- Title: DOM-based XSS via Wistia embedding.
- Reported by: reacter08.
- Bounty Rewarded: $1,152.
- Web application URL: https://trello.com.
- Description:
Trello is a web-based project management application that utilizes boards and cards based approach to convert the project into an Agile- and Scrum-like interface. It is a very useful tool used by millions of companies worldwide.
This XSS vulnerability was discovered by reactor08, and it is a very good finding because this was actually an XSS in Trello's video integration Wistia. Wistia was responsible for loading malicious JavaScript that could be executed on its client domains. So, a Wistia embedded video with malicious JavaScript can allow an attacker to execute JS on Trello's platform. The bottom line of this vulnerability is the same—that is, to include an alert pay in some part of the malicious JavaScript file and the load that files via a parameter on Trello.
In this case, for instance, the malicious JS file was fast.wistia.net/assets/external/E-v1.js.
It was identified that the wchannel parameter could be used to load JavaScript from Wistia libraries and another parameter, callback, could be used to control the output.
So, controlling the output from the Wistia URL can be similar to the following: https://fast.wistia.com/embed/medias/[video_id].json?callback=[controlled outpoot].
So, the wchannel parameter loading the external JS from the vulnerable WistiaJS file and the callback parameter being used to control the output of the JavaScript file was a combination that triggered this vulnerability.
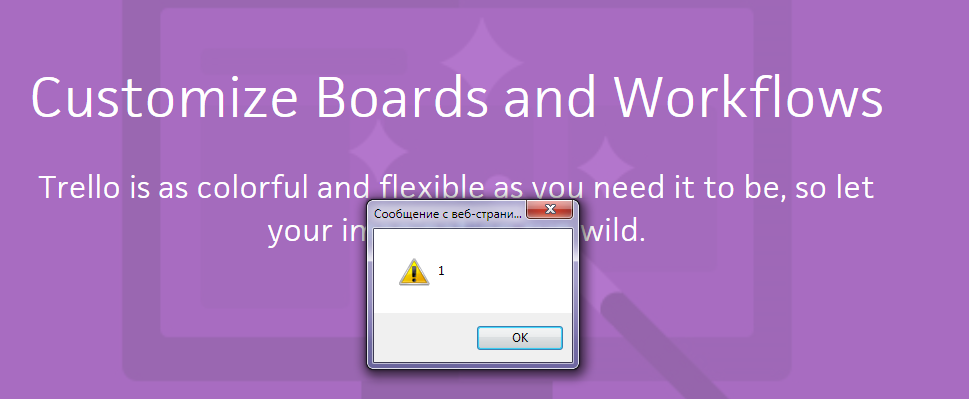
And the output of the vulnerability was displayed as an XSS alert box on every Trello sub-domain:
- Trello Board domain: https://trello.com/guide/customize.html?wchannel=../../../../embed/medias/1yqpy8ics4.json%3fcallback%3dalert(1)%253bvar%20x%3d%27%253bx(//%23
- Trello Blog: http://blog.trello.com/introducing-the-all-new-trello-business-class/?wchannel=../../../../embed/medias/1yqpy8ics4.json%3fcallback%3dalert(document.domain)%253bvar%20x%3d%27%253bx(//%23
- Trello Help domain: http://help.trello.com/article/899-getting-started-video-demo?wchannel=../../../../embed/medias/1yqpy8ics4.json%3fcallback%3dalert(document.domain)%253bvar%20x%3d%27%253bx(//%23
This vulnerability could be exploited by the attackers as a reflected XSS, allowing the attackers to compromise Trello and all other such websites using the Wistia video integration, such as olark.com and wordpress.com.
