It is not just the use of a testing string like <script>alert(1)</script> a way to detect XSS bugs, actually it is important to understand how the information is showed by the response in the application, in order to know how to exploit a XSS.
If we examine the response generated by the application, we can understand more about how the application and bug is working.
Let's check the exploited example again. Here, we have a form to submit comments to a website:
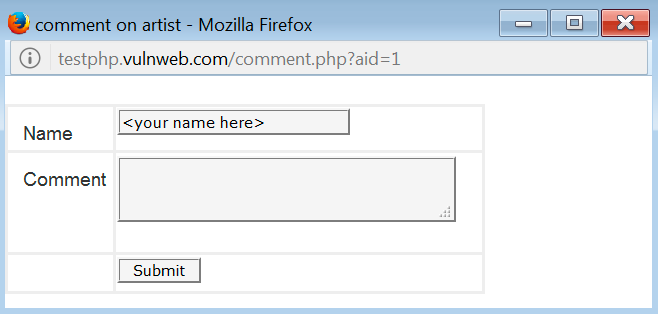
If we use the application as it is supposed to be used:
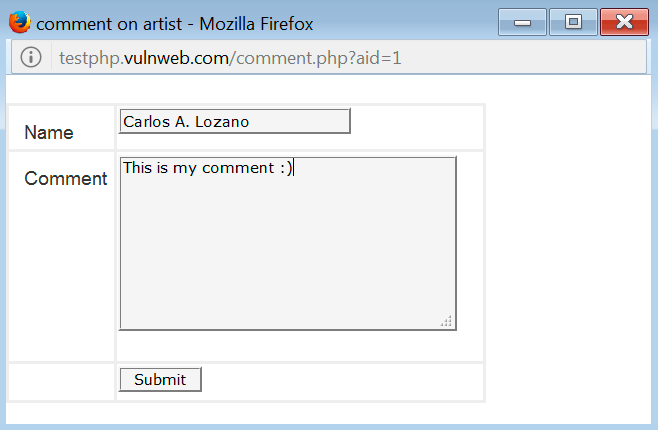
You will see that the value entered in the parameter name is immediately shown to the user in order to thank them for the comment submitted to the application:
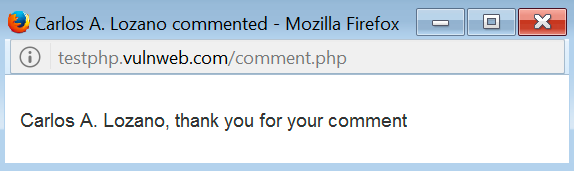
So, take it as a tip that all the inputs that are taken by the information entered by the user, and showed to the user in response, it could be susceptible to a vulnerability. OK, back again and now enter a special character to know how the application manages them:
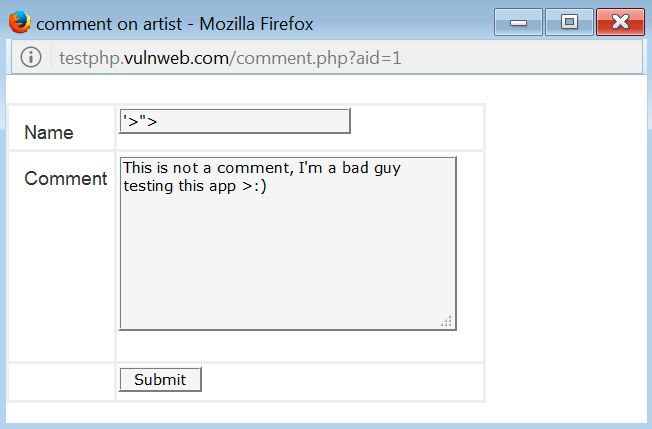
In the previous image, we are entering some special characters. I selected them because they are usually used for HTML code. So, if the application does not manage these characters in the correct way, there are a lot of possibilities that an XSS bug may be present. After sending the message, we can see the response:
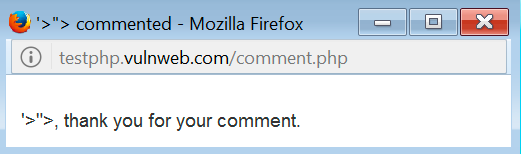
OK, the application is showing the special characters, but wait. We are going to see how these characters are represented in the HTML code, because it is possible that the application is encoding these characters or are managed in a correct way in order to show the string to the user, but without risk. The following screenshot shows how the characters are represented in the code:
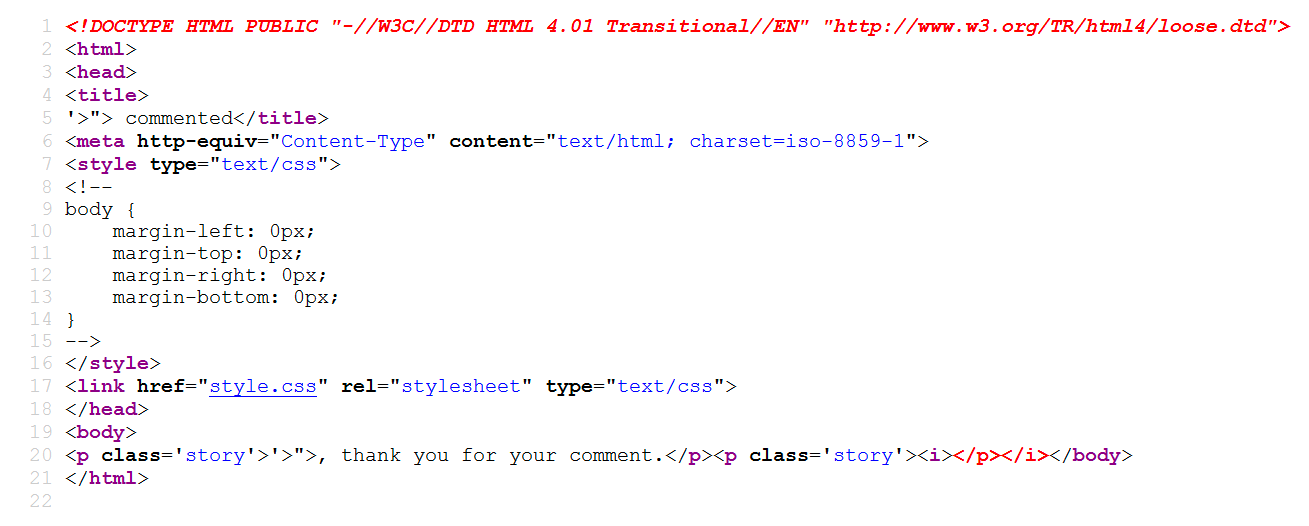
In the HTML code, we can verify that the application is showing the special characters just as they are. So, it is perfect! It means if we insert the JavaScript code here, it will be presented as is:
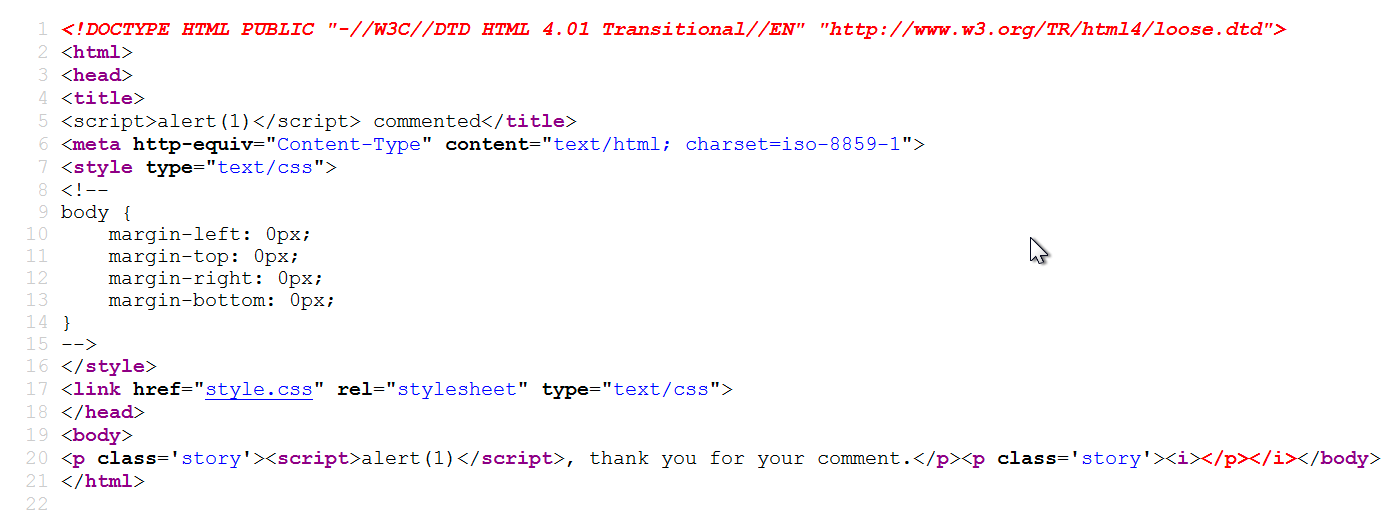
Now, you can see that the malicious string is shown as is, and when the web browser parses it, it shows the pop-up.
So, the conclusion is to find XSS bugs, and in general input validation vulnerabilities, try to understand how the application is managing the information entered by the user. And remember, test all the parameters, not just one.
