MODULE 33
Third-Party Security
If you had to worry about security only within the walls of your own organization, your life as a security professional would be far less complicated. Unfortunately, however, in this day and age, this isn’t the case. A decade or so ago, most businesses tried to do everything in-house with regard to IT security. Today, however, it’s not unusual to find a great many services outsourced by companies to third parties, or even located off the company’s campus and in the cloud. Although the company can often transfer responsibility for services to a third party or cloud provider, the ultimate accountability usually still rests with the organization. While third-party providers may be accountable to your organization for their actions and how they handle your data and services, your organization is still accountable to its shareholders, customers, management, and, of course, the law.
Because of this accountability issue, as a security professional within your organization, you still have to maintain levels of security when dealing with third-party providers that meet or even exceed the levels you provide within the organization. This module will discuss aspects of third-party security, some of the issues that can arise when dealing with these providers, and how you can help maintain a level of security and risk that’s commensurate with the same level you provide with in-house services.
Third-Party Business Practices
So why has outsourcing services and contracting with third-party providers become so attractive to companies these days? Well, several factors have affected the business practices that allow third-party providers to flourish in today’s business environment. Cost is a primary factor. It’s often cheaper to outsource services and even entire data centers to third-party providers that are primarily engaged in those types of businesses. This is because they’ve already invested the money and resources into their infrastructures and provide the services to a large volume of customers, which reduces their costs. Think of how much it would cost to build your own data center today—a lot of money; physical space; hardened facilities; utilities such as electricity, water, and gas; redundant high-speed communications lines; and, of course, the personnel to run such an operation. The resources you would expend could be astronomical, but a cost-effective alternative is simply to pay someone a tidy sum every month to perform the service for you.
![]()
In general, an organization will contract with a third party to reduce costs and increase efficiency.
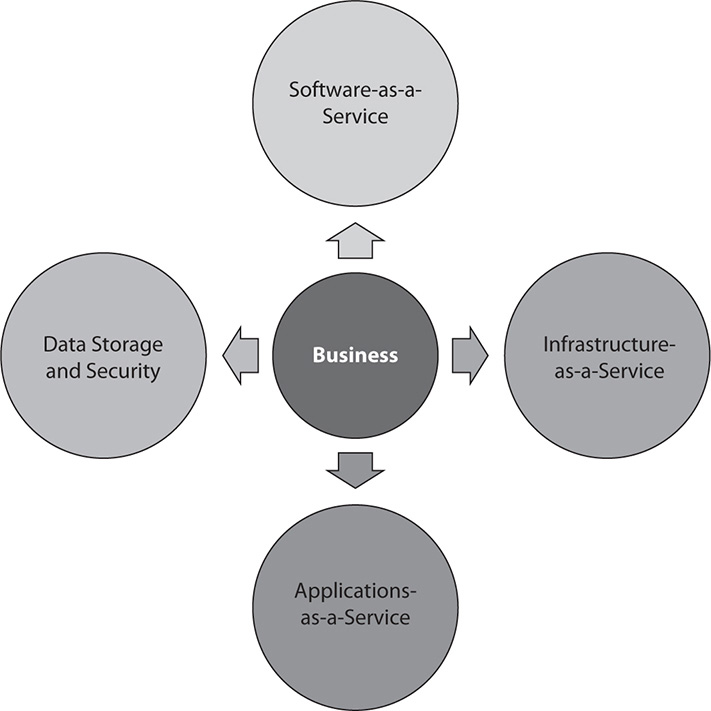
In addition to cost, efficiency can be a deciding factor in the decision to outsource services. Since many of these third-party providers already have the infrastructure in place, their operations are probably much more efficient because that is the core of their business. Consider, in contrast, a company whose business may or may not be focused in that market space, and suddenly providing a data center falls into the overhead column. In addition, a business that’s engaged in a different market segment won’t necessarily be able to run those services as efficiently as a dedicated third-party provider might. Other reasons for using third party and cloud providers for services may include the size of the business, as well as the lack of trained personnel and other infrastructure needed to provide those services. A small mom-and-pop–type company may do large volumes of business on the Internet but only have 10 or so employees, none of whom are IT personnel. Cloud and third-party providers are perfect for these types of operations. Figure 33-1 shows some examples of outsourcing services to various third-party or cloud providers.
Figure 33-1 Examples of services outsourced to third-party and cloud providers
As mentioned, however, with all the responsibility you might give third-party providers, the accountability usually stays with you and your organization. That makes information security a much more important service within your company, so that you can make sure your services and data and infrastructure are protected when in the hands of third-party providers. Security from this perspective also involves data privacy, availability, legal liability, and several other facets that you may not usually see in your day-to-day job as a security professional when dealing with services that are insourced in the organization. The next several sections cover some issues involved with transferring responsibility for information processing and storage services to external entities, as well as ways you can ensure that your security needs are met by these same external providers.
Integrating Systems and Data with Third Parties
Whenever you integrate your systems and data with a third-party provider, you’ll need to consider your organization’s business processes, systems interoperability and integration, and definitely data security. Integration should involve both parties establishing agreements on data exchange, access control, availability to authorized personnel within both parties, and data integrity. You also need to consider some processes, whether this third party is a business partner, a service provider, a subcontractor, a consultant, or whatever. Let’s take a look at a couple of key areas you’ll need to be aware of for the exam, as well as your day-to-day interactions with third-party providers.
On-Boarding/Off-Boarding Business Partners
It’s considered good practice to create a solid process for onboarding new third parties and off-boarding third parties you are no longer using. This is particularly important for onboarding a new third party. When you create a business agreement with a third party, you have to consider and agree on some negotiable things, such as response times to incidents, types of backups, time to recover data in the event it is corrupted or lost, and so on. Many of these things will be technical in nature, such as encryption strengths and the like, but a lot of it will be both policy- and process-oriented. For example, with a strategic business partner, you might need to agree on authentication methods to access shared data. Your business partner might use only usernames and passwords for authentication within their own network, but your policy might require two-factor authentication to sensitive data. You may have to set up a type of “bridge” network authentication system that allows for both types of authentication if you can’t settle on one or the other. Access control policies are another issue. Your policies may be less restrictive than those of your partners, and you may need to negotiate with the partner to determine how restrictive access control will be on shared data.
In addition to policy issues, procedural issues must be worked out. These may be different based on whether the third party is a business partner or simply a service provider that has its own procedures regarding data backups, recovery, incident response, and so on. Some things may be negotiable based upon the type of service or contract agreement you have with a third party; some may not be negotiable because of legal requirements or other types of governance. Ultimately, you have to negotiate security methods and controls that will protect your interests when sharing data with third parties, whether it’s a business partner or a third-party service provider.
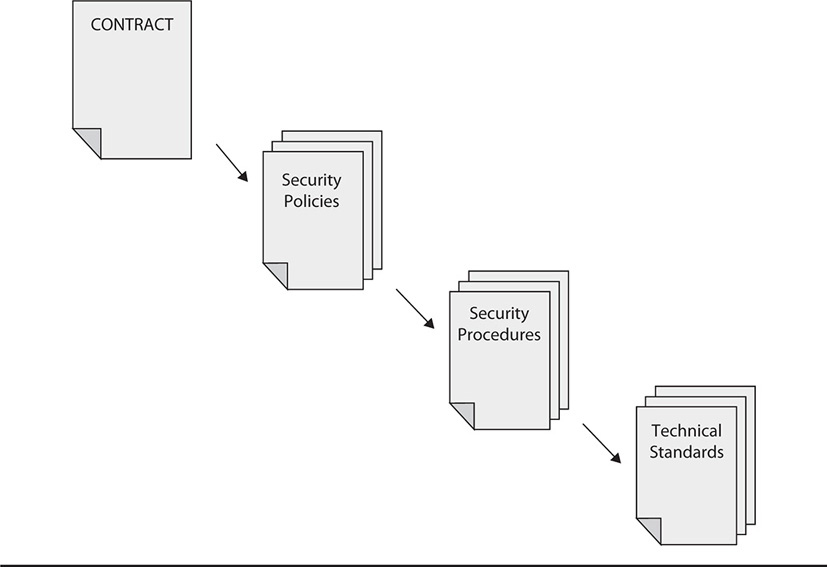
In addition to establishing policies and procedures, technical issues have to be resolved. There may be issues in the form of data format, encryption standards, applications used to access data, and even file system types that offer different security mechanisms. You may find that your organization has to buy additional applications or equipment to make use of third-party services or access data that you share with a business partner. Fortunately, with cloud computing models becoming fairly common in business, this is usually kept to a minimum, and data can be accessed in its native format through different web-based interfaces and utilities. Securing these connections and interfaces from a technical perspective is yet another issue that must be negotiated and agreed upon when onboarding a third party into your business environment. Figure 33-2 illustrates the way policies, procedures, and technical standards are included in contract agreements.
Figure 33-2 Including security policies, procedures, and technical standards in the contract
Offboarding terminated third parties isn’t as complex as onboarding, but it certainly has considerable issues, such as data retention and ownership, disposal of proprietary and sensitive data, lingering liability against claims that happen after the business agreement is terminated, and so on. You’ll also have to look at decommissioning equipment and active connections to the third parties involved. This can mean terminating physical circuits from a telecommunications provider, reconfiguring firewall rules to eliminate open ports and protocols used during the agreement, changing passwords on shared resources, and reissuing new encryption keys to some users and revoking other keys. Terminating the relationship of the third party should also involve auditing data use in resolving any outstanding security issues you may have experienced during the contract period.
![]()
The Security+ exam wants you to know the issues involved with onboarding and offboarding third parties. Take time to recognize these issues described here!
Social Media Networks and Applications
Third-party service providers may be peripherally involved in social media networks or applications that are owned and used by businesses, but typically these items are more of a concern in strategic business partnerships where shared data, as well as shared marketing of services and products, may happen. Both organizations should have a solid social media policy, but if not, then at least one should be developed when two businesses enter into a contractual agreement. The agreement may specify who has administrative access to social media networks shared by both parties, who is allowed to update publicly available information on social media, and who is able to take down, delete, or change information. Both parties should also agree on the types of information they will mutually allow to be placed on social media, possibly excluding certain types of information that should include sensitive or proprietary data, privacy data, and so on. They also may agree on the acceptable behaviors of both parties and their employees with regard to social media posts.
Third-Party Security Considerations
It’s said that the devil is in the details; this is definitely true when it comes to security considerations that involve multiple parties. When you negotiate a contract with a third-party provider or business partner, you must ensure that several considerations are specified in your business agreements. You should definitely have representatives from your security, privacy, and legal departments review any business agreements with third parties to ensure that certain security-related stipulations are included in the agreements and the day-to-day business transactions with outside entities. A few of these security considerations are discussed next.
Security Policy and Procedures
Although your organization should have its own security policies, procedures, and processes, third-party organizations usually have their own as well. Sometimes these policies and procedures conflict between the parties and have to be negotiated, resolving any differences between them, in advance. In some cases, contract agreements may specify security policies and procedures that both parties must follow regarding shared data or contracted services; this is true whether the third party is a service provider, business associate, subcontractor, or whatever other relationship your company has with it. For the most part, your organization shouldn’t accept a third party’s security policies if they cannot offer the level of protection required for your company’s data, since the data is just as critical and sensitive whether it’s retained inside the organization or placed in the hands of an external entity. Security policies and procedures that are agreed upon in advance ensure that the external entities protect your organization’s data to the level your organization would protect the data internally.
Privacy Considerations
Privacy is a serious consideration when exchanging data with any third party. If you are contracting services with a third party, make sure that data privacy is agreed upon prior to entering into any business agreements. Privacy considerations include employee data privacy; privacy related to the type of data itself, such as financial data, personally identifiable information (PII), and protected health information (PHI); and how this data will be treated by the third party. Legal or regulatory governance may provide you some protection, in that the third party has to obey laws with regard to data privacy, but you may find that your company has additional requirements that need to be met by the third party. It’s also possible that the agreement could be too restrictive in favor of the service provider, and your company requires more flexible terms to ensure data privacy to your standards. In any case, ensure that how private data is handled, including how it is stored, processed, accessed, and especially transmitted to other third parties, is specified in any agreements made between your organization and the third-party provider or business associate. For example, the Health Insurance Portability and Accountability Act (HIPAA) security regulations require that any third-party providers (referred to as a “business associate” in HIPAA parlance) that could possibly have access to protected health information be subjected to strict access control and handling requirements for that type of data.
Risk Awareness
Another hot button with security in terms of third parties is risk awareness and management. Many organizations require that third-party providers or business associates have an established risk management program that includes threat and vulnerability assessments, risk mitigation strategies, and so on. This helps an organization be assured that the third party has performed its due care and diligence in assessing and managing risk and is therefore able to reduce and mitigate it. The third party may be required to provide proof in the form of a risk assessment or risk analysis report that satisfies this requirement.
Unauthorized Data Sharing
Security policy set forth in third-party agreements should cover unauthorized data sharing and access control. In addition to setting forth minimum requirements for access control, which include administrative, technical, and operational controls, the agreement should set forth mechanisms that an organization must use in order to share data with other authorized parties, as well as conditions under which the third party must comply with the law in sharing data with government and law enforcement agencies. The agreement should also cover how the organizations will respond in the event of a data breach or unauthorized access.
Data Ownership
Organizations must define the types of data to which they claim ownership initially, and how they would classify that data in terms of its sensitivity and protection requirements. The organizations must also determine how they will decide on ownership of data that is created during the contract term and who will control it. Some third parties that process data for an organization specifically agree that any data created during the contract term still belongs to the originating organization, but other third-party providers may maintain that they have legal ownership over any data that is created on their systems, based upon their unique processes or proprietary methods. This issue must be resolved prior to engaging in business with a third party. Issues with data ownership can lead to disputes over copyrights and patents, as well as unauthorized disclosure issues between two parties that both claim to own the data produced.
Data Backups
Since availability is a significant issue with regard to security, it must be included in any third-party agreements the business enters into. With third-party service providers, specific levels of availability should be guaranteed to the business, including backup and restore strategies, transactional journaling, server and infrastructure uptime, and so on. Some third-party service providers are specifically in the business of availability and provide services directly relating to storing organizational data offsite and guaranteeing almost instantaneous availability of the data to a business in the event of serious incidents or disasters. Even if the service you’re contracting for with the third party isn’t specific to data backup and availability, service providers should provide some assurance that the data will be available whenever you need it. In some cases, your business may want to have the third-party specify exactly what methods and equipment are used to ensure availability, and how the third party will support quick and efficient access to the business’s data. Usually, data availability and other types of services are specified at predetermined levels and included in service level agreements as well as other types of contract documents, which are discussed in the next sections.
Third-Party Agreements
When your business enters into any type of business partnership or agreement with a third-party business partner or service provider, the agreements and contract documents that are created serve to protect both organizations from a legal perspective, as well as establish the terms of the business relationship. You’ll need to know several different types of documents for the exam, which cover various aspects of data protection, interoperability, interconnection, and so on. They basically define the interoperability relationship between the two (and sometimes more) parties. Obviously, these types of agreements will be negotiated by the business contracting and legal personnel in each organization, but advice and input should also come from other affected functions within the businesses, such as security, privacy, IT support, and so on. Let’s take a look at a few of these types of business agreements.
Service Level Agreement (SLA)
A service level agreement (SLA) essentially establishes the level of data availability and other types of services that a third-party provider will guarantee to the business. The provider guarantees that data or other types of outsourced services will be up and running and usable by the organization, either for a certain percentage of time or to a certain level of standards. If the provider is storing or processing data for the organization, the SLA may state that the data will be available in a particular form, through a particular application or system, in a specified format, and to authorize users within the business. If the provider is offering a service such as outsourced network or web-based transactional services, for example, the SLA states that the services will be available for authorized users whenever they need them. The SLA may describe technologies and redundant systems used to ensure availability for customer’s data and services, as well as specify what actions the provider will take in the event of incidents that may affect availability of services, and how long they have to restore full access for the business.
Business Partner Agreement (BPA)
The business partner agreement (BPA) specifies what type of relationships the different parties will have, usually from a legal perspective. An entirely separate company may be established for the business venture, combining elements of both individual businesses; this is usually for long-term or large-scale ventures. Usually, however, legal agreements dictate the type of partnerships or customer-provider relationships.
The three most common types of business partnerships are general partnerships, limited partnerships, and joint ventures. These types of partnerships are usually distinguished by scope, term length, and level of data access provided to each party in the agreement. A general partnership usually consists of an indefinite or longer term length and typically provides for equal sharing of business revenue between the parties. It also involves the least restrictive level of data access; all parties typically share equally in data access as well as decision-making authority. A limited partnership is characterized by a lesser or defined length of time and involves less data sharing and more focused or limited interaction between the parties. A joint venture involves a more defined, short-term timeframe, with data sharing limited to the minimum necessary to carry out the business venture. Interactions in a joint venture between the parties are limited to those required for specific business transactions. Of course, these are only guidelines; the specifics of business partnerships will be better defined in the agreements the parties create with each other and should be based upon their own unique business needs and requirements.
Memorandum of Understanding (MOU)
A memorandum of understanding (MOU), sometimes called a memorandum of agreement, is a document often used within a large business or government agency that establishes an agreement between two independently managed parties that may be working together on a project or business venture. In this type of agreement, a contract isn’t necessarily in place (nor required), simply because both parties work for the same overall organization. An MOU is established so that each party will agree to provide certain services or functions to the other party. Since both parties may work for the same higher level organization, money doesn’t necessarily change hands, but it could in a fee-for-service model where funds are transferred from one party’s account to another’s within the same company, for example. An example of this type of agreement would be if a division of the company provides data center services to other divisions of the same company; this memorandum of understanding would outline its responsibilities and guaranteed levels of services to another division that uses it for data storage and protection. You’ll also see this type of agreement between different government agencies; a military base, for example, may agree to provide network infrastructure services for another nonmilitary government agency that resides on the base (think of NASA, for example, which may have divisions housed on various US Army and US Air Force bases throughout the world).
You could also see a memorandum of understanding between two businesses, of course, as part of a larger contract agreement; this may simply serve to define functions and interactions between two lower level functions or departments located in each organization that weren’t specified in the overall contract. The MOU may be agreed to and signed off by the middle level managers of each department.
Interconnection Service Agreement (ISA)
This type of agreement is usually more technical in nature and may detail how two independently owned and managed network infrastructures are connected to each other. The businesses that own each network may require interconnections to share and access each other’s data, and may use this type of agreement to specify the technical details needed for the connections. The agreement may specify security requirements, such as firewall and virtual private network (VPN) use, encryption levels and methods, authentication types, allowed protocols, and so forth. This may be an attachment or amendment to the overall contract between parties. In Figure 33-3, you can see a summary of the different types of agreements you may encounter when working with third parties.
Figure 33-3 Types of agreements with third parties
Verifying Compliance and Performance to Standards and Agreements
Any agreement between business parties and providers should specify how compliance and performance standards are verified by each party when required. You may specify certain common standards and performance levels that each party has to meet, as well as legal or governance compliance. Audits or periodic inspections may be used by either party to verify the other party’s compliance and performance. Access control checks, data integrity checks, and review of availability mechanisms (such as backup and restore devices and processes) may be addressed in this part of the agreement. Performance and security metrics such as throughput, availability times, backup frequency, limits on data permissions, and so forth may be specified and used to measure whether or not each organization is adhering to compliance and performance standards. Details regarding noncompliance and failure to perform up to standards should also be addressed in such agreements, to give each party an avenue of redress against the other.
Module 33 Questions and Answers
Questions
1. Which of the following is not an example of outsourcing services to a third party?
A. Data storage
B. Applications
C. Network services
D. Software use
2. Which of the following must be included in contract agreements with third parties? (Choose all that apply.)
A. Technical interface specifications
B. Security policies
C. Security procedures
D. Proprietary data
3. Which of the following issues will need to be resolved from a technical security perspective when exchanging data with a business partner?
A. Data types
B. Authentication
C. Data formats
D. Bandwidth
4. Which of the following must be resolved when offboarding a third-party organization after a contract has ended?
A. Encryption
B. Authentication
C. Data ownership
D. Data retention
5. You are providing input for a contract agreement with a business partner. Both organizations have public social media sites, and your organization wants to be able to exclusively update the joint social media site that will be created when the partnership begins. How should this issue be resolved? (Choose two.)
A. Develop a joint social media policy.
B. Allow only your organization to have control of social media sites.
C. Restrict update permissions only to certain personnel in both organizations.
D. Allow any member from each organization to post updates to the social media site.
6. Which of the following represents a security-related concern that must be discussed in any agreement with a third party?
A. Product marketing
B. Data format
C. Connectivity
D. Privacy
7. Which of the following would a third party need to have in place to demonstrate due diligence with regard to data protection?
A. Risk management program
B. Legal compliance policies
C. Authentication technologies
D. Backup procedures
8. Which of the following types of legal agreements describes the levels of availability that a third-party cloud provider must sustain?
A. BPA
B. MOU
C. SLA
D. ISA
9. Which of the following types of agreements is often used internally between government agencies to define functions or services each will provide to the other?
A. Business partner agreement
B. Interconnection service agreement
C. Service level agreement
D. Memorandum of understanding
10. Which of the following specifically defines the technical details for interfacing systems and networks together to share data between two businesses?
A. Memorandum of understanding
B. Interconnection service agreement
C. Service level agreement
D. Business partner agreement
Answers
1. D. Software use is not an example of a service that would be outsourced to a third party.
2. A, B, C. All of these should be included in contract agreements with third parties.
3. B. Authentication must be considered before exchanging data with a business partner.
4. D. Data retention is a concern between organizations when terminating a business agreement.
5. A, C. All parties to the agreement must develop a joint social media policy and then restrict update permissions only to certain personnel in both organizations.
6. D. Privacy is a serious consideration with respect to protecting certain types of data that may be shared between organizations.
7. A. An overall risk management program demonstrates due diligence by a third party with regard to data protection.
8. C. An SLA describes the levels of availability that a third-party cloud provider must sustain.
9. D. A memorandum of understanding (MOU) is often used internally between government agencies to define functions or services they will provide to each other.
10. B. An interconnection service agreement (ISA) specifically defines the technical details for interfacing systems and networks together to share data between two businesses.