MODULE 37
Security Training
The previous module discussed social engineering and how people can be a significant security weakness in the entire system, network, and organization. This module will look at how you can minimize the effects of human security risks. Because there’s no patch for being human, and you can’t really create a new firewall rule or develop a new method of encryption to mitigate human security risks, the best way to mitigate this is by providing adequate security training and education so that users know what the stakes are and how they can do their part to protect data and systems.
Security Awareness and Training
Unfortunately, in this world of rapidly shrinking resources, when managers and executives look at cutting budgets, training is often one of the first things on the chopping block. It’s unfortunate because the temptation is to buy more technical stuff (such as firewalls, VPN concentrators, and so on) to secure the organization. Many managers think that telling people what they are, and are not, supposed to do and having them sign a form that says they understand their security roles and responsibilities will ensure that employees will not contribute to organizational security risks. However, this isn’t the case, for a few reasons.
Although tools such as firewalls and VPN concentrators can be configured to do exactly what you want, all the time, people are dynamic. You can’t simply “configure” them by training them once and then expect that they will consistently follow the rules. A simple one-time training session on security and data protection won’t work. Effective training and education requires repetition, reinforcement, and support. It should be based upon the security goals of the organization and should focus on the real-world threats that target people and how to counter those threats.
In the next few sections, we’ll talk about effective security training and awareness. We’ll look at the different types of training that can be used, and the particular areas of attention that you as a security professional, as well as your users, should focus on during security awareness and training efforts.
Types of Training
Training comes in all shapes and sizes. An effective training program doesn’t comprise a one-page briefing that users quickly review and sign. Because people learn and process information in different ways, an effective training program should use a wide variety of methods and tools to educate people on security responsibilities and threats. A good training program might make use of computer-based training modules, one-on-one briefings, classroom sessions, video presentations, and other methods. The organization should use whatever type of training tools work the best for the entire user population and not focus on just one method.
In addition to the methods used to train people, the type of training can also make a difference. Not every user needs to be trained at the same level and on the same information. For example, all employees should be trained on general security risks and their roles and responsibilities in terms of the general use of computing assets, data, and systems in the organization. Other categories of users, such as IT professionals, security auditors, or security managers, should receive this type of training, plus more, including training that focuses on what security roles they play in their particular assignments.
Security Policy and Procedures
Because security policies should apply to all personnel in the organization, it makes sense that all personnel should receive training on policies. Everyone in the organization, from the low-level user in the accounting department, to the most senior executive, should receive training on the organization’s security policies. Remember that security policies are directive in nature and tell people what they must do, based upon governance imposed on or by the organization in the form of laws, regulations, and other types of rules. Examples of such security policies include acceptable use of computing resources, equipment use, data protection, data sensitivity, and access control, to name a few.
Users must also be trained on procedures that go along with these policies. For example, in addition to a policy that restricts users from downloading certain types of files or introducing potentially harmful content into the network from personally owned devices, procedures should be developed to help enforce these policies. In this case, users can be trained on how to recognize and report suspected malware, as well as what type of actions they should and should not take when they receive e-mails or files that may contain harmful software. Procedures should exist for all the organization’s general security policies, and all users should be trained on those procedures.
This type of security training should be repeated periodically so that users are able to internalize it and make it part of their daily routines. It’s also useful to conduct such training on a recurring basis, since threats and environments are constantly emerging and changing. Users need to be aware of these constantly changing threats. In addition to receiving periodic training, users should be exposed to security information regarding their responsibilities and the harm that various attacks can pose to organizational systems, through the use of security e-mails, bulletin board postings, and so forth. All of these methods can be used to reinforce security awareness on a fairly routine basis.
Role-based Training
Role-based training is also important and is directed toward particular security roles. For example, system administrators are often trained on the technical aspects of performing their jobs and managing their systems. They should also receive role-based training that is specific to their security functions as system administrators, tailored to the types of systems they work on.
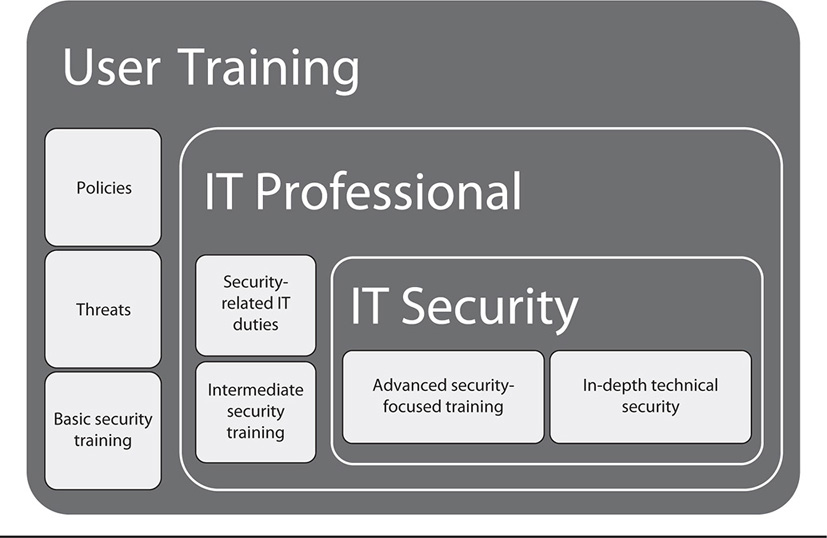
Likewise, security auditors and those in other security roles should receive training consistent with their daily jobs and their levels of responsibility in keeping data and systems secure. This type of training should also be periodic and recurring, and it should be documented. Although this type of training is definitely more in-depth and role-specific than regular user security training, it’s just as critical to maintaining security-minded professionals in the organization. Figure 37-1 shows an example of how different levels of security-related training may apply to different categories of employees in the organization.
Figure 37-1 Example training levels for users, IT workers, and IT security personnel
Key Security Areas
You must make sure that users are trained on several key security areas throughout the length of their employment, including data protection, media use, use of the Internet, properly using security mechanisms, and so forth. Most of these are common areas with which all users have difficulty, but these areas can cause the greatest number of security problems in an organization. In the next several sections we’ll look at some of these key security areas, as well as what you need to impress upon users to help them fully understand and follow through with their roles and responsibilities.
Personally Identifiable Information
Personally identifiable information, or PII, is a fundamental type of data that both individuals and organizations use on a daily basis. PII includes information about individuals, such as name, date of birth, Social Security number, driver’s license number, mailing or physical address, credit card numbers, and other identifying information concerning a person. The organization uses similar information from individuals to conduct its daily business with regard to employment, human resources records, financial records, and so on. Protecting this type of information is the responsibility of both the individual and the organization, because if an attacker compromises this information, both the individual and organization could be seriously affected. Unauthorized disclosure of PII could result in various types of attacks, including identity theft, social engineering attacks, impersonation, and more.
Normally, the PII used within an organization is protected by security mechanisms within the organization’s infrastructure. PII that individuals control is up to them to protect using methods such as device encryption, personal firewalls, and, of course, common sense, to name a few.
Information Classification
All data and information are not created and used equally in an organization. For example, data exchanged via e-mail concerning the next office party probably isn’t as important to protect as data concerning a secret manufacturing process that will put the company ahead of the competition in the marketplace. So how do individuals and organizations decide what type of data is more important and what type of data gets more protection? The answer is policy. The organization has to develop a data classification policy that spells out the types of data created and used in the organization and how it is categorized in terms of sensitivity and protection. This policy instructs users on how to treat certain types of data they create and use with regard to the amount of protection that’s required, including access control, storage, processing, and even transmitting to others. To do this, the policy will use different data classifications, decided upon by the organization, to categorize data.
The organization will determine the importance of data in terms of criticality to its business operations, its legal obligations, and other factors. For example, data could be classified in terms of high, medium, and low criticality, which would tell users that data determined to be highly critical should be protected using very restrictive access controls and measures that may require serious resources, such as secure areas, safes, access cards, restrictive permissions, and so on. Data categorized as medium or low criticality would not require as much protection and may use less restrictive controls. Normally, an organization will consider categorizing critical data in terms of how sensitive it is and how much harm could come to the organization if that data were disclosed to unauthorized persons.
Other examples of data classifications could include company confidential (which may relate to business processes or operations), private (relating to regulatory controlled data such as PII and HIPAA information), and public (information might be freely available to persons outside the company on a public web site, for example). Other classifications of information could include sensitive or proprietary. In addition to classification use within a private or commercial organization, different levels of data sensitivity are defined by the US government, such as Top Secret, Secret, and Confidential. These data classifications are based upon the level of damage that could occur (ranging from serious to exceptionally grave) if information in these categories were disclosed to unauthorized entities.
The categorizations of data criticality and sensitivity should be defined in policy and should be used to determine how different types of data are handled throughout the data lifecycle, including creation, storage, processing, receipt, and transmission. Although policy defines the types of data and how these types are classified in terms of sensitivity, procedures detail how different types of data are handled and used on an everyday basis.
Data Labeling, Handling, and Disposal
The types of protections provided to highly sensitive or critical data are not the same as those given to unimportant, possibly public data. This is a consideration of risk management at its basic level; we apply mitigations to critical areas that would have greater impacts on the organization if they were threatened or exposed. Based on the policy concerning data classifications, we can apply different levels of protection to different categorizations of data. To do this, we must label data appropriately, based on its level of sensitivity. In other words, data that finds its way into Word documents, e-mails, folders, applications, and so forth, should be labeled based upon its sensitivity. This might mean labeling the document in which it appears, labeling an application or database with sensitivity banners and fields, and so on, so that no matter where the data appears, or how it’s processed, those labels are attached to remind users how to handle it. For example, company proprietary data that describes a manufacturing process may always be marked to indicate that it is proprietary and should be handled carefully, never released to anyone who is not authorized to receive it. This caveat may be present in any word processing document or e-mail that contains the data, included in fields in a database, on physical media that contains the data, and in the metadata on files. Metadata labeling is also useful in automated systems implemented for access control or data loss protection (DLP) programs.
Procedures should detail how to handle each type of data for which the policy provides a classification level. For each data sensitivity category, procedures would tell people how to label, store, process, and send data to third parties; which systems are allowed to contain the data; and so on. Once the procedures are written, data owners (people who are responsible for use and protection of a particular type of data every day) would implement the policy and procedures and set access controls and security mechanisms on their data. Handling policies would also inform users about how to dispose of data that is no longer required by the organization. This might involve securely wiping or destroying drives that contain sensitive data so they can’t be reused, encrypting data and destroying the encryption key, or deleting data if appropriate. Disposal procedures may also dictate that sensitive printed documents must be shredded instead of simply thrown into the dumpster. Data handling procedures, to include sensitive data retention and disposal, must comply with organizational and legal governance, as discussed next.
Compliance with Laws, Best Practices, and Standards
We read stories about data breaches almost daily in the media. These breaches usually involve data that is protected under statute or regulation, such as financial data, PII, and protected health information (PHI). There are a lot of ramifications to these types of data breaches, because the organization responsible for protecting the data can be subject to legal proceedings, to include both civil litigation and criminal charges. Because of that possibility, users have to obey organizational policies, governance, and laws that dictate how different types of sensitive data will be handled and protected.
The organization must comply with laws regarding how to protect certain types of data by establishing policies and procedures that deal with controlling sensitive data. A lack of organizational policies certainly won’t get the user or the organization out of trouble if they mishandle or lose data that’s covered under some sort of legal statute. But establishing these policies and procedures can help mitigate both the risks and the liability that organizations incur when they handle sensitive data. That’s why compliance with legal and corporate governance is so important: it can reduce the risk associated with data loss and unauthorized disclosure and establish that the organization has fulfilled its required responsibilities in protecting such data.
The type of data that an organization handles could come under one or even several laws or statutes, including Gramm-Leach-Bliley (GLB), which dictates how organizations handle financial data, and the Health Insurance Portability and Accountability Act (HIPAA), which covers protected health information. In addition to laws and statutes that cover protection of certain sensitive data, there are also standards that organizations must comply with to be allowed to process certain information. For example, an organization must comply with the Payment Card Industry Data Security Standards (PCI-DSS) to process financial transactions using consumer credit and debit cards. That standard is set forth by different financial institutions and card issuers, in compliance and conjunction with federal laws. Any organization that wants to accept and process these types of transactions must comply with the PCI standard.
Some organizations make complying with an otherwise optional industry best practice or standard mandatory, simply to reinforce the importance of the processes and procedures used in protecting sensitive information. Once an organization makes compliance with the best practice or standard mandatory, it should create a policy and make sure that everyone understands that this is a requirement levied from the organization itself. Best practices might come from other similar industry members, professional or trade associations, security organizations, and so on.
User Habits
In addition to policy-related topics, topics that concern the actions and habits of users must be addressed in training programs. Many such items will also be set forth in policy, but that doesn’t mean that users don’t need training and reinforcement to break bad habits where they exist. We’ll look at some of these bad habits the next few sections, and where appropriate, discuss how they may be also established in policy and why they should be included in any organizational information security training program.
Password Behaviors
By now, you should be aware that password issues can pose serious problems in an organization. Users forget passwords, write them down where they can be easily discovered by others, share passwords, use simple passwords, and so on. These are the causes of most password security issues, and why users need training regarding how to create and use passwords properly in the organization. Following are some key points that should be emphasized:
![]() Users should create complex passwords.
Users should create complex passwords.
![]() Users must try to create passwords that don’t use dictionary words.
Users must try to create passwords that don’t use dictionary words.
![]() Users should never share their passwords or write them down.
Users should never share their passwords or write them down.
![]() Users should change their passwords often to thwart password attacks.
Users should change their passwords often to thwart password attacks.
Of course, you should also use technical measures to help reinforce some of these rules, including configuring systems to allow only complex passwords of a certain length, as well as password expiration rules. You should also periodically check around the users’ work areas to make sure they haven’t written down passwords, and ensure that multiple people aren’t using the same accounts and passwords to log into systems. In addition, you should check to see if your password policies are being complied with by occasionally engaging in password cracking yourself—with the appropriate approval from management, of course. The problems associated with password behaviors, as well as the speed and ease with which passwords can be cracked by sophisticated attackers and systems, are the main reasons why organizations should consider multifactor authentication methods.
Clean Desk Policies
A clean desk policy isn’t about asking employees not to leave old soda cans and candy wrappers on their desks! Instead, it creates a process for employees to clear sensitive data out of work areas so that it is stored securely at the end of the workday. Sensitive data must not be exposed to unauthorized people such as janitors, maintenance personnel, guards, and even other employees when an authorized employee is away from his or her desk. A clean desk policy can apply to any time employees are using sensitive data at their desks and they need to leave the area. The goal is to make sure that sensitive data is not unattended and available. This policy should be developed and implemented as a formal written policy, and all employees should be trained on it.
Preventing Social Engineering Attacks
Users should be briefed on the general concepts of social engineering and how it works, and they should also be briefed on the specific types of attacks they may encounter, such as shoulder surfing, tailgating, dumpster diving, and so on. By being aware of these attacks, they can do their parts in helping to prevent them. Tailgating, in particular, exposes the organization and others to serious harm or danger if an unauthorized person is allowed to enter the facility. Users should be trained on how to spot potential social engineering attacks, including tailgaters, and how to respond to them by following organizational policies and procedures.
Personally Owned Devices
Users should also be trained on risks posed by bringing personally owned devices to work and how they might be in a position to help prevent these risks. Using such devices in the organization can lead to a loss of privacy by the individual, as well as loss of both personal and organizational data if the device is lost or stolen. If the organization allows individuals to manage their own devices, while allowing their use in the organization to process company data, then the organization is incurring huge risk, and users must be trained on the those risks and how serious their responsibilities are. If the organization is centrally managing mobile devices with mobile device management (MDM) software, the risk is significantly lowered because the organization can use remote capabilities to lock, encrypt, or even wipe data on the device. Users should be briefed on these capabilities if they are used within the organization to manage devices, because the user must accept organizational control of their device and the policies that may be enforced on them.
Social Networking and P2P
Social networking is ubiquitous. People use it to exchange information and photographs, keep in touch with family members and friends, and post a great deal of information out there in the world for everyone to see. Unfortunately, some people post way too much information on social media, decreasing their (and others’) level of privacy. Although organizations may have very little control over what individual employees post to social media sites, it’s probably a good idea at least to create a relevant policy and train users on what they should and should not post on social media. For example, users should be briefed that they should not post any sensitive or proprietary information on their social media sites that would compromise the organization or result in any type of unauthorized access or breach of information.
Note that some organizations have even tried to compel users to hand over passwords to social media sites or even to force them to “friend” the organization so that they can continuously monitor the employees’ use of social media. Several states have ruled that these practices are illegal, but in some states, no laws or statutes prevent an employer from doing this. Establishing a social media policy that may specifically include or exclude this practice, as well as the acceptable use of personal social media with regard to organizational information, and briefing it to employees, should be part of any security training program.
New Threats and New Security Trends/Alerts
Threats and attacks don’t stay the same, and the need for security doesn’t stand still on a daily basis. Malicious people are always coming up with new ways to attack an organization, steal data, destroy or disable systems, and otherwise wreak havoc on information belonging to an organization. That’s another important reason why training should always be recurring in nature—to brief users on new attack methods and reinforce the rules and security concepts they should make part of their daily routines. You should keep users up to speed on a few different types of new threats that occur on an almost daily basis, through periodic classroom training, information e-mails, bulletin board postings, or other methods.
New Malware and Viruses
New forms of malware are released continually; look at the latest security bulletins from some of the major anti-malware vendors, equipment manufacturers, software vendors, and security sites to see this. Of course, we as security folks are always applying patches, updating configurations, and installing new antivirus signatures to combat new forms of malware. But this doesn’t mean that it won’t get through into our systems, because often users let it in to our networks out of ignorance, simply by clicking a pop-up, opening a web site, or opening an unknown file that may execute a piece of malware. That’s why training users on new threats, such as malware and viruses, is important. Of course, you shouldn’t get everybody in a classroom for a formal briefing every time a new piece of malware comes out; you’d have everybody in the briefing room all day long, every day, and no work would ever get done! But you can regularly provide information related to serious threats of malware that may include user action as an avenue of attack. Send out e-mails from verified security accounts, include links to reputable security sites, post warnings on company intranet sites, and use other methods to distribute information whenever a serious malware threat emerges.
The same applies to new phishing attempts. Once you are aware of a new phishing attack, you should send this information to users through the aforementioned venues. This gives them the information they need to understand how the attack works, what they should and should not do if they encounter suspicious activity, and what reporting steps they should take.
Zero-day Exploits
As you know, a zero-day exploit takes advantage of a vulnerability, usually the same day the vulnerability is announced, with no mitigation available. This means that as soon as you know about a vulnerability, an attacker may already be exploiting it. You may have no means of detecting it or protecting against it. Security and software vendors may provide workaround mitigations that you could use until a patch or configuration change is available to mitigate the vulnerability permanently. However, these workarounds could mean a loss of functionality in your systems.
When a zero-day exploit is announced, you should immediately notify your users, as appropriate, so they are aware of the issue, and then take steps to help prevent it from affecting your systems. If the workaround involves blocking a certain protocol or type of traffic entering the organization’s network perimeter, users will have to be briefed on this, especially if it affects critical business functionality. In the meantime, you may have to develop your own mitigations that reduce the risk of an attacker exploiting this vulnerability, while allowing critical business functions to continue simultaneously.
Training Follow-up
After training, you can’t simply walk away from the user or IT worker and assume that the training will “stick” forever and all will be OK with the world. To get your time and money’s worth out of the training, you need to be able to determine whether the users learned the information, and, more importantly, if the training did (or will) make a significant impact in reducing security vulnerabilities through improved user behavior. You also need to reinforce training periodically so that it stays fresh and relevant, and so that users don’t get complacent.
Recurring Refresher Training
User security training should be provided to employees when they first join the organization, during their on-boarding processes. You should also start a training record on the employee at this time, both for compliance and HR purposes. IT professionals and security folks will also need additional training related to their duties. After the initial training, employees should receive periodic or recurring training, usually required at least annually for compliance with some regulations, but at minimum whenever the computing environment changes or new and significant threats emerge. As mentioned, it doesn’t all have to be in-the-classroom formal training; it can be in the form of 15-minute briefings, e-mails, bulletin board or intranet postings, computer-based training, video presentations, and so on. It can also be very threat- or subject-specific, and can occur on an as-needed basis. In any case, users should have an overall periodic refresher session on general threats and security practices as determined by the training policy.
Measuring and Validating Compliance and Security Posture
How do you know that training has been worth it? How can you measure the effectiveness of security training? You might offer users surveys or questionnaires after training to collect information on how relevant the training was to their jobs. You might include questions on suggestions for improvements to training, in case it did not adequately cover issues the employees encounter in their daily routines. The responses could help you measure whether you are training them on the right issues, threats, and practices they need or how you can make the training more effective. You can also ask employees to take a survey after a security issue occurs to determine whether the training they received was helpful to them as they responded to the incident or if additional training might have helped them prevent the incident.
Additionally, you could collect data and statistics on the occurrences of security incidents in your organization, looking for trends that might indicate the effectiveness of training. For example, if you provide training and then see a decrease in that particular type of incident, you may infer that the training was effective. If incidents have increased, that may indicate a gap in training that you need to address.
Module 37 Questions and Answers
Questions
1. Which of the following is the most effective mitigation for security vulnerabilities involving people?
A. Firewall rules
B. Disciplinary action
C. Restricted access
D. Training
2. Which of the following is likely not an effective training approach for routine users?
A. Holding formal briefings
B. Classroom training
C. Asking them to read a security book
D. Sending weekly security-oriented e-mails
3. Your manager wants you to develop a role-based approach to security training. Which of the following roles will likely need more advanced security training in theory and techniques?
A. Marketing user
B. Administrative assistant
C. Security auditor
D. Manufacturing supervisor
4. Which of the following should be briefed to all users in the organization?
A. Acceptable use policy
B. Data backup and restore procedures
C. User account creation procedures
D. Technical encryption standards
5. All of the following is considered personally identifiable information, except:
A. Date of birth
B. Work section assignment
D. Home address
6. Which of the following represents levels of data criticality or sensitivity that do not require stringent protection methods?
A. Marketing blog
B. Manufacturing processes
C. Company financial data
D. Employee records
7. Which of the following is not normally considered compliance governance regarding data protection, unless specifically mandated as such in organizational policy?
A. Gramm-Leach-Bliley
B. HIPAA
C. PCI standards
D. NIST standards
8. Which of the following policies is designed to ensure that sensitive documents and materials are not left unattended for unauthorized persons to potentially access?
A. Access control policy
B. Clean desk policy
C. Acceptable use policy
D. Data classification policy
9. You’ve just received an e-mail alert from a trusted security site that informs you of a new widespread phishing attack. Which of the following should you do to help prevent this attack in your organization?
A. Configure the firewall to block inbound e-mails with the word “phishing” in the message content.
B. Configure all outbound e-mail to require digital encryption and signatures.
C. Inform users so that they will take care to avoid this type of e-mail attack.
D. Block all outbound HTTPS requests that have the word “phishing” in the URL.
10. Which of the following is the most meaningful measure of security training effectiveness?
A. A decrease in the types of security incidents the training focuses on
B. Surveys that indicate employee satisfaction with the training
C. An increase in security incidents not covered by security training
D. A decrease in the number of employees who feel they require the training
Answers
1. D. Training is the most effective mitigation for security vulnerabilities involving people.
2. C. Giving routine users a security book and having them read it is likely not an effective training approach.
3. C. A security auditor will likely need more advanced security training in theory and techniques.
4. A. The organization’s acceptable use policy should be briefed to all users in the organization.
5. B. An employee’s work section assignment is not normally considered personally identifiable information.
6. A. A public marketing blog does not typically require stringent protection methods.
7. D. Because it only promulgates standards, NIST is not considered compliance governance regarding data protection, unless the organization specifically mandates it according to policy.
8. B. A clean desk policy is designed to ensure that sensitive documents and materials are not left unattended for unauthorized persons to potentially access.
9. C. You should inform your users so that they will take care to avoid this type of e-mail attack.
10. A. A decrease in the types of security incidents the training focuses on is the most accurate indicator of security training effectiveness.