MODULE 7
Understanding Cryptography
Cryptography is a very critical part of securing information and systems. Cryptography is often used in conjunction with other access controls to ensure that only those people with a legitimate need to know and authorized clearance are able to access data and systems. This is accomplished through various means and methods, which we will discuss over the next few modules.
Cryptography Concepts
You may have been exposed to cryptography in other studies for your Network+ examination, or perhaps you use it in your daily job. However, many typical IT specialists don’t fully understand cryptography at a level required for security personnel. Security professionals must understand cryptographic concepts, methods, and terminology, as well as applied uses of cryptography. Cryptography is a foundational element to our profession, because so many security issues are related to and solved by cryptographic techniques and controls. In this module, we’ll discuss the basics of cryptography, define certain terms, and cover different cryptography-related concepts.
What Is Cryptography?
Cryptography is the science of hiding information, in the most basic sense. Cryptography is used to keep information confidential, so only people who are authorized to view it and interact with it can do so. In this respect, it supports one of our three major security goals: confidentiality. It also supports the goal of integrity, and even availability to a certain degree. Cryptography protects information in various ways, sometimes by scrambling information so it is unreadable to human eyes, and sometimes making it unreadable even to computers. The key goals of cryptography are to ensure that the people who need access to the information and systems have it when they need it, and to protect the information and systems from people who do not need access to it. Obviously, to accomplish this, methods are needed to convert information back and forth from its unreadable state to a readable one. When information can be easily readable by humans or machines, it is said to be in plaintext. When information is converted to an unreadable state, it is said to be in ciphertext. The process of converting plaintext information into ciphertext information is called encryption. The reverse of this process, converting ciphertext back into plaintext, is called decryption. In this section, we will discuss the very basics of cryptography, including its uses and some basic terms and definitions.
![]()
Remember that plaintext is encrypted to produce ciphertext. Ciphertext is decrypted to obtain plaintext.
Uses of Cryptography
As we mentioned, cryptography is primarily used to ensure confidentiality. It ensures the secrecy of data and protects it from unauthorized access. It does this by changing data into an unreadable format (encryption) until it is converted back into plaintext for authorized users (decryption). Another use of cryptography is to maintain data integrity. Cryptographic methods can be applied to data to measure and establish the state of the data and to determine whether the data is in the same state that it was when it was first examined. Examples of the practical uses of cryptography, which we will discuss over the next several modules, include protecting data while it is in storage and during transmission, ensuring data integrity, creating digital signatures (giving us non-repudiation), and concealing data within other text or data (steganography).
Cryptography Definitions
Let’s examine some important terms encountered in cryptography. You already know that readable text or data is called plaintext, and that when that data has been rendered unreadable by humans or normal computer-based methods, it is called ciphertext. Encryption is the process that converts plaintext to ciphertext, and decryption is the process used to reconvert ciphertext back to into plaintext. You also need to be aware of some other terms for your study of cryptography, a few of which we’ll discuss here and several more in the upcoming sections.
Cryptanalysis is the study of “breaking” encryption, for all practical purposes. You perform cryptanalysis on ciphertext data to reverse it to a plaintext state when you do not have access to the methods used to encrypt the data in the first place. Both security professionals and malicious actors, such as hackers, perform cryptanalysis in an attempt to decrypt ciphertext. There are several different methods for performing cryptanalysis, but many of them depend upon your having an existing piece of known plaintext that can be compared to its corresponding ciphertext, and vice versa, when you have some knowledge of the methods used to encrypt and decrypt the text. We will discuss various simplistic (and complex) methods over the next few modules.
You should also be familiar with the terms code and cipher. These terms are often used interchangeably, although they don’t quite mean the same thing. A code is a representation of an entire phrase or sentence, whereas a cipher tends to represent text on a character-by-character basis. For example, a coded version of the phrase “We attack at dawn” might be “Mother bought some brown eggs at the store.” Codes are not typically transformative; that is, there is usually no formal process to convert the true meanings of messages into their coded equivalents or back. Codes usually require a codebook, which is essentially a predefined dictionary that translates codes to their plaintext messages and back. Because of this, the range of messages that can be sent and received via codes are limited, based upon the codebook used and the needs of the users.
Ciphers, on the other hand, operate on a character-by-character basis, so they usually do require a formal transformation process to work. Additionally, the range of potential messages that can be sent using ciphers is unlimited, because these processes are usually done on the fly and don’t require a predefined codebook. You may also hear the corresponding terms encode (and decode), as well as encipher (and decipher) thrown around in the cryptography context; although they don’t technically mean the same things, they are often used somewhat interchangeably. Since our focus will be primarily on ciphers, we’ll use the more generic terms encrypt and decrypt.
![]()
Codes are entire words are phrases, and ciphers are individual characters. The cryptography methods that we discuss in this book focus on ciphers.
Data-at-Rest, Data-in-Transit (Transport), and Data-in-Process
Data is said to reside in three possible states while it is being used. The first state is called data-at-rest, which means data that is put into storage. This data is not being currently accessed, transmitted, or received, nor is it being used by the computer. Data-at-rest is normally represented by data stored in static files on a hard drive or other storage media.
Data-in-transit is data that is being transported via some transmission means. This data is in the process of being transmitted or received from one person or host to another. Examples of data-in-transit include information being sent over a network, over an Internet connection, from computer-to-computer over an Ethernet connection, or even over wireless networks. The data is not in storage; it has been transformed and formatted to be transmitted and received.
Data-in-process refers to data that isn’t in storage and is not currently being sent from one party to another, but is being actively used by the computer at the time. This is data that currently resides in the computer’s RAM and is being accessed by the computer’s CPU, operating system, and applications. Operating systems and applications are using data-in-process on a constant basis, transforming it, using it as input to processes, and so on. An example would be a Microsoft Word document that is open and being edited.
Cryptography supports data in all three of these states in various ways. Cryptographic methods are used to protect data-at-rest by encrypting files in storage. Cryptography also supports data protection from unauthorized access while it is in the process of being transmitted and received (data-in-transit). Data in-process may be protected by different cryptographic methods so that it cannot be accessed by unauthorized means while the user or computer is using it. Most of the time, however, data-in-process must be in a decrypted state so that applications and the operating system can read it and use it, since not all systems are always able to work with data in an encrypted state.
Early Cryptography
Cryptography isn’t a recent invention; people throughout the last couple of thousands of years have used it to protect personal secrets, military troop movements, diplomatic messages, and so on. Historians have discovered several examples of the uses of crude, but effective, cryptographic methods, such as the Spartan scytale, which was a baton or stick with a strip of parchment wound around it several times, from one end of the stick to the other. On the parchment as it was wrapped on the baton, a person wrote a message, in plaintext. Once the parchment was removed from the stick, the words on the strip of parchment made no sense, since they were effectively scrambled. To “decrypt” the message, the receiver had to know the exact dimensions of the baton and have an identical one so that they could rewrap the parchment the exact same way around the baton and read the message.
Other historical uses of cryptography involved using different techniques to scramble letters of the alphabet so that only the sender and recipient would know how to unscramble and read them. Those methods are discussed a bit later in the next sections. Still other, more modern ways of using cryptography involved the use of specially built machines to encrypt and decrypt messages. The classic example is the Enigma machine used by the Germans during World War II. This machine used encryption techniques that were considered unbreakable, until Dr. Alan Turing, a British mathematician, was able to determine how the machine worked and the methods it used to encrypt its information. Turing, now considered the father of modern cryptography and, to a large degree, computers, was able to decrypt intercepted German messages. The ability of the British government to decrypt German military communications gave the Allies incredible insight to enemy troop movements, invasion plans, and so forth, effectively turning the tide of the war.
Substitution
One of the first early methods of employing cryptography, which is still frequently used today, is called substitution. A substitution cipher substitutes different letters of the alphabet for other letters. To make a substitution cipher work, you have to align letters of the alphabet with the other letters that will substitute for them. For example,
ABCDEFGHIJKLMNOPQRSTUVWXYZ
could align with
MNOPQRSTUVWXYZABCDEFGHIJKL
So the plaintext phrase, WE ATTACK AT DAWN, would be encrypted to read IQ MFFMOW MF PMIZ. This particular example is called a shift cipher because it essentially shifts the entire alphabet down 13 spaces, and then starts over with the first letter. Other variations of this type of substitution cipher are called a ROT-13 cipher, which was also used by Julius Caesar (and sometimes called a Caesar cipher). Still other methods of using substitution ciphers might use different words to begin the substitution alphabet, and then follow those words with the rest of alphabet in normal order. More complex versions of substitution ciphers involve rearranging the words of the sentence into consistent groups of letters that have the same amount of letters per group. This makes it more difficult to break the cipher, since you wouldn’t have the ability to guess words based upon how many letters made up each word, particularly on easy words such as “a,” “and,” and “the,” for example. Yet another, more complex way of using substitution ciphers involves using multiple alphabets. This is called polyalphabetic substitution, and is sometimes called a Vigenère cipher. Examples of substitution ciphers can be found in the standard word puzzle books you see on magazine racks in supermarkets and bookstores.
Transposition
As opposed to a substitution cipher, a transposition cipher transposes or changes the order of characters in a message using some predetermined method that both the sender and receiver are aware of. The sender transposes the message, sends it, and when the receiver gets the message, he simply applies the same transposition method in reverse, decrypting the message. Transposition ciphers have also been used for hundreds of years. There are a variety of different transposition methods, including columnar, rail fence, and route ciphers. More complex methods use both substitution and transposition together.
![]()
Although you will likely not be asked any questions related to the history of cryptography, it’s useful to know some of this information to understand its foundations. You will, however, be expected to know some of the types of early cryptographic methods, such as substitution and transposition.
Hashing
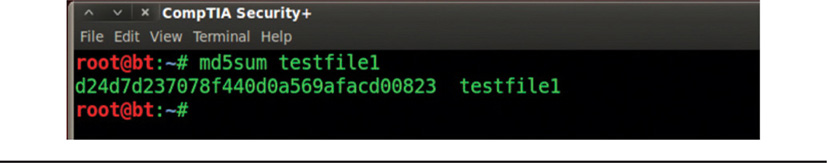
Hashing is also part of cryptography, but it’s not exactly the same as encryption and decryption. In the hashing process, variable-length text, such as a document or spreadsheet, or even a password, is exposed to a cryptographic algorithm that produces a cryptographic sum, or hash (also sometimes called a message digest), of the document. This hash is only a representation of the text; it is not the same thing as the text itself. Think of a hash as a very unique fingerprint that identifies a very specific piece of plaintext. The piece of plaintext can be any length, and it generally does not matter how large the input plaintext is. The resulting hash will always be a fixed-length piece of ciphertext, usually expressed in a hexadecimal format. An example of a typical hash is shown in Figure 7-1.
Figure 7-1 A hash value computed for a file
Unlike the encryption and decryption process, hashing is not normally reversible. In other words, you don’t simply encrypt text with a hashing function with the expectation of decrypting it later. Hashing is a one-way mathematical function whose sole purpose is to produce the cryptographic sum of the input plaintext. Think of the hashing processes as sort of a measuring process for the data, with the resultant hash being the actual measurement itself.
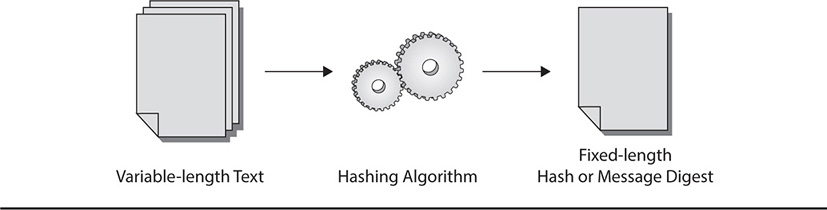
Although its purpose is not to decrypt text, the cryptographic sum produced by hashing has some uses. First, hashing is used to provide for integrity of data. A hash is unique to a particular piece of text. If even one letter or word of the text is altered in any way, then the resulting hash will be different. A change in even one binary digit, from a 1 to a 0 for example, would produce a different hash. In this way, the integrity of a piece of plaintext can be assured, since any changes would produce a different sum and be easily detected. The hashing process works as described in Figure 7-2.
Figure 7-2 The hashing process
![]()
Hashing is not the same thing as encryption, because hash values are not decrypted. It is, however, considered a cryptographic method with its own algorithms.
You can see how hashing would be useful in assuring the integrity goal. When data is transmitted over a network, it can be hashed before transmission and after reception, and the two resulting hashes can be compared. If they are the same, you know that the data has not been altered in any way. If they are different, you can assume that the data has changed in some way during transmission. We’ll discuss hashing in more depth in Module 8, when you’ll read about some of the various hashing methods.
![]()
The term “message” generically refers to any piece of variable-length text, be it a password, text document, spreadsheet, picture file, or any other type of data.
Cryptography Components
Cryptography has several basic components that are needed to make the process work. These include algorithms, keys, and cryptosystems, which we’ll discuss in the next few sections. It’s very important that you understand these different components and how they work for the exam and in your professional career. While we’ll cover only the very basics of these components in this module, the remaining modules on cryptography discuss in depth how these different components work together as well as their individual characteristics.
Algorithms and Keys
The two main components that make cryptography work are algorithms and keys. Algorithms and keys work together, hand-in-hand, to create cryptographic methods used to encrypt and decrypt messages as well as create message hashes. Algorithms are mathematical constructs that define how plaintext is altered to become ciphertext, as well as how that process is reversed during decryption. Algorithms can be very simple or very complex. For example, an algorithm used in a substitution cipher that we described earlier might require that a letter is shifted several spaces to the right. Other algorithms are extraordinarily complex and might be based upon mathematical concepts or formulas, or relationships between large prime numbers, for example.
The key is the variable (sometimes called the cryptovariable) used in the process, with the algorithm, to transform plaintext into ciphertext. In the substitution cipher example, if the algorithm (the rule) is that a letter is shifted several spaces to the right, then the key tells us how many spaces (such as three spaces, for instance) to shift. Even if the key changes periodically (on the chance that someone discovers it), the algorithm might remain the same for our substitution cipher. Although the algorithm is generally known and proven, keys are kept secret. Keys are typically not simplistic numbers, though, as described in our example. They are often complex, lengthy strings of numbers or characters. A key might also be practically seen every day as a password, passphrase, personal identification number (PIN), code word, and so on. Algorithms and keys are used to encrypt or decrypt text, as illustrated in Figure 7-3.
Figure 7-3 Algorithms and keys
Algorithms are generally well-known and tested, giving cryptographers and security professionals a level of confidence in their strength and ability to protect data. Most common algorithms in widespread use are tested and proven, while algorithms that do not go through the testing or examination processes may not necessarily invoke a lot of confidence. Algorithms that are publicly examined are in line with Kerckhoffs’s principle, which states that the algorithm should not be the secret part of the cryptographic process or method used; the key should be kept secret, not the algorithm.
One point worth mentioning here is that, although keys are generally kept secret, a concept called key escrow involves allowing a third party to maintain knowledge or copies of keys, in the event a key is lost or someone with knowledge of it is no longer available to provide it. Key escrow is often used by businesses and other organizations to store keys securely in the event they are lost, become corrupt, or an individual in the company with the only knowledge of the keys is terminated or quits. Several years ago, there was a movement in the U.S. government to attempt to require that cryptographic keys belonging to individuals be escrowed by law enforcement and other government agencies, in the event they were needed for an investigation into a criminal or terrorist act, for example. That attempt was not well received by the public or lawmakers, however, and was quashed.
![]()
Understand the definitions of algorithms and keys. An algorithm is a mathematical construct or rule that dictates how data will be encrypted and decrypted. Algorithms are generally well-known and not kept secret. Keys are the variables that algorithms use to ensure secrecy and randomness in the cryptographic process. Keys should be kept secret.
Cryptosystems
A cryptosystem is the total of the methods, techniques, algorithms, and keys used in a cryptographic process or system. A cryptosystem uses algorithms and keys as its basic components as well, but it often implements them in ways that may allow the system to be faster, more efficient, or stronger. Cryptosystems can be devices, methods, or processes, and may be strong or weak based upon the strength of the algorithms and methods used.
Block and Streaming Algorithms
Algorithms, as we discussed previously, are the mathematical rules used to transform plaintext into ciphertext and back again. Algorithms have a wide variety of characteristics that include mathematical foundation, strength, and how they operate on plaintext. Modules 8 and 9 go into detail about specific algorithms, but for now, let’s discuss an important distinction within algorithms: block and streaming. Remember that earlier we made the distinction between codes and ciphers and how they work with entire phrases (codes) or on individual characters (ciphers). The algorithms we discuss, both here and in the rest of the book, work on binary digits (bits) of plaintext, either individually or in specified groups. A block algorithm operates on a predefined size of a group of bits, known as a block. Different block algorithms use different block sizes, but typical sizes are 16-, 64-, and 128-bit blocks. Most of the algorithms we discuss in the book are block algorithms.
Streaming algorithms operate on individual bits, one bit at a time. Streaming algorithms don’t work on blocks of text; instead they look at each individual bit and perform a mathematical operation on that bit, and then move on to the next bit. Streaming algorithms tend to work much faster than block algorithms and are used in cryptographic methods that support fast communications requirements, such as wireless technologies.
![]()
Block algorithms work on predefined sizes of plaintext blocks, while streaming algorithms work on single bits of plaintext.
XOR Function
How both block and streaming algorithms perform operations on the bits of a message, to encrypt or decrypt, relates to a mathematical logic function called eXclusive OR (abbreviated as XOR). XOR looks at each bit (whether individually, as in a streaming algorithm, or in a block) and performs a binary operation on the bit. In an XOR function, each bit is compared with the keystream (the bits fed into the process by the key) and changed (or not) based upon the bit it is compared to. Essentially, any bits that compare and are the same (two binary 0’s for example) yield a resultant bit of false (and produce a 0-bit as the text output). Any bits that compare and are different (a binary 1 as the plaintext bit, and a binary 0 as the keystream bit, for example) produce a true value, and an output bit of 1 is generated. These generated bits are the ciphertext. Figure 7-4 illustrates this process.
Figure 7-4 The XOR function in action
In addition to the XOR function, different algorithms may use additional mathematical functions to operate on text, as well as complex methods to feed text and keys into the process in prescribed ways. Additionally, algorithms also use a concept called rounds. A round is an iteration of the encryption/decryption process; most algorithms use multiple rounds, repeating the process several times to ensure that the process is effective. For example, the Data Encryption Standard (DES) algorithm, discussed in Module 8, uses 16 rounds to encrypt a piece of plaintext. So it follows its mathematical process, including the XOR function, 16 times before outputting the final ciphertext.
![]()
Understand how the XOR function modifies bits when comparing them in a text and keystream. Matching bits always return 0, or false, and unmatching bits return a 1, or true, and produce corresponding bits in the output ciphertext.
Symmetric Cryptography
Different aspects of cryptography are categorized in many different ways. You’ve already learned how algorithms are generally divided up into block and steaming algorithms. Now we’ll examine yet another way of dividing up cryptography into two different methods—symmetric and asymmetric cryptography. These two types of cryptography focus more on the aspect of the keys used than the algorithms, although each type has its own particular algorithms that we’ll discuss in Modules 8–10. We’ll discuss symmetric cryptography first, followed by asymmetric cryptography in the next section.
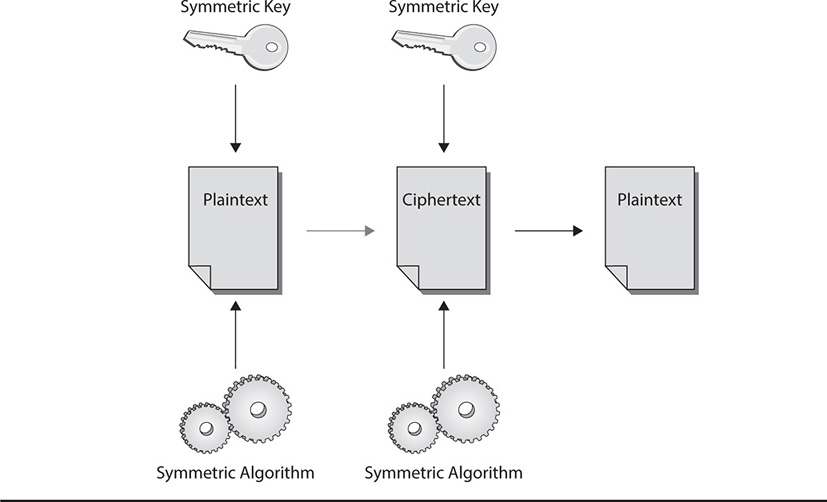
Symmetric cryptography involves the use of a single key that is known to all parties that require access to a piece of encrypted data. The same key (such as password for a protected file, for example) is used both to encrypt and decrypt the data. If someone encrypts a file or sends a secure message to another person, both persons must have the particular key used to encrypt the data in order to decrypt it.
Symmetric keys are sometimes called secret keys or session keys. Session keys, however, are normally those that are created and used for a single communications session only; they are not reused after the communications session ends. If the parties want to communicate again using symmetric cryptography, new session keys are generated by either party or by the cryptosystem in use. Figure 7-5 shows how symmetric keys are used by two parties to exchange sensitive data.
Figure 7-5 Symmetric keys in use
![]()
Symmetric key cryptography uses a single key that both encrypts and decrypts data.
Symmetric key cryptography has several advantages and a few disadvantages, which we’ll discuss now. Symmetric key cryptography is very fast and is very good at handling large amounts of data, such as storage or transmission of large files. Symmetric keys also require less computational overhead, depending on the algorithm and cryptosystem used. Since only one key is involved, if the communications are between only two parties, symmetric key cryptography works great. If more parties are involved that require access to the same encrypted data (such as a group of friends or business associates), however, the same key is still used, so many more people must have it, increasing the chances that it will get inadvertently disclosed to an unauthorized person.
Let’s look at an example. If user Meghan wants to communicate with user Amy, then both need only one secret key. If we add more users, such as Tim, Bobby, and Dawn, they each must have the same key if they are all authorized to receive or view the same encrypted data. What if, however, Meghan wants only Amy to view a particular piece of data, and she doesn’t want Tim, Bobby, and Dawn to be able to see it? She must then maintain separate symmetric keys for each party she wants to communicate with. Among a few people, as in this case, this scenario might be manageable, but imagine what happens if she needs to maintain separate keys for 100 people? How many keys must each user maintain then? Worse yet, how many total keys must be generated so that each of the 100 people can securely communicate with every other individual in the group? There’s actually an easy way to determine this: The total number of keys required is equal to the number of people in the group, multiplied by that same number less 1, and then divided by 2. In simpler terms, this equates to K = N × (N – 1)/2, where K is the total number of keys required, and N is the number of people in the group. So: K = 100 × (100 – 1)/2 = 4950. As you can see, with 100 users, a lot of keys must be generated, issued, and exchanged among each pair of users in the group who must securely communicate. That’s one of the main problems with symmetric key cryptography: it does not scale very well in larger groups or entities that must securely communicate with one another.
Key exchange refers to the process used to exchange keys between users who send a message and those who receive it. Without the key, an authorized user or message recipient will not be able to decrypt the message, and it will simply remain as ciphertext. Obviously, since only one key is used in a symmetric communication, there must be a way to deliver the key securely to the right users, with an assurance that it won’t be intercepted and compromised. E-mail is usually not the most secure way, although sometimes people send their secret keys via an e-mail message. Other ways that keys can be exchanged are old-fashioned manual means, such as giving someone a USB memory stick with a key on it or simply taking it to someone. Most of the time, especially in large organizations or when communicating with someone over greater distances, this usually isn’t practical. The problem with key exchange is getting the key to someone using a means that is considered secure—so that the key will not be intercepted and used by an unauthorized person, rendering the entire process useless. Secure key exchange is yet another problem that symmetric cryptography suffers.
In-band key exchange involves using the same communications channel you are using to send the message to send the key. This may not be the most secure way, since that channel may be monitored by a malicious person. Out-of-band key exchange involves the use of a separate, independent channel, such as snail mail, USB stick, or even a different network connection, to send the key to the authorized users. In smaller groups of users that reside near each other, key exchange may not be much of a problem. In large organizations, however, in which users may be geographically separated, key exchange can be an issue, especially when using only symmetric key cryptography.
![]()
Remember that the advantages of symmetric key cryptography are speed, efficiency, and the ability to handle large amounts of data easily. The disadvantages primarily involve scalability and key exchange.
Asymmetric Cryptography
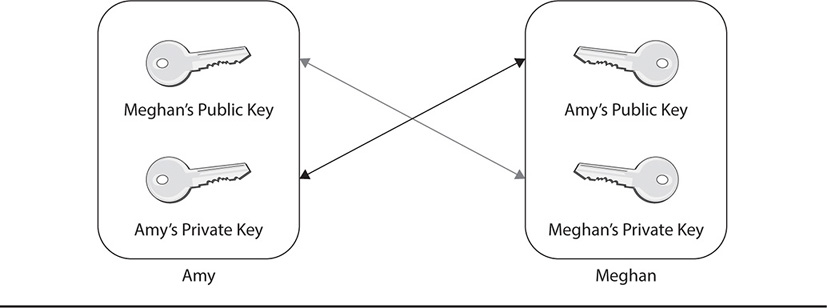
While symmetric key cryptography uses the same key for encryption and decryption, asymmetric key cryptography uses two separate keys: one key for encryption and a different key for decryption. These two cryptographic keys are called a public and a private key and are always part of a key pair. In fact, asymmetric cryptography is sometimes referred to as public key cryptography. Each user is issued or generates a key pair for her own use. These keys are not the same at all; however, they are mathematically related to each other. The public key is given away to anyone. In fact, it can even be posted on the Internet. The private key, on the other hand, is kept secret by the individual. With public key cryptography, what one key encrypts, only the other key can decrypt, and vice versa. If the key in the pair is used to encrypt a message, it cannot decrypt the same message. This makes the cryptography process, particularly sending and receiving confidential messages, a bit different from the process used in symmetric key cryptography.
![]()
Asymmetric cryptography uses two keys in a pair, a public key and a private key, which are mathematically related. What one key encrypts, only the other key in the pair may decrypt, and vice versa.
The asymmetric key process works like this: If two people want to communicate, they must each have their own key pair generated, as well as the public key of the individual they want to communicate with. Since a public key can be given to anyone or even downloaded from a central repository on the network or Internet, getting the public key is easy. To send someone an encrypted message, or to encrypt a piece of data such as a file, the user simply has to encrypt the message with the other person’s public key. Since only the other person’s private key can decrypt the message, it is protected until that other person receives and decrypts it. To exchange information back and forth, both users must have each other’s public key. Figures 7-6 and 7-7 demonstrate this process.
Figure 7-6 Distribution of public and private keys
Figure 7-7 Using asymmetric key cryptography
![]()
Earlier, we stated that keys are always kept secret. The exception to this is the public key in a key pair, which can be freely given to anyone. The private key in the pair must be kept secret and not shared with anyone.
Asymmetric key cryptography has several advantages, the major one being key exchange. Key exchange issues have been eliminated with this process, since no one really has to exchange a key. The public key is available for anyone to get. The sending party encrypts the message with the receiving person’s public key, and only the intended receiver who possesses the private key can decrypt it. Public key cryptography, unfortunately, has a couple of disadvantages as well. The first is that it is very slow and computationally intensive to generate keys. The second is that it works well only with small amounts of data; it is not suited for bulk data encryption or transmission. In Module 10, we will discuss the primary uses of asymmetric key cryptography, which involve Public Key Infrastructure, or PKI, and uses of digital certificates and signatures.
![]()
The primary advantage of asymmetric cryptography is key exchange, but asymmetric cryptography also has disadvantages, such as slower speed and the inability to handle large amounts of data very efficiently.
Hybrid Cryptography
Now that we’ve discussed both symmetric and asymmetric key cryptography, we’ll talk about how to use these two different methods together. We might use both methods together to make up for each of their individual disadvantages and to take advantage of the positive aspects of each. For example, we know that key exchange is an issue with symmetric keys. However, we have eliminated this issue with asymmetric key cryptography, since a person’s public keys are freely distributed to anyone who wants them. In a hybrid approach, a symmetric key might be generated by one user, and then that key might be encrypted with the other user’s public key. Since only the other user can decrypt it, the encrypted session key can be sent via e-mail or other non-secure means to the recipient user. When the intended recipient receives the encrypted session key, she has only to decrypt it using her own private key in her key pair. So, key exchange is one advantage of using hybrid cryptography. Another advantage is that public key cryptography doesn’t handle large amounts of data very well, and it’s very slow. If session keys can be exchanged using asymmetric cryptographic methods, then once the receiving user has possession of the symmetric session key, both users can begin to exchange encrypted data using that key. Since symmetric key cryptography is faster and handles large amounts of data very well, using this key will be more efficient.
![]()
Hybrid cryptography leverages the advantages of both symmetric and asymmetric key cryptography together and eliminates their disadvantages.
Module 7 Questions and Answers
Questions
1. Data that is said to be easily readable by humans or machines is called __________.
A. ciphertext
B. plaintext
C. coded text
D. encrypted text
2. Which of the following is the process used to convert ciphertext to plaintext?
A. Decryption
B. Encryption
C. Encoding
D. Enciphering
3. Which of the following terms describes data that is stored on media, usually in the form of files?
A. Data-in-RAM
B. Data-in-process
C. Data-in-transit
D. Data-at-rest
4. Which of the following terms refers to the output that comes from hashing a piece of text?
A. Cipher
B. Code
C. Message digest
D. Key
5. How is hashing unlike the encryption and decryption processes?
A. Hashes are not normally reversed or decrypted.
B. Hashes are encoded but not enciphered.
C. Hashes must be decrypted by a key different from the one that was used to encrypt them.
D. Hashes use the same key to encrypt and decrypt.
6. Which of the following terms describes a cryptovariable?
A. Key
B. Algorithm
C. Cipher
D. Hash
7. Which of the following components of cryptography are typically publicly known and tested?
A. Key
B. Algorithm
C. Cryptovariable
D. Cryptosystem
8. Which of the following types of algorithms encrypts specified sizes of groups of text at a time?
A. Asymmetric
B. Symmetric
C. Streaming
D. Block
9. Which of the following types of keys can decrypt only what another key encrypts? (Choose two.)
A. Public key
B. Symmetric key
C. Private key
D. Session key
10. You must implement a cryptography system in your organization. You need to be able to send large amounts of data, quickly, over the network. The system will be used by a very small group of users only, and key exchange is not a problem. Which of the following should you consider?
A. Asymmetric cryptography
B. Symmetric cryptography
C. Hybrid cryptography
D. Key escrow
Answers
1. B. Data that is said to be easily readable by humans or machines is called plaintext.
2. A. Decryption is the process used to convert ciphertext to plaintext.
3. D. Data-at-rest describes data that is stored in the form of files on storage media.
4. C. A message digest, or hash, is the resultant output from hashing a piece of text.
5. A. Hashes are not normally reversed or decrypted.
6. A. A cryptovariable is also known as a key.
7. B. Algorithms are typically publicly known and tested to ensure their dependability.
8. D. Block algorithms encrypt entire groups of bits of text, usually of specific sizes.
9. A, C. Public keys and private keys reside in a key pair, and what one key encrypts, only the other key can decrypt, and vice versa.
10. B. In this scenario, symmetric key cryptography would probably be the best choice, since the user group is very small and key exchange is not a problem. You also have the requirements of speed and efficiency, as well as the ability to send large amounts of data. All of these are advantages of using symmetric key cryptography.