On March 29th, 2017, a bug bounty hunter called InjectorPCA reported gaining access to the Amazon S3 buckets, which are used by HackerOne.
This bug is similar to the Shopify error. Therefore, we can summarize the following conclusions about it:
- Try to reproduce the previous vulnerabilities detected in the application you are assessing. There's no need to reinvent the wheel.
- A tip is to launch an automated vulnerability scan to all the targets included in the bounty, at the beginning, while you are manually assessing the application. Also, it is recommended you launch a port scan and service detector. It does not matter what the vulnerability assessment tools do; it use a specific tool like Nmap to perform the assessment.
- Try to be clear in your evidence and about the impact of each vulnerability you report. When InjectorPCA discussed the consequences of having access to HackerOne's buckets in his report, he showed a list of directories stored in a bucket, and how he uploaded and deleted files from there, as in the following screenshot:
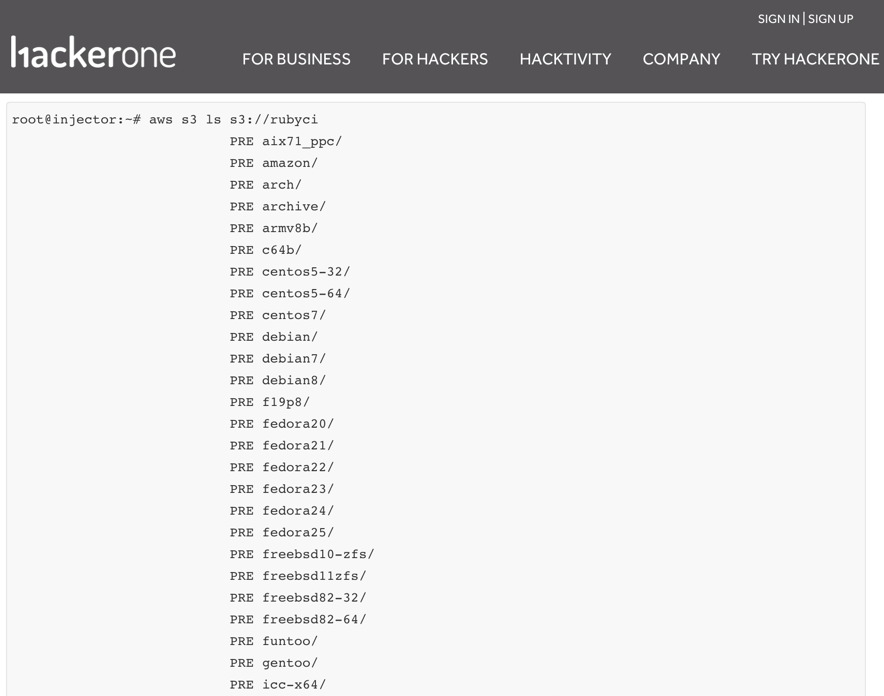
If you want to read more about this bug, visit https://hackerone.com/reports/209223.
