Most of the vulnerabilities described in this book and that you can find in web applications, the basic tool to detect, analyze, and exploit them, is an HTTP proxy. In order to detect XSS bugs, we are going to use the HTTP proxy to analyze each HTTP request made by the application that we are assessing. And field by field, we are going to be modifying the content with some basic testing strings.
The most basic string to use is this one:
<script>alert(1)<script>
This string launches a pop-up message in the browser showing the number 1; it is less useful, but perfect for finding XSS vulnerabilities. It is important to note that in easy cases, the use of the HTTP Proxy may not be necessary, and you can inject the testing string directly into the fields on the website. But nowadays, basically all applications have controls implemented in the frontend to avoid basic injections. These controls encode the strings entered with special characters, into formats less dangerous than the application can manage.
The basic rule for input validation security controls is the input validation needs to be made in the backend (or server side), not in the frontend (or server side). The validations made in the frontend are just for performance purposes, and to avoid basic script kiddies.
So, look the following image, where you can see in Burp Suite how an HTTP request looks:
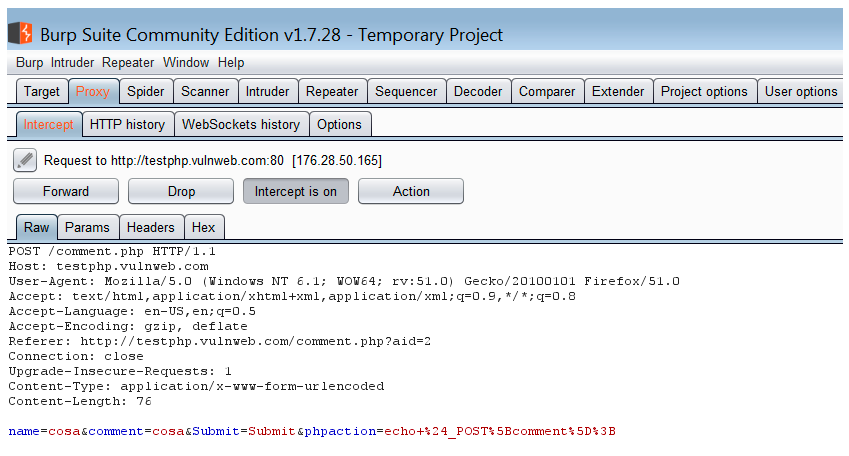
In this request, we have four parameters: name, comment, Submit, and phpaction. It is important to remember that not only do the parameters used as fields in a form need to be considered as parameters, but all the parameters in a request are equally important, because sometimes developers use these hidden parameters as control variables to manage website functionality. And as these parameters do not have user interaction theoretically; they are more likely to be vulnerable.
So, we need to substitute each value in the parameter with the testing string, and see what happens:
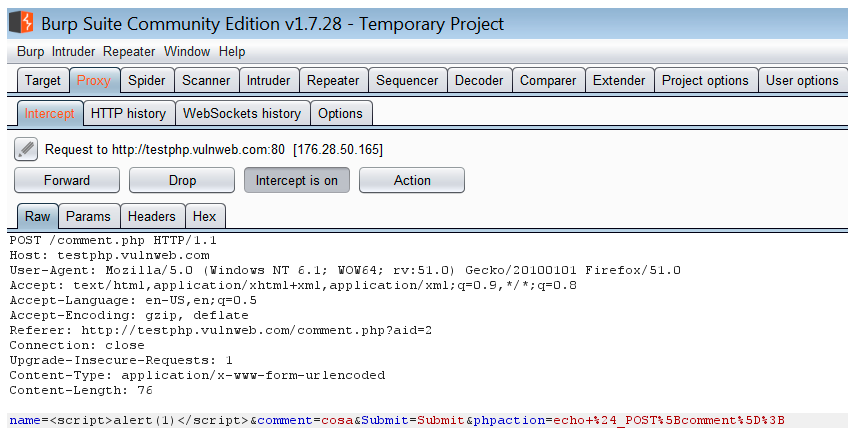
In the previous image, we substitute the cosa value in the name parameter for the testing string. And after sending the modified request to the server, the result is the following:
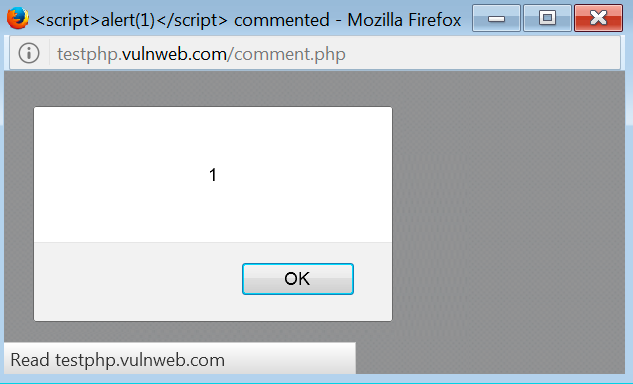
Now, you can see that this is a reflected XSS.
