On February 23th, 2016, a bug bounty hunter, Simon Brakhane, found that some of Shopify's buckets, created in Amazon S3 service, were open because of an any authenticated AWS user rule.
Despite it being reported as an application logic vulnerability, it is also related with the configuration management category. In any case, this vulnerability provides full access to any user.
You can find this kind of vulnerability by performing a vulnerability assessment on the applications and infrastructure related to a program. There are different tools that allow you to do it. Let's check out Nessus, one of the most popular tools:
Nessus is a vulnerability analysis tool, developed by Tenable. These kinds of tools perform automated vulnerability assessments, mostly by using signatures, to detect potential weaknesses. Nessus is focused on infrastructure vulnerabilities, despite it having web security policies, but not to detect vulnerabilities in all kind of web applications, just in those based on frameworks, CMS, and commercial basis.
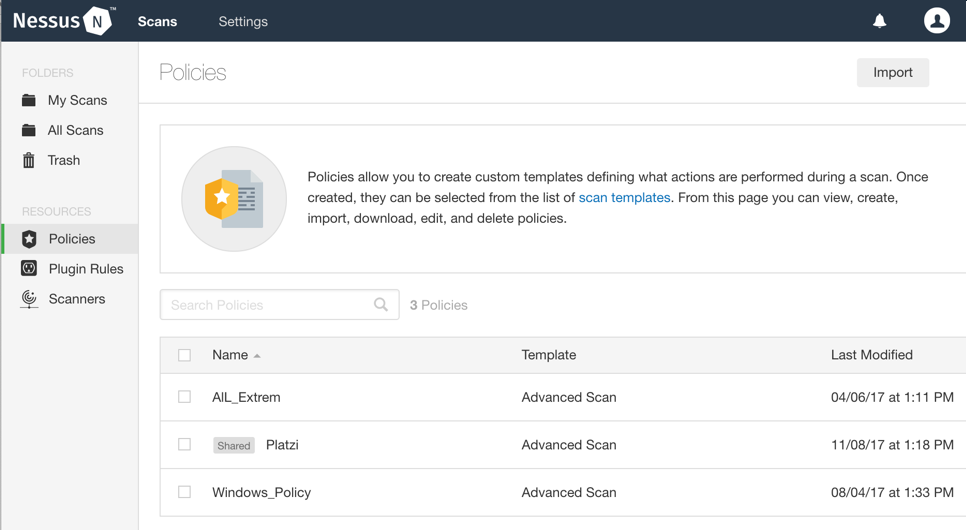
Nessus has two types of licensing: commercial and free. The difference between them is a 15-day delay for policy updates. A policy is a set of rules and clues about certain bugs, which are categorized by groups. In the following screenshot, you can see what the policies look:
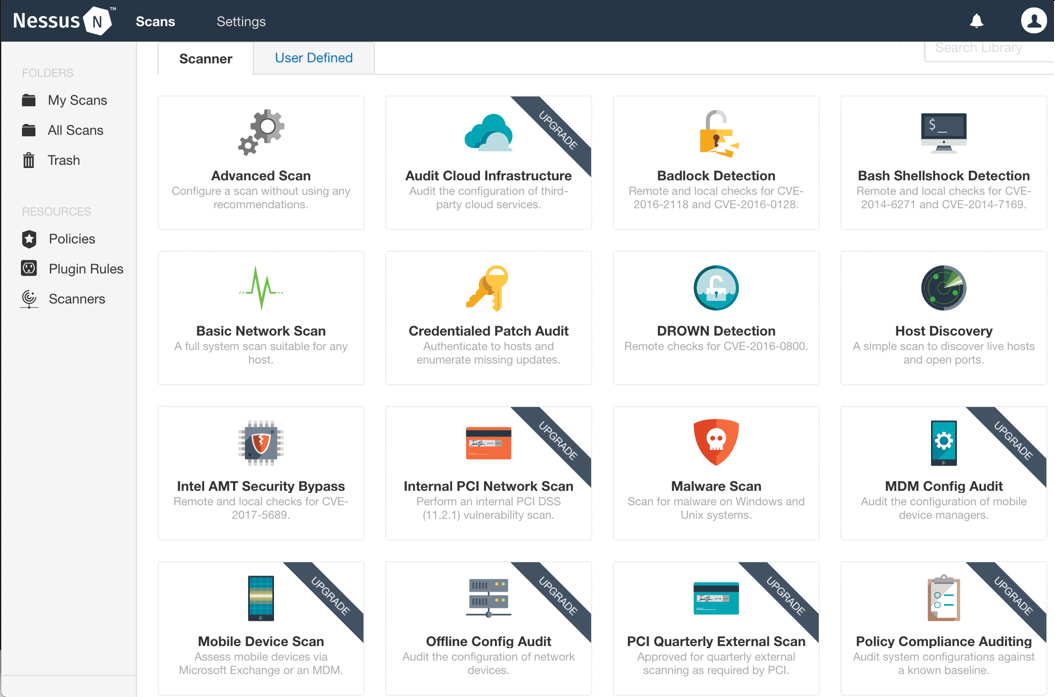
To perform a vulnerability assessment, you just need to go to Scans at the top of the application's menu, and then click on New Scan. Next, you could select a policy from the list of different preconfigured policies, or, if you want something specific to test, you can select Advanced Scan and select each policy by group.
If you are in a private program, where you are identified by an IP address and have a network exception to launch any kind of traffic, I recommend you use an Advanced Scan with all the policies selected. This scan will be very aggressive, generating a lot of traffic, so any restriction that the application derives will be blocked.
If you are not in a private program, but you are assessing an application in an open program, it is recommended that you configure the scan to be the least aggressive one possible, in order to avoid being blocked by a network security control, such as an Intrusion Prevention System (IPS), or even more a load balancer, just because you generated a lot of traffic to a target.
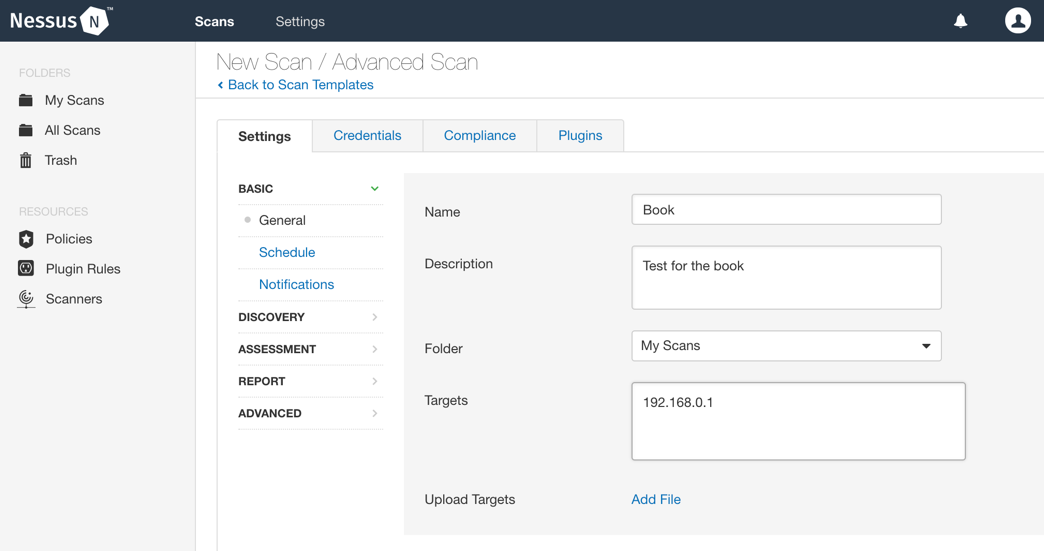
For this example, we are going to select Advanced Scan. In the next view, Nessus asks for general information about the scan, such as a name to identify it, but more importantly, the targets. These targets are usually an IP address, but it is also possible to add domain names, and Nessus will translate them into IPs:
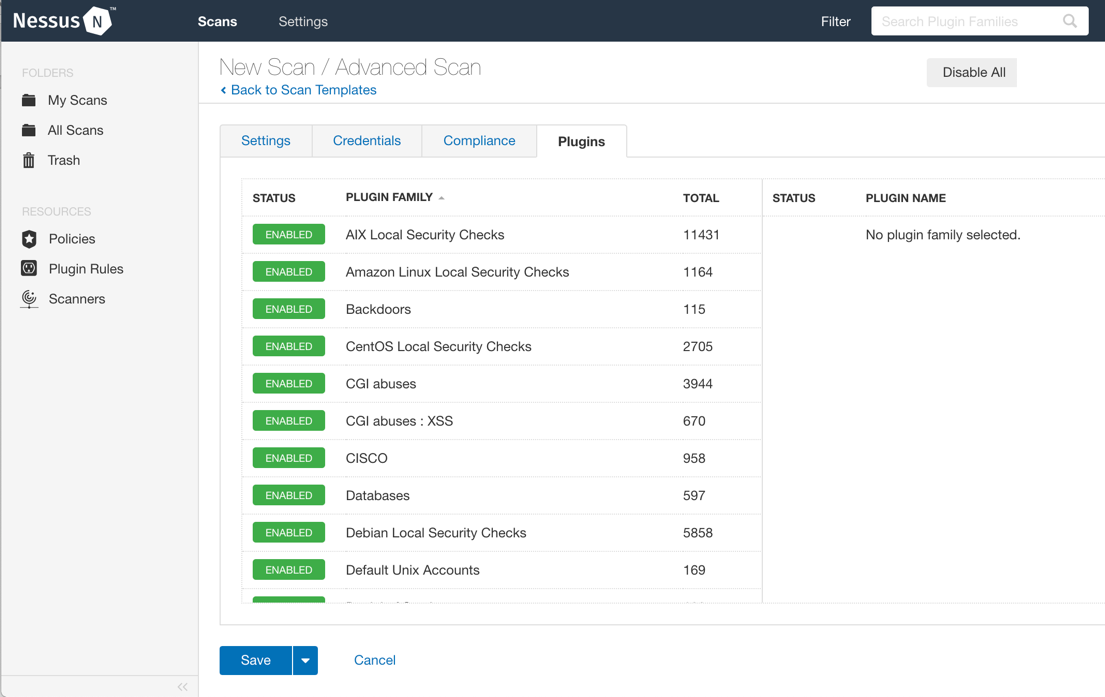
After filling in the data, click on Plugins. Here, you can select the different policies to check during the vulnerability assessment by groups. They need to be selected depending on the information we have about the target. For example, if we have an application running on a Linux server, is not necessary to launch the set of policies for Windows systems. The more personalized the set of plugins, the better:
After selecting all the plugins we want, click on Finish and then click on Start. The scan could take a while, depending on the number of targets, plugins to test, and target response. After finishing, the vulnerabilities will be displayed in Nessus as a report:
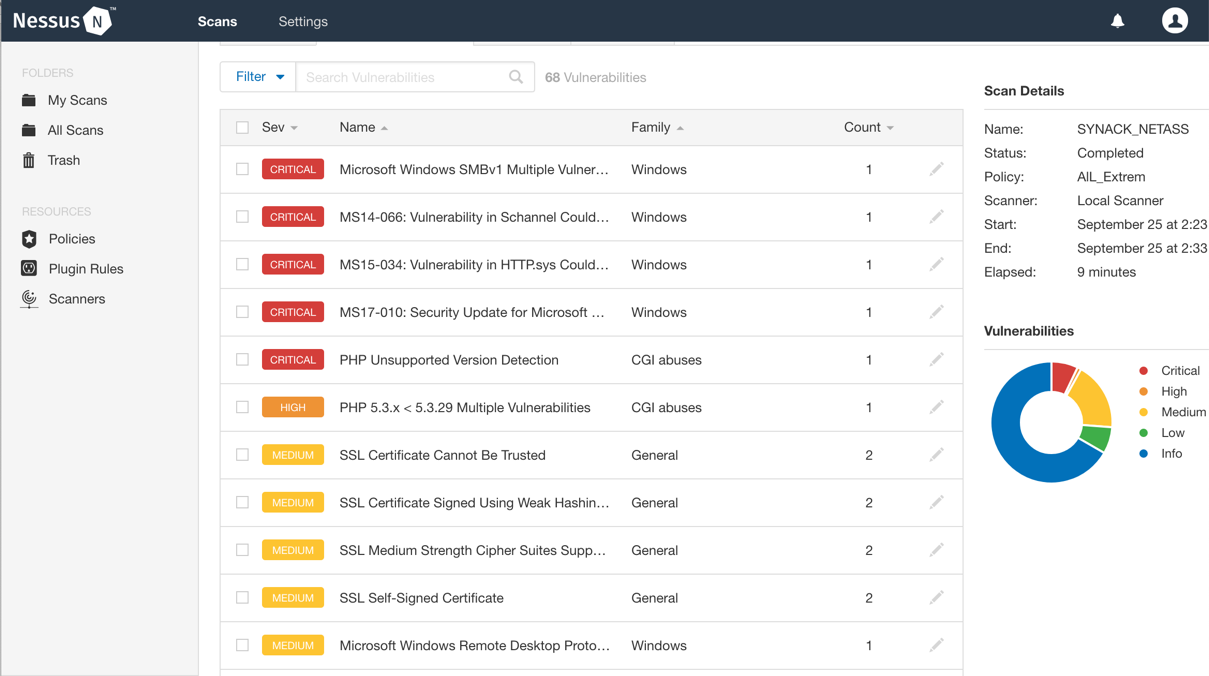
To see details about each vulnerability, click on them, and Nessus will give more information, and in some cases, show whether there is an exploit available for the vulnerability:
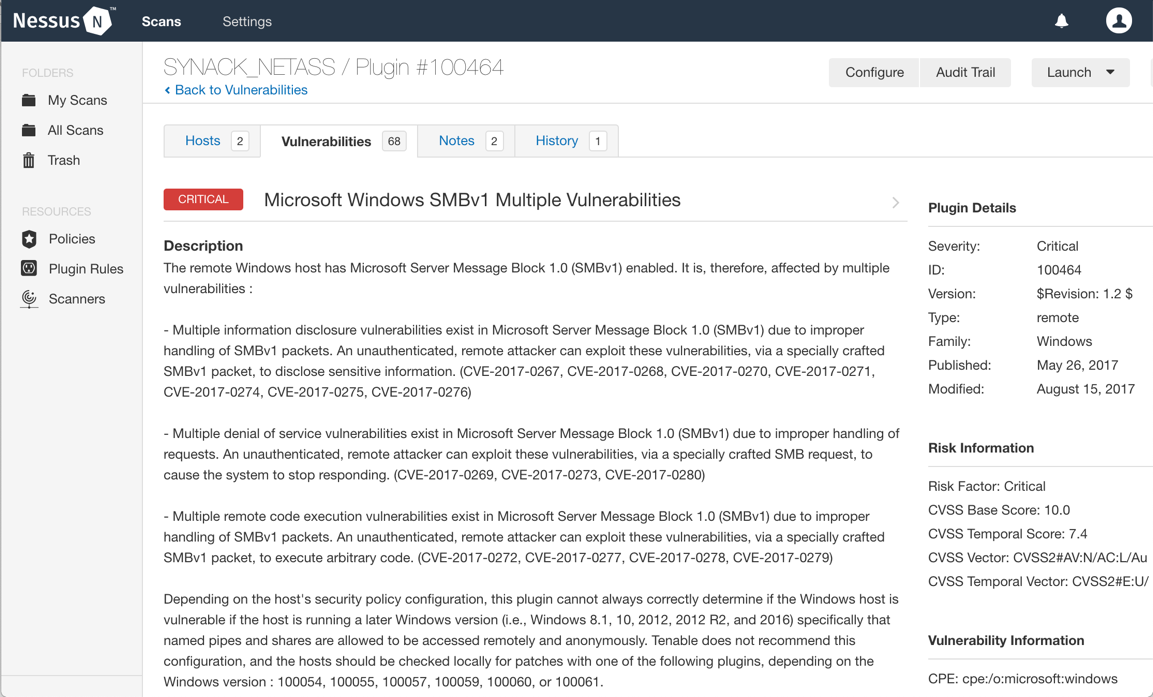
It is important to clarify that all the vulnerabilities detected by Nessus or other vulnerability analysis tools are potential, and not confirmed. Even if a tool confirms the vulnerability, using a clue, fingerprint, or banner grabbing, you need to confirm each vulnerability manually, because these tools never exploit the vulnerability to confirm it, just try to verify by behaviors.
Vulnerabilities, such as the one found in Shopify, could be detected by automated vulnerability analysis.
