This is the most important skill that's used to assess an application, so that you can understand how an application works through the data it receives and sends. That is the reason why the HTTP proxy is the most useful tool for a bug bounty hunter focused on web applications.
A HTTP request can tell us a lot about an application, for example:
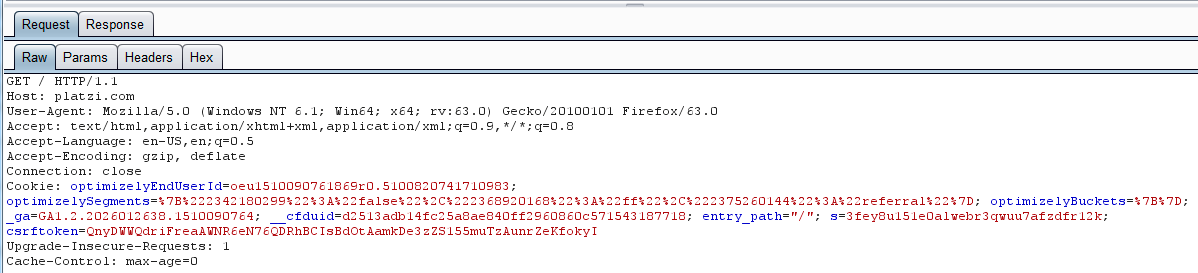
This request give us information about the application being analyzed. Just from the request, we know the host (Host:), the use of a security token to avoid cross-site request forgery attacks, and we have some variables that, at this moment in time, we do not know about regarding how they work. But, we can determine their use by analyzing requests.
You need to review each request in order to understand how the application works, and get all the possible information about it. Try to look for requests that show its structure and how the application works internally.
It is useful to detect the parts where the application is not working as you expect. Currently, most parts of the application are developed using a framework, independent of the language. But sometimes, developers avoid the framework's methods and use their own methods. This could lead to vulnerabilities, and detecting these vulnerabilities in the requests is useful.
