MODULE 36
Social Engineering
You’ve learned about the technical aspects of security, and you’ve seen how technical measures, such as firewalls, encryption, strong authentication, and so forth, can all be used to secure data and systems. But what about the people who use and interact with the systems and data within the organization? What technical measures can you use to secure the system from human security issues? Is there a patch for being human? This module shifts gears and discusses the human element, focusing on human beings as a security weakness. In this module, we’ll look at the types of attacks that can take place when an attacker finds and exploits vulnerabilities in the “wetware”—the human being. We’ll also examine why these types of attacks are so effective.
Social Engineering Attacks
Earlier in the book, we looked at some of the different types of technical attacks that can be perpetrated against a system or network. In this module, we’ll look at attacks that can be perpetrated on humans. Since humans are social creatures, we call these social engineering attacks. Social engineering essentially means that an attacker or malicious person can use weaknesses inherent in all people in general to try to gain information about a network, a system, or even an entire organization. In some cases, the attacker can even get unsuspecting people to perform actions for him.
Human beings need to be social; we interact well as a species with each other, for the most part, and most human beings need that interaction. We want to be liked and to be helpful, we respect and fear authority, and so on. In some cases, our emotions, needs, desires, and opinions can be used against us by a malicious person who is adept at manipulating and influencing people. Over the next several sections, we’ll look at what the targets and goals of an attacker may be when using social engineering attacks, and we’ll take a look at some of these attacks in depth and how they are executed.
Targets and Goals
As with any type of technical or physical attack on an organization, an attacker will use social engineering to further his goals in gaining information, harming systems, infiltrating a network, and so on. The attack methodologies used by attackers when launching social engineering attacks aren’t much different from those used when launching technical attacks; the attacker simply has to do some reconnaissance, find vulnerabilities, and exploit those vulnerabilities. In the case of social engineering attacks, the vulnerabilities usually come from people associated with the organization, network, or system, or even from other people peripherally involved with the organization.
Social engineering targets can be anyone associated with the organization, at different levels or in different capacities, that the hacker can attempt to establish a relationship with, determine weak spots or vulnerabilities with, and then exploit those vulnerabilities. A target can be a system administrator, an executive, a maintenance person, an administrative assistant, or even a janitor. Even people who are loosely associated with the organization, such as occasional contractors, delivery personnel, and so on, can become targets of an attacker simply because they can offer an avenue of attack into the organization that may allow the attacker to connect with someone else who can get them deeper into the organization. Targets aren’t always contacted personally, although that may happen later in the relationship. Targets can be scoped out and initially approached through social media, e-mail, social gatherings, and other venues.
Usually an attacker will try to gather information about a target first, finding out things about the person, such as hobbies, likes and dislikes, work and personal habits, relationships with other people, and so forth. The attacker tries to gather this information to establish a relationship with the target, or at the very least to take advantage of some weakness in the way the person interacts with the organization. In some cases, this approach can be a positive experience for the target, such as when the social engineer wants to establish a friendly relationship. In other cases, the relationship can be quite negative, such as when the attacker discovers some embarrassing or damaging information and wants to blackmail the victim into doing some misdeed. In any case, there’s usually a reconnaissance phase before the attacker makes the actual approach and attack.
The attacker may have several goals, including getting past physical security in the organization, stealing information, getting physical access to a data center, and so on. An attacker will select a target that can get him closer to those goals. Often, the target of social engineering may just be a first or intermediate step in a series of attacks.
Types of Attacks
We’ll look at several different types of social engineering attacks, including the basic types that you’ll see on the Security+ exam. These attacks can range from the very simple to the very complex, and they may involve complicated scenarios or even multiple avenues of approach. You can probably use your imagination to come up with a dozen or more types of attacks or methods that a malicious social engineer would use to get what he wanted.
Shoulder Surfing
Shoulder surfing, an attack that is often undetected by the victim, involves the attacker inconspicuously looking over the victim’s shoulder at her computer screen to see what she is typing or seeing. This type of attack is usually one of opportunity; the attacker simply waits for the right moment to walk by the victim and take a look at what she is doing, or he invents a reason to engage the victim in conversation while he glances at the screen. The attacker can use this technique to steal user credentials, account numbers, and other sensitive information, although usually it’s only in small amounts due to the brief and unpredictable nature of the attack. Users can thwart these attacks simply by being cautious with overly curious passers-by. Figure 36-1 shows how simple—and productive—shoulder surfing can be for an attacker.
Figure 36-1 Shoulder surfing yields good results!
Dumpster Diving
Often, organizations throw away papers, CDs, and other types of materials they no longer need. These materials can contain sensitive information. Depending on the local laws and where the dumpster is located, it might be perfectly legal for a dumpster diver to climb into the container and dig out materials that have been tossed. If the dumpster is located within the confines of the organizational property, the dumpster diver could be charged with trespassing if caught. If, however, it’s located in a public area, there may be nothing the organization can do to stop a dumpster diver.
Dumpster diving can help someone gather all kinds of information about an organization from discarded telephone books, organizational charts, server and operating system manuals, contract documents, financial records, and other items. For example, if the company suddenly threw away a bunch of user manuals on an older version of Microsoft SQL Server, an attacker might assume that the company recently upgraded to the newest version, and that might give him an idea about what vulnerabilities the new version could have. Telephone directories and organizational charts can give an attacker insight into who works where, how important they are, who they work for, along with personal information, such as telephone numbers and e-mail addresses. Attackers can use all of this information to prepare and execute a social engineering attack on the organization’s personnel.
Dumpster diving attacks are reasonably easy to prevent; the organization can simply screen its trash and make sure that it shreds or recycles sensitive documents and media. Anything containing potentially sensitive information should be disposed of securely and not simply thrown into the dumpster. Additionally, the organization might want to install CCTVs or fences around its dumpsters and trash areas. In Figure 36-2, you can see an example of valuable information an attacker might find when dumpster diving.
Figure 36-2 Finding treasure in a dumpster
Tailgating
Tailgating is another simple social engineering attack. When an authorized person passes through a security checkpoint or door, an unauthorized person quickly walks in behind before the door closes. Or it could involve a little bit of creativity: the intruder, with arms full, could ask for help opening a door to get in. Social engineers have also been known to ride in wheelchairs, walk on crutches, or otherwise appear to be disadvantaged and unable to open a door or get through a security checkpoint without assistance. Positive identification and authentication using access badges and accounting for every single individual who comes through a checkpoint help to mitigate vulnerabilities associated with tailgating.
Impersonation
An intruder can pretend to be a valid network user, perhaps someone with higher privileges or status in the organization than the victim. The social engineer impersonates a valid user over e-mail, telephone, or social media and convinces the victim that he actually works in the organization. Obviously, this technique is effective only if the target doesn’t personally know the user being impersonated. The victim may have heard of the impersonated user in the course of business or may have seen his name on an organizational chart. This technique is also used with others to perpetrate a more believable attack.
Hoaxes
We’ve all probably received the e-mails stating that little Timmy is dying of a serious disease and wants his e-mail forwarded to 10,000 people, or that Bill Gates is giving away his fortune and you can receive a part of it if you forward the e-mail to 10 of your friends. You’ve probably also seen e-mails asking you to provide bank account information so that a deposed prince or forgotten relative can deposit millions of dollars into your bank account to save their fortune. These are, of course, hoax e-mails, and they usually merely waste the recipients’ time, increase e-mail traffic in the organization, and cause a nuisance. Occasionally, however, hoaxes can be used to carry out more serious, sophisticated attacks. For example, a chain e-mail hoax could also have a virus attached to it, and by forwarding it to 10 friends, you are, in fact, spreading the virus. A hoax could also be used to track who the recipient knows; some chain e-mails ask the receiver to forward the mail several of friends as well as the original sender. This would enable an attacker to gain information regarding the victim’s associates, as well as their e-mail addresses.
Hoaxes aren’t confined to e-mail; fake web sites, social media sites, and even telephone calls can be used to perpetrate a hoax. The goal may be to get donations, spread a fake story, or even simply to see how many people will fall for it. As with most other social engineering attacks, a good security education and training program is the best defense against hoaxes.
Phishing
Phishing is designed to get personal or sensitive information from an individual, such as a Social Security number, driver’s license number, credit card information, bank accounts, usernames, and passwords. The attack typically involves an e-mail sent to a user claiming that the user needs to connect to or log on to a site (with the link provided, of course) to verify an account or other such pretext. The user clicks the link in the e-mail and is directed to a site that looks convincingly genuine, and may even mirror a real site. The unsuspecting user inputs her credentials or information as the e-mail requests, not knowing that instead of passing on this information in a secure way to a legitimate site, she is actually simply handing it over to an attacker.
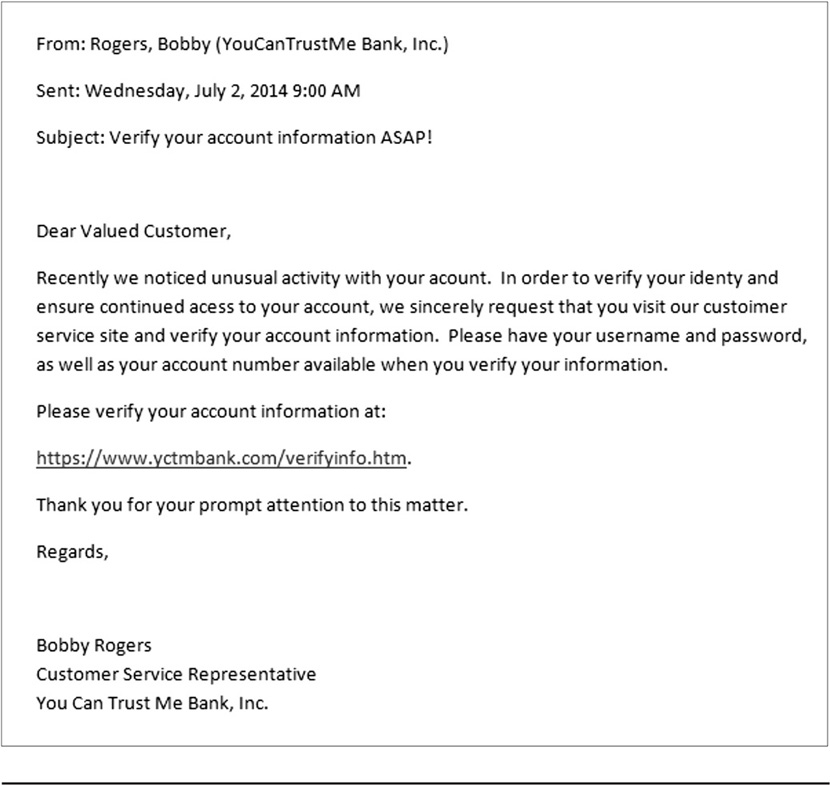
Phishing attacks have become increasingly sophisticated over the years; early phishing e-mails could be spotted as obvious frauds because they came from unknown or obfuscated domains, used broken wording or incorrect spelling and grammar in the message, and redirected the user to a site that was obviously not a legitimate business site. Nowadays, phishing attacks are executed with much more sophistication and precision; they often are very professional and convincing in their wording, use spoofed or similar-sounding domain names, and redirect users to professional-looking web sites that may even provide some sort of fake functionality. Figure 36-3 shows an example of a phishing e-mail attack.
Figure 36-3 A phishing e-mail
Note that phishing is different from pharming; in a phishing attack, the user is directed to a fake site through a link embedded in an e-mail. In a pharming attack, the user is redirected to a fake site through some other means, such as malware on the computer, host file poisoning, or redirection from a DNS server that has been compromised. The end results can be the same, however; if a user is redirected to a fake site through a pharming attack, the user may still be enticed to input sensitive information into the site, which is then collected by the attacker.
Whaling
Whaling is a variant of phishing, where the phishing e-mail is sent to a high-value target instead of the masses. Usually, senior executives and others in important positions are targeted in whaling attacks. These types of attacks involve much higher stakes, because senior personnel in the organization have information that may be considered more critical and of higher value to an attacker.
Vishing
Vishing is yet another variant of phishing attacks that are often perpetrated over voice-over-IP (VoIP) telephone networks. Vishing can be quite effective because it may use prerecorded messages and spoofed telephone numbers to convince a target that the message is legitimate. The attack may advise victims to go to a particular web URL to correct or verify their information, or even to call a particular number, where the attacker will impersonate someone who has the authority to collect the information and “help” the victim.
Spear Phishing
The last variation of phishing attacks that we’ll discuss is known as spear phishing. In this attack, the phishing e-mail is specifically targeted toward an individual, instead of being generic enough to target many people at once. In the phishing e-mail, the attacker will often use information that can be linked to the victim, such as personal information the attacker has already gathered by some other means. Examples might include the last four digits of the victim’s credit card number or Social Security number, or a partial date of birth. This lends credibility to the attack and makes it easier to persuade the victim that the e-mail is genuine. Another common spear phishing tactic is to spoof a known sender; for example, if Bob frequently receives PDF reports from Alice, a savvy attacker could spoof an e-mail to Bob from Alice containing a malicious attachment, and Bob would likely not think twice about opening it.
Social Engineering Principles of Effectiveness
Even though we train our users on what social engineering is, how it works, and what to look for in such an attack, these attacks are still quite effective. Why is that? Because it’s very difficult to fight human nature; even when we know something we’re doing isn’t quite right, that we’re not following the proper procedures, or that we’re breaking the rules, or that nagging little suspicious voice inside of us tells us that something’s not quite right, we still fall for social engineering tricks. These attacks work because people are, well, human.
You should be aware of the various attacks and why they are effective so that you can protect yourself and your users. Keep in mind that almost all of these attack methods can be used as part of an elaborate lie, hoax, or other false pretense or context, in order support an attacker’s approach.
Authority
Attacks that use authority take advantage of two reactions most of us have to authoritative sources, such as bosses, VIPs, and so on: fear and respect. Most of us respect people in authority and sometimes even fear them, because our interactions with them tell us that they are in a position of authority for a reason; they may have power over us, such as the power to fire us or give us raises, for instance. We also respect positions of authority because we’re typically taught that tendency as we grow up, and we experience it when we enter the workforce. Because of our fear of and respect for authority, we sometimes bend over backward to do what we’re being asked to do by an authority figure, regardless of how we feel about it. Sometimes we act out of fear of the authority figure, and sometimes we want to impress important people with our knowledge, helpfulness, the willingness to do our jobs, and so on. Attackers make use of these tendencies to convince us that we are required to take these actions by virtue of the position of authority they are exerting over us.
Intimidation
Intimidation can go hand-in-hand with the fear of authority. Of course, a target can feel intimidated by an authority figure he fears, but it doesn’t necessarily have to be an authority figure. An attacker can pretend to be a loud, boisterous jerk who threatens the target with all manner of bad results if she doesn’t get her way, for example. The attacker may pretend to be an irate customer who threatens to complain about the target’s actions to his boss or another real authority figure. This kind of behavior typically intimidates people and can even cause them to want the attacker and their issues to “go away,” so the victim is willing to do whatever it takes to satisfy the attacker’s request as soon as possible. For example, consider a social engineer who calls the helpdesk and demands that her password be reset. She may yell and scream and threaten to talk to the helpdesk person’s boss about his incompetence or lack of willingness to help if the helpdesk technician doesn’t reset the password. A lot of new and inexperienced technicians fold to that type of intimidation; usually it’s the better-trained and more experienced techs who know how to stay calm and handle difficult people and are able to thwart an attacker’s use of intimidation as a social engineering technique.
Consensus/Social Proof
Another technique used in social engineering is the consensus or social proof tactic. In this type of attack, the social engineer tends to be a little bit nicer, more understanding, and more sympathetic to the needs of the target. He attempts to find common ground with the target, such as a shared background, likes and dislikes, hobbies, or even opinions. He also may try to reason with a type of twisted common sense to get the target to agree that what he’s asking for makes perfect sense, building a consensus with the victim and making the victim think his way, so to speak. Since people normally like to be agreed with, like to be accepted, and like to find common ground with people, they’re more amenable to this type of attack. Additionally, everyone wants to think that they have “common sense,” so they’re more apt to break rules that don’t seem to make sense if the attacker can simply get them to agree. This type of attack may take a little bit more of an effort on the part of the attacker, simply because he has to do his homework and understand the target a bit better before he approaches and engages a target. The social proof aspect could involve the attacker dropping a few familiar names; this provides “proof” that the attacker is legitimate, since he knows someone that the target knows.
Here’s an example: In a military setting, an attacker calls a helpdesk employee. The attacker presents the help desk technician with this scenario:
I’m General Johnson’s aide, Captain Smith. Can you believe this guy is asking me to have his password reset? It’s incredible that he’s so lazy he can’t do it himself. What a guy…. But you know how it is to get an order from a general, right? You just do what you gotta do, even though it’s against the rules, you know? Can you help me out?
This attack could be effective on many levels. First, the attacker is dropping names the technician may be familiar with, so the technician may be slightly intimidated. Second, the attacker is attempting to build rapport with the technician by pretending to be just an ordinary person trying to do his job. Third, the attacker willingly admits to the technician that he’s asking the technician to break the rules, but he’s hoping the technician will feel sorry for him and do so anyway because he’s just following orders.
Scarcity
Scarcity is another tactic used in social engineering. Scarcity refers to getting the victim or target something that they really want, something that may be otherwise difficult to obtain. It may be something intangible, such as a promotion, a new position, or some other type of incentive. It also may be something very tangible, such as an object or something else the target wants. For example, the social engineer could offer the target courtside basketball tickets if the target will only reset a password over the phone instead of making the “user” the target is pretending to be drive all way over to the help desk and show his identification. It may be something as simple as an exotic coffee, or sports tickets, or something the target may not think is important enough to question. The attacker may use the scarce item as a kind of a “thank you” for doing a favor, thus continuing to build a good relationship with the victim.
Urgency
An attacker may use urgency to get a victim to perform an action or provide information quickly, without being able to think about it clearly or confirm that the attacker really needs the information or is authorized to request the action. You may have heard of an attacker pretending to be an administrative assistant, calling on behalf of his boss, who is out of town and has locked her user account. The admin assistant urgently begs or otherwise pressures the target to unlock the account or change the password without confirmation from the user. There’s usually some contrived story about how the user can’t be contacted by phone or is currently on a plane and can’t verify the request herself. The fake admin assistant may insist that he will get into trouble with the boss, or the boss has a critical meeting with a very important customer and needs immediate access to the account once she lands. All of this false pretext conveys a sense of urgency designed to pressure the target into performing the desired action or even giving the attacker information. Combined with a person’s natural desire to help someone in need, especially in an urgent or critical situation, this technique is often quite effective.
Familiarity/Liking
People like to be liked. That’s a simple fact of human existence. So people respond positively to people who like them or take the time to get to know them. Developing a bond with a social engineering target can help the attacker better persuade and influence the target into giving him what he wants in terms of information or having the target perform certain actions for him. For example, let’s say that the target works in a secure area that houses some really cool technology or scientific experiments. The attacker establishes a familiar and friendly relationship with the victim and bolsters her ego, making her feel good about the relationship. The attacker then casually asks the victim to let him into the restricted area so he can see some of the cool stuff that goes on there. After a bit of pressure and cajoling, the target may give in and sneak the attacker into the restricted area when no one’s looking, thinking that it won’t hurt if they are there together, and it’s only for a few minutes. It likely wouldn’t take an attacker long to install a hardware keystroke logger, a listening device, a small hidden camera, or even a wireless sniffer unobtrusively, once the target gets him into the restricted area.
Trust
Trust is yet another factor in successful social engineering attacks. Humans have a propensity to trust, especially when they feel that trust has been earned, and when they feel trusted likewise. Social engineers know this and seek to establish different levels of trust between themselves and their victims, based upon the circumstances, their goals, and the level of rapport they can establish with the target. The attacker may need only a very low level of trust for some purposes, but may require a deep level of trust for others. The more an attacker needs from a target, the more trust they have to establish with the victim. Often, these types of trust relationships can take weeks or even months to develop and involve using many of the techniques we’ve described previously to establish the relationship, develop a bond, and create trust between the attacker and the target. The attacker also may make the victim feel trusted as well, which can strengthen and hasten the trust relationship.
It’s interesting to note that in most successful social engineering attacks, more than a single factor or technique is used; it’s likely that none of these techniques would be very effective alone. Attackers can create complex situations involving multiple approaches to a target and use methods that establish trust, sway their victim’s opinion and actions, and generally manipulate the victim. Of course, it really all depends upon the situation. Some social engineering attacks may involve only a brief interaction with a target that last only a few minutes and involves very simple attack methods. A simple attack, again, may be used to gain access to a more important person or put the attacker in a better situation to leverage a larger, more complex attack.
So, how do we prevent social engineering attacks? Again, there’s no patch for being human, so what type of control can we exert that would mitigate the vulnerabilities associated with wetware? In the next module, we’ll look at how training is probably the best security control that can be applied to the human factor, mitigating the vulnerabilities associated with people.
Module 36 Questions and Answers
Questions
1. Which of the following elements is attacked by social engineering techniques?
A. Encryption
B. People
C. Authentication
D. Policy
2. Which of the following are human weaknesses that social engineers target? (Choose two.)
A. Desire for acceptance
B. Desire to be left alone
C. Desire to help
D. Lack of security training
3. All of the following are potential social engineering attack targets within an organization, except:
A. A business partner’s system administrator
B. The company senior executives
C. A competitor’s security engineer
D. A subcontractor’s administrative assistant
4. Which of the following attacks is conducted by trying to get a view of sensitive information on a user’s screen?
A. Dumpster diving
B. Tailgating
D. Shoulder surfing
5. You are a security administrator in a company, and a user has just forwarded a suspicious e-mail to you that directs the user to click a link to a banking web site and enter their credentials to verify the account. What type of social engineering attack is being attempted?
A. Phishing
B. Vishing
C. Man-in-the middle
D. E-mail hoax
6. An attacker who is pretending to be a known user within the organization is said to be conducting a(n) __________attack.
A. impersonation
B. physical
C. consensus/social proof
D. scarcity
7. An attacker calls an administrative assistant and tells him that she is the new executive assistant for the company senior vice president. She claims the VP is traveling, and she needs access to certain sensitive files in a file share. The attacker ties to bully the admin assistant into giving her permissions to the file share by threatening to have him fired if he doesn’t oblige. Which two characteristics of human behavior is the attacker trying to take advantage of in this attack? (Choose two.)
A. Trust
B. Fear of authority
C. Social proof
D. Respect of authority
8. An attack who promises to obtain something that is hard to get for the target is using what kind of tactic?
A. Intimidation
B. Trust
C. Scarcity
D. Social proof
9. A person calls and tells you that he has locked his account because he forgot his remote access password. He tells you that he doesn’t have time to come down to your desk and positively identify himself because he is off-site at a customer facility and must present an important briefing to the customer within the next few minutes. He insists that he needs his remote access password changed immediately, but promises to come and see you after he returns to the office to verify his identity. What kind of social engineering tactic is being used in this attack?
A. Authority
B. Familiarity
C. Intimidation
D. Urgency
10. Which of the following is considered the best defense against social engineering attacks?
A. Increased authentication measures
B. Increased punishment and consequences for workers
C. Increased training and education
D. Increased physical security controls
Answers
1. B. Social engineering attacks target the people who work in and are associated with an organization.
2. A, C. Social engineering targets human weaknesses that stem from the desire to be liked or accepted, as well as the desire to help others.
3. C. A competitor’s security engineer is an unlikely target because she will not have any information of value, nor is she able to perform any actions within the organization that may benefit the attacker.
4. D. Shoulder surfing is an attack in which the perpetrator tries to view sensitive information on a user’s screen.
5. A. A phishing attack is conducted by sending an e-mail to an unsuspecting user in an attempt to get the user to click a link in the e-mail and enter sensitive information, such as credentials or other personal information, into the site.
6. A. In an impersonation attack, an attacker pretends to be a known user within the organization in order to persuade a target to give him information or carry out an action for him.
7. B, D. The attacker is taking advantage of the human tendency to fear and respect authority figures.
8. C. Scarcity is a tactic used during a social engineering attack in which the attacker promises to get the target something of value that is normally hard to get.
9. D. The attacker is trying to use a tactic involving urgency of need in order to get the remote access password reset, without having his identity verified.
10. C. Training and educating organizational personnel is considered the best defense against social engineering attacks.