MODULE 29
Wireless Threats
Attacks on wireless networks have never been more common than they are today—but why? Given that 802.11 wireless networks have been around for more than 15 years, you’d think by now we’d be better at securing them. Truth is, we are better—but the bad guys have gotten better as well.
In this module, we’ll discuss various wireless threats and attacks that can be carried out against wireless networks, unsecure wireless protocols (such as the famous and surprisingly still relevant WEPCrack), and access points (APs). This module will discuss the attacks at length, so that by the next module, you’ll be ready to learn the various ways you can harden wireless access points and networks against these types of attacks.
Wireless Attacks
Various types of attacks can be used against a wireless network. Some of them involve sophisticated methods of intercepting and cracking the secret encryption keys that wireless networks use to authenticate clients and encrypt wireless traffic as it passes. Other types of attacks are more simplistic and involve using another access point to fool people into joining it instead of the legitimate access point. There are also attacks against Bluetooth networks that can be effective in intercepting any data passed between those devices. In the following sections, we’ll look at some of these attacks and discuss how they can be perpetrated.
Rogue Access Points
Rogue access points are a form of attack that involves setting up a false or fake AP to attract unsuspecting people to connect to it, so that a malicious person can then monitor all of the victims’ network traffic. Hackers use several techniques to set up rogue APs. In a basic attack, the attacker uses an AP configured for very weak or nonexistent authentication. This makes the victim think that it’s an open, or free, Internet AP. Often a rogue AP will broadcast a very strong signal so that users think it’s the best free Internet access point compared to several others. Rogue APs work very well where there are several APs already transmitting, such as areas within range of businesses or establishments that offer free wireless access to their customers.
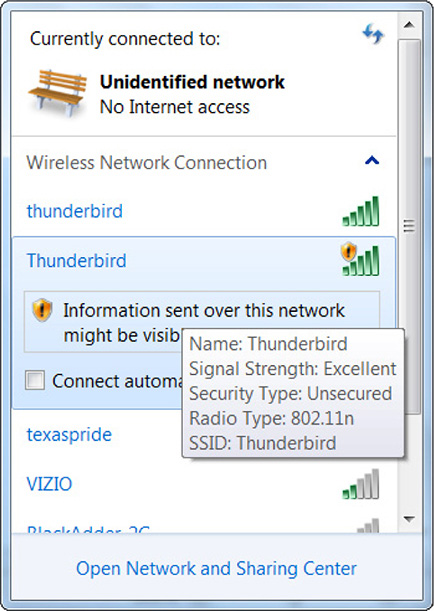
Another variation of this attack is called the evil twin attack. In this attack, a hacker could set up a rogue AP that is broadcasting the same (or very similar) Service Set Identifier (SSID), which appears as the wireless network’s name to ordinary users. Often, however, these evil twins do not use the same security levels as the legitimate AP, making it easy to connect to them. Unsuspecting users connect to this AP, thinking that it’s one that they normally should connect to. Once connected, the attacker can intercept the user’s network traffic through the evil twin, including usernames, passwords, and any other traffic passed over the AP. The evil twin attacker can gain user credentials that may also be used on other wireless networks, allowing the attacker to connect to the legitimate APs and begin an attack on those networks. The hacker may even further connect this rogue AP to the Internet, so the user never suspects that she is connected to the rogue AP. Figure 29-1 shows an example of how an evil twin wireless network also appears with a legitimate one. Notice that the two are named similarly but are not configured the same in terms of required security.
Figure 29-1 An evil twin rogue wireless access point is named similarly to a legitimate network AP.
Jamming and Interference
Occasionally, a wireless network can experience interference from another wireless device, which can occur, for example, when two wireless access points are using adjacent frequencies or channels. Interference can interrupt and interfere with wireless network transmission and reception. For the most part, this interference is unintentional. Jamming is a form of intentional interference on wireless networks, designed as a denial-of-service (DoS) attack. This type of attack is perpetrated by overpowering the signals of a legitimate wireless access point, typically using a rogue AP with its transmit power set to very high levels. However, other electronic devices can also be used to create interference, or jamming, in wireless networks, including specialized devices that can be acquired from the Internet or put together by hobbyists. The only way to prevent jamming and interference is to look proactively for sources of wireless signals that are not coming from the corporate wireless network. The sources are usually in the same frequency range and may come from malicious wireless clients or rogue wireless access points.
Wardriving and Warchalking
Wardriving has its roots from way back in the days when wireless networks first came about. A person who is wardriving literally drives around looking for unsecured wireless networks to see which ones have stronger signals, which are unsecured, and their locations. (A vehicle isn’t really necessary for wardriving; a potential attacker could also walk around and look for these unprotected wireless networks and join them surreptitiously, or at least record details about them.) Note that simply searching for and detecting wireless access points isn’t unlawful; however, connecting to them may be illegal depending upon the laws in your area. Figure 29-2 shows an example of how one might go wardriving, with the passenger equipped with the right software and wireless equipment.
Figure 29-2 Wardriving using a netbook and a wireless USB card (photo courtesy of Sarah McNeill Photography, used with permission)
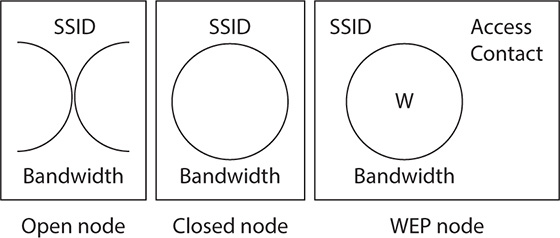
Warchalking is similar to wardriving, except that a potential attacker marks attributes of a potential wireless access point on the sidewalk or on a wall in an inconspicuous place, near the access point, with a piece of chalk (hence the name). The person who is warchalking would write down items such as the authentication method, SSID, and so forth, using particular symbols known only to other warchalkers. This lets others who can read the symbols know that they can connect to wireless access points, usually with no security protections to worry about. This attack was more prevalent years ago when there were fewer wireless networks, particularly networks that were not as secured as those we have today. Warchalking is rarely used these days, due to the proliferation of legally free wireless networks that many businesses provide to their customers. Figure 29-3 shows an example of warchalking symbols.
Figure 29-3 Warchalking symbols
Packet Sniffing
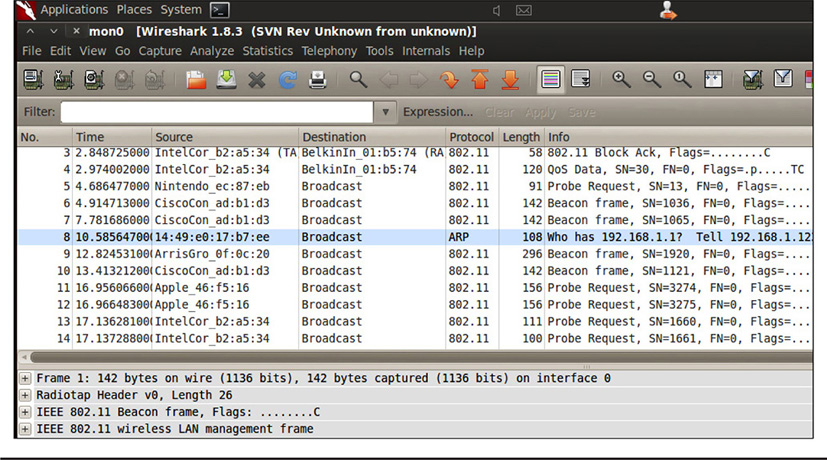
Just as wired networks can be sniffed for unencrypted data that can be captured and analyzed, wireless networks are also susceptible to traffic sniffing. Sniffing traffic on wireless networks, however, can be a little bit more difficult. Usually, an attacker has to have a special wireless network card that can intercept packets and inject traffic on to the network. The attacker usually also must have a special driver for the network card, if he is using the Windows operating system, or he must be able to put a network card into what’s called monitor or promiscuous mode in Linux. Once the attacker has his equipment set up, it’s simply a matter of using the sniffing software of choice, such as Wireshark, for example. Figure 29-4 shows a Wireshark capture of a packet sniffing session conducted on a wireless network.
Figure 29-4 Packet sniffing a wireless network
Deauthentication Attack
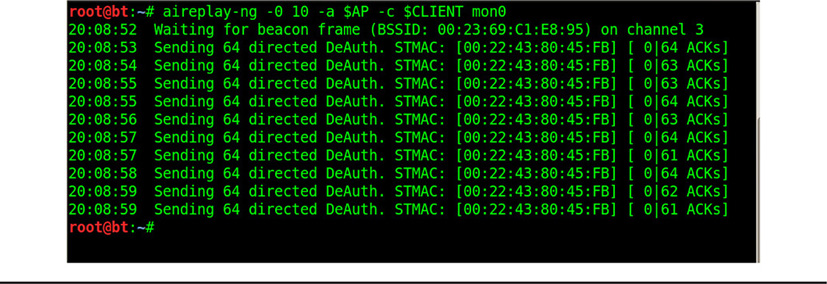
If the wireless network traffic is encrypted, then the only traffic the attacker is usually going to get are beacon frames and other types of wireless management traffic, in addition to a lot of encrypted traffic he can’t read. The attacker must already have the wireless key or conduct attacks against the wireless network to get the key. Covering the various attacks that a hacker can launch against a wireless network are beyond the scope of this book, but some of them involve disconnecting (also called deauthenticating) a wireless host from the AP, so that the victim is forced to reconnect and exchange the wireless key, allowing the attacker to intercept the key and crack it. There are different methods for conducting this type of attack, and if it is successful, an attacker can either join or intercept traffic from the wireless network. Figure 29-5 shows an example of a deauthentication attack, conducted using the aireplay-ng command in the Aircrack-ng tool suite. This tool is popularly found on Linux-based systems, particularly security distributions.
Figure 29-5 Conducting a deauthentication attack against a wireless client and its AP
Near Field Communication
Near field communication (NFC) is a newer technology that allows devices to send very low-power radio signals to each other by using a special chip implanted in the device. NFC requires that the devices be extremely close to, or even touching, each other. NFC can be used for a wide variety of consumer and business applications, including quick payments with NFC-enabled smartphones and cash registers, parking meters, and other really cool and convenient transactions. NFC uses radiofrequency identification (RFID) technologies and unfortunately is vulnerable to several types of attacks. These attacks include eavesdropping by another NFC device, man-in-the-middle attacks, and relay attacks (relaying modified information back and forth from the victim’s device, pretending to be the victim). Many Wi-Fi Protected Setup (WPS)–enabled devices (see “WPS Attacks” later in this module) also use NFC, making wireless hacking of WPS-enabled networks trivial.
Replay Attacks
In a replay attack, data, particularly credentials such as usernames and passwords, are intercepted and replayed back on the network to an unsuspecting host. The goal of the replay attack is to retransmit those credentials back to a host, effectively allowing the attacker to impersonate the victim. Credentials or other data passed in clear text is most vulnerable to replay attack, although certain versions of weak encryption algorithms can also be vulnerable to these types of attacks. Even if the attacker can’t read the victim’s credentials due to encryption, weak authentication methods may allow retransmitted credentials to be used to authenticate to a host. Note that this type of attack isn’t unique to wireless networks; wired networks also suffer from replay attacks.
Strong encryption methods are one defense against this type of attack. Another defense against this attack is through the use of timestamping, which limits the use of the credentials to a very narrow time period. The use of the Kerberos authentication protocol in Windows Active Directory networks, which makes heavy use of timestamps, counters the problem of replay attacks. Still another way of defending against this type of attack is for the originating host to digitally sign the traffic it sends. This assures the receiving host that the credentials or other data it receives are authentic.
WEP/WPA Attacks
Wired Equivalent Privacy, or WEP, was the first attempt at securing wireless networks. Before WEP came into being, no native encryption technologies were used on wireless devices. WEP was designed to make wireless networks at least as secure as their wired counterparts. WEP uses either 40-bit or 104-bit encryption keys, which is good, but sadly WEP uses a poor implementation of RC4 encryption. Like any streaming encryption, RC4 needs initialization vectors (IVs) to seed its encryption methods for protecting wireless traffic. Unfortunately, the IVs in WEP are considered weak, in that they are only 24 bits in length. This short length guarantees that WEP must repeat the IVs frequently, meaning that after sniffing a few million packets, an attacker can crack the WEP key mathematically (an IV attack). Today a number of off-the-shelf tools (such as the freeware Aircrack-ng) make cracking any WEP-encrypted SSID trivial.
Wi-Fi Protected Access (WPA) was designed as an interim fix for some of the issues that plagued WEP. To prevent IV attacks, WPA uses a protocol called Temporal Key Integrity Protocol (TKIP), which generates a new 128-bit key for every packet it sends, ensuring that there is no repetition. Secondly, WPA introduced two authentication modes: a very robust RADIUS authentication called WPA-Enterprise (often called WPA-ENT) and a much simpler and easy to use shared-key authentication called WPA Personal Shared Key (WPA-PSK). However, WPA had its weaknesses. It still used RC4 encryption, and over time cracking methods were developed to crack WPA—although it is much harder to crack WPA than WEP.
![]()
On older wireless access points there is usually an option to choose between TKIP or the Advanced Encryption Standard (AES). Always choose AES, unless you have old equipment that can’t handle it—and then upgrade your old equipment as soon as possible!
WPA2 was the name given by the Wi-Fi Alliance to the final IEEE 802.11i standard adopted for more secure wireless encryption and authentication. WPA2 is backward-compatible with WPA devices and applications, since it can use TKIP as well. However, its preferred encryption protocol is the Advanced Encryption Standard (AES), which is considered to be much stronger. Although both WPA and WPA2 are very strong wireless security protocols, if your SSID uses Pre-Shared Key with a weak passphrase, they are both easily cracked, since the four-way handshakes they use to negotiate a connection between devices contain the WPA/WPA2 encryption key. This four-way handshake can be intercepted after a deauthentication attack forces a wireless client and AP to reestablish their connection and reauthenticate with each other. Once intercepted, a weak key can be cracked using standard dictionary or brute-force attacks, again using tools such as Aircrack-ng.
WPS Attacks
Around 2006, a number of Wi-Fi vendors, tired of too many support calls, created Wi-Fi Protected Setup (WPS). The goal of WPS is to make it much easier to set up a secure wireless network for consumers. A WPS-enabled wireless router can connect to another WPS device (wireless printers are the most common) through a number of different methods. These methods all used a WPS personal identification number (PIN), which was enabled simply by pushing a button on the wireless router and the device. This PIN was used as the network’s secure WPA key. Unfortunately, an idea that was meant to help make home users more secure was actually making them more insecure. A vulnerability was discovered in 2011 that took advantage of the fact that the WPS PIN was easily brute-forced and discovered. The solution to this vulnerability was simply to turn off WPS on the user’s wireless access point.
Bluejacking
Although becoming rarer these days, Bluetooth attacks do exist. In the early days of Bluetooth, protocols did not have adequate security measures built in, and devices by default allowed themselves to connect with any Bluetooth device that requested it. This enabled attackers to connect their Bluetooth device surreptitiously with an unsuspecting person’s device and steal information from it, such as contacts and other personal information. These attacks are becoming rare because the Bluetooth protocol has evolved over time, and now more security measures are built into the protocol by default. Additionally, most Bluetooth devices have to undergo a type of authentication with each other, called pairing, making it such that intercepting traffic between them is more difficult. Another factor contributing to the rarity of these types of attacks is that Bluetooth has a very limited range: an attacker would have to be within around 35 feet of the victim to conduct the attack successfully.
There are, however, legacy devices in use, as well as new devices that are not configured securely, which are susceptible to Bluetooth attacks. One of the major attacks on Bluetooth is called bluejacking. Bluejacking involves sending data to a target device, such as a smartphone, usually in the form of unsolicited text messages. Although mostly harmless, bluejacking can be annoying at best and constitutes harassment at worst. Bluejacking does not involve removing data from the device, however.
Bluesnarfing
Bluesnarfing is yet another Bluetooth attack, in which the attacker is actually able to steal data from the target device by connecting to an unsuspecting user’s device. Bluesnarfing can be used to get contacts, e-mails, text messages, pictures, videos, and other sensitive data. Once again, this type of attack is very rare these days, since most vendors have fixed vulnerabilities in their device operating systems, and because of upgrades to the protocol itself.
Module 29 Questions and Answers
Questions
1. Which of the following would describe an attack in which the attacker sets up a malicious access point configured almost identically to a legitimate one?
A. Impersonation attack
B. Evil twin attack
C. Spoofing attack
D. Rogue traffic attack
2. Which of the following can happen if an attacker sets the power levels on a rogue access point to overpower the wireless transmissions of a legitimate access point?
A. Jamming
B. Beaconing
C. Deauthentication
D. Spoofing
3. Which of the following older attacks involves marking attributes of wireless access points on walls or the sidewalk?
A. AP tagging
B. Geo-tagging
C. Wardriving
D. Warchalking
4. Which of the following actions may be considered illegal, depending upon where they take place? (Choose two.)
A. Wardriving
B. Warchalking
C. Jamming attacks
D. Deauthentication attacks
5. You are installing a wireless network for a small business. You decide to sniff traffic on the wireless network to see if it is secure. You can read all the traffic through your wireless sniffer program. Which of the following should you configure on the wireless network to prevent packet sniffing?
A. Encryption settings
B. Username and password
C. Private IP address
D. Access point power settings
6. Which of the following technologies requires that two devices be touching each other in order to communicate?
A. 802.11i
B. WPA
C. Bluetooth
D. NFC
7. Which of the following describes an attack in which an attacker captures credentials and transmits them to another host for authentication?
A. Replay attack
B. Rogue access point
C. IV attack
D. Packet sniffing
8. All of the following are valid security issues that allow attacks on WEP, except:
A. 24-bit initialization vectors
B. Implementation of RC4
C. Repeated keys
D. Use of AES
9. Which of the following is an attack vector on networks that use WPA or WPA2?
A. Use of RC4
B. Weak passphrases
C. 24-bit initialization vectors
D. Use of AES
10. Which of the following attacks enables a malicious person to steal data via Bluetooth devices?
A. Bluesneaking
B. Bluejacking
C. Bluesnarfing
D. Rogue access point
Answers
1. B. In an evil twin attack, the attacker sets up a malicious access point configured almost identically to a legitimate one.
2. A. Jamming can occur if an attacker sets the power levels on a rogue access point to overpower the wireless transmissions of a legitimate access point.
3. D. Warchalking is an older attack that involves marking attributes of wireless access points on walls or the sidewalk with chalk.
4. C, D. Both jamming and deauthentication attacks may be considered illegal, depending on the area in which they are conducted. Wardriving and warchalking are not necessarily illegal, as long as there is no effort made to connect illegally to someone else’s wireless network.
5. A. Configuring encryption on a wireless network can prevent packet sniffing.
6. D. NFC requires that two devices be touching each other in order to communicate.
7. A. In a replay attack, an attacker captures credentials and transmits them to another host for authentication.
8. D. WEP does not use AES as its encryption protocol.
9. B. Use of weak passphrases is an attack vector on networks that use WPA or WPA2.
10. C. Bluesnarfing enables a malicious person to steal data via Bluetooth devices.