Leveraging Semantic Web Technologies for Access Control
Eugenia I. Papagiannakopoulou1, Maria N. Koukovini1, Georgios V. Lioudakis1, Nikolaos L. Dellas2, Dimitra I. Kaklamani1 and Lakovos S. Venieris1, 1National Technical University of Athens, Athens, Greece, 2SingularLogic Software and Integrated IT Solutions, Nea Ionia, Greece
Access control comprises a central concept in ICT security, leveraged for the protection of various resources, including systems, networks, applications, services, corporate assets, and information. It has also emerged as an important mechanism for the protection of personal data, resulting in a family of models referred to as privacy-aware access control. Due to the increasing complexity of the ICT ecosystem, various approaches have been proposed with the aim to provide expressive access control models and, in this context, Semantic Web technologies have also been leveraged. This chapter investigates the application of Semantic Web technologies in access control, highlighting the main trends in the area and outlining the most characteristic approaches.
Keywords
access control; Semantic Web; ontologies; privacy; security
Information in this chapter
• Implementing RBAC with ontologies
• Semantically extending the XACML Attribute Model
• Ontology-based context awareness
• Ontological specification of user preferences
Introduction
Any security violation and breach certainly includes illicit access to some resources, being systems, data, or operations. In this context, the evolution of security policies has brought access control at the core of security, but also privacy protection. Therefore, beyond legacy access control models, such as the Discretionary Access Control (DAC), the Mandatory Access Control (MAC) [1], and the well-adopted Role-Based Access Control (RBAC) [2], a variety of systems have been proposed, introducing a manifold of additional features. Most of the prominent approaches typically propose enhancements to RBAC models in order to incorporate different criteria in access control decisions, rather than just which user holding which role is performing which action on which object. In that respect, access control models have adopted concepts such as organization [3], context [4], attributes [5], and Separation and Binding of Duty (SoD/BoD) [6], among others, whereas Privacy-Aware Access Control [7] has emerged as a research field fostering personal data protection leveraging access control. The advent of the Semantic Web and the technologies it brings, such as semantic ontologies and reasoning mechanisms, have provided access control with new potentials. Therefore, several approaches have leveraged Semantic Web technologies in various ways, seeking expressiveness, formal semantics, and reasoning capabilities; as a starting point, the Web Ontology Language (OWL) [8] was used to develop policy languages for the Web, such as Rei and KAoS [9], as well as to provide interoperability while accessing heterogeneous databases, as in [10–12].
This chapter provides an overview of the most characteristic access control approaches that make use of Semantic Web technologies. The motivation, application domain, and usage patterns followed by the studied approaches vary significantly. Therefore, the following sections adopt a categorization that is by no means unique, but that highlights important differentiations among the approaches. Since currently RBAC constitutes the baseline for access control, “Implementing RBAC with Ontologies” investigates approaches targeting its ontological implementation, whereas the next three sections outline systems with more specific focus. In particular, “Semantically Extending the XACML Attribute Model” overviews approaches providing semantic extensions to the XACML attribute model, “Ontology-Based Context Awareness” investigates the use of Semantic Web technologies fostering context-awareness in access control, and “Ontological Specification of User Preferences” describes mechanisms for ontologically specifying access and usage control user preferences. The advent of online social networks fed access control with new challenges, so “Semantic Access Control in Online Social Networks” deals with the corresponding semantic approaches. In “DEMONS Ontological Access Control Model,” the DEMONS model, developed by the authors, is outlined; it is a fully ontological approach, combining various features and providing several advantages. Finally, “Discussion” concludes the chapter with a comparative discussion on the basis of important trends and features of the studied access control approaches.
Implementing RBAC with ontologies
Recently, there have been several efforts to express RBAC [2] policies using OWL. In this context, ontologies are used to represent the main concepts of RBAC—Action, Subject, Object, Role, Permission—as well as role hierarchies and dynamic and static SoD constraints. An important work in this field is presented in [13], where Finin et al. have introduced ROWLBAC, proposing two different approaches regarding role representation: the first maps roles to classes and subclasses to which individual subjects can belong, whereas the second represents roles as instances of the generic Role class. In both cases, actions, subject,s and objects are represented by the corresponding classes, while the disjoint PermittedAction and ProhibitedAction subclasses of Action are introduced in order to control access. In the first case, roles (and active roles) are represented as classes of users, and the role hierarchy relation is mapped to the subsumption relation in OWL. In addition, this approach maps static and dynamic SoD constraints to class disjointness constraints in OWL. The second approach, modeling roles as instances, uses the properties role and activeRole in order to bind users to their possible and active roles, respectively. In this case, role hierarchy is obtained by means of the subRole property and constraints are modeled through the specialized ssod and dsod properties. However, in the second approach, DL reasoning cannot be exploited for enforcing RBAC. Instead, rules need to be added in the ontology, thus degrading performance. Similar to ROWLBAC, Ferrini et al. present an approach referred to as XACML+OWL [14]. In this model, OWL is used in conjunction with XACML [15], with a view to decoupling the management of constraints and RBAC hierarchies from the specification and the enforcement of the actual XACML policies. Additionally, it addresses some shortcomings of ROWLBAC, like the inconsistency when two classes are at the same time included (according to the role hierarchy) and subject to SoD constraints. Subjects are represented as OWL individuals, information about which can be retrieved through semantic functions defined in the framework. Regarding dynamic SoD constraints, this approach goes further by adding Resource and Permission classes which, along with the Action class, can be used to specify more complex constraints involving not only subjects, but also actions and resources. XACML+OWL exploits the obligation mechanism of XACML for managing the dynamic SoD constraints, so that for each permission granted, a list of axioms is added to the ontology, thus reducing constraint evaluation to the problem of checking the consistency of an ontology.
Another approach in the same philosophy is presented in [16], where He et al. define a high level OWL DL ontology and rules expressed by means of the Semantic Web Rule Language (SWRL) [17], not only representing and extending the NIST Standard RBAC model, but also combining the latter with the Attribute Based Access Control (ABAC) paradigm [5], in order to implement access control for Web services. This approach obtains dynamic role assignments based on users’ credentials and their attributes, as well as dynamic association of access privileges with roles through attributes associated with services. Likewise, RBAC is adopted by [18] in a similar way and extended with contextual attributes, resulting in an access control system for context-aware collaborative environments, designed and built using Semantic Web technologies. The defined RBAC ontology is in turn attached to a domain-specific ontology that captures the features of the application in order to take into account attributes during the definition of policies and the access control decision. The limited expressive power of Description Logic has been mitigated by introducing SPARQL queries [19] that can check additional constraints against an available knowledge base.
Semantically extending the XACML attribute model
Apart from XACML+OWL [14], presented in the previous section, several approaches have leveraged XACML together with ontologies, most of them targeting the expression limitations of the attribute-based paradigm. In this direction, the approach presented in [20] proposes an ontology-based inference engine, which extends XACML attribute management for simplifying the specification and maintenance of ABAC policies. The standard XACML architecture is enhanced with two extensions, namely the Inference Engine and the Ontology Administration Point (OAP). User, resource, and environment attributes are ontologically represented and delivered by the OAP, and the Inference Engine in turn performs mappings between different attributes and attribute conditions. Inference is obtained with the help of SWRL rules, and derived attributes can then be queried by the context handler with SPARQL requests.
The approach presented in [21] addresses the expressiveness limitations of XACML regarding knowledge representation; it extends it in order to support ontology-based reasoning and rule-based inference, while maintaining the usability of its original features. In that respect, an intelligent XACML shell, based on a multi-layer semantic framework, is used to enhance the semantic and knowledge representation of XACML by leveraging Semantic Web technologies. It is noted that, as opposed to XACML, where the data type of an attribute is a primitive data type, this approach enables the data type to be mapped to an ontology class, thus inheriting semantic knowledge from a specific domain.
Likewise, in [22], an XML filter is created for regulating the disclosure of information, according to both the XML document structure and the semantics of its contents; this is achieved by directly integrating a knowledge base, which contains a description of the domain, in an XACML engine. In essence, the OWL files contain a description of the concepts and their relations, and of the mapping to the corresponding document elements. A Policy Semantic Point (PSP) acts as a bridge between the access control and the ontology model by executing SPARQL queries on the inferred knowledge base.
Ontology-based context awareness
An important aspect of access control is reflected by the concept of context, which generally refers to information describing a specific situation; context includes static and dynamic environmental characteristics such as temporal, spatial, and historical. Contextual parameters concerning the subject, object, or action of an access control request, usually affect the activation of a role or the enforcement of a rule. Specifying which parts of this context information are relevant for a specific authorization decision, and how the corresponding information may be elicited and defined in the associated models, constitute key aspects of access control. The significance of context in this domain is evident, as there have been proposed numerous extensions to well-established models in order to include it, such as the Extended RBAC Profile of XACML, presented in [23].
A prominent approach in this area constitutes the Temporal Semantic Based Access Control (TSBAC) model [24], which enhances the specification of user-defined authorization rules by constraining time interval and temporal expressions over users’ history of accesses, which are stored in a History Base. Indeed, the concept of history of accesses constitutes a parameter of significant importance, for example, for cases when the disclosure of some data must exclude the future access on the same or other data. This model uses logical time, rather than real time, in its authorization rules, while also providing a formal semantics specification for temporal authorizations. As TSBAC is an extension of the Semantic Based Access Control (SBAC) model [25,26], it is also based on the use of OWL ontologies for modeling access control entities along with their semantic interrelations, thus defining a Subjects-Ontology, an Objects-Ontology, and an Actions-Ontology. The most important contribution of SBAC has been the efficient propagation of policies—based on subsumption—through different semantic interrelations in the three levels of an ontology; concept-level, property-level and individual-level, where the semantic authorization flow can occur in each level or between different levels. The model proposed in [27] and referred to as GTHBAC is an extension of TSBAC, making use of real-time schemes as well; history-based constraints are integrated along with a generic access control model, thus increasing the expressiveness of the authorization rules while allowing temporal history-based decision and making it applicable to a wide variety of access control models.
Among the approaches comprising the family of context-aware semantic models, OrBAC [3,4,28] is rather the most mature, as it is the first approach to express all different types of context within a unique homogeneous framework. In particular, OrBAC defines a Context Ontology comprised not only of temporal, spatial, and historical context but also of user-declared and application dependent context; the latter depends on the characteristics that join the subject, the action, and the object and can be evaluated by querying the system database, whereas user-declared context allows for modeling contexts that are difficult to be described using environmental conditions. It is noted also that provisions targeting privacy protection can be implemented leveraging context, as proposed in [29], where the concept of purpose is modeled as a user-declared context. Starting from these elementary contexts, OrBAC allows for also defining conjunctive, disjunctive, and negative contexts. On the other hand, another specificity of the OrBAC ontology is that traditional triples <subject, action, object> are abstracted at the organizational level into triples <role, activity, view>; in particular, subjects are empowered in roles, objects are used in views, and actions implement activities, while forming hierarchies. In [30], ontologies to describe alerts and policies are defined, using inference rules to perform the mapping between concrete alerts and OrBAC contexts, which represent the necessary reaction that must be enforced when an alert is detected by the monitoring system.
Ontological specification of user preferences
Several access control approaches also incorporate in the decision-making process rules defined by the users, expressing in this way their own access and usage preferences. This trend is particularly met in privacy-aware access control [7], where XML-based languages, such as P3P [31] and APPEL [32], are used for formally representing preferences.
In order to increase the expressive power of such languages and enforce the semantics of a person’s data protection intentions, researchers have leveraged ontologies. In this context, a model for privacy preferences representation and management, in which preference rules are represented in OWL, is described in [33]. This model includes formal descriptions of how requests and preference rules are defined, properties of a consistent rule-set that must be satisfied, how requests and preferences are matched, and how the consistency of the rule-set is ensured.
In [34], Sacco et al. present the Privacy Preference Ontology (PPO) along with the Privacy Preference Manager (PPM), allowing for fine-grained access control for the Web of Data. PPO provides a lightweight vocabulary for defining fine-grained privacy preferences for structured data, in combination with the Web Access Control (WAC) ontology,1 while PPM allows users to create privacy preferences based on PPO and restricts access to their data to third-party users. PrivacyPreference constitutes the main class of PPO and various types of properties allow for defining: access restrictions to statements, resources, and named graphs; conditions to specify which particular statements, resources, and named graphs are being restricted; which access privilege should be granted; and attribute patterns that must be satisfied by requesters. Specifically for the specification of attribute patterns, SPARQL ASK queries are leveraged.
In the same context, Hu et al. [35] propose that the semantic formal model for P3P can be enforced and expressed as a variety of ontologies and rules combinations, either by means of homogeneous integration, where all of the major terms are defined in ontologies and rules are used to overcome the expression limitations of ontologies, or through hybrid integration, where some of the terms in privacy protection policies are not explicitly declared or defined in ontologies but they are declared as predicates in each rule. Three types of ontologies are proposed, namely data user ontology categorizing the type of users, data type ontology describing personal profiles and digital traces, and purpose ontology to describe the intention of a data user to use a particular type of data.
Another approach leveraging P3P is [36], which relies on an ontology-based representation of the standard P3P base data schema, showing the internal structure of complex credentials in terms of fine-grained items. The P3P ontology is applied in order to automatically extend available XACML policies to include semantically equivalent additional conditions on users and resource description metadata. Augmented access control policies can be used as a replacement of the original ones, automatically incorporating ontology knowledge.
Semantic access control in online social networks
Online Social Networks (OSNs) have become a major type of online applications allowing information sharing among a large number of users, raising at the same time, however, new security and privacy concerns. The complex relations considered in such applications highlight the need for semantic organization of the contained knowledge and for semantic access control mechanisms.
In this context, Giunchiglia et al. [37] propose a Relation Based Access Control model (RelBAC), providing a formal model of permissions based on relationships among communities and resources. RelBAC can be used to model access control in terms of lightweight ontologies of users, objects, and permissions, allowing for automatically managing permissions. Similarly, the approach presented in [38] exploits relationships with the individuals and the community in order to determine the access restrictions to community resources. All this knowledge is represented in an ontology using OWL DL, while semantic rules are added on top of the ontology providing the sufficient expressivity and decidability to infer the indirect relationships.
Carminati et al. provide in [39] a much richer OWL ontology for modeling various aspects of online social networks, while also proposing authorization, administration, and filtering policies that depend on trust relationships among various users and are modeled using OWL and SWRL. In particular, the authors suggest modeling the following five important aspects of OSNs using Semantic Web ontologies: personal information, relationships among users, resources, relationships between users and resources, and actions.
A more detailed approach is presented in [40], which proposes the Ontology-based Social Network Access Control (OSNAC) model, encompassing two ontologies; the Social Networking systems Ontology (SNO), capturing the information semantics of a social network, and the Access Control Ontology (ACO), which allows for expressing the SWRL access control rules on the relations among concepts in the SNO. Finally, it captures delegation of authority and empowers both users and the system to express fine-grained access control policies.
DEMONS ontological access control model
In the context of the EU FP7 DEMONS project,2 a novel ontological access control model has been proposed aiming at introducing privacy awareness into distributed processes [41,42]. It is the latest of a series of ontology-based access control models that our group has developed during the last years [43–47]. The DEMONS approach has been conceived with expressiveness in mind and combines several features, including context, attributes, privacy-awareness, SoD and BoD, and a variety of dependencies, while having been successfully applied in the automatic privacy-aware verification and transformation of distributed workflows. It consists of two OWL ontologies, namely the Information Model Ontology (IMO) and the Policy Model Ontology (PMO), with the former containing the domain knowledge and the latter providing all the necessary classes and properties for the ontological specification of access control rules. Knowledge extraction is performed by means of a targeted reasoning software library implemented in DEMONS.
The DEMONS model is grounded on the concept of actions, referring to the situation where an actor performs an operation on a resource within an organization, that is, an action is a structure <ai, opi, resi, orgi>. Access control rules are used for defining permissions, prohibitions, and obligations over actions and can be specified at three abstraction levels: abstract, concrete, or semi-abstract. An access control rule is a structure:
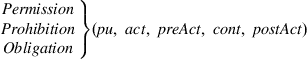
where act is the action that the rule applies to, pu is the purpose for which act is permitted/prohibited/obliged to be executed, cont is a structure of contextual parameters, preAct is a structure of actions that should have preceded, and postAct refers to the action(s) that must be executed following the rule enforcement. The basis for the access control rules specification is provided by the IMO, where the considered concepts comprise classes characterized by intra- and inter-class relations that are implemented as OWL object properties. The main intra-class properties are isA, isPartOf and moreDetailedThan that essentially comprise AND- and OR- hierarchies (e.g., purposes OR hierarchy; data types, roles, and operations AND and OR hierarchies, etc.), enabling inheritance, as well as dependencies specification. Inter-class relations describe associations between concepts of different classes, indicating, for instance, the roles that may act for a purpose, or the attributes characterizing a concept.
The main components of access control rules are actions. As shown in Figure 30.1 depicting the PMO, actions are ontologically implemented as Actions class instances, with <ai, opi, resi, orgi> being reproduced by means of the corresponding object properties. Within actions, actor, operation, resource, and organization are defined at either the abstract or the concrete level; in that respect, for the representation of an action’s elements at the abstract level, instances of the EnhancedEntities class are leveraged, constraining the referenced IMO semantic type with respect to its attributes and/or sub-concepts, while for the concrete level, the aforementioned properties point at instances of the class ConcreteEntities.
Two useful tools for defining constraints upon actions’ elements, and also achieving rich expressiveness in general, are expressions and logical relations. The latter, implied by thick lines in Figure 30.1, allow specifying logical structures of concepts. Expressions enable the definition of contextual conditions and constraints on concepts (e.g., on an actor’s attributes); they comprise ternary relations assigning a value to a subject through an operator, or logical structures of such triples.
Actions instances are used for specifying the main action and pre- and post-actions of a rule; in the latter cases this association is indirect, with the RequiredActions class mediating and enabling the specification of time and sequence constraints. Beyond such constraints, the DEMONS approach incorporates a mechanism for combining actions, so as to form complex structures thereof, referred to as skeletons, following various sequence patterns. Finally, dependencies among all the entities comprising the actions of a rule enable the specification of advanced SoD and BoD constraints, instead of relying only on role-/user- centric constraints.
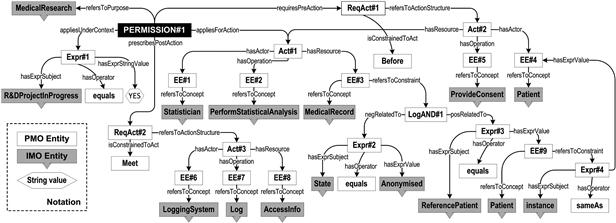
Figure 30.2 illustrates the ontological representation of an example rule, inspired from guidelines for the health sector [48]: “For the purpose of medical research and in the context of an ongoing R&D project, a statistician is allowed to perform statistical analysis on identifiable medical records of a patient, if the said patient has provided consent therefore; for accountability reasons, access should be immediately logged.”
In that respect, three actions are considered, corresponding to the statistical analysis (Act#1), the pre-action of consent provision (Act#2), and the post-action of logging (Act#3). The use of the SequenceConstraints instance Meet imposes a strict temporal constraint, prescribing that the end of the main action should coincide with the beginning of the post-action (Act#3), whereas Before implies a loose sequence constraint, meaning that the pre-action Act#2 should be executed sometime before the main action. Additionally, these actions involve various enhanced entities, most of which are unconstrained, such as EE#1 corresponding to the Statistician actor, or EE#2 reflecting the statistical analysis operation. On the other hand, EE#3 referring to the MedicalRecord resource has two constraints, described by expressions Expr#2 and Expr#3, and associated through an AND logical relation (LogAND#1). Specifically, Expr#2 implies identifiable data, through negation over Anonymised state, while Expr#3 is an example of concepts’ binding. MedicalRecord, being the resource of statistical analysis (Act#1), is assumed to contain the ReferencePatient field, indicating the patient it refers to. Since Patient is a Roles instance, it has to be explicit that it is not any patient who has provided consent, but the one being the data subject of the MedicalRecord. In that respect, EE#9 is constrained by Expr#4, specifying that the reference patient instance should be sameAs the patient implied by EE#4.
Actions themselves may comprise resources of other actions. This is the case with Act#1, comprising the resource of Act#2, in the sense that the patient must have provided consent for Act#1 execution. Finally, the permission of Figure 30.2 applies for the purpose of MedicalResearch, given that an R&D project is in progress (R&DProjectInProgress).
Discussion
In the previous sections, some of the most representative state-of-the-art ontological access control models have been presented. Seeking the description of inheritance of authorizations and properties, as well as advanced reasoning capabilities, a common characteristic of these models is that they leverage ontologies in order to construct hierarchies of the considered concepts. Support of hierarchies may vary from simple role hierarchy (e.g., as in [13]) to hierarchies of all the concepts associated with the access authorization, such as purposes or operations (e.g., as in [41]).
Moreover, apart from the main features that they support, these models can be further evaluated against a set of key access control aspects; Table 30.1 provides an overview of the features that each of the afore-presented models supports, either directly or partially. The basic criterion for categorizing an access-control model as privacy-aware is whether it takes into consideration the purpose for which access to resources is requested during the access decision process; for instance, [33] and [41] explicitly base their authorizations upon the concept of purpose. Other approaches, such as [40], allow for the specification of usage policies by the owners of the requested resources, whereas other models, for example, [22], are characterized as privacy-aware for aiming at the minimization of data disclosure, this way addressing the necessity, adequacy, and proportionality privacy principles.
Table 30.1
Comparative Overview of the Semantic Access Control Models
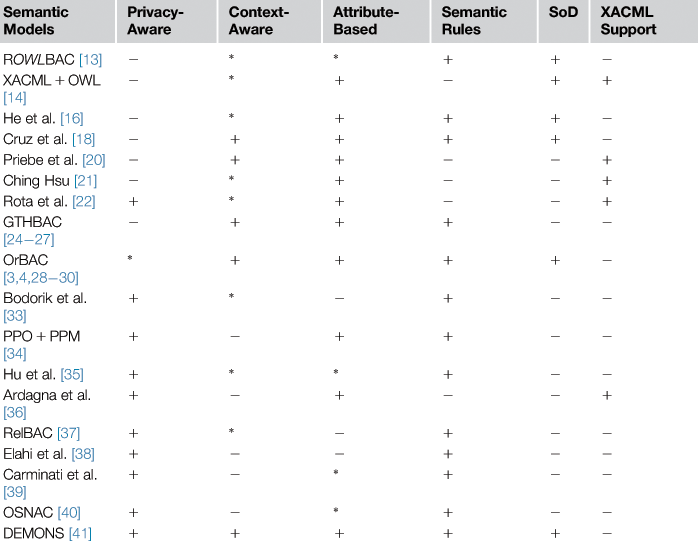
The symbols “+”, “*” and “−” indicate, respectively, direct, partial/indirect, and no support for the corresponding feature.
Most of the models studied use Semantic Web technologies for the specification of access control rules. In that respect, the majority of the presented models leverage SWRL for expressing the rules over the application domain ontologies, while some approaches, like [18] and [41], completely integrate access control with ontologies by introducing dedicated access control ontologies, and evaluate the access requests by means of reasoning over these ontologies. Lack of semantic rules support means that the model under consideration instead makes use of XML-based standards, such as the XACML policy language, for specifying the corresponding authorizations, leveraging though Semantic Web technologies for their semantic extension. In fact, supporting XACML is by itself an important feature, since this way, an access control model can be employed by systems already using the XACML standard, regardless of the technology used for the specification of access control rules.
Furthermore, a few models provide the means for specifying SoD constraints. Most of them support both static and dynamic SoD, constraining the actors of the access actions, while [30] and [41] allow for the specification of SoD and BoD constraints not only on the actor but also on every entity associated with the access action.
Finally, as context and attributes are not always treated as independent sets, we consider as attributes those parameters further characterizing the entities of an access action, while contextual information refers to all the external parameters. The purpose of using both these concepts in access control is similar, serving the need to further refine access control rules with parameters that are either dynamic and external or describe variants of similar concepts. Context and attributes provide for describing expressive policies, but also require high expressiveness from the underlying models; in that respect, various approaches have leveraged Semantic Web technologies toward describing constraints on context and attributes, as also implied by the popularity of these aspects highlighted in Table 30.1.
Acknowledgments
The research of M. N. Koukovini is co-financed by the European Union (European Social Fund–ESF) and Greek national funds through the Operational Program "Education and Lifelong Learning" of the National Strategic Reference Framework (NSRF) —Research Funding Program: Heracleitus II. Investing in knowledge society through the European Social Fund. We also acknowledge partial support from the EU FP7 DEMONS and ARUM projects.
References
1. Samarati P, di Vimercati SDC. Access control: Policies, models, and mechanisms. In: FOSAD 2000: Foundations of Security Analysis and Design, vol. 2171 of Lecture Notes in Computer Science; Springer; 2001. p. 137–196.
2. Ferraiolo DF, Sandhu R, Gavrila S, Kuhn DR, Chandramouli R. Proposed NIST standard for role-based access control. ACM Trans Inf Syst Secur. 2001;4:224–274.
3. Abou-El-Kalam RE, Baida P, Balbiani S, Benferhat, F, Cuppens Y, Deswarte A, et al. Organization based access control. In Policy'03: 4th IEEE International Workshop on Policies for Distributed Systems and Networks; 2003 Lake Como, Italy. p. 120–131.
4. Cuppens F, Cuppens-Boulahia N. Modeling contextual security policies. Int J Inf Secur. 2008;7(4):285–305.
5. Yuan E., Tong J. Attributed based access control (ABAC) for Web services. In ICWS '05: Proceedings of the IEEE International Conference on Web Services; 2005.
6. Botha RA, Elo JHP. Separation of duties for access control enforcement in workflow environments. IBM Syst J. 2001;40(3):666–682.
7. Antonakopoulou A, Lioudakis GV, Gogoulos F, Kaklamani DI, Venieris IS. Leveraging access control for privacy protection: A survey. In: Privacy Protection Measures and Technologies in Business Organizations: Aspects and Standards. Yee G, editor. IGI Global; 2012. p. 65–94.
8. The World Wide Web Consortium (W3C). OWL web ontology language overview. W3C Recommendation. [Internet]. Retrieved from: <http://www.w3.org/TR/owl-features>; 2004.
9. Tonti G, Bradshaw J, Jeffers R, Montanari R, Suri N, Uszok A. Semantic web languages for policy representation and reasoning: A comparison of KAoS, Rei, and Ponder. In: The SemanticWeb-ISWC 2003. Lecture Notes in Computer Science. Springer. 2003;2870: 419–437.
10. Mitra P, Pan C-C, Liu P, Atluri V. Privacy-preserving semantic interoperation and access control of heterogeneous databases. In: ASIACCS '06: Proceedings of the 2006 ACM Symposium on Information, Computer and Communications Security; ACM; 2006. p. 66–77.
11. Pan C-C, Mitra P, Liu P. Semantic access control for information interoperation. In: SACMAT '06: Proceedings of the 11th ACM Symposium on Access Control Models and Technologies. New York, NY; ACM, 2006. p. 237–246.
12. Sun Y, Pan P, Leung H-F, Shi B. Ontology based hybrid access control for automatic interoperation. In: Lecture Notes in Computer Science, Springer 2007;323–332. Xiao B, Yang L, Ma J, Muller-Schloer C, Hua Y, eds. Autonomic and Trusted Computing. 4610.
13. Finin TW, Joshi A, Kagal L, Niu J, Sandhu RS, Winsborough WH, et al. ROWLBAC: representing role based access control in OWL. In SACMAT '08: Proceedings of the 13th ACM Symposium on Access Control Models and Technologies; ACM; 2008. p. 73–82.
14. Ferrini R, Bertino E. Supporting RBAC with XACML+OWL. In SACMAT '09: Proceedings of the 14th ACM Symposium on Access Control Models and Technologies; ACM; 2009. p. 145–154.
15. Organization for the Advancement of Structured Information Standards (OASIS). eXtensible Access Control Markup Language (XACML) Version 2.0. OASIS Standard. [Internet]. Retrieved from: <http://docs.oasis-open.org/xacml/2.0/access_control-xacml-2.0-core-spec-os.pdf>; 2005.
16. He Z, Huang K, Wu L, Li H, Lai H. Using semantic web techniques to implement access control for web service. Information Computing and Applications In: Springer 2011;258–266. Zhu R, Zhang Y, Liu B, Liu C, eds. Communications in Computer and Information Science. 105.
17. Parsia B, Sirin E, Grau BC, Ruckhaus E, Hewlett D. Cautiously approaching SWRL Tech Rep. University of Maryland 2005.
18. Cruz F, Gjomemo R, Lin B, Orsini M. A constraint and attribute based security framework for dynamic role assignment in collaborative environments. In: Springer 2008;322–339. CollaborateCom 2008: Collaborative Computing: Networking, Applications and Worksharing, Bertino E, Joshi JBD, eds. Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering. 10.
19. The World Wide Web Consortium (W3C). SPARQL query language for RDF. W3C Recommendation. [Internet]. <http://www.w3.org/TR/rdf-sparql-query>; 2008.
20. Priebe T, Dobmeier W, Kamprath N. Supporting attribute-based access control with ontologies,. In ARES 2006: Proceedings of the First International Conference on Availability, Reliability and Security. IEEE Computer Society; 2006. p. 465–472.
21. Hsu C. Extensible access control markup language integrated with Semantic Web technologies. Inf Sci. 2013;238(0):33–51.
22. Rota SS, Rahaman MA. XML secure views using semantic access control. In EDBT '10: Proceedings of the 2010 EDBT/ICDT Workshops. New York, NY; ACM; 2010. p. 5:1–5:10.
23. Abi Haidar D, Cuppens-Boulahia N, Cuppens F, Debar H. An extended RBAC profile of XACML. In SWS '06: Proceedings of the 3rd ACM workshop on Secure web services. New York, NY; ACM; 2006. p. 13–22.
24. Ravari AN, Amini M, Jalili R, Jafarian J. A history based semantic aware access control model using logical time. In ICCIT 2008: Proceedings of the 11th International Conference on Computer and Information Technology; 2008. p. 43–50.
25. Javanmardi S, Amini M, Jalili R. An access control model for protecting Semantic Web resources. Web policy workshop 2006;32–46.
26. Javanmardi S, Amini A, Jalili R, Ganjisafar Y. SBAC: A semantic-based access control model. In: NORDSEC-2006; 2006.
27. Ravari AN, Jafarian J, Amini M, Jalili R. GTHBAC: A generalized temporal history based access control model. Telecommun Syst. 2010;45:111–125.
28. Preda S, Cuppens F, Cuppens-Boulahia N, Garcia-Alfaro J, Toutain L. Dynamic deployment of context-aware access control policies for constrained security devices. J Syst Softw. 2011;84:1144–1159.
29. Ajam N, Cuppens-Boulahia N, Cuppens F. Contextual privacy management in extended role based access control model. In: Lecture Notes in Computer Science. Springer 2010;121–135. Garcia-Alfaro J, Navarro-Arribas G, Cuppens-Boulahia N, Roudier Y, eds. Data Privacy Management and Autonomous Spontaneous Security. 5939.
30. Cuppens-Boulahia N, Cuppens F, Autrel F, Debar H. An ontology-based approach to react to network attacks. Int J Inf Comput Secur. 2009;3(3):280–305.
31. The World Wide Web Consortium (W3C). The platform for privacy preferences 1.1 (P3P1.1) Specification. [Internet]. Retrieved from: <http://www.w3.org/TR/P3P11>; 2006.
32. The World Wide Web Consortium (W3C). A P3P preference exchange language 1.0 (AP- PEL1.0). [Internet]. Retrieved from: <http://www.w3.org/TR/P3P-preferences>; 2002.
33. Bodorik P, Jutla D, Wang MX. Consistent privacy preferences (CPP): model, semantics, and properties. In SAC 2008: Proceedings of the 2008 ACM Symposium on Applied Computing; ACM; 2008. p. 2368–2375.
34. Sacco O, Passant A, Decker S. An access control framework for the web of data. In: Proceedings of 2011 IEEE 10th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom); 2011. p. 456–463.
35. Hu Y-J, Guo H-Y, Guang-DeLin. Semantic enforcement of privacy protection policies via the combination of ontologies and rules. In: Proceedings of IEEE International Conference on Sensor Networks, Ubiquitous and Trustworthy Computing (SUTC '08); 2008. p. 400–407.
36. Ardagna C, Damiani E, De Capitani di Vimercati S, Fugazza C, Samarati P. Offline expansion of XACML policies based on P3P metadata. In: Lecture Notes in Computer Science; Springer 2005;363–374. Lowe D, Gaedke M, eds. Web Engineering. 3579.
37. Giunchiglia F, Zhang R, Crispo B. Ontology driven community access control. In: SPOT2009-Trust and Privacy on the Social and Semantic Web; 2009.
38. Elahi N, Chowdhury M, Noll J. Semantic access control in web based communities. In ICCGI 2008: Proceedings of the Third International Multi-Conference on Computing in the Global Information Technology; IEEE Computer Society; 2008. p. 131–136.
39. Carminati B, Ferrari E, Heatherly R, Kantarcioglu M, Thuraisingham B. A semantic web based framework for social network access control. In SACMAT '09: Proceedings of the 14th ACM Symposium on Access Control Models and Technologies; ACM; 2009. p. 177–186.
40. Masoumzadeh A, Joshi J. OSNAC: An ontology-based access control model for social networking systems. In SOCIALCOM '10: Proceedings of the 2010 IEEE Second International Conference on Social Computing. IEEE Computer Society; Washington, DC, USA; 2010. p. 751–759.
41. Papagiannakopoulou EI, Koukovini MN, Lioudakis GV, Garcia-Alfaro J, Kaklamani DI, Venieris IS, et al. A privacy-aware access control model for distributed network monitoring. Computers & Electrical Engineering; 2012.
42. Koukovini MN, Papagiannakopoulou EI, Lioudakis GV, Kaklamani DI, Venieris IS. A workflow checking approach for inherent privacy awareness in network monitoring In DPM 2011: Proceedings of the 6th International Workshop on Data Privacy Management. vol 7122 In: Garcia- Alfaro J, Cuppens-Boulahia N, Navarro-Arribas G, eds. of Lecture Notes in Computer Science. Springer 2011.
43. Lioudakis GV, Koutsoloukas EA, Dellas NL, et al. A middleware architecture for privacy protection. Comput Netw. 2007;51(16):4679–4696.
44. Lioudakis GV, Koutsoloukas EA, Dellas N, Kapitsaki GM, Kaklamani DI, Venieris IS. A semantic framework for privacy-aware access control. In: Proceedings of the 2008 International Multiconference on Computer Science and Information Technology. 3rd International Workshop on Secure Information Systems (SIS 2008); 2008 Oct 20–22; Wisła, Poland; 2008. p. 813–820.
45. Lioudakis GV, Gogoulos FI, Antonakopoulou A, Kaklamani DI, Venieris IS. Privacy protection in passive network monitoring: An access control approach. In WAINA 2009: Proceedings of the IEEE 23rd International Conference on Advanced Information Networking and Applications (AINA) Workshops/Symposia; 2009 May 26–29; Bradford, UK. 2009. p. 109–116.
46. Gogoulos F, Antonakopoulou A, Lioudakis GV, Mousas AS, Kaklamani DI, Venieris IS. Privacy-aware access control and authorization in passive network monitoring infrastructures. In CIT 2010: Proceedings of the 10th IEEE International Conference on Computer and Information Technology; 2010.
47. Antonakopoulou A, Gogoulos FI, Lioudakis GV, Mousas A, Kaklamani DI, Venieris IS. An ontology for privacy-aware access control in network monitoring environments. Journal of Research and Practice in Information Technology; 2013.
48. Data Protection Commissioner of Ireland. Data protection guidelines on research in the health sector. 2007.
1WAC-http://www.w3.org/ns/auth/acl.
2DEcentralized, cooperative, and privacy-preserving MONitoring for trustworthinesS (DEMONS), homepage: http://fp7-demons.eu/.