As we mentioned in the introduction, the problem with exploiting blind SQL injection vulnerabilities is that it is not possible to see the result generated directly; it is necessary to infer whether the injection is working or not.
Basically, there are two ways infer whether a blind SQL injection is working or not: the first one is by the differences in the HTTP response content. A tip to identify these differences is to use the information provided by Burp Suite related to the response size.
In the next screenshot, you can see some HTTP requests. You can use this window to determine the differences between all of them using the Length column:

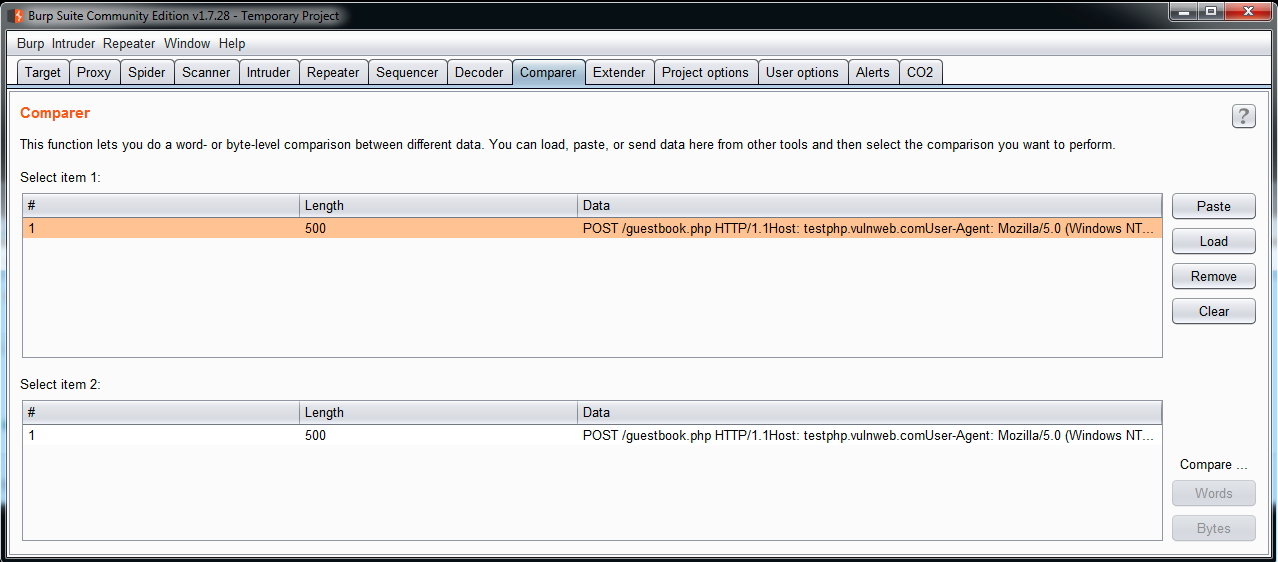
When you identify a different request, compare the original with the different request using the Comparer tool, which is also included in Burp Suite. Just copy and paste the requests or responses to see the differences, as shown in the following screenshot:
The other main method to determine when there is the possibility of a blind SQL injection is using time operators to generate a delay and seeing whether a SQL statement was executed or not. The most commonly used operators are the following:
BENCHMARK
ENCODE
waitfor
IF
