MODULE 21
Network Threats
We’ve already discussed host-based threats, and although many threats exploit vulnerabilities and issues on the host, most host threats actually come from the network in the form of network attacks or malware that is sent through the network to infect a host through phishing e-mails and so on. So it makes sense that we should talk about network-based threats specifically, since they are often used to carry out attacks on hosts. In this module, we’ll look at some of the basic large-scale network and denial-of-service attacks used on hosts and networks.
Network Attacks
A defining characteristic of a network attack is that it comes in the form of specially crafted network communications traffic. This could involve large volumes of traffic, specially formed packets, or even attacks using particular characteristics of network communications in malicious ways. Another characteristic of network attacks is that they’re often used as initial steps in carrying out larger attacks. So a network-based attack might be used to gain access to a host, send malware to a system, or cause a host to become unstable so other attacks could be conducted against it. In this section, we’ll look at the various basic types of attacks that can be conducted over the network.
Types of Attacks
We’ve already discussed different types of attacks on hosts; most of these relate to unauthorized access of data, malware, buffer overflow attacks, execution of arbitrary code, privilege escalation, and so on. Many of these host attacks are carried out through networks. Several network-based attacks are used to weaken host systems so that more severe attacks can be launched later. In this section, we’ll discuss some of those network-based attacks, which can be used to disrupt or gain access to hosts or to steal or alter data during transmission between hosts. Some network attacks are also designed to deny access to systems and data from others. Understand that many other attack methods are being used out there, including some that are incredibly sophisticated.
Spoofing
In a spoofing attack, a characteristic of a user or host is impersonated. For a user, spoofing usually entails impersonating the user through the use of their credentials or by spoofing their identity through e-mail, for example. For a host, spoofing could mean impersonating the host’s IP address, MAC address, or host name. The purpose of spoofing is to fool other hosts into believing that they are communicating with a known or authorized host. Spoofing is often used as a first step in preparation for carrying out other attacks later on. Spoofing is not as difficult as you might think; this attack can be executed in different ways, depending upon the end goal and how other hosts will be fooled. For example, to spoof a MAC address, an attacker could use a technique called ARP poisoning to make false updates to a host’s ARP cache, causing it to communicate by MAC address to the attacker instead of the actual host. For IP address spoofing, an attacker could simply statically change an IP address on his host to that of another, but frequently this will cause errors on the network and it won’t be successful. More often than not, usually a much more sophisticated method is used. This involves simply using a program to change the source IP address in the IP packet header as it is transmitted out into the network. This actually isn’t difficult to do, but it does require software such as hping3 (for Linux) or something like ColaSoft Packet Builder for Windows, for example. With these two pieces of software (and many others like them), you can easily spoof MAC or IP addresses. In fact, Figure 21-1 shows a screenshot from hping, showing how easy it is to spoof an IP address.
Figure 21-1 Spoofing an IP address using hping3
Man-in-the-middle
In a man-in-the-middle (MITM) attack, two hosts are communicating and an attacker breaks into this communication stream, inserting itself into it. Once the attacker breaks in, a few different things could happen. He could simply eavesdrop on the connection, intercepting data without modifying it. Or he may decide to take an active part in the network communication, which requires him to spoof both ends of the communication to the other host. So if two hosts, A and B, are communicating, an attacker would insert himself into the communication, and both hosts would believe that they were communicating with the other, when actually both would be communicating with the attacker. The attacker could freely intercept data, change it, and retransmit it to the other host. Figure 21-2 shows how an MITM attack works.
Figure 21-2 How a MITM attack works
An attacker can pull off an MITM attack in several different ways. He might be able to decrypt encrypted communications between hosts if he has access to the session key or is able to exploit a weak cryptographic algorithm used for encrypted communications. He could also use some type of session hijacking technique, such as cookie hijacking, to gain the session key used for the encrypted communications session. Other techniques used in MITM attacks include TCP sequence guessing and source routing. TCP sequence guessing involves an attacker attempting to predict the sequence numbers of TCP segments passed between two hosts; if he guesses the numbers correctly, he can inject false, specially crafted segments into the conversation. Although the traffic is coming from the attacker, both sender and receiver victims believe they are communicating with each other. Source routing is used to trick victims into routing their traffic through a network device of the attacker’s choosing, so the traffic can be intercepted and possibly read on its way to the intended receiver. Source routing also allows an attacker to spoof an IP address when sending packets and still receive the response, even though they have used a fake IP address.
Replay
A replay attack involves intercepting a user’s credentials as they are being transmitted over the network. An attacker would intercept these credentials and attempt to reuse them by retransmitting them to the authentication server or target host in an effort to reauthenticate as that user. An attacker can use several methods to conduct a replay attack; all can be prevented by the use of strong encryption algorithms with strong keys, as well as sequence numbers and timestamping. Timestamping in particular is used to thwart replay attacks, because the credentials the attacker intercepts are good for only a finite period of time, and then they expire. This causes the user to have to renew their credentials and reauthenticate, so any credentials that the attacker intercepts are no good after a specific amount of time. Kerberos is one such protocol that is used to thwart replay attacks through its use of timestamping and session authentication tickets.
DoS
A denial-of-service (DoS) attack is used to deny legitimate users access to networks, systems, data, and other resources. Sometimes a DoS attack will be a last-ditch effort by an attacker who can’t otherwise infiltrate a system or network to steal data. However, more often these days, a DoS attack is the end goal and is carried out for purposes of revenge, to cause monetary loss to the victim or to send an activist message.
DoS attacks are usually carried out through network-based attacks, although increasingly, malware is used to conduct these types of attacks. From a network perspective, a DoS attack can involve an attacker sending large volumes of specially constructed (malformed) network traffic to a host with a TCP/IP stack that can’t handle it, or even sending pieces of traffic that are too large for the receiving host’s memory buffers or network card to handle. In some cases, this might be due to a flaw in the operating system, or it could simply be that the host doesn’t have enough physical resources (RAM, CPU power, robust network card, and so on) to handle the traffic.
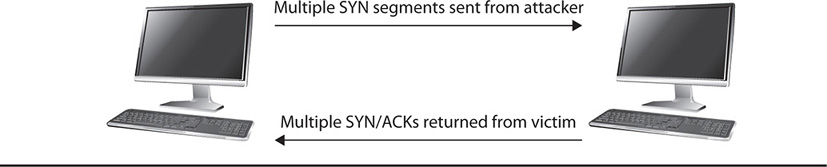
Examples of harmful network traffic could be oversized Internet Control Message Protocol (ICMP) packets, massive volumes of ICMP traffic, or even incomplete communications sessions. For example, in the three-way handshake that TCP is required to establish when communicating with a host, both hosts expect a certain sequence of segments with particular flags set. An attacker can begin the TCP three-way handshake, sending a segment with the SYN flag set, which causes the receiving host to send a segment back with both the SYN and ACK flags set. The receiving host would normally then expect another segment from the sending host with the ACK flag set, completing the three-way handshake and synchronizing the communications session. However, an attacker would never complete the three-way handshake and would never send the final ACK segment back. Instead, he would continually send SYN requests to the victim. This might cause the victim host to try to respond to the synchronization requests over and over, but never receive the final ACK segments back. The result of this is that the receiving host would continually be sending large volumes of traffic out, eventually using up all of its RAM, CPU, and network bandwidth. Figure 21-3 shows how this particular type of attack, called a SYN flood, works.
Figure 21-3 A SYN flood attack
DDoS
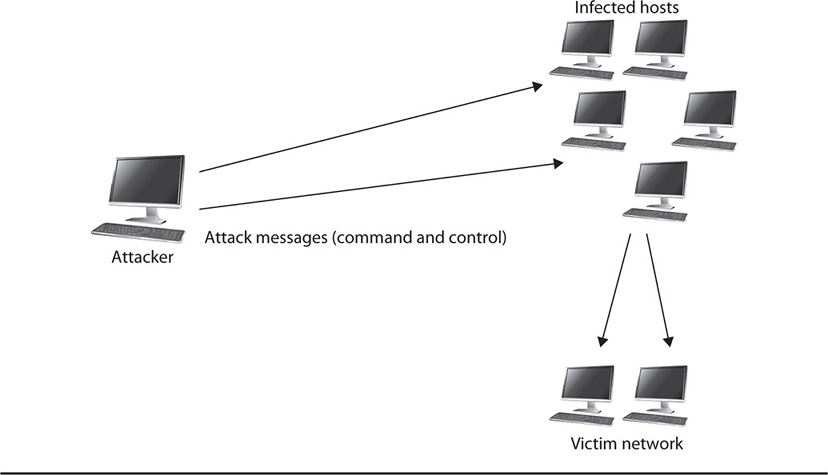
A DoS attack normally targets a single host and comes from a single host. A distributed denial-of-service attack (DDoS), however, uses multiple hosts to attack a target. In addition to the network-based communications attacks we discussed previously, a DDoS attack makes heavy use of malware. In the pre-attack stage, an attacker may use other attacks or means to get malware installed on many different victim computers. This malware has a very specialized purpose: it’s used to control the victim computers remotely during an attack, causing them to launch attacks on other computers. Malware that infects the victim computers is called a bot; when all of these victim computers are tied together and controlled by a single attacker, this is referred to as a botnet. Sometimes the individual victim computers conducting the attack are called zombies.
The purpose of a DDoS attack is to bring massive chaos to the target network. A botnet can quickly take down an entire network belonging to an organization, including all its hosts. Additionally, some botnet attacks are designed to further infect the victim computers they are attacking, adding them to the botnet as well and increasing the attack forces. Figure 21-4 illustrates how a botnet works.
Figure 21-4 A botnet in action
A smurf attack is yet another example of a DDoS attack. It uses ICMP, which you know from previous discussions is a maintenance protocol that works at the Network layer of the OSI model (or the Internet layer of the TCP/IP protocol stack). ICMP can be used to conduct a variety of attacks, and in a smurf attack, the attacker will send a large number of ICMP packets through the ping utility, with a spoofed source IP address (the victim’s IP address), but destined to the network’s broadcast address. Naturally, when any computer on the network receives something intended for the broadcast address, it’s going to reply to that traffic. In this case, the hosts on the network will all receive a ping packet, and they will all reply to it. However, they’re all going to reply to the victim’s IP address, since it’s the source IP address in the ping packet. This has the effect of sending a massive amount of ping replies to the victim from every host on the network. In large networks, this continual barrage of ICMP traffic targeted at the host will not only bring the host down eventually, it will also create so much noise that legitimate traffic won’t be able to traverse the network. This type of attack can also be conducted using utilities such as hping3 and several others.
To prevent this type of attack, the network administrator should filter out ICMP traffic at the border security device. In some operating systems, there are configuration settings that prevent this type of attack from occurring, by preventing the host from responding to ICMP broadcasts. It’s also common practice to deny ICMP traffic on host-based firewalls if they are used on the network. Figure 21-5 illustrates how a smurf attack is conducted.
Figure 21-5 A smurf attack
Module 21 Questions and Answers
Questions
1. Which one of the following terms is used for impersonating a host or user?
A. Smurf attack
B. Man-in-the-middle
C. Session hijacking
D. Spoofing
2. All of the following are characteristics of a man-in-the-middle (MITM) attack, except:
A. Intercepting data
B. Altering and retransmitting data
C. Spoofing both sides of the communications session
D. Flooding the network with ICMP packets
3. Intercepting a user’s credentials and retransmitting them in the hopes of authenticating as that user is known as a __________ attack.
A. session hijacking
B. replay
C. man-in-the-middle
D. spoofing
4. Which of the following can be used to conduct a denial-of-service attack? (Choose all that apply.)
A. Specially crafted traffic
B. Malware
C. Large amounts of traffic
D. Man-in-the middle attacks
5. You have received reports that a user’s host is very sluggish and unresponsive. After troubleshooting other items, you decide to use a sniffer to examine the network traffic coming into the host. You see that large amounts of ICMP traffic, in the form of ping replies, are being sent to the host. The host is having trouble processing all of this traffic, causing it to slow down. Which of the following is the most likely explanation for this?
A. Faulty network card
B. Man-in-the-middle attack
C. Smurf attack
D. SYN flood
6. In a SYN flood attack, which of the following is a receiving host expecting back as a reply to complete the TCP three-way handshake?
A. Repeated SYN segments
B. A SYN/ACK segment
C. A SYN segment
D. An ACK segment
7. Which of the following would be considered a distributed denial-of-service attack?
A. An attacker uses her own machine to attack another machine.
B. An attacker uses a network of 20 malware-infected hosts to attack a web server.
C. An attacker uses a SYN flood attack against a target’s external router.
D. An attacker uses a MITM attack against an unsuspecting rival hacker.
8. Which of the following terms describes an infected host that joins a malicious network used to conduct a massive DDoS attack against another network?
A. Zombie
B. MITM
C. Drone
D. Trojan
9. Which of the following network attacks is used to further conduct a smurf attack on a victim host?
A. SYN flood
B. ARP poisoning
C. IP spoofing
D. MAC spoofing
10. All of the following actions could be used to protect against ICMP-based attacks, except:
A. Denying ICMP inbound at a border security device
B. Allowing ICMP inbound through a host-based firewall
C. Configuring the host OS to disregard ICMP packets
D. Configuring all hosts to ignore broadcast ICMP
Answers
1. D. A spoofing attack involves impersonating a user’s identity or the IP address, MAC address, or host name of a computer.
2. D. Flooding the network with ICMP packets is not a typical characteristic of a MITM attack.
3. B. A replay attack involves intercepting a user’s credentials and retransmitting them in the hopes of authenticating as that user.
4. A, B, C. All of these can be used to conduct DoS attacks. A man-in-the-middle attack is not used to conduct a DoS attack; it is used to intercept and/or modify data.
5. C. A smurf attack would cause large amounts of ICMP traffic to be directed at a host.
6. D. A receiving host expects to receive an ACK segment as a reply to complete the TCP three-way handshake, but in a SYN flood, it receives continuous SYN segments instead.
7. B. An attacker using a network of 20 malware-infected hosts to attack a web server qualifies as a distributed denial-of-service attack, since it involves using many hosts against the target.
8. A. A zombie is an infected host that joins a malicious network used to conduct a massive DDoS attack against another network.
9. C. IP spoofing is used to further conduct a smurf attack on a victim host.
10. B. Allowing ICMP inbound through a host-based firewall will not prevent an ICMP attack.