MODULE 11
Understanding Identification and Authentication
In Module 3, we defined several information security concepts, including identification, authentication, and authorization. These concepts will be revisited and expounded upon in the next several modules, as we go more in depth in defining them and the methods and technologies used to facilitate them. First, in this module, we’ll look at identification methods as well as authentication factors. In Modules 12, 13, and 14, we’ll look at authorization concepts, authentication methods, and managing account credentials, respectively.
Authentication Concepts
Before we get into the details of identification and authentication, let’s revisit what these terms mean. They are often used interchangeably, but they are actually distinct parts of the process of accessing systems and data. Identification takes place when you are presenting credentials to a system to indicate exactly who you are with respect to the system. Credentials, also called authenticators, are the pieces of information you present to the system to assert your identity. Credentials could include any one of several types of identifiers, which we’ll discuss shortly. Authentication, as you remember, is the process of verifying that the credentials presented are valid and that they do indeed belong to a user authorized to access the system. The credentials are validated against a database of user credentials, and if those credentials match, the user is allowed to access the system and is said to be authenticated. Authorization, the next part of this access process, covers the rights, permissions, and privileges that a user has only after he has been successfully authenticated to a system. We’ll cover authorization more in Module 12. We’ll look at authentication factors and identification methods in the remainder of this module, as well as trusted authentication methods.
![]()
Understand the difference between identification and authentication: identification involves presenting credentials to a system, while authentication involves the validation of those credentials.
Authentication Factors
Authentication systems use different characteristics of identification to identify a user and validate her credentials. These different methods are sometimes called factors and are dependent upon the method of identification used. We’ll discuss some of the more common factors in the next few paragraphs. Several different factors can be used either separately or, preferably, together. If one factor is used, we call the process single-factor authentication. If more than one factor is used, we refer to it as multifactor authentication (previously also known as two-factor authentication, since traditionally only two factors were used). Obviously, using more than one factor at a time is considered more secure and a better form of authentication to use. Let’s discuss the factors we can use in different authentication methods.
![]()
Understand the difference between single-factor and multifactor authentication. Single-factor authentication uses only one factor, and multifactor uses at least two, and possibly more, factors.
Something You Know
The first factor that we’ll discuss is probably the most commonly used. This factor is called the knowledge factor, and it relates to something you know. It is used, for example, when you identify yourself to a system with a username and password combination. You know your username and password, so it is presented to the system from your memory. Although you use two particular details for this credential, it is still considered a single-factor form of authentication because it involves only something you know. This single-factor form of authentication can be compromised easily if someone gains access to it—in this case, if they know your username and password. If you’ve written them down somewhere or told someone your username or password, you have effectively transferred that factor to the other person, and it could be considered compromised.
Something You Have
The next factor is also fairly commonly used these days. This factor relates to something you have and is also called the possession factor. Possession means that you physically possess an object that is used as an authenticator. An example of this type of authenticator would be an automated library card or gym membership card, which you could scan with an automated reader at the door of the facility. When used in this manner, the card could be considered a single-factor form of authentication if you don’t have to do anything else to use the card except for scanning it. More often than not, however, these types of authenticators usually require some additional method of authentication. Typically, this could be something you know, such as a personal identification number (PIN) or password. When used in this manner, this would be considered a multifactor form of authentication, since you are required use two different types of factors: the possession factor and the knowledge factor. Smart cards and tokens are probably the most commonly used multifactor form of authentication that uses the possession factor. Smart cards are plastic cards with electronic chips in them, which contain a limited amount of information related to the user, such as public and private keys. Smart cards can be used to access facilities, secure areas, and even computer systems. Tokens are also physical objects that usually display a complex series of changing numbers. When a token is used to access a system, the user must also enter a PIN or password known only to her, in conjunction with the token and its own number. The system uses these two factors to validate the user. An example of a token is shown in Figure 11-1.
Figure 11-1 A hardware token
Something You Are
Another factor that is becoming more widely used is the inherence factor. This factor relates to something you are, and it is the basis of biometric authentication, discussed a bit later in the module. This factor relates to a person’s unique physical characteristics that can be used as a form of identification, such as fingerprints, retinal eye patterns, iris patterns, handprints, and voiceprints. These are all very unique characteristics of a person and very difficult to replicate or fake. These factors can also be used in conjunction with an additional factor in a multifactor authentication system. For example, newer laptops and smartphones often arrive with a fingerprint scanner built into them, and the user must scan his fingerprint and enter a PIN or password to access the system. Secure facilities may also require fingerprint or handprint factors in their authentication systems. It’s also not unusual to see multiple inherence factors used for an even stronger authentication system. We’ll discuss more about inherence factors when we talk about biometric authentication systems in the next section.
Something You Do
The next factor is a bit less common but slowly coming into mainstream use as authentication technologies become more mature. This factor relates to something you do, meaning that when you present your credentials to the system, you are required to perform an action. The best example of this type of authentication factor is when you use a finger or hand gesture on a smartphone or tablet to log in. The pattern you create using your hand is the something you do, and this pattern is stored in the user credential database of the system you’re accessing. When the authentication system confirms that these patterns match, you are allowed access the device or system. Some forms of authentication that use this type of gesture are single-factor if that’s the only thing you’re required to do to access the system. Other authentication systems may also require an additional factor, such as entry of a PIN, making it a multifactor form of authentication.
Somewhere You Are
Yet another factor is the location factor, which relates to where you are when you authenticate. This factor could use either physical or logical locations and requires you to be a in a certain location when you authenticate to the system. For example, from a physical perspective, in a highly secure facility, you may be required to be at a certain workstation, located in a certain room, in order to authenticate to the system before you are allowed to work on it from any other location. Because you would likely have to authenticate with other physical protections and controls to get into this room, this would be a very secure form of authentication that would allow only a very limited number of people to access the system. From a logical perspective, a location factor could be used as an authentication factor if you are required to authenticate from a certain device that had a specific digital certificate assigned to it, or from behind a certain network device, physical port, or even a subnet. This doesn’t necessarily limit you by requiring authentication from a specific physical location; rather the logical location with respect to the network and the authentication system being used would be important. This might ensure that you did not attempt to authenticate from an untrusted network or device, for instance.
Time/Temporal
Time, called the temporal factor, can also be used as a factor in authentication systems. You could see temporal factors used in a few different ways. The simplest way to use it would be to limit the timeframes in which users are allowed to access the system, limiting their authentication only to a specific set of hours, for example. You might set a policy that allows users to log in to the system only during normal business hours and days, such as Monday through Friday. In this policy, you might further restrict them from logging in and authenticating during nonbusiness hours. A less frequently used method of using time as an authentication factor might require you to perform an action, such as scanning a smart card or typing in a PIN, and then giving you only a certain amount of time to complete the authentication process using an additional method or factor. This might be used if you were working in a secure facility and had to travel from the control entry point to another system to authenticate, when you’re only given a certain amount of time between those actions. This would prevent an unauthorized user from interrupting the authentication process and attempting to perform the second part of the authentication sequence, and it also serves to help track user movements and actions. Typically, a very secure facility might use this type of authentication system.
![]()
The most common factors that authentication systems use include the knowledge factor (something you know), the possession factor (something you have), and the inherence factor (something you are).
Identification Methods
Now that we have discussed the factors that can be used during the identification and authentication processes, let’s look at identification methods. Each of these methods uses a particular type of identifier or authenticator, and each has its advantages and disadvantages. When selecting methods for identification, you should carefully consider whether or not they are single-factor or multifactor, as well as how they secure user credential information and how they interoperate with the authentication and authorization systems in the network.
In general, identifiers should be unique and used by only one individual. This enables identifiers to be traceable to an individual user or other entity, ensuring accountability and facilitating the auditing process. Authenticators should also be kept secure by individuals; when authenticators are issued, the individual should acknowledge their receipt and acknowledge that they understand their use and care. Credentials should not be shared with anyone or written down (in the case of usernames, passwords, or other knowledge factors). They also shouldn’t be carelessly lost or left unattended (in the case of smart cards or physical tokens, for instance). Group accounts, which will be discussed in detail in Module 14, should also be avoided whenever possible. In group accounts, several people share the same username and password to access a system or network. Finally, identifiers should be considered as sensitive as the level of information they are used to access; in other words, if sensitive data uses identifiers and authentication methods that differ from routine information, these identifiers should be considered equally as sensitive as the information they protect, since an unauthorized person, if they possess these authenticators, could access the same information.
Username and Password
We have discussed, and will continue to do so throughout this book, the use of username and password combinations to authenticate systems. This is probably still the most commonly used method of authenticating to systems and data, but, unfortunately, it is the most unsecure, because it uses only a single factor to authenticate to a system, the knowledge factor. Knowledge is easily transferred from one person to another, either intentionally or accidentally, so this form of authentication can be easily compromised. On the other hand, if you are using a two-factor method of authentication, such as a smart card and PIN, even if you inadvertently lost your smart card, an unauthorized person couldn’t use it, since the person would not have the other factor—the PIN. If only one factor is compromised, the system still can’t be accessed.
Most larger organizations, and even some users on personal systems, are slowly moving away from the use of username and password combinations, because they are so insecure. Even when users keep their passwords safe and secure, usernames are easily guessable, because they normally follow a standardized format in an organization. Passwords are also easily cracked using various methods, as we will discuss in Module 15. In general, the use of username and password combinations, or any other single-factor method of authentication, is becoming more and more discouraged in favor of using multifactor forms of authentication.
![]()
Even though there are two elements to username and password combinations, it is still considered single-factor authentication because it uses only one factor, the knowledge factor, to authenticate. This is still true even if you must answer security questions along with inputting a username and password combination—they’re all based on only the knowledge factor.
Personal Identification Verification Card
We briefly mentioned the use of smart cards earlier in the module, which are personal identification verification cards. These cards allow access to facilities and systems and may also serve as a means of identification for human beings, since they frequently also have the user’s photograph and other identifying information on them. Most cards of this type can be read by magnetic card strip readers, but some also have passive radio frequency identification (RFID) chips in them that allow them to be read by close proximity to the reader, so the user need only scan the card near the reader in order for the data to be transmitted and read.
Smart cards also typically have an embedded chip that contains some degree of personal information. In addition to information such as user’s name, organization, and other employee information, the chip could also store personal digital certificates as well as public and private keys. The private key would be encrypted and could be accessed and used only when the user also input the corresponding PIN or password to verify the person’s identity to the authentication system. Most smart cards are part of a multifactor authentication system, since you must physically possess the card and use a PIN to gain access. The classic example of simple smart card authentication that almost everyone is familiar with is the use of an ATM card, which requires both the card and the PIN to access a bank account. Figure 11-2 shows an example of a smart card and keypad used to enter a PIN, which controls access to a secure area.
Figure 11-2 Using a smart card and PIN to access a secure area
![]()
The use of smart cards and PIN combinations are the most common example of multifactor authentication.
Biometric Authentication
Biometric authentication is a system that uses inherence factors (a person’s physical characteristics) as at least one of the factors to authenticate a user, along with other factors, such as knowledge, possession, or temporal factors. Examples of biometric factors include fingerprints, handprint geometry, voiceprint, retinal or iris patterns, and even DNA. These physical characteristics are unique to every individual and are very difficult to mimic or fake. This makes biometric authentication an extremely secure form of authentication in theory, although sometimes the methods used to implement it are not as secure and can be circumvented. With biometric authentication, in particular, you should be familiar with some terms and concepts for the exam and as a security professional.
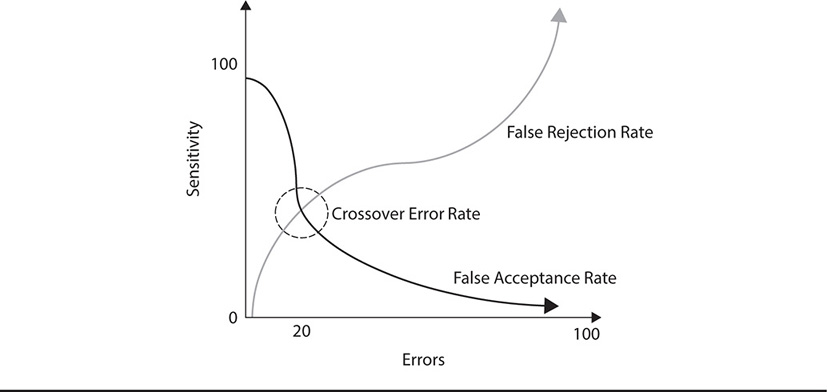
Because biometric systems are not necessarily built to be foolproof, several levels of errors are associated with them. The first term we’ll discuss is the false rejection rate, or FRR. This is also known as a type I error. This relates to the error caused from rejecting someone who is in fact an authorized user and should be authenticated. The false acceptance rate, or FAR (also known as a type II error), indicates the level of errors that the system may generate indicating that unauthorized users are actually identified and authenticated as valid users in a biometric system. Both of these error rates can be dealt with by tuning the relative sensitivity of the biometric system in question; however, tuning it too much to reduce one type of error usually results in increasing the other type, so a trade-off is involved. This trade-off is usually tuned to the level of the crossover error rate, which is the point at which one error rate is reduced to the smallest point that does not result in an increase in the other error rate. This concept is illustrated in Figure 11-3.
Figure 11-3 The crossover error rate
![]()
Understand the difference between the false reject rate (FRR) and the false acceptance rate (FAR) in biometrics. The FRR is the rate of errors from incorrectly rejecting authorized users. The FAR is the rate of errors from incorrectly authenticating unauthorized users. The crossover error rate (CER) is the point at which the system must be tuned to reduce both types of errors effectively without increasing either one of them.
Trusted Entity Authentication
Trust is a cornerstone of authentication for several reasons. First, the system must be able to trust that the user presenting credentials is in fact the user represented by those credentials. Second, the system must be able to trust the integrity of the user credentials database, in that the data is current and correct and the system is functioning normally and returns the correct information so the user can be validated. Organizations must trust their own authentication systems and, sometimes, those of another entity or organization. In this section, we’ll discuss authentication across organizational boundaries, both from within and outside an organization. This authentication often involves trust relationships that must be established between hosts, systems, and other organizational entities.
Centralized and Decentralized Authentication
When an organization manages all of its user accounts, policies, credentials, and authentication systems as one unified system, this is said to be centralized authentication. In a centralized enterprise authentication system, credentials are stored in one database and user accounts have uniform security policies and requirements that apply across the entire organization. The authentication system performs authentication services for all systems, data, and resources across the enterprise. Often, you will hear the term single sign-on in relation to a centralized system; this means that a single set of user credentials is used to access resources across the enterprise. Whether a user is allowed or denied access to those resources depends on the authorization and access control policy in place, not the user’s credentials in the authentication process. In a centralized model, all hosts and resources trust the central credentials database to take care of authenticating the user for them; after that, it’s merely an issue of whether or not that user has the correct rights, privileges, and permissions to access a resource or perform an action.
A decentralized model is quite different. In this model, authentication occurs on a per-system, per-host, and even per-resource basis. No centralized authentication mechanism serves to validate the user’s identity first; each system or resource makes an authentication decision based upon its own user credentials database or access control list. For example, in a small office setting, each user may be an administrator for her own workstation and have the ability to create accounts on that workstation. If another user wants to access a shared folder on another user’s workstation, he would need a separate username and password just for that resource. It usually won’t be the same username and password he uses for his own workstation; even if an effort is made to duplicate these across workstations, both accounts still reside in separate databases on each workstation and are therefore not technically the same. If a password in one set of credentials changes, for example, this doesn’t guarantee that the other set of credentials on the other workstation will be updated as well. Decentralized systems do not trust each other’s credentials database or authentication mechanisms; they require a user to authenticate using his own systems and credentials. Decentralized authentication also means that user account and password policies will be different as well. We discuss the centralized and decentralized management of credentials further in Module 14.
Trusts and Federated Authentication
Outside of organizational boundaries, users must often be authenticated to systems within another organization’s infrastructure. Examples of this include business partner relationships, where employees are expected to access documents in the partner company’s network, or university students who have to access an affiliate university’s shared library resources. In these examples, each organization may have its own centralized authentication system that trusts its own users and systems, but not users outside the organization’s boundaries. Two ways of allowing outside users to access resources internal to an organization, and authenticating those users, are though trust relationships and federated systems.
A trust relationship is established between authentication systems, allowing users from each system to authenticate to the other’s resources. The authentication system in one company, for instance, may trust the authentication decisions (and vice versa) of a partner company, allowing its users to access sensitive resources such as shared folders and files. Trusts can be one-way or two-way (bidirectional); two entities may trust each other’s authentication systems, but the relationship can also be such that entity A trusts entity B’s authentication systems and decisions, but the reverse is not true. One variation on this trust relationship is called a transitive trust. In this type of trust relationship, there are more than two entities; if Company A trusts Company B’s authentication systems, and Company B trusts Company C, then Company A may also trust Company C’s systems by default. More often than not, though, trust relationships between entities must be explicitly established, instead of defaulting to transitive trusts.
![]()
Understand how trust relationships work with authentication, particularly how a transitive trust relationship works. A transitive trust usually means that the organization trusts another entity simply because they are trusted by someone else that the organization trusts.
A federated system involves the use of a common authentication system and credentials database that multiple entities use and share. This ensures that a user’s credentials in Company A would be acceptable in Company B and Company C, and only access permissions would be the determining factor in accessing systems and data. Windows Active Directory is a good example of a federated system in practice; user credentials from different domains could be used in other domains if they are all part of the same Active Directory forest.
Module 11 Questions and Answers
Questions
1. Which of the following is the process of validating user credentials?
A. Identification
B. Authorization
C. Authentication
D. Accountability
2. Each of the following would be considered an example of an authenticator, except:
A. Username and password
B. Smart card
C. Token
D. Folder permissions
3. Which of the following authentication factors relies on a specified time period, during which a user must authenticate?
A. Temporal
B. Location
C. Inherence
D. Possession
4. Which of the following authentication factors would require that you input a piece of information from memory in addition to using a smart card?
A. Possession
B. Knowledge
C. Inherence
D. Temporal
5. All of the following are examples of single-factor authentication, except:
A. Using a username and password combination to log on to a computer system
B. Answering security questions to reset a password
C. Use of a magnetic-strip security card to enter a secure door
D. Use of a smart card and PIN to log on to a computer system
6. Which of the following is the error rate at which biometric systems should be calibrated?
A. False positive rate
B. False rejection rate
C. False acceptance rate
D. Crossover error rate
7. Which of the following are factors used in biometrics? (Choose two.)
A. Password
B. Handprint geometry
C. Token
D. Retinal patterns
8. You are implementing an authentication system for a new company. This is a small company, and the owner has requested that all users be able to create accounts on their own individual workstations. You would like to explain to the owner that centralized authentication might be better to use. Which of the following are advantages of centralized authentication? (Choose two.)
A. Centralized security policies and account requirements
B. Ability of individuals to set their own security requirements
C. Ability to use single sign-on capabilities within the entire organization
D. Requirements have different usernames and passwords for each workstation and resource
9. Which of the following scenarios describes a transitive trust situation?
A. Company A trusts the authentication systems of Company B, and vice versa.
B. Company A trusts the authentication systems of Company B, but Company B does not trust Company A’s authentication systems.
C. Company A trusts the authentication systems of Company B, and Company B trusts the systems of Company C, so Company A trusts Company C.
D. Company A trusts the authentication systems of Company B and Company C, both explicitly.
10. Which of the following terms describes a common authentication system used by multiple entities, enabling users from any of the entities to authenticate seamlessly to one another’s systems?
A. Federated
B. Decentralized
C. Centralized
D. Transitive trust
Answers
1. C. Authentication is the process of validating user credentials.
2. D. Folder permissions have to do with authorization, not authentication. Authenticators are elements used in the identification and authentication process.
3. A. The temporal authentication factor relies heavily on time and might be used to require a user to authenticate during a specified time period.
4. B. The knowledge factor would require that you input a piece of information, such as a password or PIN, from memory in addition to using a smart card.
5. D. Using a smart card and PIN is an example of multifactor authentication.
6. D. The crossover error rate is the point at which biometric systems should be calibrated to reduce false acceptance and false rejection rates.
7. B, D. Both handprint geometry and retinal patterns are factors used in biometric authentication systems.
8. A, C. Centralized system security policies as well as the ability to use single sign-on throughout the organization are two advantages of centralized authentication.
9. C. In a transitive trust situation, Company A trusts the authentication systems of Company B, and Company B trusts the systems of Company C, so Company A trusts Company C.
10. A. A federated system is a common authentication system shared among all people entities. It allows users from any of the entities to access systems in one another’s infrastructure.