MODULE 35
Mobile Security
Mobile devices have become as common in our daily lives as pairs of pants. Everybody has at least one, and most people have more than one. In fact, many people seem to be unable to function without their mobile devices, which includes smartphones, laptops, and tablets. Many people also use other highly specialized mobile devices on a daily basis, including global positioning system (GPS) devices, game consoles, headphones, media players, and so on. Given the ever-increasing speeds and bandwidth of the Internet providers, and the wide range of applications that are being developed for mobile devices every day, it’s no wonder that these devices have become the world’s most important way to connect.
The corporate world has also experienced the invasion of mobile devices. These days, desktop processing capabilities and mobile device capabilities have pretty much evened out. Employees are experiencing a new way of operating by using mobile devices to perform productive work, instead of using them only for games, chatting with people, posting pictures, and so forth. Applications are being rapidly developed for mobile devices with serious business functionality and use. Because of this, the adoption of mobile devices into the business infrastructure has been rapidly increasing for a few years.
In this module, we’ll look at how this rapid influx of mobile devices directly affects the security of business infrastructures. We’ll take a look at security characteristics and issues with mobile devices and discuss the ramifications of a new business paradigm called bring your own device (BYOD).
Mobile Devices in the Business World
When so-called “smart” devices first started rapidly entering the consumer market, they were all the rage because they allowed users to communicate rapidly with friends and family, using not only typical voice communications through the smartphone, but also by using social media sites, sharing photos and videos, using text and chat messages, and so on. They also became the ubiquitous computing platform, replacing traditional desktops and laptops to a large degree, enabling users to play games, manage their finances, dictate short documents, and perform other tasks. The problem was, however, that users expected to see the same cool wide-ranging functions on their work computers as well, but the business world hadn’t caught up with the mobile device app explosion. As a result, many users started bringing their devices to work, most of the time without management approval, and doing company work on them. Figure 35-1 shows examples of some of the personal mobile devices that tend to wander into the office from time to time.
Figure 35-1 Personal mobile devices that tend to show up at work (photo courtesy of Sarah McNeill Photography, used with permission)
That’s all changed now, of course, as businesses are rapidly adopting mobile devices into their infrastructures. Businesses now issue smartphones and tablets to employees, provide for their communications links and Internet services, and allow employees to use these devices to perform work functions—and, in some cases, even do some of their personal stuff on them.
Unfortunately, with any new technology or change in the business infrastructure, security issues are a concern. Sometimes technology gets implemented so fast that security isn’t considered a real issue, and the main focus is on how much stuff the device can do—in other words, the focus is on the functionality of the device or technology rather than on security. However, with the infiltration of mobile devices into the business world, security is becoming more important. Developers and engineers, business managers, and even users to a certain degree are all a lot more security conscious than they were 10 years ago. So as mobile devices have entered the workforce, more attention is being paid to security in developing the devices and their operating systems and applications, as well as securely using them to protect both company and personal data.
In the next few sections, we’ll look at some of security features that mobile devices offer, and how they can be integrated into the corporate infrastructure and networks. We’ll also take a look at the issues that are prevalent when integrating an employee’s personal device with the business network.
Mobile Security Concepts and Technologies
As mentioned, security has become a lot more important over the past several years as engineers and developers create new technologies. Businesses are also more security conscious and are balancing security with functionality and resources a great deal more than they used to. In the past, as new technologies were invented and introduced into the infrastructure, the main focus was on how to make it work and get the most bang for the buck in terms of functionality. Unfortunately, a lack of security focus resulted in a lot of unsecure devices, systems, operating systems, applications, and so on, leading to problems with unauthorized data access and loss. Users also wanted more and more functionality out of devices—they just wanted them to do more “stuff.”
As we became more security conscious as a society, both end users and the people who develop and implement these technologies began to strike a better balance between security and functionality. The mobile device revolution is a good example of a technology introduced both into the consumer and business markets with far better security features than desktop counterparts were 20 or 30 years ago. Mobile devices and technologies come with built-in security features that can go a long way in securing personal and company data, provided they are used properly and integrated with other security measures in the corporate infrastructure.
This part of the module will focus first on company goals regarding securing mobile devices and then on the end user device security measures that are in place on most mobile devices. Companies can make use of these end user device features to enable security for the device and the user.
Mobile Device Management
Mobile device management (MDM) is a relatively new process in the business infrastructure, in which the company can bring mobile devices under the umbrella of their existing end user device management, just as they would for traditional desktops and laptops. The goal is central management of all the devices that connect to a company’s network—not just the devices that are tied to a desk and don’t walk out of the office in someone’s pocket. Many considerations go into MDM, including the wide variety of vendors, platforms, operating systems, applications, features, and even telecom providers for these devices. Unless the business standardizes on one particular vendor or platform, it can be a challenge to manage all of these different devices.
Fortunately, as devices and technologies have matured, common standards have evolved to enable businesses to manage all these different devices centrally, regardless of vendor, operating system, or platform. MDM includes all of the infrastructure devices, software, and even management programs that enable a business to manage all devices that connect within its network, including everything that happens on a device—the applications that run on it, the data that’s processed on it, and the different actions the users can take on it. MDM can integrate with the organization’s existing network infrastructure and make use of the standard network services the company provides for desktops, servers, network devices, and so on. The services include, of course, firewall and proxy servers, Dynamic Host Configuration Protocol (DHCP) and Domain Name System (DNS), centralized authentication through Active Directory or another Lightweight Directory Access Protocol (LDAP) type of method, and so on. Essentially, through MDM, a business can manage a mobile device using the same technologies and methods used for traditional desktops and get the same level of control. Figure 35-2 shows an example of a basic MDM software user interface.
Figure 35-2 Basic MDM software
Inventory Control and Asset Tracking
One of the great things about using mobile devices in the business is that they are mobile and can be used anywhere. Unfortunately, however, that means that the devices don’t always reside on the company property. They walk off with the user, so the company often doesn’t know exactly where they are and what they’re being used for, or even who’s using them. As with traditional desktops, inventory control is important with mobile devices, perhaps more important, since they are portable. Several technologies make it easier to manage mobile devices, even when they are off the company campus.
Although many of these technologies will be discussed later when we get into device-specific security methods, none of them can be implemented really well unless they are part of an overall MDM infrastructure. MDM allows for the centralized control of devices, including inventory control, so not only do you always know where the device is, but in many cases, you know which authorized users have control over it. Since mobile devices tend to talk to the MDM infrastructure often, you can have an almost 100 percent real-time inventory of your mobile devices at your fingertips via the MDM software. Of course, the traditional method of having a user bring the device to you or going to the office to scan it with a barcode reader can also make sure that you know the device is safely checked in or out.
Along with inventory control, asset tracking is important. Asset tracking means knowing where your devices are at all times, who has them, and what they are being used for. Asset tracking can be provided through the MDM infrastructure as well as via the device—such as GPS and other location-based services, as well as software agents that can be placed on the devices when they come under management control. Combined with strong security policies applied to mobile devices through MDM, asset tracking can provide visibility into what’s happening with these devices at all times. Figure 35-3 illustrates how location services can show you the exact location of a device.
Figure 35-3 Location services make it easier to track mobile device assets.
Device Access Control
Yet another management goal of business when integrating mobile devices into its networks is controlling what data, systems, and resources the mobile device connects to and accesses. Obviously, as with any other device or user, the goal is to make sure that people using mobile devices can access only the data and systems they need to do their job, and no more. Traditional access controls can and should definitely be used, which include restrictive rights, permissions, and privileges. These can be implemented at the resource level, such as assigning permissions to a folder or file, but they can also be implemented at the network level. For example, modern mobile devices can use strong authentication mechanisms, such as certificate-based authentication, which can be integrated with your network’s directory services, such as Active Directory. This can prevent an unauthorized user from stealing a mobile device and attempting to connect to your network and access your resources. Other traditional methods of access control that can be used in conjunction with mobile devices include firewalls, network access control devices, and so on.
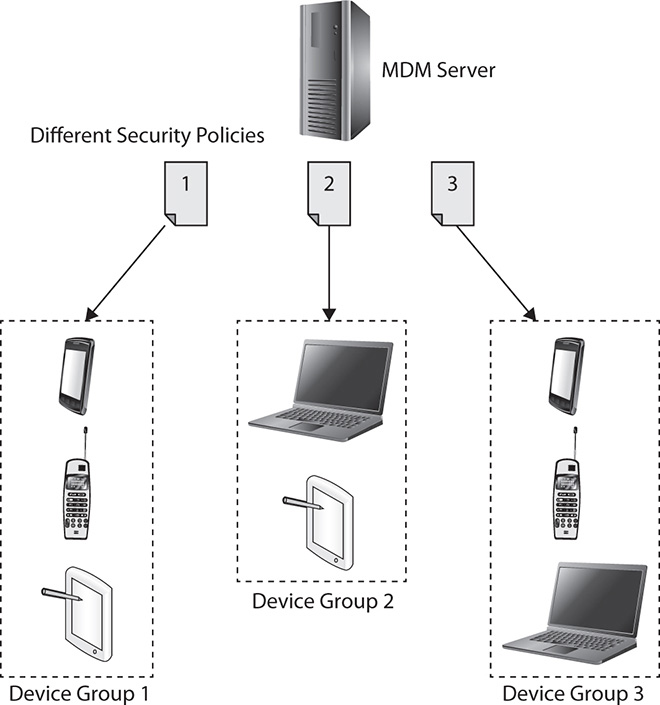
On the flip side of device access control, in addition to the desire to control access to network resources within the business perimeter, most administrators also want to control what a device can access and do when it leaves the company network. This can be harder to control, of course, since the device is no longer under the physical or logical control of the company. It may connect to unsecure home or hotel networks, for example, or to unsecure free Wi-Fi networks that have no required authentication or encryption. These are challenges when trying to control devices remotely and control what they can access off site. Fortunately, MDM security policies can be applied to the device to control access to certain content, applications, as well as Internet sites. These policies prevent users from doing things or accessing content that’s prohibited by the company. Figure 35-4 illustrates how this works.
Figure 35-4 MDM can push security configuration and policies to all of your mobile devices in the enterprise.
Geotagging
Geotagging is the process of including metadata in a file, such as a picture, video, e-mail, or other type of message that contains the location information of the device when the file was created or processed. For example, people often take pictures and geotag them with location information, which might include the GPS coordinates, time and date stamps, and other types of information, to include a description of an event. Geotagging is useful from several perspectives in the corporate environment. For example, a forensics analysis of a device could include looking at geotag information in the file metadata so the investigator might determine patterns of where the device has been and how it has been used. Geotagging also may serve a purpose in verifying the time, date, and location of an employee who performs a certain action, which may be required for compliance or policy reasons.
The use of geotagging in tracking employees and their activities must be carefully considered, however, in environments where users are allowed to process corporate data on their own personal devices. As with all personal data, geotagging can give away information that an employee might not want the company to have, especially if it involves information of a personal nature. We’ll discuss that particular environment later in the module. As with all the other issues we’ve discussed, geotagging should be addressed in policy documents, as well as the technical configuration of mobile devices.
Remote Management
Remote management is the key to protecting data in the corporate infrastructure. As mentioned, once the device leaves company property, it’s difficult to control it—that is, unless remote management capabilities have been installed and configured. This requires the MDM software to be configured properly, as well as settings on the device itself. Remote management enables a business to reach out and touch the device to monitor its location and use, as well as to protect data in the event the device is lost or stolen. You need to be aware of a few different remote management functions for the Security+ exam, as well as for use on the job.
Remote wiping is a capability you should use in the event a device is lost or stolen and is not likely to be recovered. In this scenario, the MDM software would enable you to send commands to the device that will completely wipe its storage areas, erasing sensitive data, configuration, and so on. Wiping the device could effectively render it useless, or at least reset it back to factory conditions. Before implementing device wiping, it’s a good idea to implement some sort of routine device backup strategy, because once the device is wiped, you will likely never recover that data again unless it has been backed up. If there’s no backup, you may have saved the data from being accessed, but that critical data is lost forever.
Remote control is another security feature that can be enabled on the device through MDM software. You can use this feature to take over the device if a user can’t figure out how to do something, of course, but a more useful security feature might be to take control of the device to prevent its misuse or to extract data from it before it’s wiped. You can also remotely unlock a device using this feature if the user has forgotten a passcode and doesn’t want to keep typing it in and risk wiping the device after several incorrect entries.
Onboarding/Offboarding
Managing mobile devices starts with the processes the organization uses in onboarding and off-boarding mobile devices. Onboarding encompasses all of the processes used to introduce a new mobile device into the network, as well as assignment to the user. This includes provisioning the device to ensure that the device has the right settings to access the mobile service provider or telecom provider, as well as installing all of the company-approved applications on the device. Provisioning also entails making sure the right user permissions and accesses are installed on the device, such as usernames and passwords, digital certificates, and so on. The point of onboarding and provisioning a device is to make sure that the device is fully functional so that a user can use it to process company data.
Offboarding, as you might guess, is almost the exact opposite of onboarding and provisioning. During offboarding, the device is collected from the user, and access to the network with this device is taken away. In an orderly offboarding process, user data is removed from the device and, if applicable, returned to the user. Corporate data is also removed from the device and stored or disposed of as appropriate. The device might be decommissioned completely, removing it from inventory and disposing of it, in the case of legacy devices or devices that no longer function properly. If the device is not disposed of, it might be reused within the enterprise and issued to another user; in that event it would go through the onboarding and provisioning process again (although it may not require as much in terms of device activation, and so on). If the device has been collected from the user based upon a violation of policy or the law, the device might also be subject to forensics analysis and examination, as well as retention of any personal and corporate data on the device. In any event, a process should be established within the organization for both onboarding and offboarding mobile devices securely.
Application Control and Security
Application control means that the organization determines what applications can be installed and used on the mobile device, as well as where it gets those applications from. The organization can impose technical policies on devices that prohibit them from downloading applications from certain app stores, for example, and restrict them to downloading applications only from the internal company app repository or a specific vendor or platform app stores.
Application control also means exercising control over what apps can do on the device, as well as what data they can access. For example, an organization can use certain methods to prevent a user’s personal app from accessing any corporate data stored on the device. These methods may include restricting copy and paste operations, restricting a user’s personal e-mail app from accessing the corporate e-mail’s contacts list, and other controls. Application control can be imposed on the device using different technical policies, as well as tight control over user rights and privileges on the device. Other methods, such as sandboxing and containerization (which we’ll talk about a bit later) can be used to separate applications and data from each other so that no interaction is possible between them.
Application Security
The organization should exert some sort of control over the security of the applications themselves, simply because there may be security and interoperability issues with all the different apps on mobile devices. Some of these applications may not exactly work well with company-approved enterprise applications, and some of these apps may not store, process, or transmit sensitive data securely. The organization may want to control which types of apps can be installed and used on mobile devices, using either MDM or mobile application management (MAM) technologies. The company may also want to set up its own app store, rather than allowing users to download apps from a vendor’s app store.
Application Whitelisting
In application whitelisting, the organization allows only certain trusted applications to be installed on mobile devices. Certain applications may be excluded due to security, interoperability, or even licensing issues. Applications that are acceptable in the organization might include secure e-mail applications, file transfer applications, and productivity applications. Whitelisting allows the organization to include accepted applications in policy configuration files that are sent to and maintained on the mobile device. These policies may prevent a user from downloading and using unapproved apps or from using certain vendor app stores. Often, secure configuration files for these apps are also included for an app when the device is provisioned.
Encryption and Authentication
Using encryption on mobile devices can protect data while it is stored on the device, or during transmission from the device back to the corporate network through untrusted networks, such as the Internet. Mobile devices can make use of encryption in various ways, including encrypting both internal and removable storage, and providing encryption for secure data exchange during file transfer and e-mail, for example. The key point about encryption is that, although most mobile devices support current encryption standards, the different levels of encryption, including algorithm and strength, as well as encryption negotiation methods, must be configured identically on both the device and the end point, such as a server or network device. If the two devices don’t have compatible encryption methods configured, neither will be able to send or receive information securely. In some cases, using different encryption methods may prevent them from communicating at all.
Authentication
You’ll remember from earlier discussions that the first step in the authentication process is for the user to identify herself, either through a username and password combination or through some other form of multifactor authentication means, such as a smartcard and pin, biometric thumbprint, and so on. Once the user has identified herself, the authentication process verifies and validates the user against a database of credentials. The user is authenticated only when the system can confirm that she is, in fact, the user that presented the identification to the system, and no one else.
Mobile devices use the same types of authentication systems and technologies that traditional desktops and server systems use. The catch is that they must be compatible with existing authentication systems, such as username and passwords (including length and complexity requirements), biometric methods, and digital certificates. Regardless of the authentication method used, mobile devices must support the different standards and protocols used in an enterprise authentication system. Most mobile devices built today, especially those that are typically seen in an enterprise environment, do support all of those authentication methods and technologies. The trick is to configure them properly through device and user provisioning to get the correct authentication methods and other security configuration settings installed on the device. Beyond that, normal considerations with access control and user authentication are typically the same as with traditional devices. This means accounts have to be properly issued, users have to be trained on secure identification and authentication processes, troubleshooting has to happen when users can’t authenticate to the enterprise, and so on. Supporting the authentication process is the process of managing a user’s credentials, including username, password, and even the cryptographic keys associated with digital identities. These topics are covered next.
Credential and Key Management
Credential management involves all of the processes and technologies involved with provisioning and maintaining user accounts and credentials. This usually includes account provisioning, creating secure passwords for users, and ensuring that passwords are managed throughout their lifecycle (including password changes, compromise, and so on). Credential management also may involve issuing and managing digital identities, which are commonly associated with digital certificates and cryptographic keys. This might entail establishing and using a public key infrastructure (PKI) within the organization. All credentials to all the different systems in an organization might be managed by a central authority, such as an account management section or even the helpdesk. There might need to be different credentials for different users based upon differing roles and responsibilities, or even based upon disparate systems that don’t communicate authentication information to each other. In the event that different systems within the organization can use the same authentication systems and identities, password synchronization and Single Sign-On (SSO) capability must be considered and managed appropriately. If authentication systems cross business or organizational boundaries, federated identities may be considered and managed to facilitate those needs.
Key management refers to the ability of the organization to manage cryptographic keys—the digital certificates and keys that people use to authenticate to corporate systems. These digital certificates could be used for e-mail authentication, digital signatures, and encryption, and to ensure data integrity within the organization. Key management involves managing the lifecycle of cryptographic keys from their creation through their destruction, and all of the use that occurs with them in between. Digital identities must be securely issued to users by confirming their identities, setting them up for the proper usage, installing them on mobile devices, and troubleshooting any issues with them. Between the events of key creation and destruction, cryptographic keys may also be subject to reissue, suspension, revocation, and renewal. All of these processes require that the organization have a stable certificate management process installed, even before the introduction of mobile devices into the business environment. Digital identities may be installed on mobile devices to enable secure access of corporate e-mail and other sensitive resources. Because of the mobile nature of these devices, and the possibility of device loss or theft, it’s also very important that an organization has the processes in place to suspend or revoke cryptographic keys quickly and their associated digital identities if needed.
Transitive Trusts and Authentication
Along the same lines as secure authentication, trust relationships affect the secure authentication to systems that don’t necessarily use the same types of authentication methods and technologies, or to systems that aren’t within the control of the organization’s security domain. For these types of systems, trust relationships have to be established that may enable pass-through authentication, SSO authentication, or even federated identities that are shared among business entities. This might be the case if a mobile device needs to authenticate to a business partner’s system or to a public network, such as a telecommunications provider’s network. Trust relationships can also affect how mobile users authenticate back to their own corporate network; the trust relationship, along with the associated credentials, may have to be provisioned on the device so that the corporate network would trust the device and allow the user to authenticate.
Device Security
Now that we’ve talked about a few of the main security goals from a corporate perspective, let’s talk about some of the device-specific security measures that can help ensure that sensitive data is protected. Some of these measures are already included on the device and can be quite effective when used by themselves, and others are effective only when integrated into the corporate MDM infrastructure. All measures are used to protect the device and its data from unauthorized access and loss.
Screen Lock and Device Lockout
A screen lock enables the user to manually lock access to the device from anyone, unless the person inputs the correct passcode or pin. While the screen lock is engaged, the device may have only very limited functions, including the ability to make an emergency phone call or advance tracks if some sort of media file is playing on the device. In any event, more advanced operations and data access are prevented while the screen lock is engaged. In addition to being manually engaged by the user, screens can be configured to be locked after a certain amount of inactivity on the device—3 minutes, for example. This prevents unauthorized access to the device if the user lays it down or someone grabs it while the user is still logged in.
Device lockout occurs when the device prevents someone from accessing it because the person has incorrectly entered the password or pin too many times. If this is a valid user, and he has simply forgotten his passcode, lockout features can take different actions. First, the user might simply be locked out of the device for a specified period of time, giving him enough time to contact the company and either obtain the correct passcode or have an administrator remotely unlock the device. Lockouts can also be more drastic, such as wiping the device after a certain amount of incorrect passcode entries. More advanced features may include having a device remotely contact the administrator if it has been locked out.
Full Device Encryption
Full device encryption protects all the data on a mobile device. With this security feature, the storage device itself, such as the device’s internal hard drive, is fully encrypted and can’t be used unless it’s decrypted when the device is powered up. In some cases, you could set full device encryption to require a passcode or passphrase on startup, before the user even logs on. In other cases, you could also make sure that the device storage can’t be accessed periodically, even while it’s on without the user reauthenticating occasionally.
In addition to encrypting the device on startup, you might also configure it to fully encrypt the drive whenever an incorrect passcode or passphrase has been entered to unlock the screen after so many tries. This is used to protect the device in case it is lost or stolen and still powered up. This can keep someone from connecting the device via a cable to a computer in order to access the storage areas as they would an external drive. Full device encryption should be set up when the device is first issued or purchased; until it’s actually turned on and configured on the device, it’s of no use if the device is lost or stolen, unless it can be activated remotely.
GPS Services
All mobile devices have certain built-in technologies and functions to help determine their precise location and provide location-based services to the users. The most common technology is GPS. Today, GPS receivers are built into almost every mobile device. In addition to typical user services, such as finding the nearest restaurant or gas station, location-based services using GPS can assist network administrators in managing mobile devices in the enterprise in several different ways. First, they can use GPS to help maintain an accurate location fix on the device. This might be necessary if the organization wants to ensure that devices are used only in certain areas or tracked by location. These same services can also be used to help the network administrator maintain a fix on the device if it gets lost or stolen. Another use of GPS and location-based services is to ensure that the device remains on company property, a practice called geofencing. Geofencing ensures that a mobile device stays within a preset perimeter established by the administrator, using MDM software. If the device leaves the company property or gets beyond this perimeter, it will send an alert to the administrator. In addition to GPS, mobile devices can also use Wi-Fi networks to ascertain their location information, although this isn’t as accurate.
Storage Segmentation
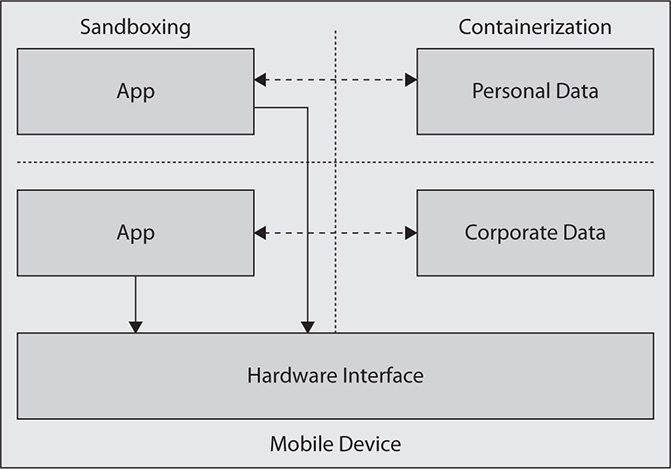
Storage segmentation is the practice of partitioning off storage areas in the device, usually to provide separate areas for company or sensitive data and personal data. Through storage segmentation, it’s possible to impose different access controls on specific types of data. This is related to the concepts of sandboxing and data containerization, techniques used to ensure that apps on a mobile device do not access each other’s data or storage areas, keeping them separate. Figure 35-5 describes the concepts of sandboxing and containerization. Storage segmentation can be imposed on the device’s built-in storage area or on removable media as well.
Figure 35-5 Sandboxing and containerization are used to separate apps and data from each other.
Removable Storage
Speaking of removable storage, most mobile devices made today can accept different types of removable media, such as Secure Digital (SD) cards or their smaller counterparts, mini- and micro-SD cards. These cards are used to store additional data to help prevent using up all of the device’s primary storage. In the enterprise, removable storage media can be used in different ways. First, through MDM policy, removable storage media could be used to store all of the user’s personal data, versus corporate data. This way, when the device is returned to the network administrator, all she has to do is remove the SD card that contains the personal data. A business can also do the exact opposite and allow only corporate data to be stored on the removable media. That way, when the device leaves the company property, the removable media could be stored on site, reducing the risk of data loss when the device is out of the company’s physical control. In either situation, data could be encrypted on the removable media, so that if it’s removed from the device, it can’t be accessed.
Disabling Unused Features
From your experience in securing user desktops in the organization, you probably already know that one of the best security practices you can use is to disable any unused features, services, ports, protocols, and so on, because doing so reduces the computer’s attack surface. For example, if the user is only typing e-mails, surfing the web, and so forth, he probably has no need for applications or services on the box that might allow him to perform administrative actions on the network. Likewise, the server running the company’s web page probably doesn’t need to have e-mail services running on it. In any case, the same is true with mobile devices.
Depending largely on what the business’s security policy states, users may not need to have certain services running on their mobile devices. They also may not need to use some of the native apps that come on some mobile devices, such as smartphones. This might include third-party or free e-mail programs, chat programs, games, and so on. Through MDM policy, as well as MAM, you can limit what applications and services a user can access and use on a mobile device. Of course, this may not make you very popular with the employees in the company, but it will go a long way toward helping to secure mobile devices that connect to your network.
BYOD Concerns
At some point, consumers became so enthralled and obsessed with their mobile devices that they decided they couldn’t live without them. For some strange reason, this hadn’t happened a few years before when most people acquired desktop systems. They certainly didn’t start bringing their own desktop systems to the office, of course, because of the mobility issue (or lack thereof). However, once “smart” devices became the norm, Internet speeds became quick, Facebook was invented, and people could play music and movies on their phones, that all changed. They suddenly became addicted to their phones and all the functionality that mobile devices could provide, so they started taking them to work. Unfortunately, it became difficult for users (and administrators) to keep personal stuff separate from corporate work and data on mobile devices. Users check their e-mail on their own devices, they copy files to and from their own devices to the company network, and so on. After fighting this for a few years, many businesses finally gave up and eventually allowed users to bring their own mobile devices into the walls of the business, and in some cases, even allowed them to join the corporate network. Thus the paradigm of BYOD was born.
With this new shift came a whole bucket of issues with concerns over company data loss and theft, introducing malware and unauthorized data into the corporate network, and how much control the company had over data stored on devices that belonged to employees. There were also concerns over the employees’ data privacy and rightful use of the device. The next few sections discuss issues and concerns with BYOD and how they might be solved.
Data Ownership
So, if I bring a personal device to work and my music, videos, e-mails, text messages, and other personal information are stored there, and I decide to put corporate data on it and process it using different apps, e-mail, and so forth, how much ownership does the company have over my device? It’s actually a hugely difficult question that a lot of companies have had to face in the wake of the BYOD revolution. Because the device belongs to an individual, does the company have the right to erase the device remotely, or even manage it at all, in the event it is lost or stolen? Would using your own device to process corporate data actually mean that the company might even own your private data as well? These types of questions can be answered when creating company mobile device security policies.
The organization has to determine to what extent it will allow personal mobile devices used in its network, what rights to manage the device and the data it contains the company can exercise, and what rights to device use and privacy the employee has. If all of this is decided up front, and expressed in a formal policy, then there’s a clear line on data ownership and use with regard to personal mobile devices. At that point, the user can accept the policy and allow the company to manage her device and the data on it, or not accept it and keep the device at home.
Fortunately, in addition to security policies that spell out all of this, there are also technologies that can help enforce these policies. If the user agrees to have the device managed through MDM, and the device supports it, then technologies such as sandboxing and data containerization can help separate corporate from personal data. This would allow the organization to manage only its data, while keeping the user’s personal data separate. Of course, this may not solve other issues, such as the ability to wipe a device remotely if it’s lost or stolen, or decisions on use of the device in certain circumstances. Some of these circumstances may include surfing to prohibited sites that the organization doesn’t allow, or installing and using apps that are not approved by the organization.
Support Ownership
Another issue that comes up often in BYOD situations is the issue of support ownership. If the user brings a personal smartphone into work and uses it to perform company functions or business, who pays the bill? Often companies will provide a small sum of money, or stipend, to an employee who is authorized to perform company business on her phone in order to offset the monthly service charges. A company could also agree to pay the entire amount of the service fee, under certain conditions, or even the insurance on the device if it’s broken or lost. Some companies even have discount programs and agreements with telecommunications providers. In any event, the company may require a detailed copy of the bill to separate expenses incurred by the employee when doing business, and those the employee should pay for. Again, policy can help determine these things up front to help avoid any surprises for the business or the employee.
Patch Management
In a BYOD environment, patch management can be problematic as well. The user may never patch his device, or he may allow it to sync with the vendor for application or operating system upgrades whenever they are available. The company, on the other hand, may require that all mobile devices be kept at a certain patch level, for security as well as interoperability reasons. Part of the company policy on BYOD should address the user’s responsibilities for patch management, even on a personally owned device. The company may require a certain patch level but also may require that the user bring the device in to work to be patched by the network administrator for specific apps or operating system upgrades. The business may also want to restrict certain patches from being applied to mobile devices that could break certain applications, rendering them nonfunctional.
Antivirus Management
Yet another concern in the BYOD environment is use of antivirus software on mobile devices. Perhaps a user doesn’t want to use antivirus at all, or she may want to use a different antivirus software that’s not the company standard, or she may not update the signatures as often as she should. Again, company policy should address this issue. If the company has a specific antivirus solution already licensed and purchased for its mobile devices, then the user may gladly accept it, particularly if it’s centrally managed and doesn’t require the user to do anything to keep it updated.
Privacy
Now we’ve come to the largest issue in the BYOD problem—the issue of privacy. Many people feel that individual privacy might be incompatible with using a personally owned device to store and process company-sensitive data. This is because, realistically, the company may have the legal right and responsibility to protect any company data on the device. This entails being able to centrally manage the device, which also leads to the company being able to view and access any personal data on it. The mantra of “if you’re not doing anything wrong, then you don’t have anything to hide” doesn’t necessarily apply here. This is because people use mobile devices for all manner of personal things, such as calling and texting loved ones, storing and accessing financial data, viewing legally protected political or religious material, and even accessing content that, although not necessarily within the guidelines of company policy, is still perfectly legal for private individuals to view. With all this in mind, most people probably wouldn’t want arbitrary intrusions by their employers into their personal world stored on their mobile device. For example, what if you kept a record of your doctor visits on your smartphone? Would you really want a network administrator getting that information and letting the HR folks know, possibly prompting them to question your health or even causing your insurance rates to go up? Another example might be if you are receiving e-mails from a competing company on your personal account when you’re negotiating for a job there. You probably wouldn’t want your company finding out that piece of information and letting your boss know!
In any case, privacy is a serious issue to consider when bringing personally owned mobile devices into the company network. Like all the other issues we’ve discussed so far, company policy on the expectation of privacy is a good starting place. The company may decide that the user has no expectation of privacy on his own device, and if this is the policy that the user agrees to, then so be it. However, based on this policy, the user could simply choose not to use the device in conjunction with work. Depending upon the technologies the company has available to it, it could also adopt a less draconian policy and permit privacy on the device, provided there is some sort of data separation technology in place, so the company could control sensitive data it owns. The company policy could also state that the user has every expectation of privacy on his or her own device. This would be a very lenient and open way to approach the problem, but could result in a lack of control over the device and could ultimately lead to data loss or disclosure. The point is that both the organization and any users wishing to use their own devices for work must agree up front on how privacy will be approached and dealt with.
Other Security Concerns
In addition to the security concerns mentioned previously with BYOD, are other, more general concerns that affect the organization, regardless of whether the mobile devices used throughout the company are personally or corporately owned. In some cases, the concerns are more pronounced if the devices belong to the employee, but they are still relevant even for devices the company has bought and issued to employees. Some of these concerns involve legal matters, such as privacy, forensics, and the users’ acceptance of and adherence to policies. Other concerns are from a broader perspective and affect how mobile devices interact with the existing corporate infrastructure, in terms of both security and interoperability. Finally, there are concerns with the use of mobile device cameras and onboard video capabilities in sensitive areas and with regard to the privacy of fellow employees. We’ll take a look at each of these potential issues in the following sections.
Legal Concerns
There are several different legal concerns involving the use of mobile devices in the corporate infrastructure. First, as with all end user devices, rules must be set up so that users know what they are required to do (and not allowed to do) with these devices, both when connected to the corporate network and even when disconnected from it. These rules, established in the form of policies, come from both legal requirements (the law) and corporate governance. Violation of any of these policies or laws could result in either criminal or civil liabilities or charges against not only the individual users, but the business itself. This is definitely true of company-issued devices and their misuse, but it could also be true of personally owned devices that the company has permitted employees to bring into the corporate environment. Legal concerns with these devices include privacy, data sensitivity and access, forensics, and acceptable use.
Forensics
Mobile device forensics is a fairly new field, although it borrows a lot of techniques and procedures from traditional computer forensics. Many mobile devices require specific software to retrieve data from them and may require the devices to be connected to a forensics collection or analysis workstation to get the right data from them. Unfortunately, forensics is often driven by investigations, which may involve the user who owns the device that’s being investigated. This could become an issue if, for example, the company does not want the user to know she is being investigated, but the company need to perform a forensics analysis on her mobile device. It also may be an issue if the user is not required by any enforceable regulation or law to surrender the device to the organization. Policy may dictate the procedures in these cases, but this may be a requirement that isn’t easily enforceable on the user. In some cases, remote forensics could be conducted for devices that fall under MDM.
User Acceptance and Adherence to Corporate Policies
Whether a user has brought his own device used in the network, or he’s been issued a device purchased by the company, it should be treated like any other piece of equipment used to access the corporate network. Users should be bound by the corporate policies addressing authorized system and data access, care of equipment, acceptable use, and so on. Obviously, policies are the first step in this process; users must be able to read, understand, and obey well-written and firmly enforced policies set up by the organization. Policies must also be translated into technical configuration details that are imposed on the corporate network in the mobile devices to ensure adherence to security policies.
User acceptance of the corporate rules for mobile devices is necessary in order for the policies to work; if the user is presented with a policy, he doesn’t necessarily have to accept it, but he may not be able to use his personal mobile devices on the network, or he may not be issued any device that the company has issued. In the event the user refuses to accept corporate policies as they pertain to personal devices, then the alternative is simply for the user not to be allowed to bring and use personal devices to work, at least for work purposes. If the user refuses to accept or continually violates policies that are imposed on corporate-owned devices, then he should be subject to disciplinary action or the possibility of having corporate devices taken away from him. This could impede his work significantly, and in some cases may even render him ineligible to perform a certain job (such as a position that requires the user be available 24/7 for on-call work, or a sales position where the employee is constantly on the road).
Acceptable Use Policy
Acceptable use comes from the business’s desire to maintain compliance with laws and corporate policies on what users may and may not do using mobile devices and the company network infrastructure. An acceptable use policy normally covers items such as Internet access, data use and access, disclosure of any sensitive data to unauthorized parties, use of unauthorized software on mobile devices, and possibly the use of social media, and access of certain content (pornography, pirated music files, and so on). All of these issues should be spelled out in the acceptable use policy and all apply to corporately owned devices. In certain circumstances, the policy could also apply to a user’s personally owned device, in the event she agrees to use it on the corporate network in accordance with the organization’s policies. Acceptable use policies should not only spell out the requirements of what a user can and can’t do, but also the consequences if the user violates the policies.
Architecture and Infrastructure Considerations
Several other considerations must be examined before introducing mobile devices into the corporate infrastructure. Security is, of course, a huge consideration, since any mobile devices and their associated network management equipment must be able to integrate securely with the network. You’ll have to make sure that any mobile device, as well as the related MDM equipment or network access devices, is compatible with security standards you use on the network. For example, mobile devices must be able to use particular levels of encryption or authentication in order to connect to the corporate network. MDM software and hardware must be able to smoothly manage mobile devices in conjunction with other network devices, such as firewalls and proxies.
Interoperability is another important consideration. Not only must mobile devices and associated equipment be able to operate securely within the network, but they must also work with existing network infrastructure from an interoperability perspective. They must use common protocols, services, data formats, and so on, to communicate efficiently with network servers and applications. Mobile app use should be compatible with any line-of-business applications used in the organization, since data will have to be processed on mobile devices and possibly passed on to network-based enterprise applications or databases, for example. In any event, security and interoperability are two important considerations when integrating mobile devices into the existing network infrastructure.
Onboard Camera and Video Concerns
Onboard cameras and video is another interesting security issue in the corporate environment. Since almost all mobile devices have some sort of built-in camera or video recorder, this can be an issue in the corporate environment with regard to using the device in sensitive areas or processing sensitive corporate information on the device. It can also be a privacy issue, in that people have the right to choose whether to be photographed or filmed in certain settings. With smartphone video capabilities being fairly ubiquitous, many employees, especially in sensitive areas, would not want to find that they are now the subject of a viral YouTube video, for example! Obviously, the company would probably not want this as well. In some highly sensitive data processing areas, cameras of any type are prohibited, meaning that smartphones, tablets, or other items the user might normally use to process company data on would have to be excluded from the areas in question.
The use of cameras and video recorders of any type, including those on mobile devices, should be addressed in security policies, to set rules on where and how they may be used, or even banning their use in certain areas and situations. The policy may simply require that they be turned off within the company property or certain secure areas, or it may state that mobile devices having cameras may not be brought into certain areas at all. Policy may also further state that any employee taking unauthorized pictures or videos of any persons or areas may be subject to having those devices confiscated and their video or pictures deleted from the device.
Module 35 Questions and Answers
Questions
1. Which of the following are ways that centralized mobile device management uses location services? (Choose two.)
A. Remote wiping
B. Asset tracking
C. Mobile application management
D. Asset inventory
2. Which of the following cannot be controlled through Mobile Device Management (MDM) software?
A. User applications
B. Content filtering
C. Security configuration
D. Device location
3. Which of the following involves including metadata in a file that embeds the location of the device when the file was created or processed?
A. Geofencing
B. Geotagging
C. Content filtering
D. Geocaching
4. Your manager wants you to include a configuration file in the MDM software that contains all of the mobile apps that are preapproved for use on the company’s mobile devices. Which of the following terms describes this practice?
A. Containerization
B. Sandboxing
C. Application whitelisting
D. Application blacklisting
5. You are trying to troubleshoot an issue with a mobile device authenticating to the network. The device seems to have issues with establishing a secure connection to the VPN server. Which of the following configuration items should be checked to ensure that the device is configured properly on both the mobile client and the VPN server?
A. Encryption settings
B. Username and password
C. Mobile device IP address
D. VPN server IP address
6. Which of the following are typical actions that could cause a device to be wiped? (Choose two.)
A. Detection of malware on the device
B. A user inputting an incorrect passcode too many times
C. An administrator issuing a remote command to wipe the device
D. Failure of a screen to unlock
7. Which of the following would enable an administrator to impose different access controls on different types of data residing on a mobile device?
A. Mobile application management
B. Storage segmentation
C. Geofencing
D. Application whitelisting
8. All of the following are valid BYOD concerns, except:
A. Privacy
B. Data ownership
C. Support ownership
D. Internet restrictions for company-provided devices
9. Which of the following types of policies dictates what users can and cannot do with mobile devices issued to the users by the company?
A. Access control policy
B. Data backup policy
C. Acceptable use policy
D. Equipment care and use policy
10. Which of the following device functions may be strictly limited when using mobile devices in certain sensitive areas?
A. Text messaging
B. Onboard camera and video
C. Personal e-mail
D. Incoming phone calls
Answers
1. B, D. Centralized mobile device management uses location services to enable asset tracking and inventory.
2. D. MDM can control all of these items except the location of the device itself.
3. B. Geotagging embeds metadata in a file that contains the location of the device when the file was created or processed.
4. C. Application whitelisting enables an administrator to configure mobile devices to use only approved apps.
5. A. The encryption settings used to establish a secure connection between a mobile device and the VPN server must be compatible on both devices.
6. B, C. A device can be remotely wiped by the administrator, or configured to initiate the wiping process after the passcode has been entered incorrectly too many times.
7. B. Storage segmentation would enable an administrator to impose different access controls on different types of data on a mobile device.
8. D. Internet restrictions are a valid concern, but not one specifically associated with BYOD, since the answer specifies that they are company-owned devices.
9. C. An acceptable use policy dictates what users can and cannot do with mobile devices issued to the users by the company.
10. B. Onboard camera and video functions may be restricted by policy when using mobile devices in sensitive areas.