MODULE 20
LAN Review
Now that we’ve discussed hosts, it’s time to turn our attention to networks. We’ve touched on several aspects of network security, including secure protocols, network-based attacks, and so on. We’ve just scratched the surface, and we have even more to cover in terms of securing the network portion of an infrastructure. In this part of the book, we’ll discuss network security at a greater depth, focusing on all of the different elements of the network that are connected together to provide secure communications for an enterprise. In this module, we’ll briefly review the different local area network (LAN) technologies, including devices, architectures, and secure networking principles.
Securing Networks
Although we’ve already briefly discussed secure network protocols, we’ll take an in-depth look at network security in this section, discussing network devices and how to configure them securely, the design elements that go into a secure network, and, finally, different security methods and technologies that help make up secure network administration. We’ll lightly cover some topics in preparation for other modules ahead of this one, and we’ll go into much greater depth on others. Understand that network security is an extremely important part of security in general, so reach back into your mind for all the knowledge and experience you’ve gained from your Network+ exam and courses, as well as real-life experience. Also understand that we’re not simply going to repeat the Network+ exam review; although we’ll be discussing many topics that may serve as a reminder of those studies, we’re focusing on the security aspects of networking here.
Securing Network Devices
In this section, we’ll discuss different aspects of configuring certain network devices securely. Obviously, we will be discussing firewalls, since they are the ubiquitous network security device. However, there’s more to a secure network than simply deploying firewalls. Many other network devices have critical security functions built into them that you should be aware of and understand how to configure. We’ll discuss the security aspects of routers, switches, and load balancers as well. We’ll also discuss other security devices in later modules that are just as critical.
Firewalls
A firewall is the ubiquitous network security device. Many people mistakenly think that if you have a firewall in place, your network is secure. Although a firewall is definitely a critical piece of the security infrastructure, it’s not going to provide for every security requirement. It is simply a part of a layered infrastructure that works together with other pieces to ensure defense-in-depth for the entire network.
So what is a firewall, actually? It can be a specialized hardware device or software that runs on a traditional operating system. Its purpose is to separate networks and filter traffic between those networks. It does this by inspecting the traffic based upon preconfigured rules that determine whether the traffic should be allowed into or out of a network. Think of a firewall as a traffic cop between two networks. In a traditional example, the firewall separates the public network (such as the Internet) from the internal private network. It typically blocks undesirable traffic from coming in and prevents sensitive traffic from going out. We refer to filtering incoming traffic as ingress filtering, while inspecting and filtering outbound traffic is called egress filtering. We’ll discuss the details of firewall rules later on in this module.
Firewalls can be network-based (usually hardware devices) or host-based (usually software-based firewalls that run on a host’s operating system). Network-based firewalls are typically used to protect entire network segments. Traditionally, firewalls were thought of in terms of separating only public from private networks; but modern security theory also emphasizes the use of firewalls in an internal network to separate sensitive network segments from other internal networks. Firewalls can filter traffic based upon a wide variety of criteria, including port, protocol, network service, time-of-day, source or destination host, and even users or entire domains. More advanced firewalls can also do deep-level traffic inspection, so even traffic that meets rules allowing it to pass through the firewall could be denied due to the content of its traffic. For example, HTTP traffic is normally allowed through a firewall, so firewall rules might allow it based upon protocol alone. However, an advanced firewall might inspect the HTTP traffic and discover that a hacker has embedded malicious code into this traffic. In this case, the firewall would drop the traffic and possibly alert the administrator to it, or at least write the event to a log.
Routers
Routers are network devices that serve to send IP traffic from one LAN to another, usually across a wide area network (WAN). Routers could separate LANs within an organization or send traffic from an internal LAN to an external network by routing it across the Internet, for example. As a security device, however, a router can serve some basic functions that closely resemble what a firewall can do, although not at the same level. In addition to routing traffic, a router can also filter traffic just as a firewall does. Typically, however, a router does not have the advanced functionality of the firewall, but it can filter traffic based upon some basic criteria. These criteria might include source or destination IP addresses or domain, port, protocol, service, and so on. Normally, routers do not do any advanced deep-level traffic inspection, since that would involve far more resources (CPU processing time, memory, and so on) than a router typically has. Additionally, this is not the router’s main function on the network, so deep packet inspection is a little out of scope for what it’s designed to do. Using a router to filter traffic, however, can help offload the work involved in filtering out the “low-hanging fruit” of bad traffic. For example, if an entire protocol or port is to be filtered, or an entire domain, then a border router might be the best candidate to provide those services. That way, only more complex traffic requiring the advanced features of a firewall are passed through and left for the firewall to deal with. Anything that involves complex rules or decisions is better left up to a firewall rule set to filter that type of traffic.
Switches
As a network device, the switch’s job is to separate collision domains and cut down on the amount of network “noise” generated by hosts during normal operations. Where a router separates LANs from each other and eliminates broadcast domains, a switch segments LANs into multiple physical (and sometimes logical) parts. From a network perspective, a switch does this job very well. From a security perspective, an intelligent switch can also add additional functionality.
First, a switch can be used to prevent network sniffing. A sniffer usually requires access to all the traffic that hosts on a shared medium transmit and receive. Since a switch eliminates collision domains, it also eliminates the ability of a sniffer to “hear” traffic from other hosts. If a sniffer is plugged into a normal switch port, the only traffic it can sniff is traffic between itself and the switch, in addition to broadcast traffic from other hosts. It can’t pick up on traffic sent directly between other hosts. The only way a sniffer can be used on a switched network is to place it explicitly on a spanned port (one in which an administrator has configured to span all the traffic on a switch), or to use various malicious attacks to render the switching functions of the device inoperable. So switches can be used to help prevent interception of sensitive network traffic.
Second, a switch can be used to prevent unauthorized hosts from connecting to the network. If port security is turned on in a switch, only specified MAC addresses can plug into a switch port and connect to the network. Any unauthorized hosts will not be allowed to connect, and the connection can be logged and an alert sent to an administrator.
The third major security function that a switch performs requires intelligent switches, such as those referred to as layer 3 switches. These types of switches have advanced functions that enable them to perform some of the same functions that a router performs—namely, the separation of LANs. Normally, switches physically segment LANs into different pieces, but a layer 3 switch can also logically separate hosts into entirely different LANs, called virtual LANs (VLANs). We’ll discuss VLANs a bit later in the module. For now, you should know that VLANs enable network administrators to separate sensitive hosts from other hosts based upon a logical VLAN assignment.
Load Balancers
A load balancer is a network device used to provide efficient and rapid workload sharing between network devices (such as routers or firewalls) or hosts, typically web or file servers or storage devices. A load balancer contributes to security by providing for high availability. If a server goes down, the load balancer can transparently and immediately provide for availability by transferring network and resource requests to an identically configured backup server. Most of the time, the devices configured to work with a load balancer are all performing the same functions at the same time; the load balancer merely ensures that there is an even amount of traffic and requests going to all the members of the device cluster attached to the balancer. This helps provide for efficiency, eliminates delays or latency, and provides for system and data availability in the event that a member of the cluster is unable to fulfill requests. Load balancers may use several different criteria to determine which device gets a particular request. It may base its decisions on network traffic conditions, for example, or it may use a turn-based system (otherwise known as a round-robin type of system).
NAC
Network Access Control (NAC) provides network protection and security by prohibiting hosts from connecting to the organization’s infrastructure unless they meet certain criteria. A NAC device is used as an entry point or gateway into the network, typically for remote or mobile clients. This device checks the health and security settings of the client against a specified set of criteria before allowing it to access the network. For example, a NAC device could check for the latest antivirus signatures, the latest security updates, and other security configuration items. If the client did not meet these requirements, it would not be allowed to connect to the network. Additionally, the NAC device might be able to update the client dynamically or reconfigure certain options so that the client could proceed with authentication and connection to the infrastructure. A NAC could also be used to authenticate devices, allowing only authorized devices to connect. Normally, a NAC would be placed on a secure segment within a demilitarized zone (DMZ) network.
Secure Network Design
Having the latest and greatest network security devices on your network is a good start, but if your network design is not effective, then having even the best, most securely configured firewall in the world won’t help you. Network design is a critical element in security, simply because knowing how and where to place different components such as security devices, hosts, and so on, in relation to the internal and external networks makes a difference in whether these secure network devices are effective at doing their job.
In the next few sections, we’ll discuss elements of secure network design, such as DMZs, VLANs, and so on. We’ll define them, examine their places in the overall network architecture, and see how they relate to securing the infrastructure. Beyond design considerations, some of the topics we’ll discuss relate not only to where network devices and hosts are placed, but also to how they are integrated into the overall security architecture.
Secure Architecture
Architecture has a significant effect on security in a network. When designing a secure network, you must take into account the entry and exit points (logical and physical), traffic flows, placement of devices, traffic filtering, and network separation. These considerations affect the design and structure of the network, both from performance and security points of view.
Bastion Host
In modern security design, a sensitive network isn’t normally directly connected to the Internet. It usually has some sort of security devices between it and a public (or non-secure) network. In an extremely simple design, a single secure host could separate an internal network from an external or non-secure network. This is referred to as a bastion host and is usually a single hardened device that provides a choke point for traffic entering into and leaving from the internal network. A bastion host has several issues, however. First, it is a single point of failure. If it goes offline or is compromised, there is no longer any defense between the external and internal networks. Second, performance could be an issue during high traffic situations, since all traffic flows through that single point. Yet another problem is that an attacker has to get through only one host, so she can focus all of her attention on that host for an attack. Figure 20-1 shows how a bastion host might be implemented.
Figure 20-1 A bastion host setup
DMZ
For the reasons explained previously, among others, most modern networks don’t implement a single bastion host type of architecture. More often, they implement a perimeter network structure, consisting of security devices and other hosts that serve as a buffer between the internal network and any other non-secure networks, such as the Internet. This perimeter or buffer network is sometimes called a demilitarized zone, or DMZ. A DMZ provides a buffer for traffic coming into the organization’s networks. Not only does it filter traffic, inspecting it for potential attacks, but it also sends traffic to an appropriate network location. For example, normally an organization wouldn’t put an Internet-accessible web server on its internal network, because this could allow external clients access into the internal network. So the web server would be placed in the DMZ, and security devices would route the appropriate traffic to that particular host.
In the DMZ, the different host devices you would normally find might include firewalls, routers, proxy servers, web servers, VPN servers, external DNS servers, and so on. You normally would not put any host in the DMZ that contains sensitive data, or at least not without securing the connection between that external host and any internal hosts. You can implement a DMZ in a few different ways; some designs include the use of two firewalls, one at the outside of the DMZ that filters all traffic coming through and routes it to the appropriate network device, and another firewall that is directly in front of the internal network, protecting it from any traffic that’s allowed into the DMZ. You also might have different network segments off of the DMZ for specific purposes—a secure DMZ segment might be used for a business partner, for example. Figure 20-2 shows how a typical DMZ is constructed; keep in mind this is just one design among several different ways you could implement a DMZ.
Figure 20-2 An example DMZ architecture
Network Separation
Network separation can contribute to security because sensitive hosts can be segregated from others, protecting them from unwanted access. Hosts can be assigned to different networks, both physically and logically, so that different security policies can be applied to them; traffic can be selectively filtered between sensitive and non-sensitive hosts; and access controls can be better implemented. Physical separation involves plugging hosts into physically separate devices that may be located in secure areas, and that are able to communicate with other hosts only through secure means or not at all. Physical separation is very important, of course, but often, for convenience, performance, or functionality, hosts can’t be physically separated from the people who need access to the resources housed in them. For example, plugging sensitive servers into a particular switch locked up in a room and managing that switch as a single device with one set of policies may sound reasonable, but sometimes it may be necessary to apply different security configuration elements to the different hosts on that switch. Physical separation alone won’t allow you to do this. Logical separation, on the other hand, enables administrators to separate hosts, and entire network segments, based upon the use of network protocols, such as IP, while maintaining flexibility, security, and functionality. Logical separation involves the use of different IP subnetworks, VLANs, Network Address Translation (NAT), and other means. In this section, we’ll discuss how we can divide up networks based upon these methods, starting with subnetting.
Subnetting
Subnetting, if you remember from your Network+ studies, enables you to divide up networks (based upon IP address ranges) logically into separate subnetworks (subnets). This lets you place hosts logically in a different network, even if they are sitting side-by-side. While we’re not going to reteach you subnetting at the Network+ level, it’s worthwhile to review a few points about it here, since it can be somewhat relevant to security.
Subnetting takes the default address classes (A, B, and C, usually) and can divide up those networks based upon the number of bits in the subnet mask. Remember that a subnet mask is used to tell a host which part of its IP address represents the network ID, and which part represents the host ID. Organizations subnet the default address classes to gain more networks, trading them for numbers of available host addresses. The more subnet bits in a mask that are used for additional networks, the less subnet bits are available for individual hosts in those networks.
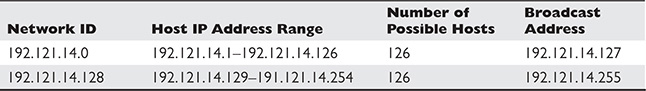
Let’s look at an example. In an ordinary default class C address, the default subnet mask is 255.255.255.0 (a 24-bit mask). With an IP address of 192.121.14.7, for example, we know that the host is on the 192.121.14.0 network, and that there are 254 possible host addresses for that network, since 0 is reserved for the network ID and 255 is reserved for the broadcast address. So the valid host range is 192.121.14.1 through 192.121.14.254.
However, if we were to subnet that address, possibly dividing the same address space into two separate networks, we would have a new subnet mask of 255.255.255.128 (trading a host bit of 0 for a network bit of 1 in the last octet), which is a 25-bit mask. This gives us two new network IDs, 192.121.14.0 and 192.121.14.128. Each of these networks would have 126 possible host addresses (and one address each for the broadcast address). Table 20-1 summarizes this.
Table 20-1 Subnetting a Class C Network Address into Two Networks
So, now that we’ve reviewed (very briefly) how subnetting works, of what use is it to us in security? Well, since subnetting breaks up larger networks into multiple smaller ones, it can be used to segment groups of hosts from each other. By itself, this offers no real security, but separating networks can cut down on traffic that may affect availability, such as broadcast traffic. Remember that different LAN segments require a router to communicate between them, so a router can be used to impose some traffic restrictions on the different subnets connected to it. This could enable filtering of undesirable traffic between subnets. Additionally, subnets provide a convenient grouping for hosts to which policies can be assigned when applying security policies in routers, firewalls, and other security devices. Subnets can be physically separated, enabling some degree of physical security, but they can also be logically separated, as in the case of VLANs, discussed next.
VLAN Management
Earlier in the module, we discussed the security functionality that switches provide. One of the things we mentioned was that it enables us to create VLANs. A VLAN doesn’t depend upon the physical layout of the network; it doesn’t matter if the hosts are physically sitting next each other or are located several buildings apart. A VLAN creates a logical network for hosts to be assigned to. You know that the defining characteristics of a LAN are that hosts are on the same subnet; that they communicate to each other without the need to be routed; and that they use hardware (MAC) addresses to identify each other during communications. In a VLAN, once a host is assigned to a VLAN, it follows those conventions, as if it were physically a part of a LAN. VLANs are created on layer 3 switches, by configuring the switches to establish and recognize VLANs with certain characteristics. These characteristics include a particular IP subnet as well as VLAN membership. VLAN membership can be based upon the switch port the host is plugged into (called a port-based VLAN); it can also be based upon the MAC address of the client (a MAC-based VLAN). You could also have a protocol-based VLAN, which would ensure that any client with an IP address on a particular subnet would be assigned to a particular VLAN by default. Different hosts can be assigned to different VLANs, even if they are plugged into the same switch and sitting right next each other. Since VLANs operate with the same characteristics as normal LANs, broadcasts are not passed between them. In fact, it’s actually necessary to route traffic between VLANs. You could use a traditional router for this, or, more often, you could configure the switch to route between VLANs (called inter-VLAN routing). If VLANs need to access networks that aren’t controlled by the switch, the traffic must pass through a traditional router.
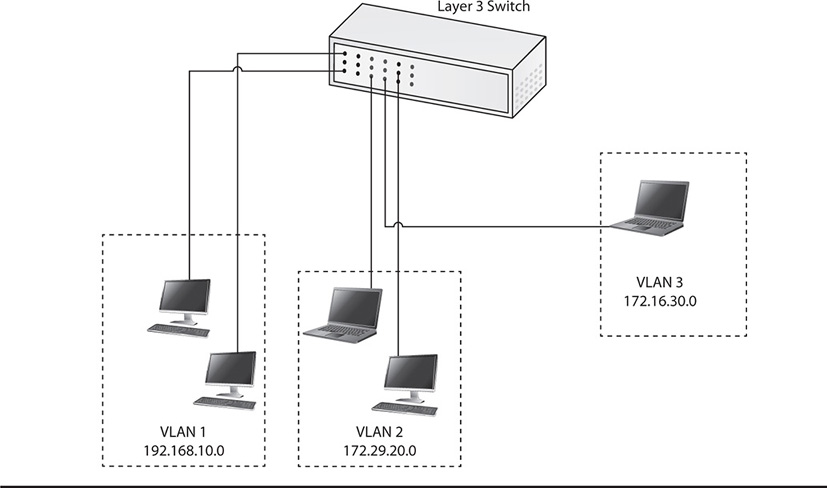
VLANs contribute to security because they allow administrators to separate hosts from each other, usually based upon sensitivity. In other words, you can assign sensitive hosts to a particular VLAN and control which other hosts access them through the VLAN. Since VLANs are logical (and software-based), you can control other aspects of them from a security perspective. You can control what types of traffic can enter or exit the VLAN, and you can restrict access to hosts on that VLAN via a single policy. You can also provide for increased network performance by using VLANs to eliminate broadcast domains, the same as you would with a traditional router. Figure 20-3 illustrates an example VLAN setup.
Figure 20-3 VLANs on a switch
NAT
Network Address Translation, or NAT, was initially developed when it became apparent that the IP version 4 (IPv4) address space was at its limits. More and more organizations had larger numbers of hosts but were unable to obtain the numbers of public IP addresses to support those hosts. To slow down the inevitable exhaustion of IPv4 addresses and provide a way for larger organizations to use very limited numbers of public IP addresses, NAT was used, along with the private IP address space mentioned earlier. This enabled internal hosts to have their own non-routable IP address ranges that could comfortably accommodate even large numbers of hosts. NAT requires a network device capable of handling public-to-private IP address mappings, such as a router or security device. NAT works like this: An organization could have only one or just a few public IP addresses. It can have many more internal hosts than the number of available public IP addresses, so the public IP addresses can be dynamically mapped to internal private IP addresses during communications sessions. There are a few ways to do this. First, one public IP address could be temporarily mapped to a single private IP address. Or a public IP address could be mapped to a pool of private IP addresses. In this option, called Port Address Translation (PAT), the internal client’s source port is kept in a table and used in the translation process, so that when external communications are returned for that particular client, the device handling NAT knows which client the traffic is intended for. You can also use a pool of public IP addresses, if you have more than one, in the same manner. You can also use static NAT, which creates a persistent mapping of a public IP address to a private one. This is typically used only when an internal host needs to receive traffic constantly from external clients, such as a web server. Static NAT, however, should be used minimally whenever possible.
From a security perspective, NAT enables the organization to hide its internal IP address range from external networks and clients. This can help prevent attacks on particular hosts, since external clients won’t know the internal IP address of any hosts. NAT can also help prevent certain types of attacks that require spoofing of a victim’s IP address. If an attacker doesn’t know the victim’s IP address, or can’t send traffic into the internal network because the firewall or security device blocks inbound traffic from its internal address space, then he can’t easily spoof addresses or initiate certain types of network attacks. Until recently, NAT caused certain types of security protocols, namely IPsec, not to function properly; however, this issue was resolved with later versions of the protocol.
Secure Network Administration Principles
Now that we’ve discussed the benefit of using security devices, and how they are placed with respect to internal and external networks, we also need to go over the fundamentals of securely administering a network. Even with a solid design that considers security, as well as the placement of some well-configured security devices, the day-to-day administration of the network is vitally important to ensure that it stays up and running and remains secure. In the next few sections, we’ll look at several ways that you can keep your networks available and ensure the confidentiality and integrity of the data and systems that use it.
Rule-Based Management
Most security devices use some sort of rule-based management configuration; in other words, a set of rules tell the device how to filter certain types of traffic and what actions to take. Rules are made up of different elements—parameters that you configure as part of the rule. These parameters could include filterable elements, such as port, protocol, service, user, source or destination addresses, and so on. You could also use preconfigured groups or domains as rule elements. Rules normally take allow or deny actions. Some rules have elements that allow you to log a particular event, regardless of the action, while other events may not be logged at all.
Rules are normally listed in a sequential form, and when traffic enters the device, it is checked against each rule, one at a time, until the traffic matches the parameters of a particular rule. Once a match happens, the rule checking process normally stops; no other rules are checked, and whatever action is configured in the rule for the traffic is implemented. So, if a rule states that HTTP traffic inbound to the network for a particular IP address is allowed, then any traffic that matches the conditions of that rule will be allowed into the network. For example, if HTTP traffic that is inbound to a different IP address comes in, it doesn’t match all of the different elements of the particular rule in question. And if there’s no match, rule checking continues. If that particular type of traffic matches elements of a different rule, then it is processed accordingly. If no match occurs by the time all of the rules are checked, the traffic is usually dropped because of a feature known as implicit deny, discussed next.
Implicit Deny
The concept of implicit deny can be a difficult one to wrap your head around. It’s helpful to explain a few related terms first. Essentially, it involves a deny action, which means that traffic isn’t allowed to pass through the device. An allow action, on the other hand, means that traffic is allowed to pass through the device, of course. An explicit rule means that the rule is actually configured in the rule set specifically for a particular type of traffic. An implicit rule is not created in the rule set; it’s more of a default action that a security device takes when all the other rules have been examined and processed. So you could have explicit rules that allow or deny traffic, and how these rules interact with each other depends upon your policies. In a default-allow policy, all traffic is allowed, except for explicitly denied traffic. In this type of policy environment (usually more of an open and relaxed environment), most traffic is allowed into the network. Only particular instances of undesirable traffic are denied in the rule set. On the other hand, in a default-deny policy, everything is denied by default, and only by exception is traffic allowed. This is usually found in a very security-conscious or restrictive environment. Again, this might make use of an explicit rule defined in the rule set.
The concept of implicit deny essentially means that after all other rules have been applied in a rule set, whether they are allow or deny rules, any traffic that makes it through all of those rules without a match is automatically denied. In some firewall rule sets, an implicit deny is enough; traffic that doesn’t match any rules in the list is simply dropped. However, some administrators still choose to place a catch-all explicit deny rule at the bottom of the rule set, so that any traffic that is not matched by a previous rule will definitely be denied. It’s important to remember that any type of catch-all rules, such as an explicit deny, are placed at the very bottom of the rule set. This is because any traffic would match this rule, and most firewalls and other secure devices will stop processing once a match happens. So if this rule were to get into the top of the rule set accidentally, all traffic would match it, processing would stop, and the firewall would deny everything into and out of the network. Rule placement is very important, as you can see, within a rule set. Figure 20-4 shows the Windows Firewall With Advanced Security window, which shows a number of rule sets.
Figure 20-4 Rule sets
Access Control Lists
Access control lists (ACLs), when discussed in the networking context, are simply rule sets that are normally found on network devices, usually routers. They usually follow the same types of rules that we discussed earlier regarding firewall rule sets. One big difference between firewall rule sets and regular ACLs is that firewalls can normally perform advanced filtering operations on traffic and require more complex rule sets that use a wide variety of elements in those rules. ACLs, on the other hand, are usually very simplistic, especially when found on routers, for example. An ACL is normally applied to each interface of a router, so it really applies to a single network segment. In an ACL, elements that make up the rules are very simple; these are usually only the very basic elements used in traffic filtering, such as port, protocol, source IP address or destination IP address, and so on. As we’ve mentioned before, routers offload some of the work from firewalls by filtering very basic types of traffic. The ACL rule sets are used to perform this basic filtering.
Secure Router Configuration
Because we’ve discussed managing firewalls and their rule sets, as well as ACLs, we should spend a few moments talking about securely managing routers. Router management involves several aspects. First, the use of ACLs is a must; remember that these apply to the different network interfaces connected to the router, so you have the flexibility to impose different security rules on different network interfaces, based upon their sensitivity. Other secure router management principles involve some of the same things you would do to secure a host, such as keeping the router OS updated and patched and applying the principle of least privilege to router access. This means that only authorized network administration personnel should be able to access a router, and this should be only through a secure means, such as SSH, for example. Older methods of router access, such as Telnet, should be disabled, since credentials would be sent in clear text to the device and could be intercepted. Physical interfaces to the router should be disabled unless absolutely needed; this includes network interface connections, as well as console connections.
Additionally, it’s a good idea to manage routers as well as other network devices using only a secure version of the Simple Network Management Protocol (SNMP). You should use at least a minimum of SNMP version 3, because it provides some level of security protection. You should also change the community strings used for the SNMP configuration on the router; in other words, you must change them from their default values of public and private. As with other types of devices, you should follow the minimum functionality principle as well. In other words, limit the number of protocols that run on the router only to what you need, and turn all others off. You should also avoid the use of unsecure protocols whenever practical, such as FTP, TFTP, and of course Telnet. There are other details to locking down the configuration of a router, but most of these are vendor- or operating system–specific. Review those hardening guides from the vendor and follow them as closely as possible to secure your network.
802.1X
For network devices, such as switches and routers, port security is an important concept that you should be aware of. Port security involves securing the physical ports that allow hosts to plug into a network device as well as logically securing those ports. Ports on networking devices can be configured such that only specified hosts can connect to them, based upon MAC address or other criteria. Ports should also be completely turned off if they are not being used, so that unauthorized hosts can’t plug into them and attempt network connections or attacks.
From a logical perspective, disabling unused ports or enforcing criteria that hosts must meet in order to connect to the network via a switch port are good practices, but you can also do other things regarding port security. One key security control that you can use is a port-based authentication system, such as the IEEE standard 802.1X. This standard provides for port-based authentication and can be used on both wired and wireless networks. It is most commonly seen on wireless networks, however, and then only when a more robust security method, such as WPA/WPA2 Enterprise is used. 802.1X can use a wide variety of authentication protocols, including Extensible Authentication Protocol (EAP), and allows for not only user authentication, but device authentication as well. Additionally, it also provides for mutual authentication among users, hosts, and the network.
In wired networks, 802.1X can be implemented on network devices to provide for authentication of wired devices. This ensures that only authorized devices can connect to the network. Any unauthorized host attempting to connect is denied access and unable even to detect any traffic.
Flood Guards
Although flooding and water damage are definitely a threat to computing resources and people, in this context we aren’t talking about the types of floods associated with natural disasters. We’re talking about flooding from excessive or malformed traffic that enters a network. A network can encounter several different types of floods. We’ve already discussed SYN floods, which are excessive amounts of SYN segments sent to a host to conduct a denial-of-service attack against it. Other types of network flooding include Internet Control Message Protocol (ICMP) floods, User Datagram Protocol (UDP) floods, MAC floods, and other types of protocol-based flooding.
Attackers use traffic floods primarily to conduct denial-of-service attacks on networks and hosts, since many hosts and network devices don’t always react very favorably to excessive amounts of traffic or malformed traffic. Because flooding is a routine tactic of attackers, most modern network devices (and even some hosts) have flood protection built into their operating systems. These flood guards work by detecting excessive traffic (by volume, as well as by rate of speed) and take steps to block the traffic or drop it, so that the host doesn’t have to process it. Most security devices, such as intrusion detection systems, firewalls, and robust network devices, have flood guards built in.
Loop Protection
In relation to network architectures, a loop is a condition that exists when more than one logical or physical path exists between two networks. This could happen for a couple of reasons: a switch or router may be misconfigured, multiple physical cables are plugged into ports that span different networks, and so on. When the network device detects that multiple paths or multiple networks are connected to it and aren’t supposed to be, the device tries to adjust for the new network conditions, sometimes sending wrong or excessive traffic out to the different networks. Under the right conditions, this traffic can loop right back into the same network it left. Loops can cause issues on the network because they contribute to an increased amount of unnecessary network traffic, such as broadcasting. Although looping is more of a network administration issue, it can cause security issues because it affects network availability. Hosts may be unable to communicate with the other hosts or other networks because of looping issues, or their performance can be degraded due to excessive network traffic.
Most modern network devices offer some sort of loop protection, which means that they have mechanisms built into their operating system to check for looping conditions and correct them. This may mean rerouting traffic or reconfiguring ports on the fly, or even shutting down a particular port or network connection. From a security perspective, loop protection is very important, since network availability is a security issue.
Remote Access
As with our discussion on other network-related subjects, we’re not going to get into an involved discussion over the different remote access technologies here; those subjects are best left to the Network+ studies. As a reminder, however, methods of remote access include good old-fashioned dial-up over a modem, ISDN services, and of course VPN connections. Each of these has its advantages and disadvantages, but an in-depth discussion on dial-up and ISDN is more of a history lesson than anything. We discuss VPN technologies elsewhere in the book, so we’re going to discuss remote access here in this section. You need to be aware of and plan for some critical elements of remote access, since they contribute to the security of remote access connections. Two critical elements in remote access are encryption and authentication.
Remote access these days typically means VPN connections, some type of remote desktop connections, or even remote shells. All of these connection methods require encryption and authentication. In VPN connections, the most common types of protocols are IPsec for security, coupled with the Layer 2 Tunneling Protocol (L2TP) tunneling and encapsulation protocol. Another common type of VPN connection uses secure sockets layer (SSL). For both of these types of VPNs, public key technologies and other types of authentication methods can be used. It’s important that you ensure that remote access connections are authenticated as well as encrypted. The VPN client and the concentrator side must support the same levels of encryption and authentication, which should be configured in advance; otherwise, a secure connection can’t be established.
For remote shell connections, ensure that you’re using only secure protocols, such as SSH, for example. Older protocols, such as Telnet, rexec, and rsh (remote shell), are non-secure because they do not encrypt information; everything travels over them in plaintext. There’s also no authentication for these protocols. SSH, however, provides for secure authentication and encryption between the local and remote host. It also can use public and private key technologies to generate key pairs and certificates for local and remote hosts. As a bonus, SSH can be used for secure file copy between two hosts (using Secure Copy Protocol, or SCP) and secure file transfer for multiple hosts (with Secure File Transfer Protocol, or SFTP).
Remote desktop technologies provide varying degrees of security, depending upon the vendor and the type of protocol used. However, even many of these non-secure remote desktop protocols can be tunneled through other secure protocols, such as IPsec, SSL, or SSH. If they are not tunneled, you should ensure that the maximum compatible levels of security are configured on both ends of the connection—this includes encryption algorithm, key strength, and authentication methods.
Telephony
Until a few years ago, telephony was not really considered part of the security administrator’s responsibility. However, with changes in technology and the desire to unify all communication services, including voice, into the network, and to save resources, these days more network and security administrators are controlling more telephone and voice services in their jobs. Previous telephone setups involved an organization setting up its own private branch exchange (PBX) to defray costs involved with the telephone companies. A PBX is an internal telephone switch that is controlled and managed by the organization. Older security vulnerabilities with PBXs were associated with a lack of administrative controls, such as accounts and passwords, backdoor entry points via dial-up, and the lack of auditing. These vulnerabilities allowed attackers to take advantage of poorly configured PBXs to access the organization’s network, use the phone switch to make free long-distance phone calls, and generally take advantage of an organization.
Although the lack of security characterized PBXs, newer technologies that use Voice-over-IP (VoIP) protocols are more secure, since VoIP typically involves using the same infrastructure that data uses—namely, the network. So any types of security controls that data uses over the network, VoIP can use as well. This includes firewalls, VLANs, and even encryption. Also like data over the network, VoIP is vulnerable to several attacks, including spoofing, denial-of-service, interception and eavesdropping, and spam. Administrators must take precautions with telephony services that use the network, ensuring security while also making sure that performance is maintained.
Module 20 Questions and Answers
Questions
1. Which one of the following types of filtering is used to control traffic entering a network?
A. Egress filtering
B. Ingress filtering
C. Implicit deny
D. Explicit deny
2. Which network device is used to send traffic to different physical networks, based upon logical addressing?
A. Router
B. Switch
C. Load balancer
D. Firewall
3. Which type of device is used to provide network protection and security by preventing hosts from connecting to the organization’s infrastructure unless they meet certain criteria?
A. Switch
B. NAT device
C. Firewall
D. NAC device
4. You need to install a new network for a customer, and you are looking at different ways to design the perimeter network and entry points. You determine that you will need a firewall, border router, and two separate network segments off of the firewall for Internet-accessible servers. Which one of the following architectures best describes your network design?
A. Bastion host
B. VLAN
C. DMZ
D. Subnetwork
5. Which of the following statements is true about subnetting?
A. Adding network bits to the subnet mask creates more networks but fewer hosts.
B. Adding network bits to the subnet mask creates more networks and hosts.
C. Adding host bits to the subnet masks creates more networks but fewer hosts.
D. Adding host bits to the subnet masks creates more hosts and networks.
6. All of the following characteristics describe VLANs, except:
A. VLANs require routing between them.
B. VLANs separate hosts into logical networks.
C. VLANs can be used to apply security policies and filtering to different segments.
D. VLANs allow any host plugged into the switch to become a member of the virtual segment.
7. Which of the following allows you to map a single public IP address to a pool of private IP addresses?
A. Virtual LAN
B. Port Address Translation
C. Network Access Control
D. Static NAT
8. One of your coworkers has recently reconfigured the firewall rule set, and users immediately began to report that they cannot receive any traffic at all from the Web. You examine the firewall rule set for issues. Which of the following could be considered a likely issue that would prevent all traffic from passing through the firewall?
A. Implicit deny
B. Explicit allow at the bottom of the rule set
C. Explicit deny at the top of the rule set
D. Implicit allow at the top of the rule set
9. Which of the following would be needed to block excessive traffic from a particular protocol?
A. Flood guard
B. Loop protection
C. ACL
D. 802.1X
10. Which of the following issues must be addressed in any remote access method or technology? (Choose two.)
A. Encryption
B. Loop protection
C. Authentication
D. Traffic flooding
Answers
1. B. Ingress filtering is used to control traffic entering a network.
2. A. A router is used to send traffic to different physical networks, based upon logical addressing.
3. D. A Network Access Control (NAC) device is used to provide network protection and security by preventing hosts from connecting to the organization’s infrastructure unless they meet certain criteria.
4. C. In this scenario, a demilitarized zone (DMZ) is the best architecture to meet your requirements.
5. A. Adding network bits to the subnet mask creates more networks but fewer hosts.
6. D. VLANs do not allow any hosts plugged into the switch to automatically become a member of the virtual segment; membership is based upon switch port, MAC address, or IP address.
7. B. Port Address Translation allows you to map a single public IP address to a pool of private IP addresses, based upon the source ports of the internal hosts.
8. C. An explicit deny at the top of the rule set would cause all traffic flowing through the firewall to be denied.
9. A. A flood guard is used to block excessive traffic from a particular protocol.
10. A, C. Both encryption and authentication issues must be addressed in any remote access method or technology.