MODULE 32
Perimeter and Physical Controls
Perimeter and physical security is not normally a concern of IT security professionals. If it doesn’t involve bits and bytes, packets, and encryption, then we don’t usually have much to do with it. However, like the environmental security controls we discussed in the previous module, physical security is important, because it not only helps protect our data, systems, and networks, but it also provides for personnel safety. As an information security professional, you need to be aware of how perimeter and physical controls are used to protect your systems and people. In this module, we’ll look at perimeter and physical controls from both the safety and protection standpoints. First, though, we’re going to look at the different types of security controls in general and discuss the control types and their functionalities, so you can get a better idea of how controls work.
Classifying Controls
You probably already know that a security control is a measure or mitigation put in place to prevent something bad from happening or to increase security in a system or facility. If you go back and look at earlier modules in the book that discuss risk and terms associated with threats and vulnerabilities, you will remember that controls are essentially put into place to minimize risk and to reduce the likelihood of a threat exploiting a vulnerability or the impact to a system if it does occur. It’s important that you understand how security controls are categorized. Security controls can be sliced and diced in several different ways, and for the exam, you need to know how to classify controls in terms of types as well as their functions. In the next two sections, we’ll examine the different control types as well as what functions these controls serve.
Control Types
Different books and security professionals refer to the basic control types using different terms. You need to be aware of three basic control types, how they are classified, and the various names used to refer to them. Administrative controls are also frequently called managerial controls. These controls are associated with the paperwork and program management aspects of security, such as policies and procedures, personnel policies, acceptable use policies, and so on. Administrative (managerial) controls form the basis of the other types of controls, because policies drive everything we do it security.
The second type of control is the technical or logical control. You’ll hear either term used in different texts and by different security professionals. Technical or logical controls are basically the technical measures that you might encounter in everyday hands-on security, such as firewalls, encryption technologies, access control lists on routers, secure protocols, and so on. For better or for worse, this is where you may see most of the focus on security from novice security professionals; most of the techno-geek security folks tend to focus more on these types of controls than they do administrative and managerial controls.
The third type of control is known as either physical or operational controls. You’ll see some distinction between these actual controls, however, in that physical controls are typically lumped with environmental controls, and operational controls may be sometimes lumped in with administrative and managerial controls. Physical controls are associated with safety, environmental factors such as temperature and humidity, gates, guards, guns, security cameras, and so on. Operational controls can be thought of as the actual operational procedures used for particular physical security processes. For example, requiring a visitor to sign in before entering a restricted area such as a data center may be considered an operational control. Again, you’ll hear these two terms used interchangeably.
Figure 32-1 illustrates the differences between administrative, technical, and physical control types.
Figure 32-1 Administrative, technical, and physical control types
Control Functions
Control functionalities are designed to focus on a certain aspect of security, such as deterrence, detection, and so on. It would be nice if the different control types (administrative, technical, and physical) all fell neatly into these different control functionalities, but, unfortunately, they don’t. Some administrative controls, for example, might be considered deterrent controls (an acceptable use policy, for example), while others might be considered preventative controls (think background checks on employees). If that weren’t bad enough, it’s also possible that the different individual controls may be considered to fill more than one function. For instance, the acceptable use policy could be a deterrent, in that it deters people from performing actions that are prohibited by the organization. Of course, it won’t deter everyone; some people will still violate this policy. However, part of this acceptable use policy should also state what the consequences are if the policy is violated. This part of the policy might be considered corrective in nature. So it can be confusing, and a little bit difficult, to classify controls precisely in terms of one distinct functionality or another. Adding to the confusion is that this is all very subjective. What one security professional may consider a preventative control, another may consider corrective, detective, or compensating. It really depends upon the context of how the control is used. In any case, let’s briefly discuss each of the different control functionalities you are likely to see on the exam and in the real world.
Deterrent
A deterrent control is designed to deter people from committing security violations or from performing actions that are inherently not secure. An example of a deterrent control might be the acceptable use policy or closed-circuit television (CCTV) cameras placed conspicuously in different areas of facility. These controls would deter someone from committing a security violation or a prohibited act, simply because they may be afraid of getting caught or suffering the consequences of those acts. Deterrent controls are usually effective because the users know they exist; if users have no idea that a control is there, and that there are consequences for violating it, then it doesn’t do much to deter them. That’s actually the distinguishing factor between a deterrent control and a preventative control.
Preventative
A preventative control doesn’t have to be visible or known to the user in order to prevent a security issue from happening. Although the value of a deterrent control is that users are aware of it and know there will be consequences if they violate it, a preventative control does its job regardless of whether the users know about it or not. For example, a preventative control might be a rule in the firewall designed to filter out the port and protocol that a certain type of malware uses. It prevents this malware from coming into the network, but users don’t necessarily have to be aware of it for it to be effective. Another example, this time using a physical control, may be an electronic locking system at the entrance to a secure area. It prevents unauthorized users from entering the area; they don’t have to be aware of it for it to be effective.
Detective
A detective control is designed to detect and alert security personnel if a violation has occurred or if a non-secure condition exists. For example, a detective control can be an intrusion detection system (IDS) alert that notifies an administrator if the network starts to receive massive amounts of malformed packets from the Internet. The IDS will detect this condition and alert the administrator, and it could also take preventative or corrective actions. In this case, the technical control in use could be considered a detective control, a preventative control, and even a corrective control, all at the same time. Another detective control might be the security event logs on a Windows server that record all security-relevant events that occur on the host. While reviewing these event logs might be a manual task, if a security incident is uncovered during the review, this makes it a detective control. Physical security controls can also be detective in nature; a motion-sensor that alerts when someone unauthorized enters a restricted area is a detective control.
Compensating
Compensating controls can be difficult to understand, simply because most controls could be compensating in some way or another for different weaknesses. A compensating control is really a control you might use to make up for a temporary shortfall or weakness in the system or facility, in case another control you already have in place fails or is temporarily not working properly. The temporary nature of a compensating control is what classifies it as a compensating control and not one of the other control functionalities. If the control will be replaced or made permanent, then it’s simply reclassified as one of the other control functionalities. As an example, suppose someone cut a large hole in a perimeter fence while trying to break into a facility. Until the fence can be repaired, there’s a gaping hole there that someone could still try to use for unauthorized entry. Until it’s repaired, you might deploy extra guards to that area or put up some other type of barrier to prevent someone from going through the hole in the fence. The damaged portion of the fence will eventually be repaired, and that might be the more permanent control action. In the meantime, however, the extra guard or temporary barrier would be considered compensating controls.
Corrective
A corrective control is also difficult to understand, simply because this type of control is normally considered one of the other control functionalities (that is, deterrent, detective, and so on). In the example with the IDS, after detecting an anomalous bit of network traffic and alerting an administrator, the IDS might automatically block traffic coming from a particular source IP address or domain, or even drop traffic matching a particular protocol to stop the attack. This would be considered a corrective control, simply because it corrects a security issue that was otherwise not being mitigated at the time. If a rule is later entered into the IDS to make this corrective action permanent, then it might not be considered a corrective control any longer; it might be classified as a preventative control.
Recovery
A recovery control is used to recover from an incident or security issue. What distinguishes this from a corrective or compensating control is that it’s used to restore operations back to a normal state. For example, suppose the hard drive in a server fails and it must be restored from backup data. Restoring the backup will be the recovery control implemented to bring the server back to an operational state. As with all the other control functionalities mentioned, controls could be classified as recovery, preventative, or other control functionalities at the same time as well. The same backup can also be viewed as a preventative control in different circumstances, since it prevented data from being lost.
Now that we’ve thoroughly confused you with a discussion of control types and functionalities, and how they overlap a great deal, understand that for the exam you will likely be able to tell by context what type of control a question is asking about, as well as a particular functionality. Keep in mind, however, that the classification of control types and their control functions can be quite subjective. Table 32-1 lists the different control functionalities and some possible controls that may fall into the category.
Table 32-1 Control Functionalities with Examples
Physical Controls
Because the real focus of this module is physical controls, let’s move from the general control types and functionalities to discuss specific physical security and related controls. Physical controls are used to complement administrative and technical controls by controlling physical access to information systems and areas, and to protect the people who work in the facility housing the systems in those areas. We’ve already discussed, in the previous module, how environmental controls affect the security (primarily availability) and safety of systems and personnel. Here we’ll extend that discussion by describing how physical access controls, such as fences, cameras, guards, alarms, and so on, help protect systems and people from threats such as theft, intruders, and unauthorized access. Physical controls have both security and safety considerations, which we’ll also discuss.
Perimeter and Safety Controls
Perimeter controls surround a facility or a sensitive area to prevent unauthorized personnel from entering those areas. They also protect the authorized people who are allowed to enter those areas. Perimeter controls have both a security and a safety value, and in the next few sections, we’ll discuss both of those aspects.
Perimeter controls are the first line of defense at a facility. They protect the facility, its personnel, and its equipment from a variety of threats, such as theft, physical harm, natural disasters, or even terrorist attacks. Perimeter controls usually include the standard gates, guards, and other physical security measures. You might wonder whether a particular control should be classified as a physical perimeter control or a safety control; the classification depends on whether the control is used primarily to ensure the safety of personnel or to provide for protection against security problems or threats that may target asset vulnerabilities. The answer is subjective, because some controls may fall under both categories.
Fencing
Fencing is the first big physical deterrent most facilities use to keep unwanted and unauthorized visitors out. Fencing is often used at facilities that require higher security than a simple lock on the door. Fencing can be intimidating to would-be trespassers or attackers, particularly tall fencing with barbed wire strung across the top. Fencing can be very expensive, but it serves several purposes.
First, fencing establishes specific entry and exit points around the facility. It establishes an area between outer entry and inner entry points, creating a buffer zone of sorts, to provide distance between the facility entrance and the public area. A well-lit buffer zone makes it more difficult for a trespasser or thief to get from the fence to the facility without being seen. Second, a fence can artificially create those entry points in specific areas around the facility. In other words, someone can’t simply walk up to the side of the building and try to enter through a window; they first must pass through a central entry gate to get in. When the fence is built, the entry gate can be placed wherever it makes sense for more easily controlled access; it doesn’t necessarily have to be at the front door of the building.
When planning facility security, you should consider several particular characteristics of fencing. The first is height. Depending upon the desired security level, a short fence (about 4 feet) might be okay to keep out the general public and curious trespassers. Higher fencing, possibly 7 or 8 feet high, is used to deter even very athletic and determined people from getting in. Barbed wire strung across the top of the fence provides a little extra incentive for people to decide that breaking into your facility is not worth the trouble. Fencing should be in good repair, not rusty, firmly in place in the ground to prevent someone from digging under it, and secured with concrete whenever possible.
Another consideration is the fence’s wire gauge. The gauge of the wires that make chain-link fence, for example, is important to fence strength. Fences come in various wire gauges, but a good gauge for secure fencing is 11, 9, or 6 gauge. Six gauge is the thickest fencing wire and provides the strongest fence. Gauge size directly affects how easily an intruder may cut through the fence. Mesh size is also a characteristic to consider. Mesh size refers to the size of the holes between the wire mesh. Smaller mesh sizes are much better for security than larger mesh sizes, because the smaller holes make it more difficult to climb the fence. Figure 32-2 shows an example of a high-security fence.
Figure 32-2 A high-security fence
Signage
Signage is very important as a deterrent mechanism in and around the facility. Signage can also contribute to the safety of personnel. Signs can warn intruders away from restricted areas and instruct authorized personnel to the proper security and safety procedures. Signs can direct personnel during an evacuation to the correct exit points, warn personnel about potential safety hazards in the facility, or help them find proper safety or fire suppression equipment. In short, the value of signs cannot be understated, because they may be required to help deter unauthorized activities or intruders but can also help protect the safety of the people who work in the facility. In some cases, signage throughout a facility may be required by laws or safety regulations to prevent the organization from being involved in liability issues.
Signs should follow national and international standards for symbols and colors, especially those that mark hazardous conditions. New employees should be briefed regarding the signs, as periodically all employees should be updated. Signs should be placed in well-lit areas and not obstructed by large objects. Figure 32-3 shows how a well-placed sign can help protect both personnel and equipment from unauthorized access and harm.
Figure 32-3 Signage that protects people and equipment
Lighting
Lighting is another critical aspect of perimeter security. During evening or dark hours, lighting can help ensure that trespassers, attackers, and thieves are deterred from venturing out into open areas when trying to approach a facility or harm its personnel. Lighting can be placed at various points along the perimeter fence, at least at distances that allow the outer edges of the areas of light projected from poles to overlap with each other (usually no more than about 20 or 25 feet for tall poles, or about 8 to 10 feet for smaller ones). Lighting should also be placed at gates, door entrances, along sidewalks, and in foyers or entryways. Emergency lighting should be in place throughout a facility in the event of a power outage.
Some lights may be controlled differently than others, depending upon their location and security needs. For example, fence perimeter lighting may be programmed with a timer to come on at certain hours only, such as from dusk till dawn. Such fencing is naturally lit by daylight during daytime hours, and fencing is usually placed in easy-to-see areas. Other types of lighting make use of motion sensors that turn lights on only when someone approaches an area. Still other types of lighting may be lit when an alarm or IDS is triggered.
Locks
Locks are physical security controls that can help keep unauthorized persons from entering doorways, secure areas, and perimeters. Depending on where the locks are placed and what other security measures are in place, locks can be simple and inexpensive or very complex. Although most locks can keep casual intruders out, they really serve only to delay a determined intruder for certain amount of time and rely on multiple other physical controls to assist in keeping an intruder out. Delay factor is sometimes a consideration in choosing a lock for a particular use.
Among the different types of locks are hardware (or mechanical) locks and electronic locks. Most hardware locks use ordinary keys and can be purchased from a hardware store. Combination locks, which require a numerical combination or pin code to unlock them, and locks built into the door or other type of entrance (such as a gate or vault) are also popular hardware locks. Each has advantages and disadvantages, depending on the level of security you require. Each also has different variations. Ordinary padlocks, referred to as warded locks, may appear to be strong, but they can easily be cut or picked. Physical locks, called device locks, are used to lock down items that are easily stolen, such as laptops. Some mobile devices have a special slot to facilitate this type of lock.
Electronic locks are more sophisticated and may use various protection mechanisms. Usually, an electronic lock uses a PIN code and may be known as a cipher lock. Electronic locks usually have their mechanisms protected by metal containers or embedded into walls. They may be programmable, offering a number of configurable options, such as the ability to program in separate PINs for different people, a lockout threshold for the number of incorrect PIN entries, a lockout delay, and so on. They also may be tied to other security measures, such as smart card and biometric mechanisms.
Guards
Guards are the quintessential picture of physical security controls. Most facilities that have any type of physical security have guards, and despite all of the new advances in technologies that might one day eliminate them, human guards will likely be a cornerstone of facility security for years to come. Guards offer several advantages over electronic physical controls. First, guards are human beings and can make the split-second decisions that are sometimes needed in fast-moving security, safety, or emergency events. Second, a well-trained guard force can provide vast, intelligent coverage of all physical security areas within a facility. If guards have solid, comprehensive security procedures they execute on a timely basis, they can help eliminate the huge majority of physical security problems. Guards are required to be conscientious, observant, well-trained, and even a little bit suspicious and paranoid to do their jobs well.
The disadvantages of using guards don’t outweigh the advantages, but you should be aware of them all the same. First, guards require resources, such as specialized equipment, training, and even monetary resources (whether contracted out or as part of the organization’s own internal security force). Maintaining a guard force can be quite expensive and has challenges that are typical to maintaining human resources, such as pay, benefits, disciplinary problems, promotions, and so forth. Guards are human beings, like any other employee, and some have the same weaknesses that any other employee would have, regardless of specialized security training. Human beings miss things sometimes, they aren’t always in as observant as you would like, and sometimes they can fail to follow security procedures to the level you need. They can also be subject to social engineering attacks (discussed in a later module). All-in-all, however, guards provide an effective set of security controls that are considered deterrent, preventative, detective, corrective, compensating, and recovery, all at the same time. They can also be assisted by other types of physical security controls, including alarms, surveillance devices, and other IDSs.
Video Surveillance and CCTVs
Closed-circuit television systems can be placed throughout a facility. CCTVs use cameras to record surveillance video and transmit it to a central monitoring station, which enables guards to extend their view of the facility. CCTV systems are designed to detect and watch intruders in areas where guards can’t be all the time. Some considerations with CCTV devices include whether the device will be used indoors or outdoors. Outdoor environmental factors such as temperature, wind, rain, and so on can affect how well certain CCTV devices work outside. The size of the area under CCTV surveillance is also a consideration, in that the field of view (how large an area the camera can “see”) for different CCTV systems varies. The amount of light in an area is also a consideration when you install CCTVs in an area, since more light provides a better picture of the area. Some CCTV systems are specifically designed for use in poorly lit or dark areas.
CCTV systems should be integrated with other physical security systems, such as alarms, motion detectors, and so on, and should be directly integrated with the central monitoring console used by the physical security personnel. They should also allow you not only to view areas in real-time, but to record events to media for later review. Systems should also date and timestamp those recordings so that a realistic timeframe of events can be reconstructed if needed.
There may be some speculation as to which is better—a human guard or a video surveillance system. Human guards can make quick decisions and perform a wide variety of security functions, but they can’t be everywhere at once and they can miss things. Additionally, a guard’s memory may or may not be reliable when trying to determine exactly what happened during an incident. Video surveillance systems, on the other hand, can be placed wherever you need them, can provide real-time surveillance of areas, and can record video for later playback and review. Any speculation over which to use isn’t really worthwhile, though; a good layered physical security system should use both guards and video surveillance systems to provide comprehensive coverage of a facility. Video surveillance systems can be used to extend the eyes and ears of guards into places where they can’t be all the time. Guards can quickly be dispatched to any areas that video surveillance picks up any potential security issues and can effectively mitigate those issues. Guards and video surveillance systems complement each other and should be used together. Facilities security managers shouldn’t need to make the choice between guards or video surveillance because of budget or resource restrictions; they should simply use both.
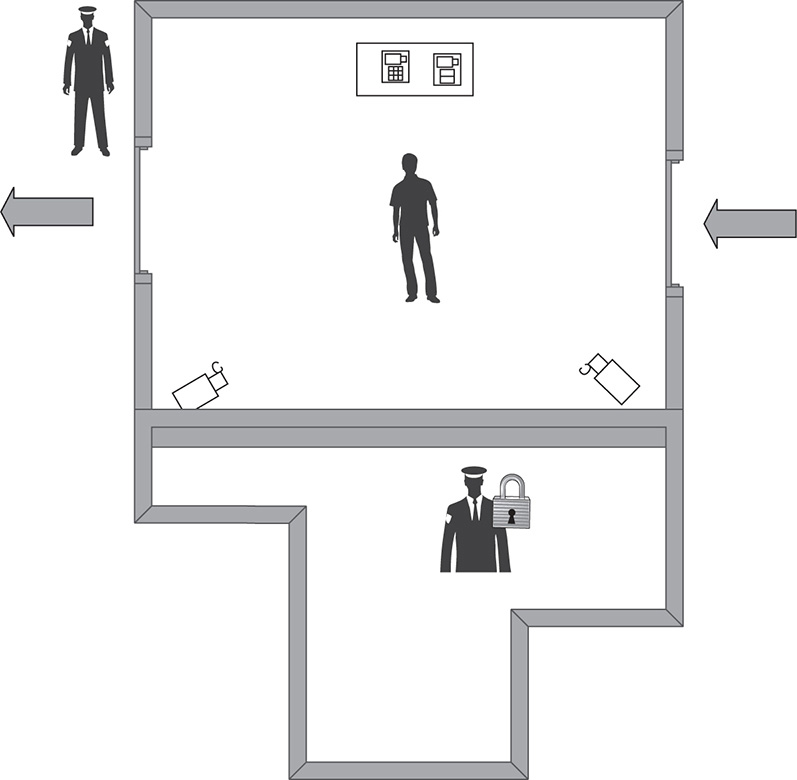
Mantraps
Mantraps are used to guide and control individuals physically as they enter or exit a facility. A mantrap is a small room or compartment, with two doors that are individually locked, usually electronically. One individual at a time enters the mantrap, and the entry door is locked. There’s usually some type of authentication station in the room, or even a one-way glass window so that a guard can observe the individual and confirm his or her identity, or ensure that the visitor doesn’t possess any unauthorized weapons or items. The individual may have to use biometrics or a smart card and PIN to authenticate themselves at the station. If the individual is properly authenticated, the exit doors open and allow the person to enter into the secure area. If the individual is not authenticated, or the guard suspects an issue with the person, he or she can be detained until the proper authorities or security personnel can be summoned to help secure the person. Mantraps are normally used in highly secure facilities when positive authentication of personnel is of critical importance. Mantraps also are used to control tailgating and piggybacking, making them virtually impossible. Mantraps may also use additional security features, such as video cameras, body scanners, metal detectors, and even scales to compare weights when a person enters and exits a facility. This last measure might be employed to ensure that individuals are not stealing items from the facility on exit. Figure 32-4 shows a diagram of a mantrap.
Figure 32-4 A diagram of a mantrap
Access List
You’ve already read that access lists can be used to determine who has access to a particular piece of data, information system, or shared resource on a network. An access list can also be used in the physical security world to determine who can access a particular sensitive area, whether they require an escort or not, and if they are allowed to escort others into an area. An access list can be a typewritten list posted at the entrance door to a sensitive area, showing a list of names of people who are authorized to enter the area, or it can be an electronic access list integrated into a facility’s physical security system. If a person is entered into the system, their access badge will allow them to enter the sensitive area. If it’s not entered into the system, they might be denied access or a guard or a manager may be alerted that an individual who is not on the list is trying to enter a secure area.
Biometrics
We’ve already discussed biometrics extensively throughout the book, but more from a technical or logical control perspective than from a physical security perspective. Biometrics can also be used to control physical access to facilities in secure areas. In addition to smart cards and PINs, biometrics can be used to provide for multifactor authentication that may be required for entrance into a secure area. Examples of biometric methods used for secure entry into a facility include thumbprints, palm scans, retinal or iris scans, and voiceprint recognition. Since each of these methods uniquely identifies an individual, combined with another factor, such as a passphrase or PIN, they can provide for secure access and entry into sensitive areas.
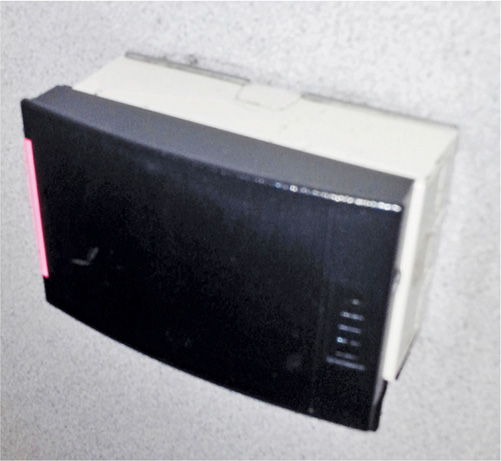
Proximity Readers
A proximity reader device is used to help authenticate personnel entering or exiting a facility. The person places a smart card or other access device near the sensor so it can be read via RFID or another passive wireless technology. The reader receives information from the card regarding the individual’s identity. The individual may further authenticate by using a PIN or biometric methods, such as a thumbprint, retinal scan, or voiceprint. In addition to proximity readers, full contact readers are also available for a facility to use. These readers require that a smart card or other device actually touch the reader or be swiped into the reader a certain way so that it can read a barcode or other type of coding on the card. Full contact readers normally don’t require any kind of passive wireless radio signals. For more efficient and economic use, the same smart cards used to authenticate people physically can also be used to authenticate individuals to information systems, enabling a sort of one-stop physical single sign-on capability. Figure 32-5 shows an example of a proximity badge reader.
Figure 32-5 A proximity badge reader
Barricades
Barricades are physical security devices that can block unauthorized personnel from entering an area. Barricades are often used in the area surrounding a facility to keep vehicles from getting too close to a building, for example. They can also be used inside a facility to control the flow of people through secure areas.
Barricades can be made out of various materials, including concrete and metal. They are usually constructed to delay a determined intruder long enough for security and other response personnel to neutralize any threats posed by the intruder. Bollards are examples of barricades that might be placed outside of a facility around drive-through areas, parking lots, and even sidewalks. Figure 32-6 shows an example of a bollard.
Figure 32-6 Common bollard
Protected Cabling Distribution
Physical security also involves protecting equipment and systems, but it wouldn’t be very effective if the cables that connected the systems were damaged or cut. The systems wouldn’t be able to communicate, rendering them as ineffective as if someone had destroyed or damaged them. Protecting physical cabling is as much about facility design as anything else. The facility should be designed so that physical cabling is run outside of normal traffic areas, through ducts in the walls or ceiling. Their end connection points should be physically protected from unauthorized access, by placing termination points such as switches in locked closets, and protecting end user device connection points in offices and other rooms from unauthorized access. In addition to physical security design, protecting cabling involves other possible measures, including using shielded cabling to prevent eavesdropping (or using fiber cable); configuring systems to send alarms when a connection is lost, possibly indicating a cut or damaged cable; and even using technical or logical controls that prevent unauthorized devices from connecting to end user cable connection points, such as network outlets, by controlling port access.
Alarms and Intrusion Detection Systems
Physical alarm and intrusion detection systems are a must in any physical security program. Alarm systems can be loud and obnoxious, such as fire or tornado alarms, but they can also be silent alarms that sound or activate only at a guard station. Silent alarms alert security personnel without alerting an intruder that he or she has been discovered, giving security personnel time to reach and subdue the intruder. Alarm systems can be activated by any number of factors, including manually by personnel, by opening alarmed doors, and even by motion sensors in an area.
Motion detection involves sensing the presence of a person in an area using different types of sensors. Motion sensors might use invisible light beams that are emitted from photoelectric sensors in a room; breaking the light beams would trigger the alarm. Or the sensor could monitor environmental factors such as temperature, humidity, and air pressure, so that an individual entering that area would change those factors and cause the temperature to rise a few degrees or the air pressure or flow to change slightly. These almost imperceptible changes to the environment might indicate unauthorized personnel in the area and trigger an alarm. Yet another type of motion sensor are plates in the floor that detect weights or pressure on the plates; individuals stepping on one of these plates would trigger an alarm. Keep in mind that motion sensors and some other advanced types of physical intrusion detection systems are typically used only in highly secure areas, although commercial and private grade motion sensors can be used in small businesses and homes.
Escape Plans and Routes
Escape plans directly affect personnel safety. In addition to the standard plans that are required for fire evacuation and other disasters, escape plans should also be provided in the event of human-based threats, such as terrorist attacks, active shooters, thieves, or other types of intruders. All escape plans basically include the same requirements: they should show all the possible exits from a facility, provide for facility-wide notification in the event of an emergency that requires evacuation, and provide for orderly exit of all personnel, including accounting for everyone in the facility so that no one accidentally gets left behind. Escape plans should be written with personnel safety as the top priority; they should not normally include provisions for shutting down equipment, backing up data, and so forth. Although those areas are important in the event of a disaster, saving human life and preventing injury must come first, before worrying about data or equipment. The time to worry about backing up data occurs well before a disaster strikes. Later modules on business continuity (Module 41) and disaster recovery (Module 42) discuss those issues in depth.
Escape routes are of critical importance during an emergency or other disaster, simply because all the personnel working in the facility need to know how to get out in the event of a fire or another type of incident. If this hasn’t been planned for in advance, confusion and mayhem may result in someone getting hurt or not being able to get out of the facility safely. Most local laws and regulations stipulate that escape routes be established, briefed to personnel, and posted throughout a facility so they can be referenced in the event of an emergency. Escape routes should provide for the safest, quickest, and most efficient way out of the building, and they should never be blocked by any obstacle or be made difficult to access. Building alarms and electronic locks should be configured in the event of a disaster so that alarms sound loudly to alert people to an incident, and so that electronic locks do not fail open so that people can use otherwise secured doors to get out of a building. Figure 32-7 shows a posted escape route for a facility.
Figure 32-7 A posted escape route
Testing Controls and Drills
Perimeter controls should be periodically tested to ensure their effectiveness. Testing involves exercises and drills that are conducted on a frequent basis to make sure that they work properly. It does no good to have a secure entryway if you’re not sure it’ll work in the event someone actually tries to break into it. Physical security testing should be conducted against the facility by authorized personnel who are trained on those types of tests. Guards should be tested for following their procedures and being able to react quickly and efficiently to physical security threats. Automated and electronic alarms and physical security systems should also be tested to make sure they work properly and will actually detect and alert a real threat. While some tests should be pre-planned and scheduled regularly, some of these tests should be conducted on a no-notice basis, so that people have to remember what to do and react quickly in the event of a physical security threat. Although tests can be inconvenient and sometimes disrupt operations, they’re a necessary evil to make sure that physical security controls work the way they’re supposed to.
Drills are a form of testing, in which incident and disaster response procedures are tested to ensure that everyone knows what to do and that the procedures function effectively. A drill can be a fire drill, a tornado drill, or even an active shooter drill where everyone practices what to do in the event a disgruntled employee or someone from outside a facility intrudes with the intent of perpetrating acts of violence on people or facilities. Drills should be carefully planned out and executed frequently, sometimes with no notice, so that facility managers are able to determine if everyone knows what to do when unexpected emergencies occur. Like other types of disaster response testing, drills should be monitored for compliance with procedures, as well as for those instances where procedures don’t work the way they should. Drills can tell you whether the right procedures are in place, whether everyone knows what to do, and whether the right supplies and equipment are in place to evacuate everyone from the facility quickly and efficiently. They can point to training deficiencies and help you improve your emergency procedures.
Module 32 Questions and Answers
Questions
1. To which of the following types of controls do policies and procedures belong?
A. Physical
B. Administrative
C. Logical
D. Operational
2. Which of the following control functions are used to determine if a security issue or violation has occurred?
A. Detective
B. Preventative
C. Compensating
D. Recovery
3. All of the following are characteristics of fencing you should consider when deploying it around your facility, except:
A. Gauge
B. Height
C. Mesh
D. Fire rating
4. Your manager wants you to deploy signage around your facility that expressly warns potential intruders that the facility is alarmed and that intruders will be met with armed response. In this situation, what kind of control functionality is the signage fulfilling?
A. Preventative
B. Deterrent
C. Compensating
D. Corrective
5. How should lighting installed along a perimeter fence be set to activate?
A. To activate when someone approaches the fence
B. To activate only when alarms detect an intruder
C. To activate between dusk and dawn
D. To be turned on 24 hours a day
6. Which of the following are advantages to employing a guard force in a facility? (Choose two.)
A. CCTVs can be in places where guards cannot always be.
B. Guards can make split-second decisions during security incidents.
C. The vast majority of facility security issues can be handled by well-trained guards.
D. Guards are not susceptible to social engineering.
7. Which of the following is not a benefit of using a mantrap?
A. It can serve as a single controlled entry point into a facility.
B. It can assist with positive identification and authentication of individuals entering the facility.
C. It can prevent unauthorized individuals from entering a secure facility.
D. It can protect individual information systems from unauthorized access.
8. Which of the following is a valid physical cabling protection control?
A. Running cable away from high pedestrian traffic areas
B. Terminating cabling in public areas
C. Running fiber cabling through a high traffic area monitored by CCTVs
D. Using unshielded cabling in highly sensitive data processing areas
9. Which of the following is the top priority when planning evacuations and escape routes?
A. Backing up critical data
B. Shutting down servers in an orderly fashion
C. Personnel safety
D. Securing sensitive information before the evacuation
10. What purpose does conducting no-notice evacuation drills serve?
A. To find fault with the evacuation planning manager
B. To determine if people have the right training and procedures in place
C. To motivate people to learn the proper evacuation procedures
D. To satisfy the company’s legal obligations
Answers
1. B. Policies and procedures are administrative controls.
2. A. Detective controls are used to determine if a security issue or violation has occurred.
3. D. Fire rating is not a consideration when deploying fencing, since fences are not designed to prevent or suppress the spread of fires.
4. B. In this situation the signage is acting as a deterrent control, since it relies on potential intruders knowing about what it says and understanding the consequences in order for it to be effective.
5. C. Lighting installed along a perimeter fence should be configured to activate from dusk to dawn.
6. B, C. Guards can make split-second decisions during security incidents, and most facility security issues can be handled by well-trained guards.
7. D. A mantrap cannot protect individual information systems from unauthorized access.
8. A. Running cable away from high pedestrian traffic areas is a good physical security control.
9. C. Personnel safety is the top priority when planning evacuations and escape routes.
10. B. No-notice drills are used to determine if people have the right training and procedures in place.