In 2014, a bug bounty hunter named Patrik Fehrenbach, found a file showing the phpinfo() result on Yahoo. This is a common issue.
The tips to detect these kinds of issues are explained in the following section.
You can use an extended list of the most common files in Burp's Intruder tool, and send it to an application, as follows:
- In the Intruder tool's window, navigate to the Payloads tab, select a file with your most common files list, and click on load:
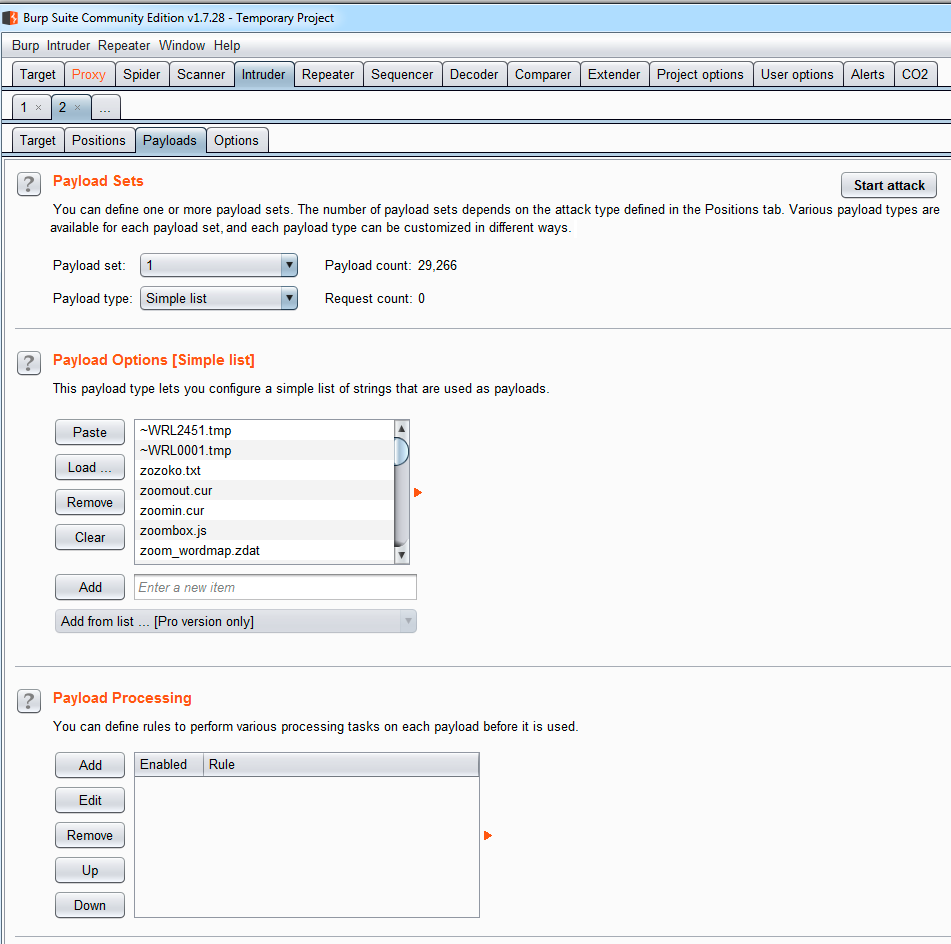
- Navigate to the Positions tab, where you will find the request you want to fuzz with Intruder. Usually, here, we select the variables to test, but in this case, we will launch the Intruder to the path. This means that we are going to create an imaginary variable to select a position, and then test the files and paths on it:
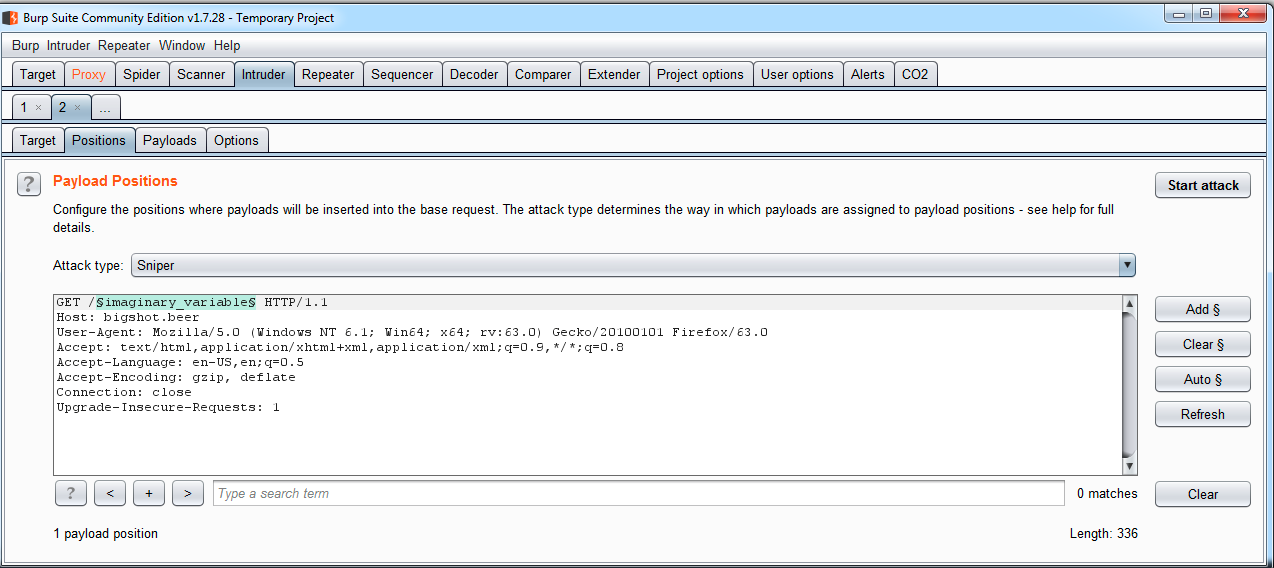
- Launch the Intruder tool's attack and analyze it, looking for an HTTP 200 error code, which means that the file exists. This is a simple way to detect juicy files and paths, without generating a lot of noise (so much traffic) to the application, which could be detected by security controls:
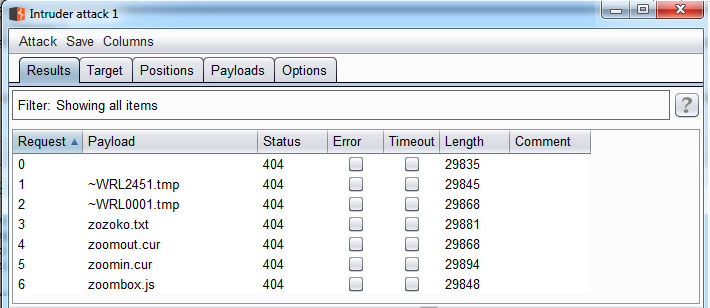
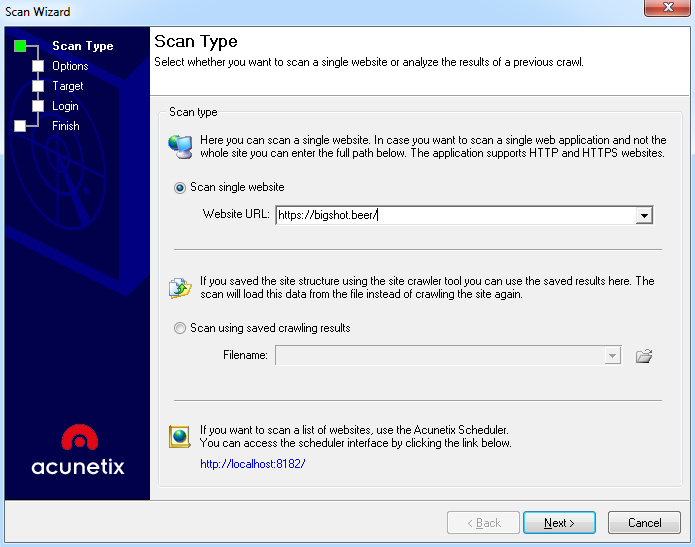
Another method to detect this type of issue is by using a vulnerability scanner—but not for an infrastructure like Nessus, but a vulnerability scanner focused on applications. There are many scanners, but all of them have the same basic flow. Let's check out Acunetix, a very popular scanner:
- Acunetix has a wizard to launch the scan. The first window is used to enter the target. You can add an IP address or a domain name:
- As Nessus, it is possible to select a profile, which is the set of rules to scan the application. Sometimes, you want to be selective and just launch scans to detect certain types of vulnerabilities, because of security controls, or because you are looking for something in particular. Also, it is possible to figure out the number of requests, latency, or time stamps:
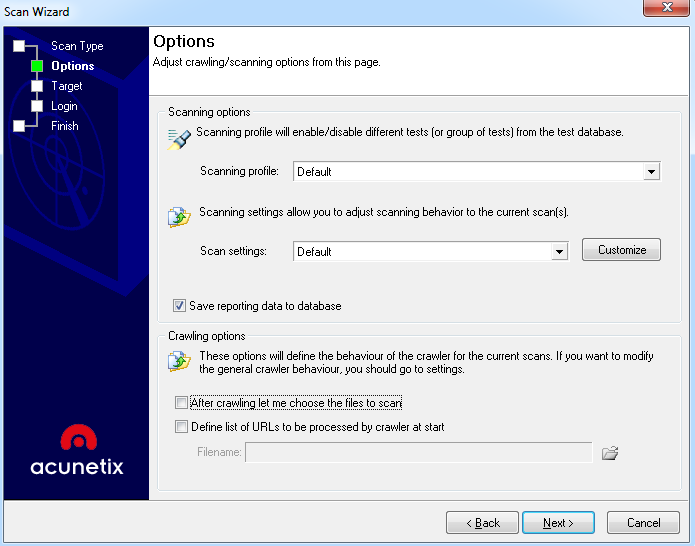
- Acunetix is going to configure some improvements to the scan by detecting the technology used in the application:
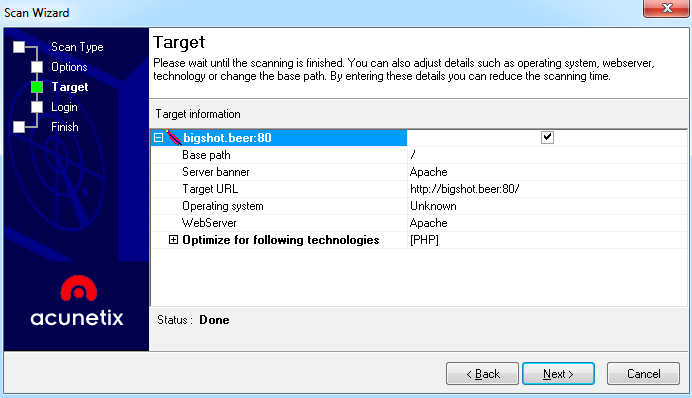
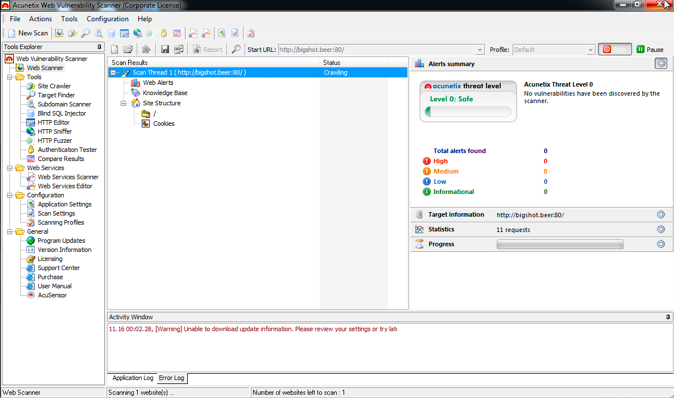
- Launch the scan. Acunetix will be showing the findings, such as sensible files and paths, but also vulnerabilities such as cross-site scriptings (XSS) and SQL injections (SQLi). Remember, any tool can detect application logic vulnerabilities by itself; human intervention is necessary for it:
If you want to read more about this bug, visit https://blog.it-securityguard.com/bugbounty-yahoo-phpinfo-php-disclosure-2/.
