Jihad: An exploratory study. The Hague: Netherlands Institute of International Relations; 2006.
18. Wadgy L. The psychology of extremism and terrorism: A Middle-Eastern perspective. Aggression and Violent Behaviour. 2007;12(2):141–155.
19. Rijpkema R. Theoretical frames on pathways to violent radicalization. Office of Naval Research 2009.
20. Davis R, Atran S, Sageman M, Rijpkema R. Theoretical Frames on Pathways to Violent Radicalization. Office of Naval Research 2009.
21. Correa D. Solutions to detect and analyze online radicalization. IIITD; 2011.
22. MacKinnon L, Bacon L, Gan D, Loukas G, Chadwick D, Frangiskatos D. Cyber security countermeasures to combat cyber terrorism. In: Akhgar B, Yates S, eds. In: Strategic Intelligence Management: National Security Imperatives and Information and Communications Technologies. Elsevier 2013;234–257.
23. Gustavson T, Sherkat DE. Elucidating the web of hate. The ideological structuring of network ties among right wing hate groups on the Internet Annual Meetings of the American Sociological Association 2004.
24. Qin J, Zhou Y, Reid E, Lai G, Chen H. Analyzing terror campaigns on the internet: technical sophistication,content richness, and Web interactivity. Int J Hum Comput Stud. 2007;65:71–84.
25. Kay R. Web Harvesting. Computer World. [Internet] Jun 21. Retrieved from: <http://www.computerworld.com>; 2004.
26. Reilly B, Tuchel G, Simon J, Palaima C, Norsworthy K, Myrick L. Political Communications Web Archiving: Addressing Typology and Timing for Selection, Preservation and Access, 3rd ECDL Workshop on Web Archives, Trondheim, Norway, 2003. Available online from: <http://old.diglib.org/pubs/news05_01/nyunews5.htm>.
27. Gerstenfeld PB, Grant DR, Chiang C. Hate online: a content analysis of extremist internet sites. Analysis of Social Issues and Public Policy. 2003;3(1):29–44.
28. Borgman L, Furner J. Scholarly communication and bibliometrics. In: Cronin B, ed. Annual Review of Information Science and Technology. Information Today 2002.
29. Chang Lee K, Sung Kim J, Ho Chang N, Jea Kwon S. Fuzzy cognitive map approach to web-mining inference amplification. Expert system with application. 2002;22:197–211.
30. Hong T, Han I. Knowledge-based data mining of news information on the Internet using cognitive maps and neural networks. Expert System with Application. 2002;23:1–8.
31. Srivastava J, Cooley R, Deshpande M, Tan P. Web usage mining: Discovery and applications of usage patterns from Web data. SIGKDD Explorations. 2000;1(2):1–12.
32. Chau M, Xu J. Mining communities and their relationships in blogs: a study of online hate groups. Int J Hum Comput Stud. 2006;65(1):57–70.
33. Yang CC, Liu N, Sageman M. Analyzing the terrorist social networks with visualization tools. Intelligence and Security Informatics. 2006;3975:331–342.
34. L’Huillier G, Alvarez H, Rios A, Aguilera F. Topic-based social network analysis for virtual communities of interests in the dark web. SIGKDD Explorations. 2010;12(2):66–73.
35. Chen H, Thoms S, Fu T. Cyber extremism in Web 2.0: An exploratory study of international Jihadist Taipei: IEEE; ISI; 2008; p. 98–103.
36. Papageorgiou EI, Stylios CD, Groumpos PP. Active Hebbian learning algorithm to train fuzzy cognitive maps. International Journal of Approximate Reasoning. 2004;37:219–249.
37. Stach W, Kurgan L, Pedrycz W, Reformat M. Genetic Learning of Fuzzy Cognitive Maps. Fuzzy Sets and Systems. 2005;153:371–401.
38. Craiger JP, Goodman DF, Weiss RJ, Butler A. Modeling Organizational Behavior with Fuzzy Cognitive Maps. International Journal of Computational Intelligence and Organisations. 1996;1:120–123.
39. Groumpos PP. Fuzzy cognitive maps: basic theories and their application to complex systems. In: Dr. Glykas M, ed. Fuzzy Cognitive Maps Advances in Theory, Methodologies, Tools and Applications. Springer-Verlag Berlin Heidelberg Publishers 2010;1–22.
40. Wei Z, Lu L, Yanchun Z. Using fuzzy cognitive time maps for modeling and evaluating trust dynamics in the virtual enterprises. Expert Systems with Applications. 2008;35:1583–1592.
41. Xirogiannis G, Glykas M. Intelligent modeling of e-business maturity. Expert Systems with Applications. 2007;32:687–702.
42. Stach W, Kurgan L, Pedrycz W. Expert-Based and Computational Methods for Developing Fuzzy Cognitive Maps. In: Dr. Glykas M, ed. Fuzzy Cognitive Maps Advances in Theory, Methodologies, Tools and Applications. Springer-Verlag Berlin Heidelberg Publishers 2010;23–41.
43. Kosko B. Fuzzy Cognitive Maps. Int J Man Mach Stud. 1986;24:65–75.
44. Papakostas GA, Koulouriotis DE. Classifying patterns using fuzzy cognitive maps. In: Glykas M, ed. Fuzzy Cognitive Maps Advances in Theory, Methodologies, Tools and Applications. Springer 2010;291–306.
45. Alizadeh S, Ghazanfari M. Learning FCM by chaotic simulated annealing. Chaos, Solitons and Fractals. 2009;41:1182–1190.
46. Aguilar J. Dynamic Fuzzy Cognitive Maps for the Supervision of Multiagent Systems. In: Dr. Glykas M, ed. Fuzzy Cognitive Maps Advances in Theory, Methodologies, Tools and Applications. Springer-Verlag Berlin Heidelberg Publishers 2010;307–324.
47. Preece J. Online communities: Designing usability, supporting socialability New York City: Wiley; 2000.
48. Thompson R. Radicalization and the use of social media. Journal of Strategic Security. 2011;4(4):167–190.
49. Yunos Z, Hafidz S. Cyber terrorism and terrorist use of ict and cyberspace. In: Searcct, Ramli DP, editors. Searcct’s Selection Of Articles. Kuala Lumpur, Malaysia: Southeast Asia Regional Centre for Counter-Terrorism (SEARCCT). 2011 (vol 2.).
50. Kahne J, Middaugh E, Lee N, Feezell JT. Youth online activity and exposure to diverse perspectives. New Media and Society 2011;1–21. doi 10.1177/1461444811420271.
51. Kelley J. Terror groups hide behind encryption. USA Today. [Internet]. Available at: <http://www.usatoday.com/tech/news/2001-02-05-binladen.html>; 2001.
52. Livingstone S, Bober M. Regulating the Internet at home: contrasting the perspectives of children and parents. In: Buckingham D, Willett R, eds. Digital generations: Children, young people and new media. Mahwah, NJ: Lawrence Erlbaum; 2004;93–113.
53. Lee E. When and how does depersonalization increase conformity to group norms in computer-mediated communication? Communic Res. 2006;33:423–447. doi 10.1177/0093650206293248.
54. Coll S, Glasser SB. Terrorists turn to the Web as base of operations. Washington Post. 2005;7.
55. Jenkins BM. World becomes the hostage of media-savvy terrorists: Commentary. USA Today. [Internet]. Available at: http://www.rand.org/>; 2004.
56. Mainz. Right-wing extremism online–Targeting teenagers with stylish websites. [Internet]. Available at: jugendschutz.net; 2009.
57. Qin J, Zhou Y, Reid E, Lai G, Chen H. Analyzing terror campaigns on the Internet: Technical sophistication,content richness, and Web interactivity. Int J Hum Comput Stud. 2007;65:71–84.
58. Weimann G. www.terror.net: How modern terrorism use the Internet. Special Report, US Institute of Peace. [Internet]. Available at <http://www.usip.org/pubs/specialreports/sr116.pdf>; 2004.
59. Becker A. Technology and terror: The new modus operandi. Frontline. [Internet]. Available at: <http://www.pbs.org/wgbh/pages/frontline/shows/front/special/tech.html>; 2004.
60. Reid E, Qin J, Zhou Y, et al. Collecting and analyzing the presence of terrorists on the web: a case study of Jihad websites. Intelligence and Security Informatics. 2005;3495:402–411.
61. Ashour O. Online de-radicalization? countering violent extremist narratives: Message, messenger and media strategy. Perspectives on Terrorism Terrorism Research Initiative 2010;15–20.
62. ISTS. Examining the cyber capabilities of Islamic terrorist groups. Report, Institute for Security Technology Studies. [Internet]. Available at: <http://www.ists.dartmouth.edu/>; 2004.
63. Axelrod R. Structure of decision: The cognitive maps of political elites Princeton, NJ: Princeton University Press; 1976.
64. Mendel. (2008). A short fuzzy logic tutorial. IEEE; 2008.
65. Tabatabaei F, Akhgar B, Nasserzadeh SMR, Yates S. Semulating online customer satisfaction using fuzzy cognitive mapping. ITNG 2012;540–547.