MODULE 28
Virtualization Security
Virtualization is one of the “next big things” in the infrastructure world, and, as such, it’s also become one of the “next big things” in the security world. Virtualization has become a major player in scaling entire network architectures to include operating systems, applications, and almost any other component you can think of that exists in the physical infrastructure. Virtualization has many benefits, including its ability to reduce expensive hardware, expand the network infrastructure, and even outsource expensive overhead involved in maintaining a network to a third-party provider. However, security is still a consideration, simply because virtualization houses so much data but is still required to maintain high availability standards, particularly when supporting large organizations. In this module, we’ll look at security as a primary consideration in virtualization.
Securing Virtual Environments
The virtual environment includes environments in which host machines have virtualized computers running on them. Some of the same challenges that face physical machines and networks also concern virtualized environments. Although there are some unique challenges in securing virtual environments, they have a lot in common with their physical counterparts in terms of risks and security controls. In this module, we’ll look at securing the host operating system as well as the virtual operating system.
Virtualization Concepts
You probably have an idea of what virtualization involves. However, you may have learned about only part of it, or perhaps you have been peripherally involved in setting up a virtual environment. Maybe you’ve put together a test lab on a single PC and run a few virtual machines on it, or perhaps you’ve designed and architected an entire virtualized environment for a large organization. In any case, you’ll need to be familiar with several important concepts for the exam, so we’re going to cover them here. These concepts include the basics of how virtualization works, the different types of hypervisors that can be used, and virtualization architecture. We’ll get into some of the things that virtualization can do for us as networking and security administrators. We’ll also talk about the security considerations of virtual environments, to include risks and security controls that we may want to implement with those environments.
Virtualization Architecture
In the basic sense, virtualization means that we usually run at entire instance of an operating system on a host physical machine. The virtual machine (VM), or guest as it is sometimes known, exists as a file in an application. When the machine is not in use and powered on, the VM is simply a series of files that reside on the file system of the host machine. Applications known as hypervisors (or virtual machine monitors) create and use these files and instantiate a guest machine. When the machine is turned on, the hypervisor acts as a mediator between the host operating system and the guest operating system, providing access both to physical and logical resources. These resources could include soundcards, network connections, hard disks, USB drives, and any other peripherals that a physical machine could use. As far as the virtual machine is concerned, it doesn’t “know” that it is not a physical machine; it functions as if it were a completely solid physical device. That means that it behaves as a physical device and can run applications, service user requests, make network connections, and so on. Virtual machines can be used as file servers, user workstations, DNS servers, web servers, and almost anything else that a physical machine is used for. Unfortunately, this also means it has the same weaknesses as a physical device, and it must be secured and hardened against attack.
Virtual machines can be almost any operating system—Windows, Linux, UNIX, BSD, and (to a lesser extent) Mac operating systems can all be virtualized. Even the Android operating systems used in mobile devices can be run as a virtual machine. The host machine, on the other hand, can also run various operating systems, including Windows, Linux, or Mac. The real requirement is that a compatible application must create and run virtual machines on a particular host operating system. That brings us to the discussion of hypervisors.
The hypervisor can be an application that creates and runs virtual machines. There are two types of hypervisors: Type 1 and Type 2. A Type 1 hypervisor is actually a limited function, stripped-down operating system in its own right. It runs the host machine and serves to provide the single functionality of managing the virtual machines installed on it. These types of hypervisors are usually called bare-metal (or sometimes native) hypervisors, because they provide a very limited functionality and really only boot up the physical machine and handle resource access from the virtual machines. Several popular Type 1 hypervisors are available; some of them are even free to use. Microsoft has a Windows-based hypervisor (Hyper V), as does the Linux community. Commercial hypervisors are also available, such as those developed by VMware.
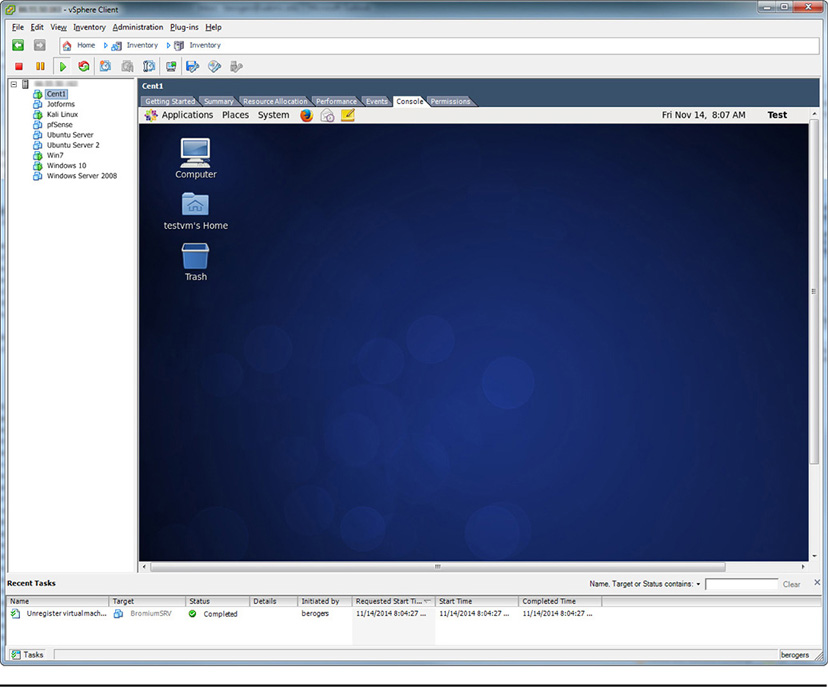
For the most part, Type 1 hypervisors are usually installed and then run in “headless” mode, meaning that they don’t require a user to sit down at a keyboard console or monitor. They are usually managed remotely through client software on a workstation after their network connectivity has been set up. Figure 28-1 shows an example of how VMware’s ESX server, a popular bare-metal hypervisor, is accessed and managed remotely via the VSphere client. Rarely, an administrator might have to sit at a console at the host server to perform configuration tasks that can’t be done remotely.
Figure 28-1 Accessing an ESX server through the VMware VSphere client
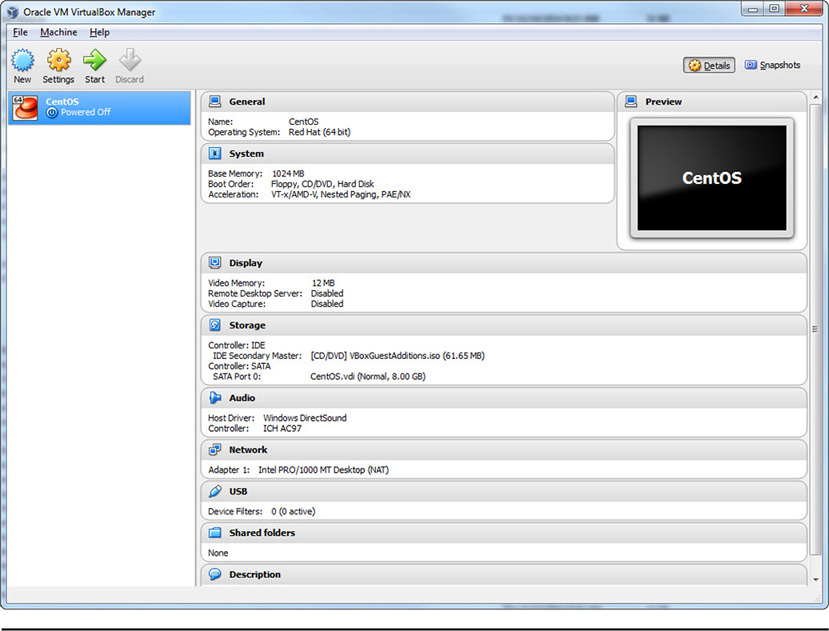
You might be more familiar with a Type 2 hypervisor if you have ever set up a small virtual environment. This type of hypervisor is an application that runs on top of a fully fledged operating system. You may have used a hypervisor product such as VMware Workstation, VMware Player, Microsoft Virtual PC, or even the open source VirtualBox software. All of these are Type 2 hypervisors that can be used to create and manage a limited number of virtual machines. Usually these types of hypervisors are used in small environments to create and test different aspects of virtualization. For larger production environments used in businesses, Type 1 hypervisors are normally used and are typically installed on very powerful, robust physical hardware. Figure 28-2 shows the user interface of VirtualBox, a popular free hypervisor application produced by Oracle.
Figure 28-2 The VirtualBox Type 2 hypervisor
Virtual machines can also have unique network architectures. They can use multiple network configuration options, depending upon the type of host system they are installed on. You can configure a network connection that is directly connected to the outside network through the host machine’s network interface card, and the VM receives its IP addressing information from the outside network. This is called bridging. A VM could also receive its IP addressing information directly from the hypervisor installed on the host. In this regard, the hypervisor acts as a Dynamic Host Configuration Protocol (DHCP) server and provides private IP addressing (through network address translation, or NAT) to the virtual hosts. The host would then act as the default network gateway for any VMs installed on it. It’s also possible, if you so desire, to set up a virtualized network within the host so that only virtual hosts can communicate with it and each other. In other words, they can’t contact the outside world through the virtual network unless the host is configured to allow it. You can configure the network portion of the virtual environment in several different ways, based upon how you want virtual machines to communicate with the outside network, the host, and each other.
Virtualization Risks
Of course, even beneficial technologies like virtualization have inherent risks. Virtualization is the solution to many problems, such as scalability, hardware production, and even security in some respects, but there are risks that go with it. For example, with virtualization, single points of failure for host machines are risks, because if the host machine becomes unavailable, loses connectivity, or encounters a serious hardware error, all of the virtual machines that reside on it are also lost. In addition, because multiple virtual machines may be running on a host, and some may have several services running on them, this adds to the attack surface of the host. All of the services that the virtual machines run communicate with the outside world and the network, so they all represent different attack vectors as well. These represent a threat not only to the each individual virtual machine, but also overall to the host.
Yet another risk involves redundancy and availability. Although virtualization actually helps in ensuring redundancy and availability, failure on the part of administrators to take advantage of these features could result in the loss of critical data if a virtual machine fails and it has not been backed up or otherwise preserved. Security could also be considered at risk with virtual machines because complacent administrators often mistakenly think that securing the host machine is enough, and sometimes they forget to secure the guest machines as well. So it might not be unusual to see a fairly secure host machine, with guest machines running on it that have blank passwords or default security configurations. Remember that almost any risk that a physical machine can incur can also be incurred on a virtual machine. You should take the same security measures on VMs that you take on a physical machine.
Hardening Virtual Machines
Locking down and securing virtual machines is not much different from doing the same to physical hosts. All of the security considerations for physical hosts also apply to virtual machines. They require frequent patching and updating, they require locking down configuration settings, they need secure account settings, and when setting up users, you should follow the principle of least privilege. One nice thing about a virtual machine is that once you have hardened the configuration as needed, you can always use it as a baseline and replicate it multiple times, so that each virtual machine you create starts out with that hardened baseline and requires only recent patches or configuration changes. This makes it much easier to deploy machines on a large-scale basis.
As with physical machines, with VMs, you need network connectivity to ensure that patches get updated in a timely manner. You also need to make sure that you install antimalware on the VMs, since like all networked hosts, they are susceptible to malware from web sites, malicious files, and so forth. They should all also have host-based firewalls or multipurpose packages that take care of firewall, antimalware, and intrusion detection installed on them.
In addition to the normal things that you would do to secure physical hosts, virtual machines lend themselves to some other security measures. When not active, they are simply files located in storage, and as such they can be protected through permissions, encryption, and separation, the same as you would protect any other types of sensitive data files. They can also be copied and stored securely on secure media. Also like physical machines, they should be backed up periodically to ensure availability; we’ll talk about backing up virtual machines next.
Snapshots and Backups
Like physical machines, virtual machines also need to be backed up from time to time, because they process data like their physical counterparts and store user data that may be critical for operations. Virtual machines can be backed up using the same strategies used for physical machines. However, virtual machines also have some advantages, in that they are native files located on a file system of some sort, so you can treat them like files for backup purposes as well. So you could simply perform file backups to network-based or offline storage, and you can also encrypt these files when they’re backed up. They can also be restored at will if a virtual machine fails or becomes inaccessible. And they can be used to create additional duplicate virtual machines for redundancy purposes.
You can also perform snapshots on VMs. A snapshot is a point-in-time backup of the current system state of the VM. This means the VM would back up and preserve any applications in use, user data, or other configuration details particular to that system’s state at that moment. So, for example, you could take a snapshot of a virtual machine before installing a new application or a critical patch, and save the snapshot so that if the patch or software caused a functionality or security issue, the snapshot could be restored, enabling you to revert back to the state the virtual machine was in before the installation. You could use incremental sets of snapshots or combine them with traditional backup methods to maintain highly focused, comprehensive system state backups for availability.
Using Virtualization for Security
Although you’re probably already aware of some of the fantastic uses of virtualization, there are several aspects of security that virtual environments can help with. Virtual environments can provide stable, segregated environments in which to test applications, software, and even malicious code. Virtualization can also contribute to system and data availability by maintaining multiple redundant copies of identical virtual machines. In the next few sections, we’ll go into a bit more detail on how virtualization contributes to the overall security posture in the organization.
Patch Compatibility
You already know that patches should be tested before being applied to production environments. This is because sometimes patches have unforeseen negative effects on production hosts, which can quickly take down critical operations. One thing that a virtual environment can give you is a complete test environment that mirrors the production environment. It’s actually possible to copy a physical machine and create an identically configured virtual machine out of it. You can use this to your advantage by creating an almost exact replica of your physical environment in the virtual world, and test your patches, configuration changes, and updates in this test environment before you apply them to the physical machine. This helps avoid unintentional issues when you apply patches to production machines. It also allows you an opportunity to see where there may be issues and determine ways to correct them before the patch goes into production.
Host Availability and Elasticity
Virtual environments offer real flexibility in the use of an organization’s infrastructure for both availability and elasticity. Availability can be supported by virtualization in that production hosts (whether physical or virtual) can be almost instantly duplicated in a virtual environment, adding redundant capabilities for availability purposes or assets for use when existing hosts aren’t enough. Physical machines can be copied and converted to virtual machines, and virtual machines, since they are merely files, can be copied and reinstantiated as a new additional virtual machine (with a few basic configuration changes, of course).
Elasticity means that resources in the environment (in this case, virtual hosts) can be expanded, duplicated, reconfigured, repurposed, and reused on the fly, as the need for them arises or shrinks. This allows an organization to be flexible in its use of resources, saving physical machines and reallocating, activating, and deactivating hosts as needed in dynamic use situations. Virtual machines can be provisioned, configured, and stored in advance for just such instances.
Security Control Testing
Another use of virtualization technology that is beneficial to security professionals is the ability to test various security controls on virtual hosts, either before implementing them in production or as changes to the production environment occur. Different controls can be configured to test effectiveness and balanced with functionality, to ensure that the appropriate control is implemented correctly for the environment. This can help confirm whether a new security patch will actually break an application, whether a configuration change is effective in reducing a vulnerability, whether a change to an operating system’s function or configuration breaks its security baseline, and whether a target host is configured as securely as you need it to be for vulnerability and penetration testing purposes.
Sandboxing
Sandboxing is a technique used to provide an enclosed environment in which to run potentially dangerous applications, or even malware, to determine the effect they would have on the environment. Often, security professionals need to see the effects of an application or software on a host, to determine how it interacts with the system and the network. This can help identify potential issues with untrusted software, such as executables and scripts. Sandboxing allows you to test potentially harmful software in a controlled, isolated environment, without the possibility of affecting other hosts or allowing unwanted communication to the network. Virtualization easily provides sandboxing capabilities by giving you the option of running an isolated virtual host for that purpose.
Supporting Legacy Software
From a security perspective, supporting legacy applications and operating systems can be problematic. Integrating them into an existing infrastructure that has been updated with the latest operating systems and patches can be difficult, because the existing network and systems may require security features that are not always backward-compatible with legacy systems. Additionally, making the legacy systems work with newer, more secure systems often requires that you lessen the security posture of other systems. Virtualization can help lessen the risk posed by legacy systems. Using virtualization techniques, legacy applications and operating systems can be run on a virtual machine, using a more secure system as its host. This enables you to fit legacy systems into a more secure network and reduce the risks posed by running less secure hosts on the network. The host OS can be locked down and secured, serving as an additional layer of protection for the legacy VM and the rest of the network.
Module 28 Questions and Answers
Questions
1. Which of the following statements best describes a hypervisor?
A. A guest operating system
B. A host virtual machine
C. An application used to create and manage virtual machines
D. A virtual machine that controls other virtual machines
2. A bare-metal hypervisor is also referred to as a __________.
A. host machine
B. guest machine
C. Type 2 hypervisor
D. Type 1 hypervisor
3. A virtual machine that gets its IP addressing information from the outside network is using a technique called __________.
A. bridging
B. NAT
C. routing
D. switching
4. Which of the following are security risks that could apply to virtual machines? (Choose all that apply.)
A. Lack of up-to-date patches
B. Non-secure configuration
C. Excessive user privileges
D. Theft of a virtual machine
5. Which of the following hardening methods makes more sense on a virtual machine than a physical one?
A. Securing user accounts
B. Backup and encryption of the actual virtual machine disk files
C. Configuring minimal functions with least privileges
D. Patches and security updates
6. Which of the following terms describes the ability to take point-in-time system state captures of a virtual machine?
A. Backups
B. File captures
C. Snapshots
D. Packet captures
7. Which of the following would be considered a contribution to system availability that virtualization can provide?
A. Ability to rapidly replicate physical and virtual machines
B. Ability to secure VM files through encryption
C. Ability to run a separate instance of an operating system on a physical machine
D. Ability to store VM backups securely
8. Your manager needs you to patch several production servers rapidly due to a critical security vulnerability that has just been published. You know you need to patch them quickly, but you’re concerned that the patch may actually break functionality or security on the production servers. Which of the following strategies would help you to be sure that the patch would not adversely affect production systems?
A. Test the patch on both the production server and identical VM simultaneously and note any issues that occur.
B. Test the patch on a generic virtual machine to see if it causes any issues on the VM.
C. Install the patch on production servers and have a backup ready in case there are adverse effects.
D. Replicate the production servers into a VM, and then test the patch on the replicated virtual machines.
9. Which of the following would be the best way to perform a penetration test on a mixed physical and virtual environment?
A. Perform the penetration test on all production machines at the same time.
B. Test only very specific security controls on both physical and virtual production machines.
C. Replicate all production machines (whether physical or virtual) as virtual machines, and perform a penetration test on the replicated VMs.
D. Do not test the virtual machines.
10. Which of the following methods can use virtualization to test untrusted software and potential malware safely?
A. Sandboxing
B. Filtering
C. Containerization
D. VLAN segmentation
Answers
1. C. An application used to create and manage virtual machines is known as a hypervisor.
2. D. A bare metal hypervisor is also referred to as a Type 1 hypervisor.
3. A. A virtual machine that gets its IP addressing information from the outside network is using a technique called bridging.
4. A, B, C, D. All of these are valid threats against virtual machines, which suffer from the same types of threats regarding excessive user privileges, faulty security configurations, and lack of patch management. Additionally, virtual machines can also be stolen, since they are files and can be removed from a facility and re-created elsewhere.
5. B. Backup and encryption of the actual virtual machine disk files is a security measure you can take that is unique to virtualization. There are normally no such files associated with a physical machine. The other choices are appropriate for both virtual and physical machines.
6. C. A snapshot is a point-in-time system state capture of a virtual machine.
7. A. The ability to rapidly replicate physical and virtual machines contributes to system availability.
8. D. Replicating the production servers into a VM, and then testing the patch on the replicated virtual machines is the best way to determine if there will be any adverse effects before you put the patch in the production.
9. C. Replicate all production machines (whether physical or virtual) as virtual machines, and perform a penetration test on the replicated VMs.
10. A. Sandboxing uses virtualization to test untrusted software and potential malware safely.